System and method for data security deduplication in fog computing environment, and cloud storage platform
A technology of data security and fog computing, which is applied in the field of cloud storage, can solve the problems of high re-encryption overhead, MLE is not dynamic, cloud server is not safe, etc., to prevent side channel attacks, save communication overhead, and overcome the problem of high delay Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0072] In order to make the object, technical solution and advantages of the present invention more clear, the present invention will be further described in detail below in conjunction with the examples. It should be understood that the specific embodiments described here are only used to explain the present invention, not to limit the present invention.
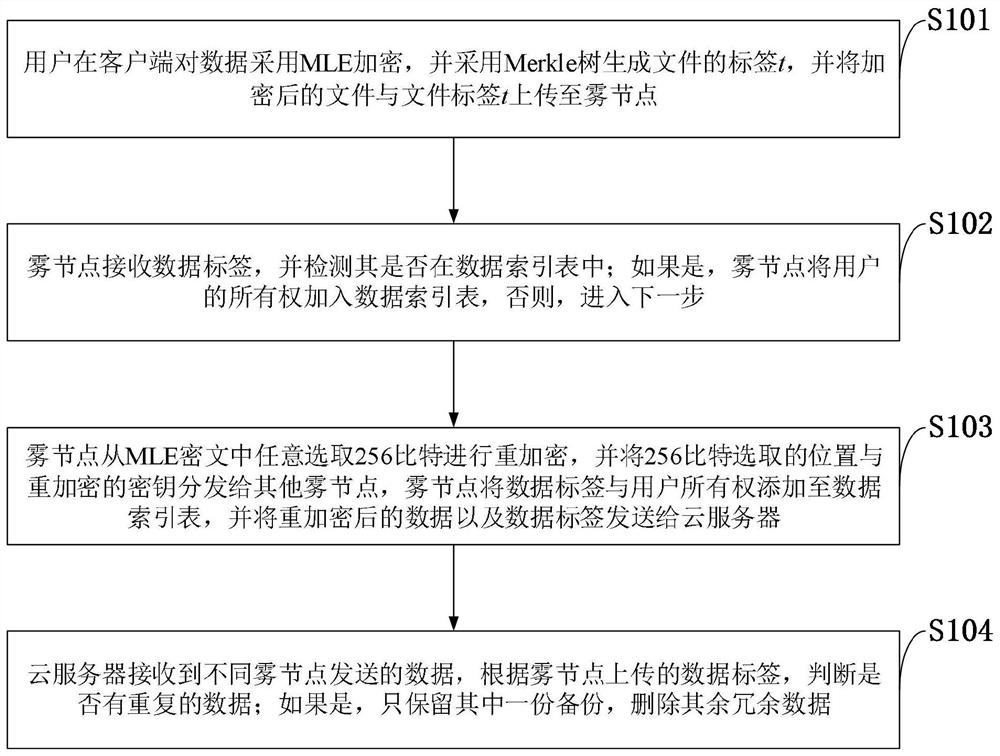
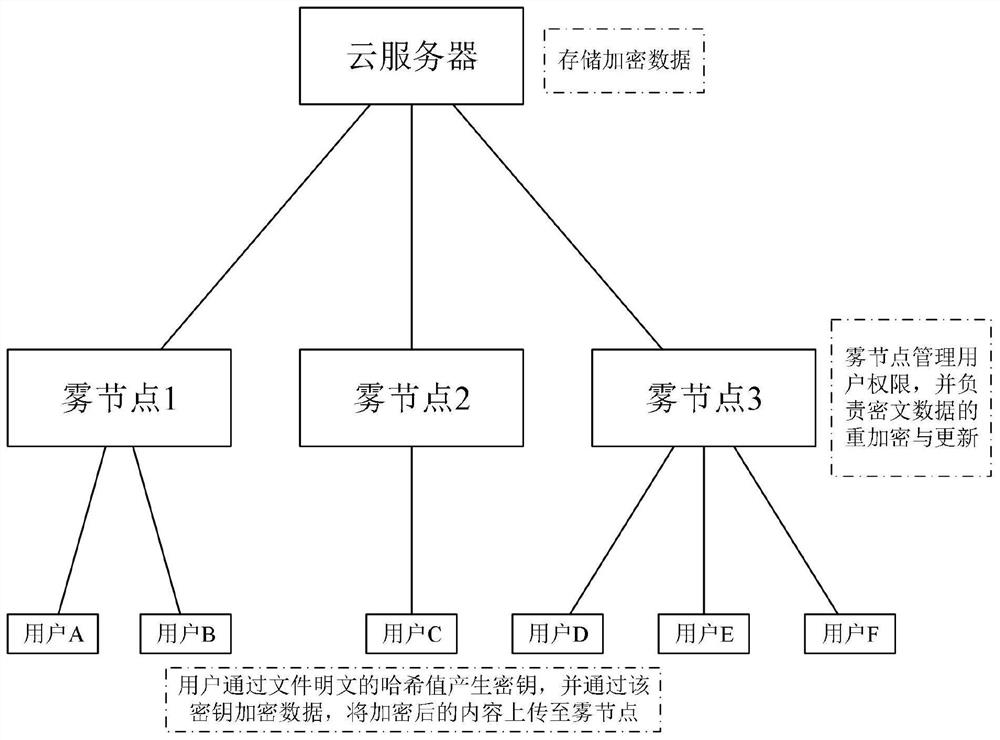
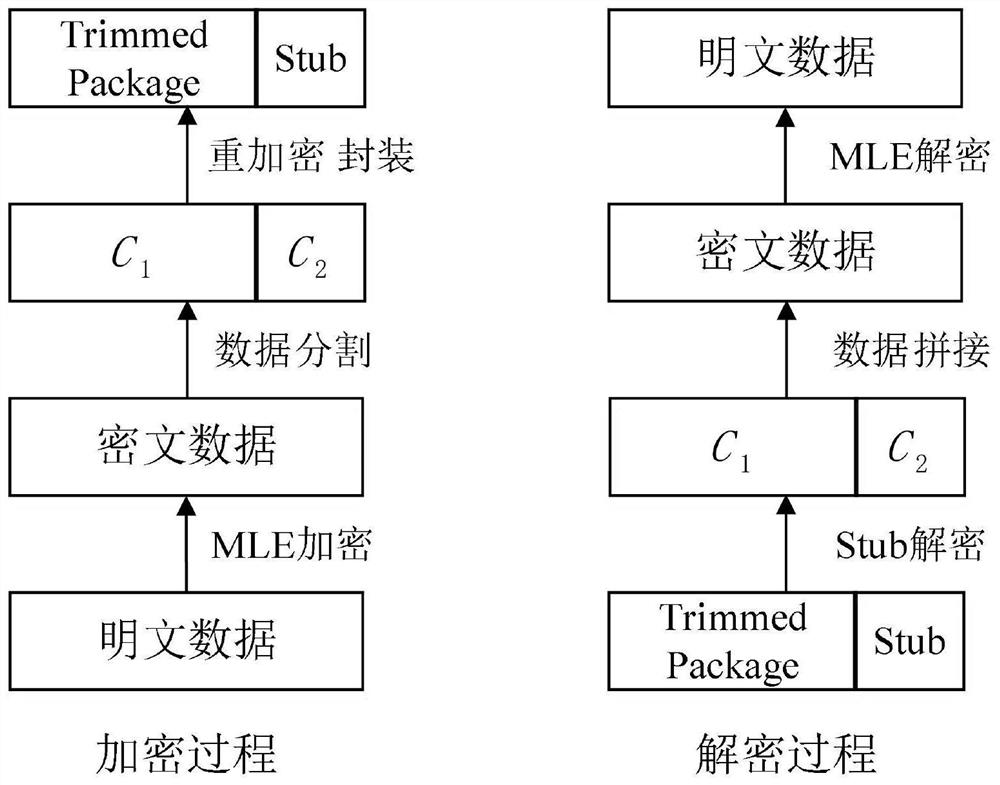
[0073] The data deduplication of the present invention is aimed at a large amount of data stored in the server, and some data are completely the same, and the data deduplication is to delete these same data, and only keep a data backup. From the fine-grained distinction of deduplication execution, data security deduplication can be divided into two types: file level (File Level) deduplication and block level (BlockLevel) deduplication: file level deduplication means that a file is the smallest unit of deduplication , that is, the server performs deduplication detection based on the file label, and only keeps a unique copy o...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com