A trusted computer system and its application method
A technology of computer system and application method, which is applied in the direction of computer security devices, calculations, instruments, etc., to achieve the effects of reducing production costs, solving mismatching access speeds, and increasing security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0063] The present invention will be further described below in conjunction with the accompanying drawings and specific embodiments, but not as a limitation of the present invention.
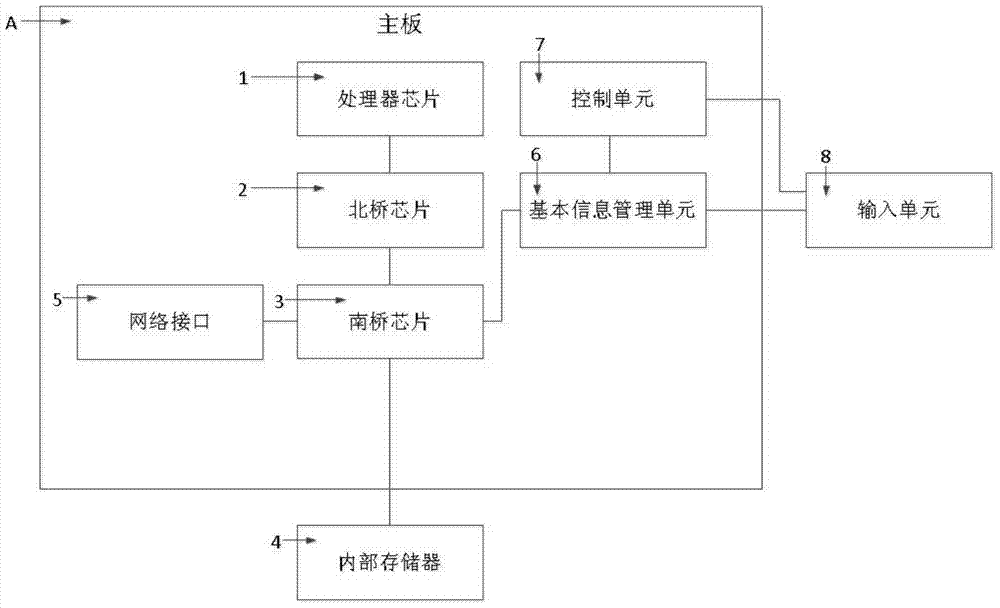
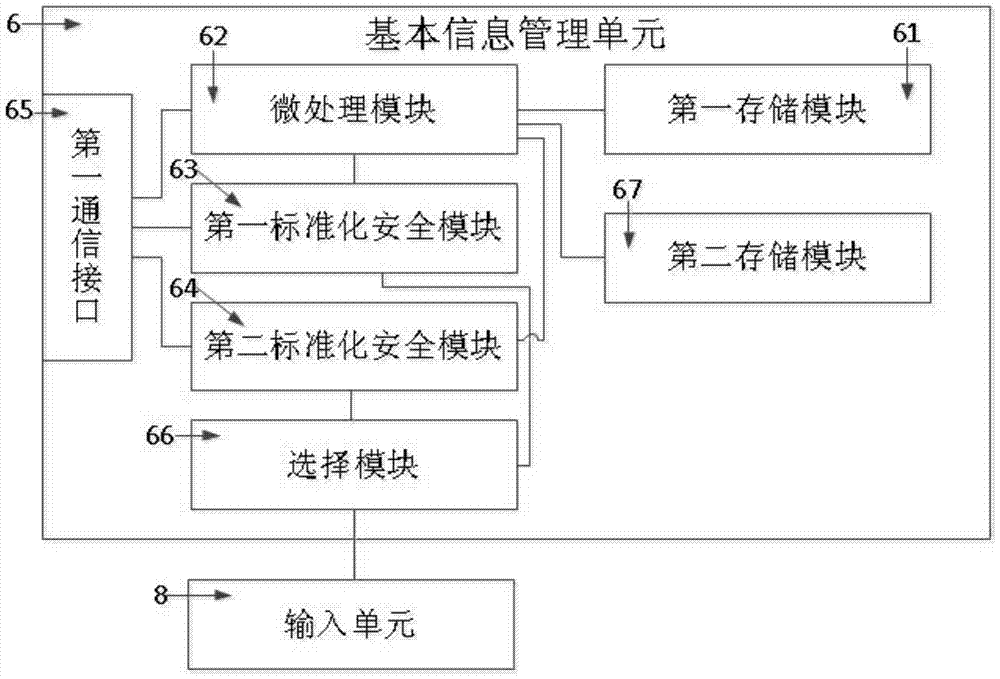
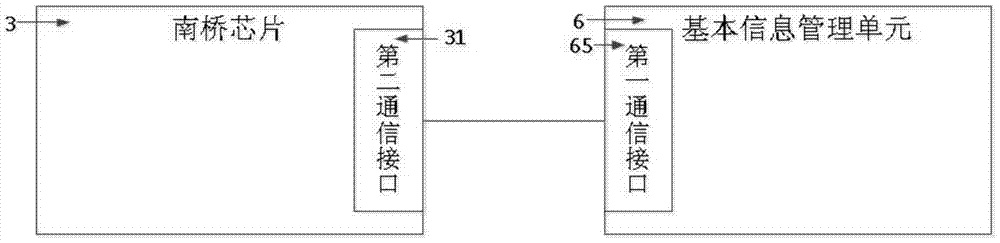
[0064] like figure 1 As shown, in a preferred embodiment of the present invention, a trusted computer system usually includes a motherboard A, on which:
[0065] The processor chip 1, as the core of the trusted computer system for processing data and instructions, supports the normal operation of the trusted computer system. In a preferred embodiment of the present invention, the processor chip 1 may be a high-performance processor chip.
[0066] North bridge chip 2 is connected to processor chip 1. Northbridge chip 2 is the most important part of the mainboard chipset, also known as the main bridge. Internal transmission, providing support for the type and main frequency of the processor chip, the frequency of the front side bus of the system, the type and maximum capacity of the memory, AGP...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com