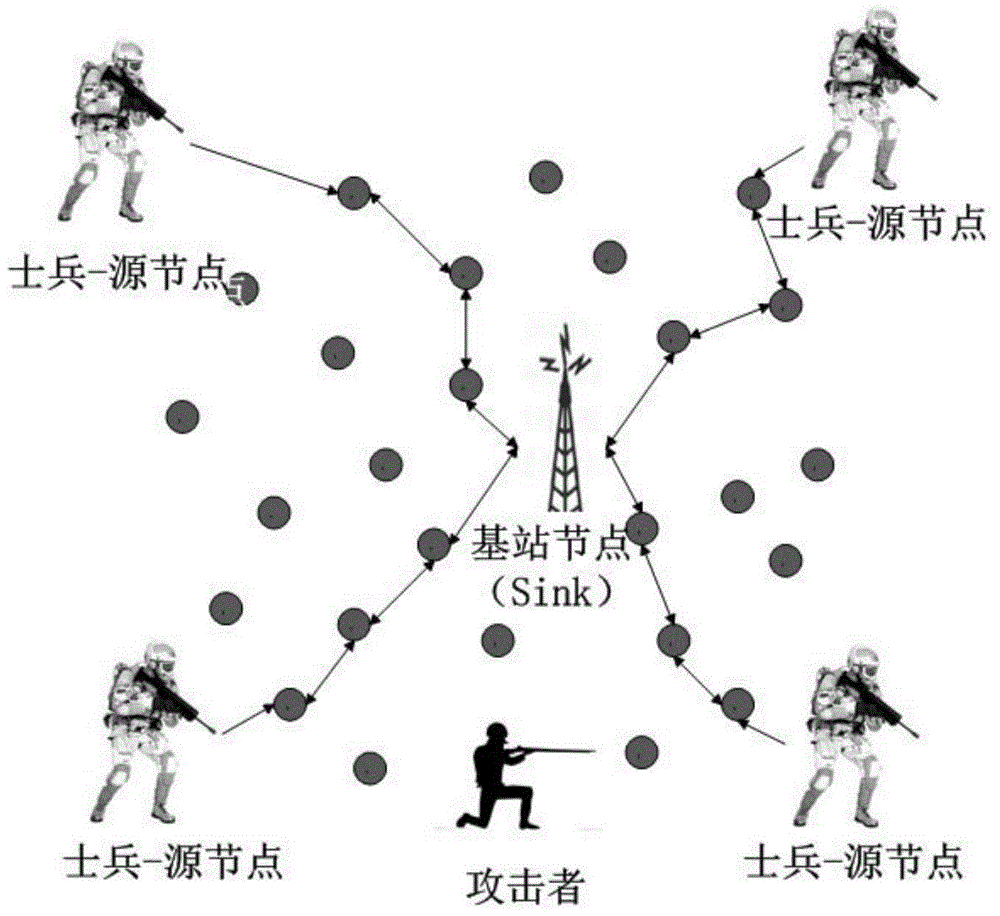
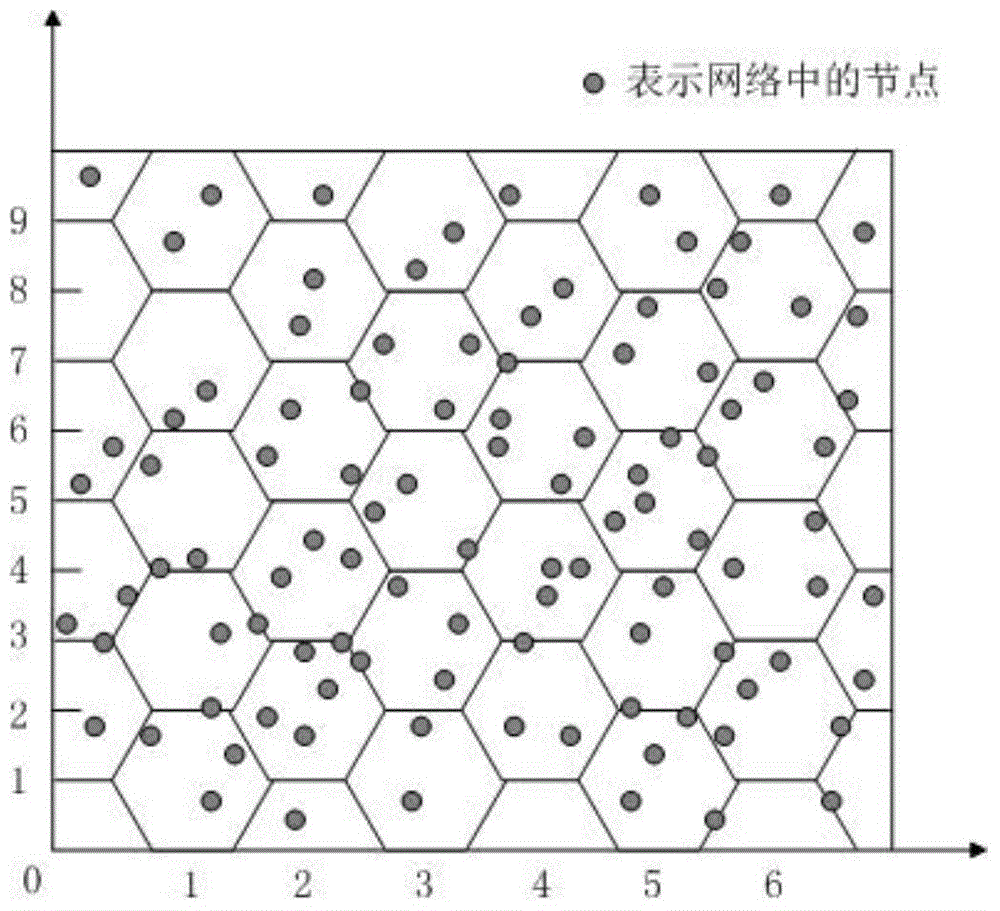
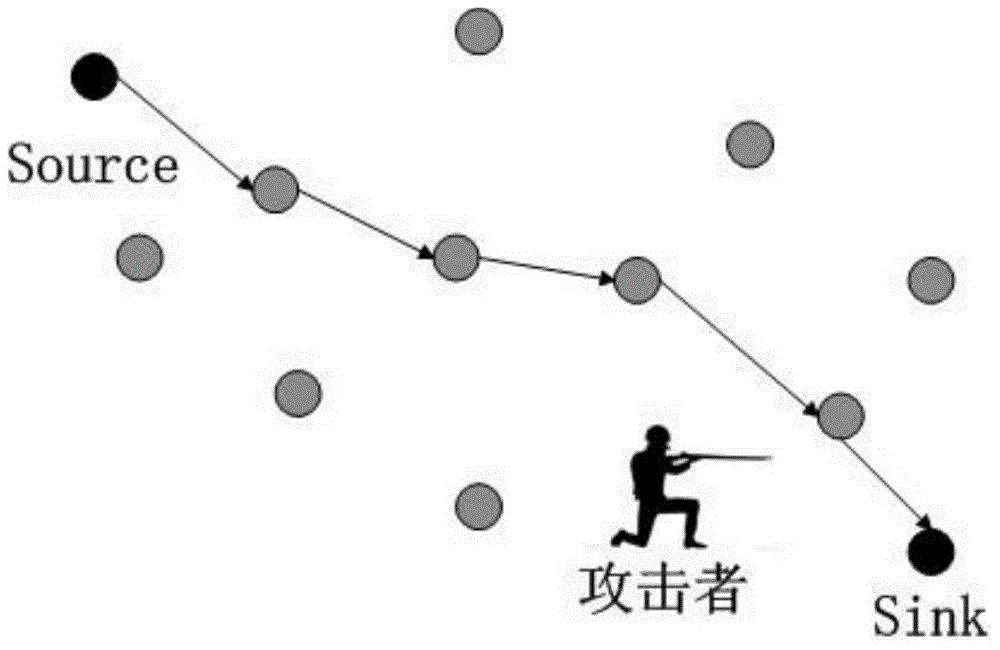
Privacy protection method of soldier information in field battle environment
A privacy-preserving, soldier's technology for wireless communications, advanced technologies, climate sustainability, etc., capable of solving internal attacks, external attacks, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0079] Step 1. Key initialization phase
[0080] Due to the limited energy of sensor nodes and small communication coverage, nodes usually only communicate directly with neighbor nodes. First, the entire wireless sensor network coverage area is divided into smaller areas, and the key pool is also divided into subsets corresponding to the area. The sensor nodes select keys from the corresponding key subsets, and then deploy them according to the divided areas. This increases the probability of shared keys among nodes in the same area. The nodes between adjacent areas achieve a certain sharing probability through the overlap of key subsets (the sharing probability will be set according to the specific military scenario).
[0081] After the entire wireless sensor network is divided into multiple areas, the sensor nodes in each area have different area identifiers, and can associate the information obtained by themselves with the geographic location of the area. When the base st...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com