Continuous identity authentication method based on touch screen slip behavior characteristics
An authentication method and touch-screen technology, applied in the direction of digital data authentication, input/output process of data processing, instruments, etc., can solve the problems of observation attack and guess attack, theft, loss of resistance of touch screen equipment, etc. Robustness and fault tolerance, the effect of ensuring stability
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
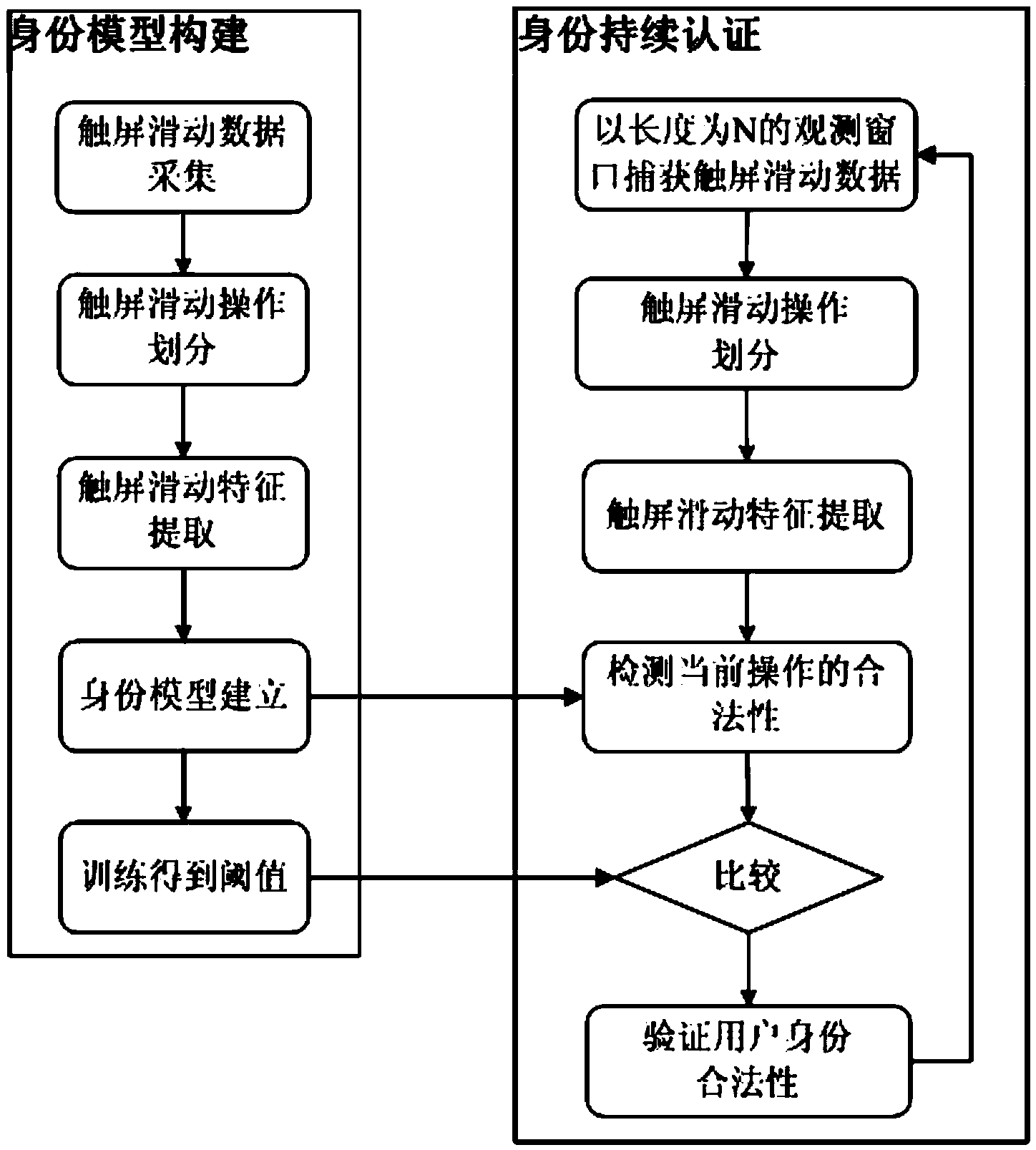
[0044] see figure 1 According to the present invention, the identity authentication method based on the sliding behavior characteristics of the touch screen can be used for real-time monitoring of the legality of the identity of the operator of the touch screen device, and realizes the security protection of the sensitive information stored inside the touch screen device. The present invention includes two parts: user identity model construction and operator identity continuous authentication. The specific implementation steps are as follows:
[0045] 1. The user identity model construction part includes the following steps:
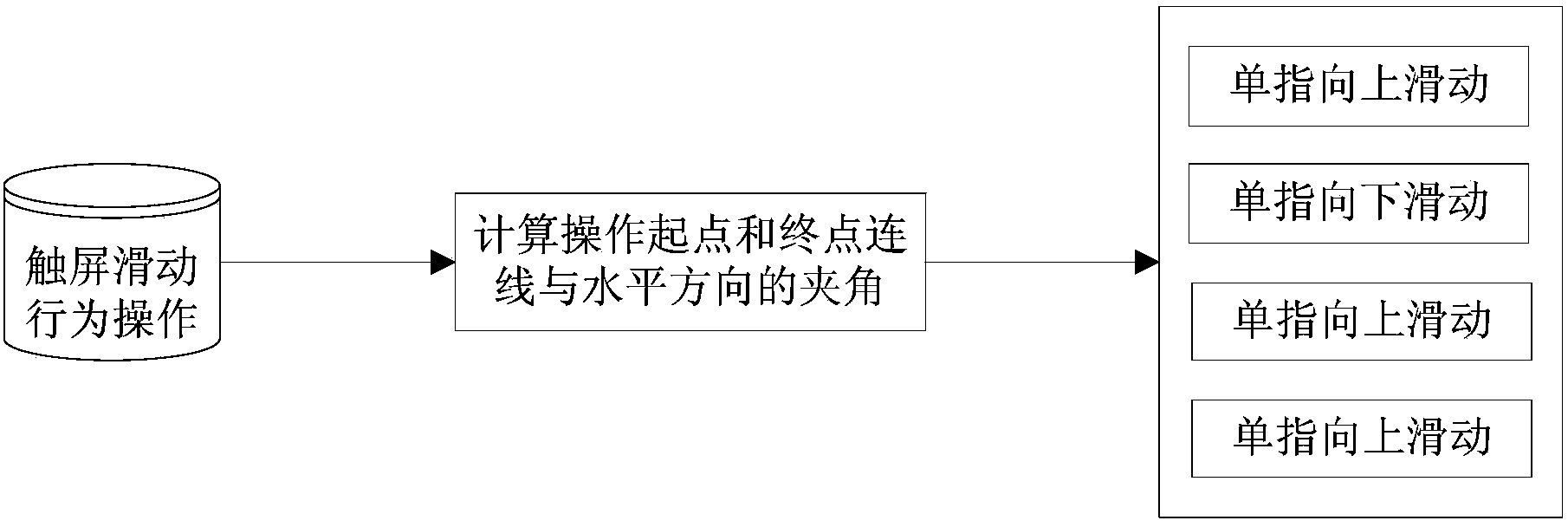
[0046] (1) During the normal use of the touch-screen smart device by the user, collect and record the user's touch-screen sliding operation data to form the touch-screen sliding behavior training data set required for identity model construction; the format of the touch-screen sliding operation data is: {time, touch screen position, finger pressure, fin...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com