A Java Card Realization Method Supporting Data Signature
A data signature and data information technology, applied in the field of information security, can solve the problems of restricting java card identification applications, java cards cannot support national secret algorithms, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
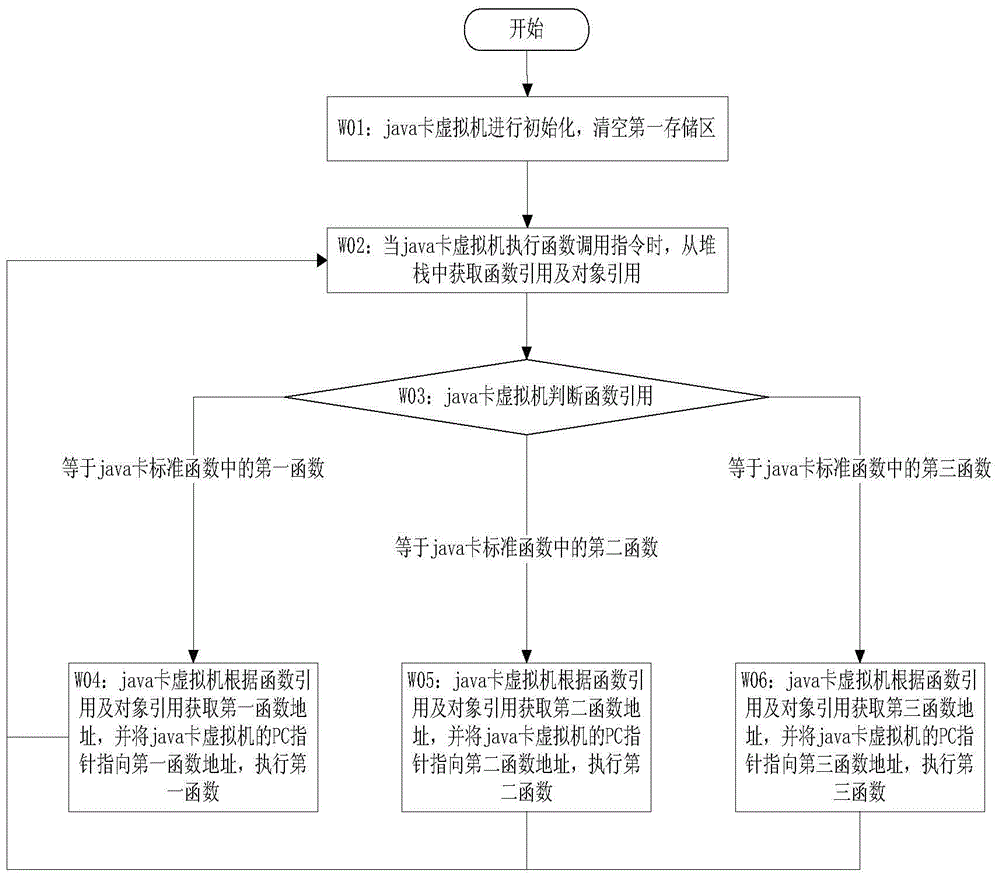
[0069] The present invention provides a java card implementation method supporting data signature, such as figure 1 shown, including:
[0070] Step W01: the java card virtual machine is initialized, and the first storage area is cleared;
[0071] Step W02: when the java card virtual machine executes the function call instruction, obtain the function reference and the object reference from the stack;
[0072] Step W03: the java card virtual machine judges the function reference, if the function reference is equal to the first function in the java card standard functions, then perform step W04; if the function reference is equal to the second function in the java card standard functions, then perform step W05; if If the function reference is equal to the third function in the java card standard function, then step W06 is performed;
[0073] Step W04: The java card virtual machine obtains the first function address according to the function reference and the object reference, a...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com