System security permission treatment state machine model based on intelligent terminal
A technology for system security and processing status, which is applied in the fields of electrical digital data processing, computer security devices, instruments, etc., and can solve the security risks of users' intelligent terminals
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0020] The present invention will be further elaborated below by describing a preferred specific embodiment in detail in conjunction with the accompanying drawings.
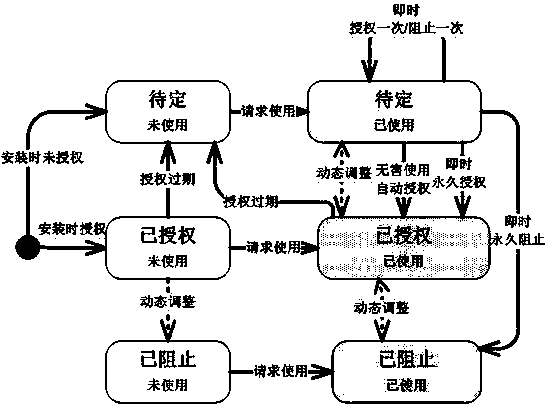
[0021] A state machine model for system security authority processing based on an intelligent terminal, which is set on an operating system platform of a mobile terminal. The operating system includes an authority use interception module and an authority request decision-making module, wherein the authority request decision-making module controls the application authority Permission classification is carried out, and the permission categories include: authorized permission, pending permission and blocked permission; the permission usage interception module monitors the category of permissions, and dynamically adjusts between permission categories through the permission request decision module.
[0022] A permission can be adjusted from a blocked or pending permission to an authorized permission if and only if the ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com