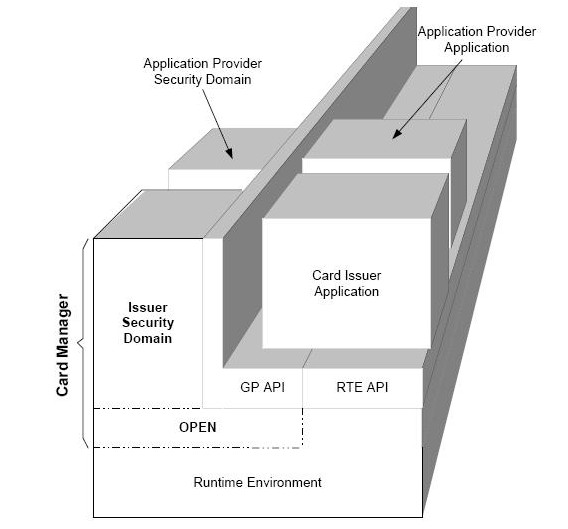
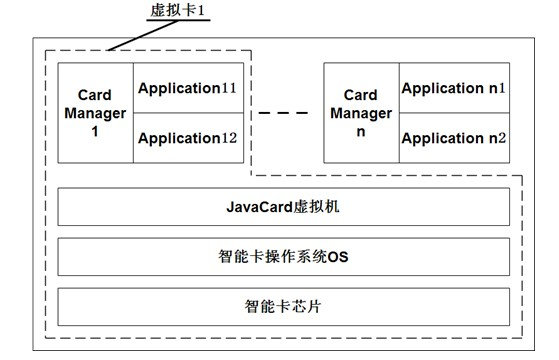
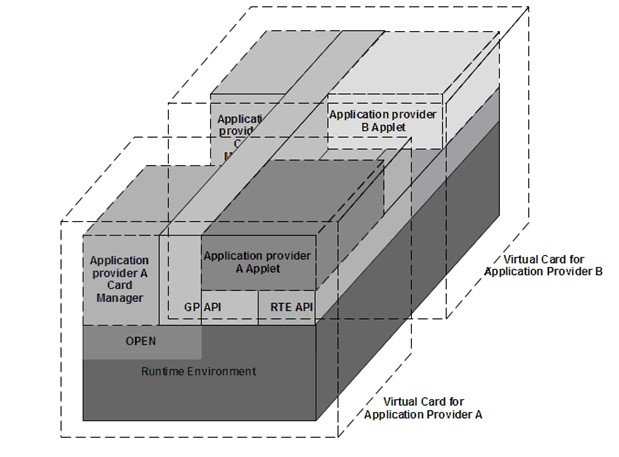
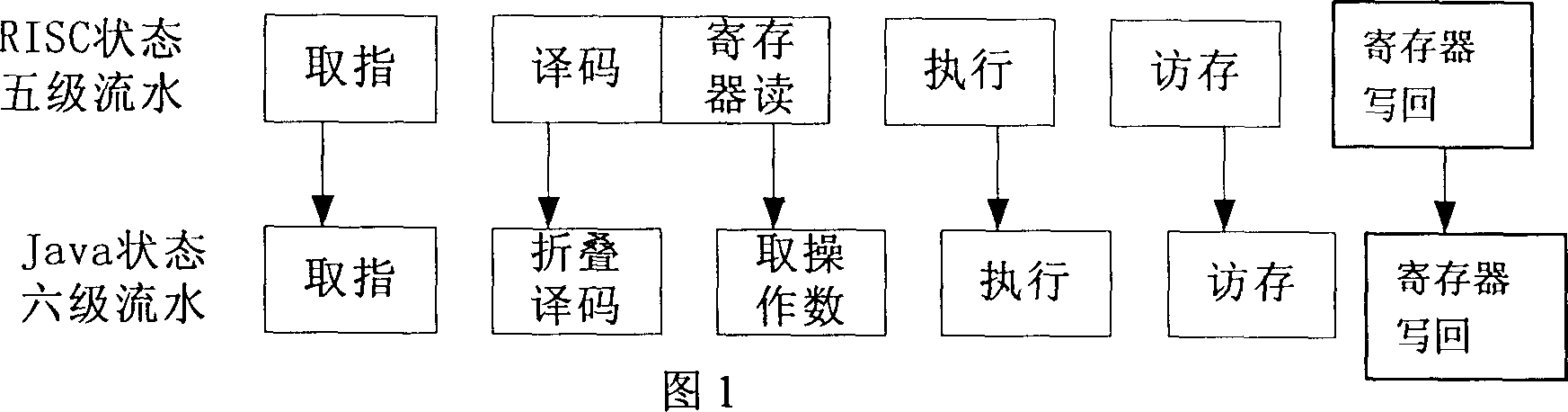
Patents
Literature
37 results about "Java card virtual machine" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
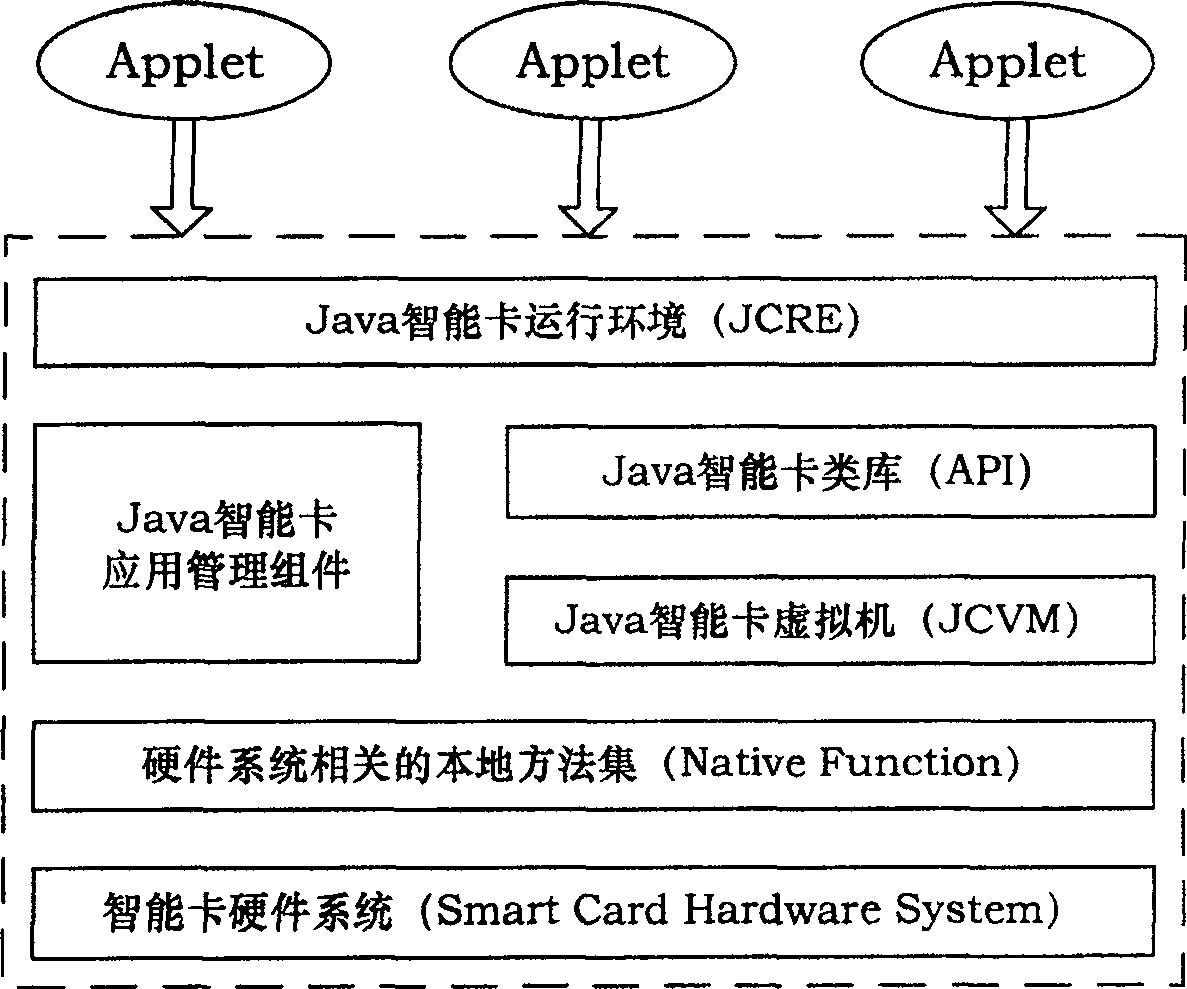
Java Card bytecode run by the Java Card Virtual Machine is a functional subset of Java 2 bytecode run by a standard Java Virtual Machine but with a different encoding to optimize for size. A Java Card applet thus typically uses less bytecode than the hypothetical Java applet obtained by compiling the same Java source code.
