Document safe browsing method
A document and security technology, applied in computer security devices, instruments, electrical digital data processing, etc., to achieve the effect of preventing copying and spreading, and preventing re-save
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0022] The present invention will be described in further detail below in conjunction with the accompanying drawings.
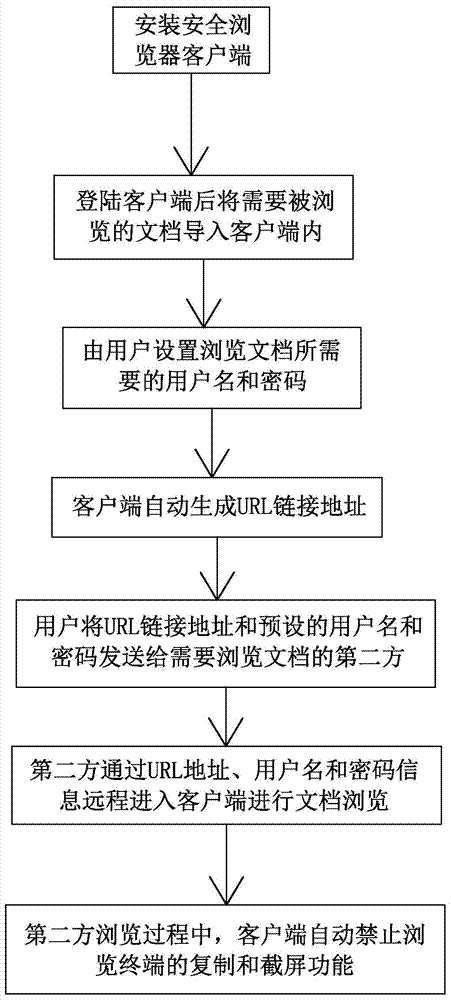
[0023] combined with figure 1 , a document safe browsing method, it comprises the following steps:
[0024] 1. Install the Safe Browsing client;
[0025] 2. After logging in to the client, import the documents to be browsed into the client;
[0026] 3. The user name and password required to browse the document are set by the user;
[0027] 4. The client automatically generates the URL link address;
[0028] 5. The user sends the URL link address and the preset user name and password to the second party who needs to browse the document;
[0029] 6. The second party remotely enters the client through the URL address, user name and password information to browse documents;
[0030] 7. During the second-party browsing process, the client automatically prohibits the copying and screenshot functions of the browsing terminal.
[0031] Preferably, the browsed d...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com