Multi-application Java smart card
ActiveCN102087716AMeet the requirements of the issuing partiesRecord carriers used with machinesSoftware simulation/interpretation/emulationProgrammable read-only memoryOperational system
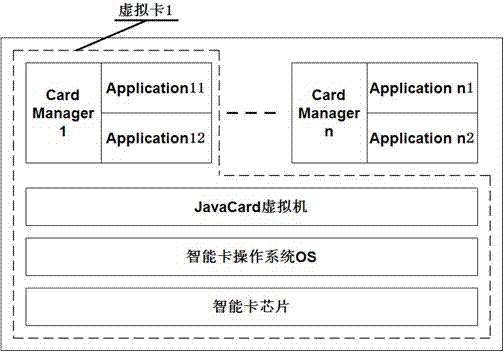
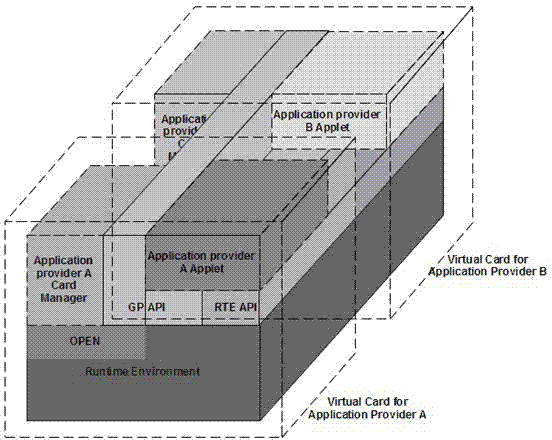
The invention discloses a multi-application Java smart card which comprises a Java Card virtual machine, a smart card operating system and a smart card chip. The multi-application Java smart card is characterized by further comprising a plurality of virtual cards mutually independent; each virtual card is corresponding to one application provider for providing application; each virtual card comprises a Card Manager for independently controlling the resource of the corresponding virtual card to provide the safety verification service of a terminal access corresponding to the virtual card; and each virtual card correspondingly manages the respective Electrically Erasable Programmable Read-Only Memory (EEPROM) for the content management of the virtual card. The smart card can realize that the issuer and the application provider of the smart card coexist on one physical card mutually and independently and have mutually equal status, thereby satisfying the requirement of each issuing partyof co-branded cards.
Owner:WUHAN TIANYU INFORMATION IND
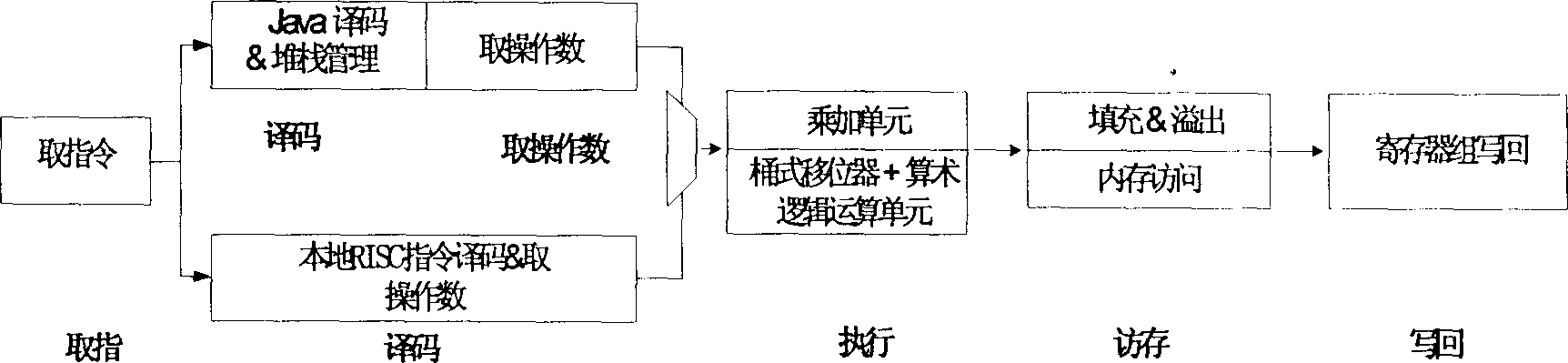
32-bit embedded microprocessor adopting double instruction set
InactiveCN1450450AImprove efficiencyResolve streaming conflictsConcurrent instruction executionProcessor registerJava card virtual machine
Owner:FUDAN UNIV
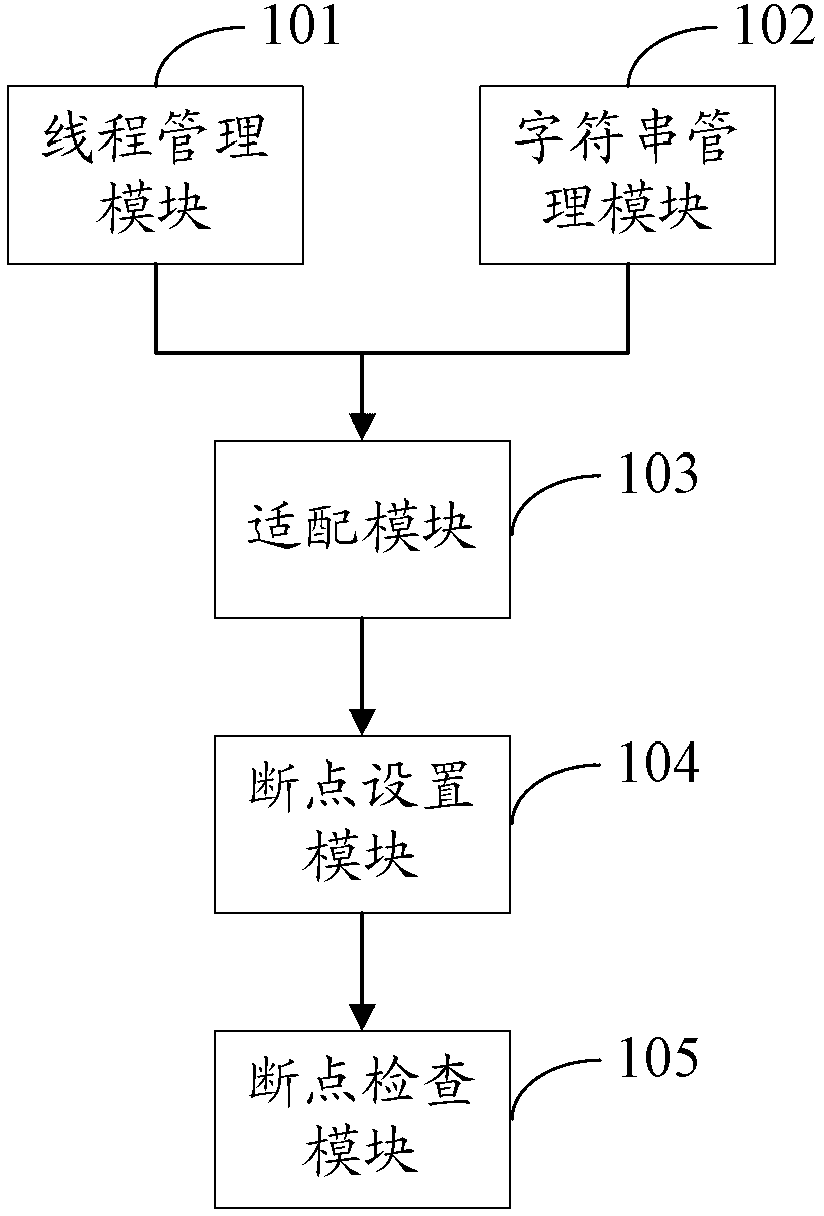
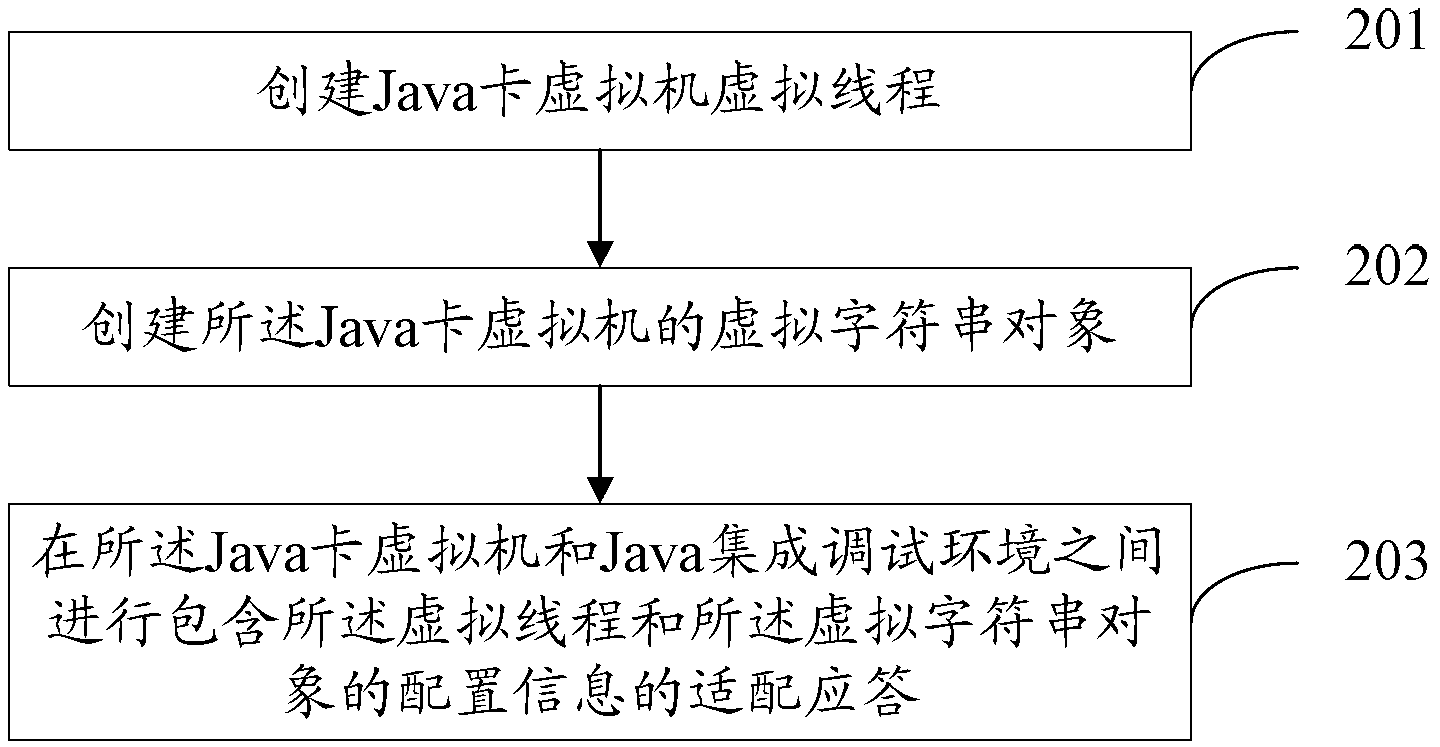
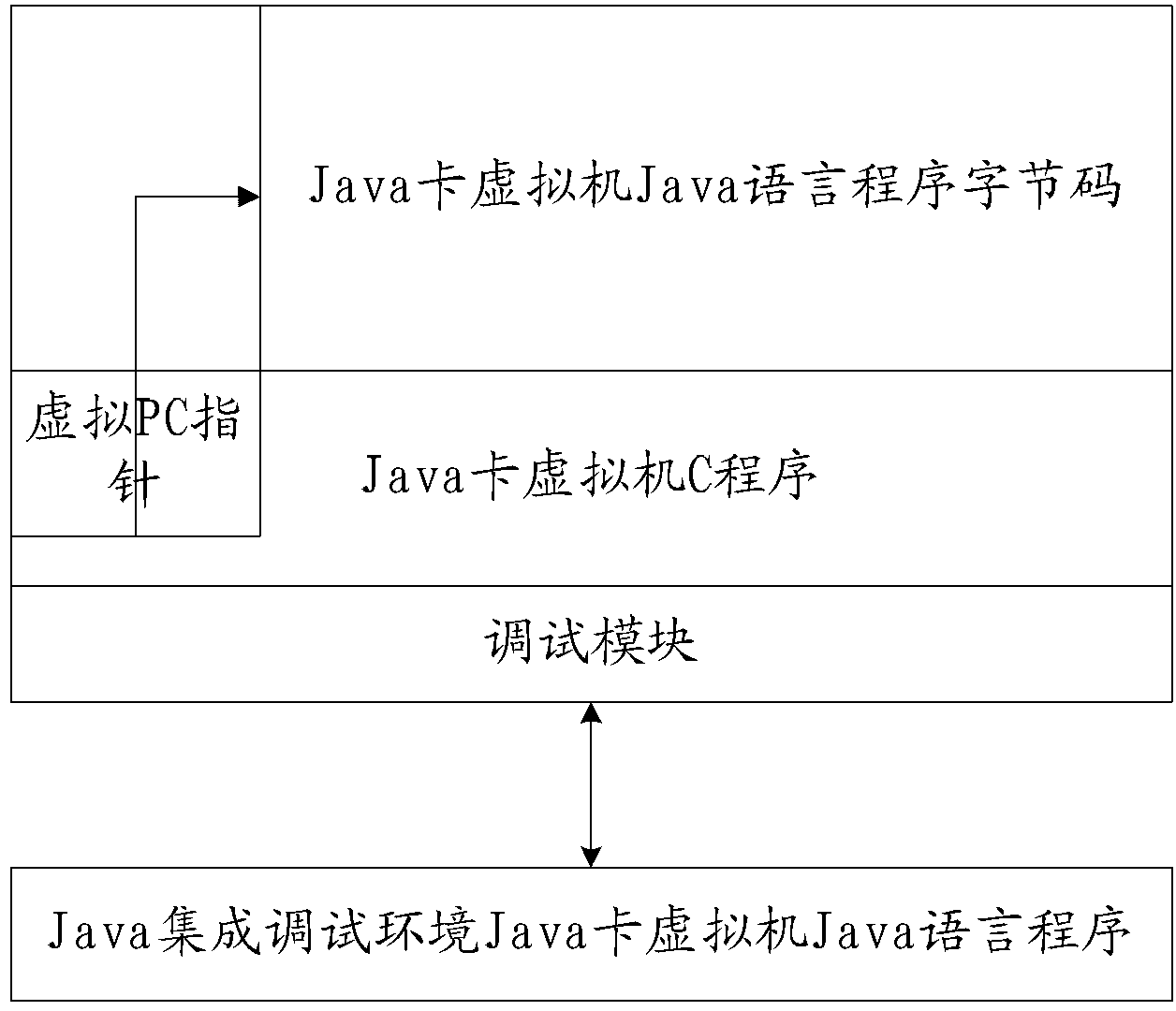
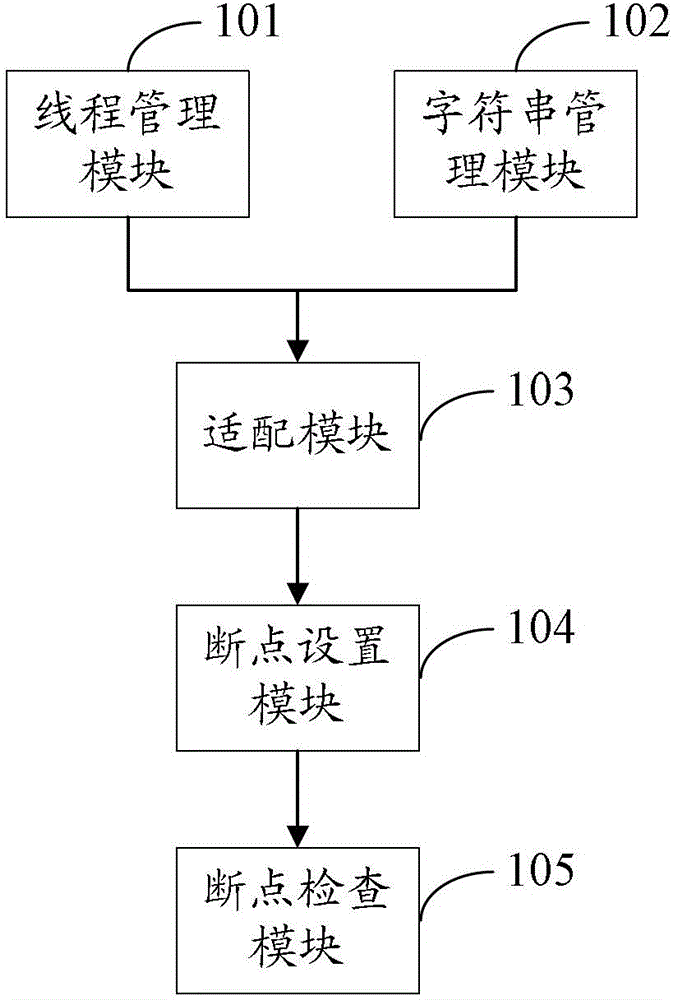
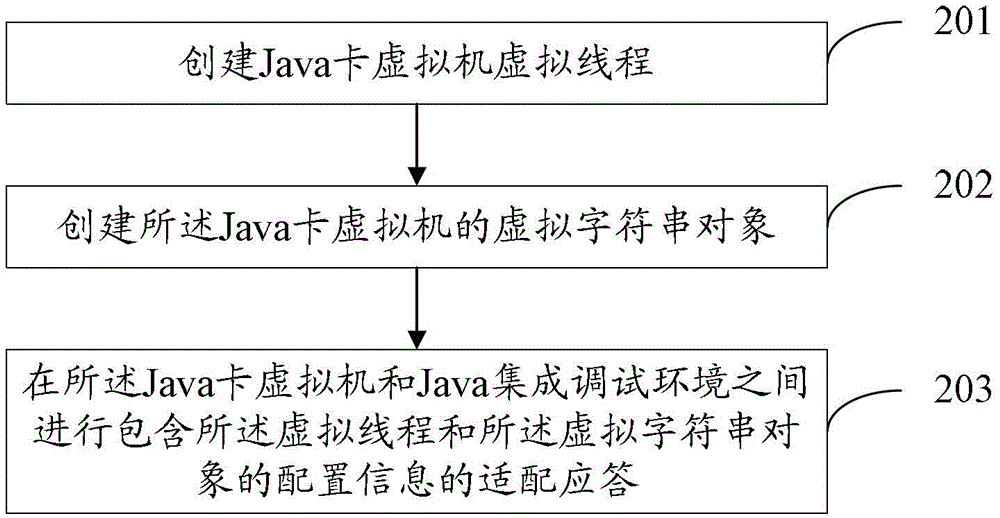
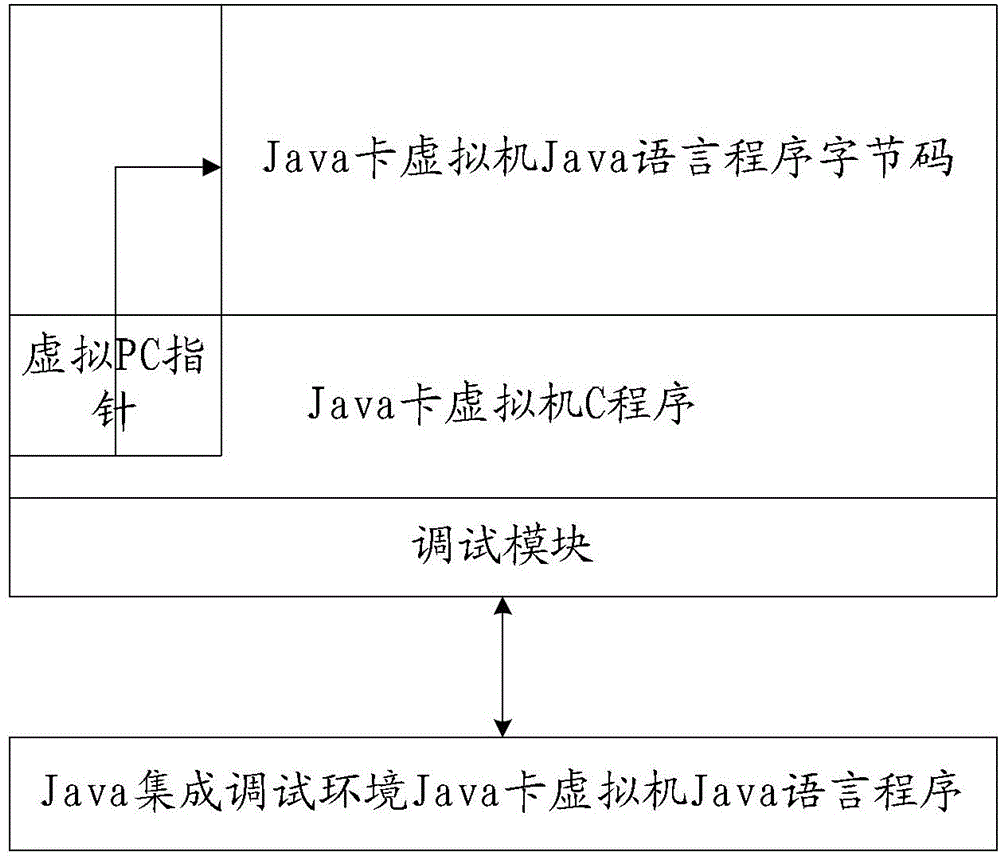
Program debugging method and device
ActiveCN103019941ARealize common debuggingSolve the convenienceSoftware testing/debuggingJava card virtual machineHuman language
The invention provides a program debugging method and device, which relates to the field of software engineering. The problem that current debugging method is lower in debugging efficiency and maintenance convenience is solved. The method comprises the steps of: establishing a virtual thread of a Java card virtual machine; establishing a virtual character string object of the Java card virtual machine; and carrying out adaptive response of configuration information comprising the virtual character thread and the virtual character string object between the Java card virtual machine and a Java integrated debugging environment. The technical scheme provided by the invention is adaptive to synchronous debugging of Java language and C language, so that jointed debugging of virtual machine programs compiled by Java and C languages is realized.
Owner:DATANG MICROELECTRONICS TECH CO LTD
Page operation-based electrically erasable programmable read-only memory (EEPROM) cache method
ActiveCN102073544ARun fastExtended service lifeMultiprogramming arrangementsProgrammable read-only memoryJava card virtual machine
The invention discloses an electrically erasable programmable read-only memory (EEPROM) cache method for enhancing the performance of a Java card virtual machine. The contradiction of low performance caused by multi-application of a Java card and frequent writing of EEPROM is overcome. A full-page transaction mechanism is adopted, a process for writing EEPROM repeatedly in a transaction flow is combined into one or more large transactions, and one-step submission to EEPROM is performed in a page, so that transaction operation of the conventional small unit is substituted. By the method, using cost of the EEPROM is saved, and practical performance of the Java card is enhanced.
Owner:WUHAN TIANYU INFORMATION IND
Method for improving execution efficiency of static field access command
InactiveCN102103489AImprove runtime performanceImprove execution efficiencyProgram controlMemory systemsPhysical addressStatic field
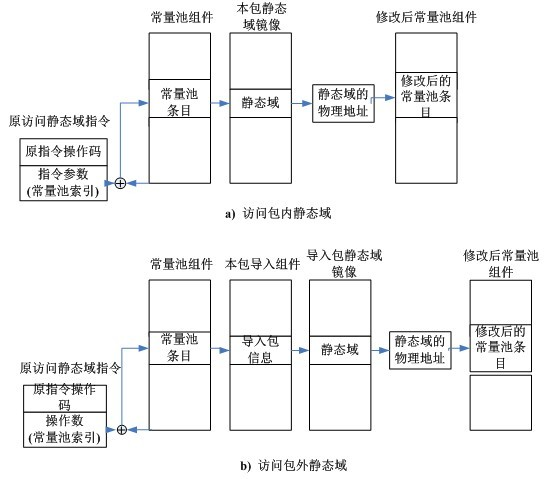
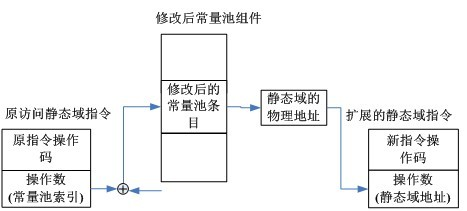
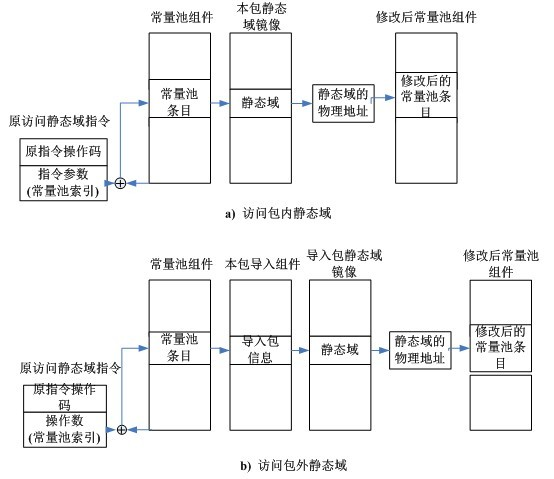
The invention discloses a method for improving the execution efficiency of a static field access command during running of a Java card virtual machine. The method comprises the following steps of: (1) completing resolving of the physical address of a static field during downloading of a CAP (computer-aided production) file, namely replacing contents of a corresponding entry of the static field in a constant pool with a physical address of the static field during downloading of a constant pool component of the CAP file; (2) during resolving of an quotation position, storing the physical address of the static field in the command; and (3) during running of the Java card virtual machine, directly acquiring the physical address of the static field by using the static field access command. By adopting the method, the physical address of the static field can be directly accessed during running of the Java card virtual machine, the execution efficiency of the static field access command is improved, and the running speed of the Java card virtual machine is increased.
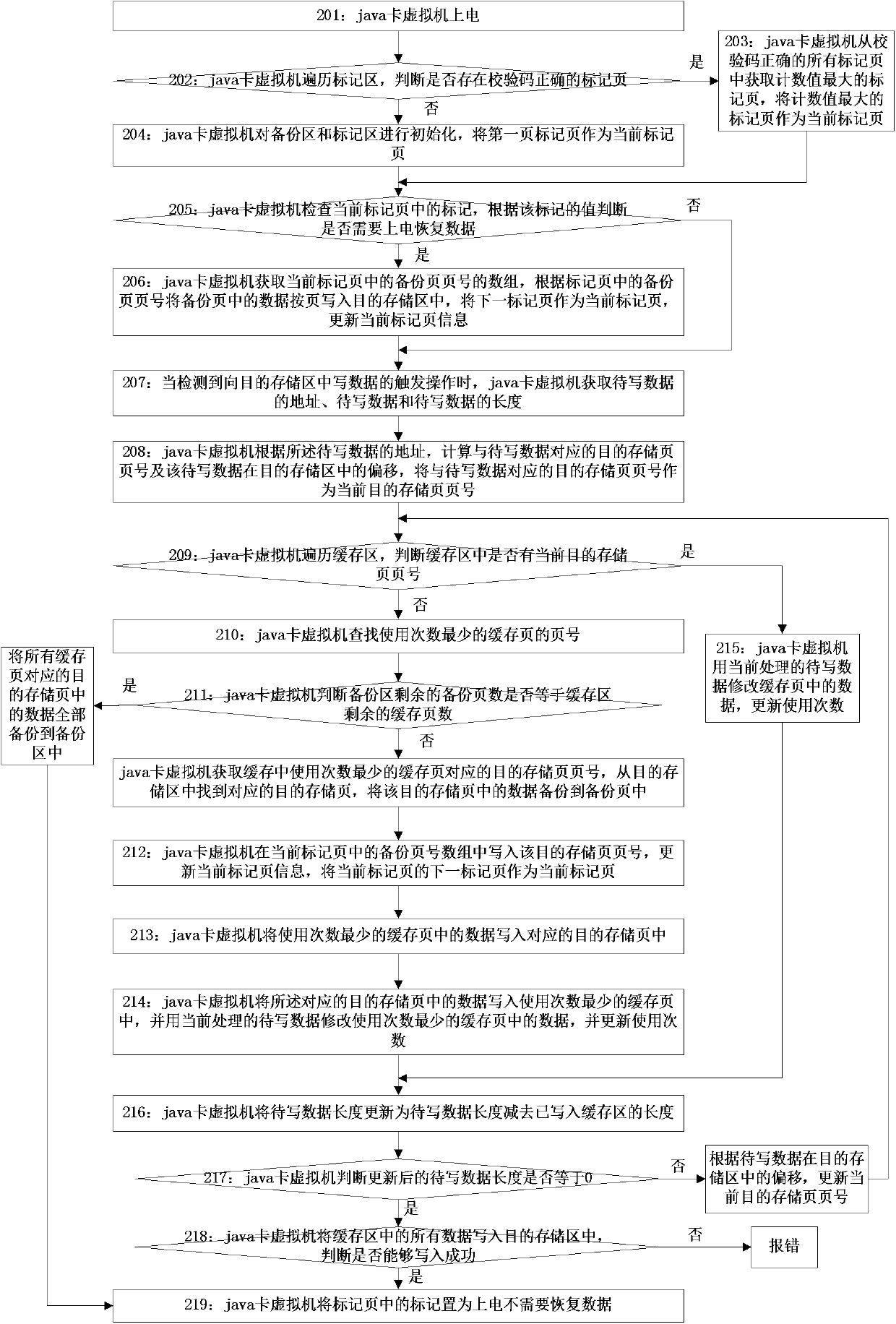
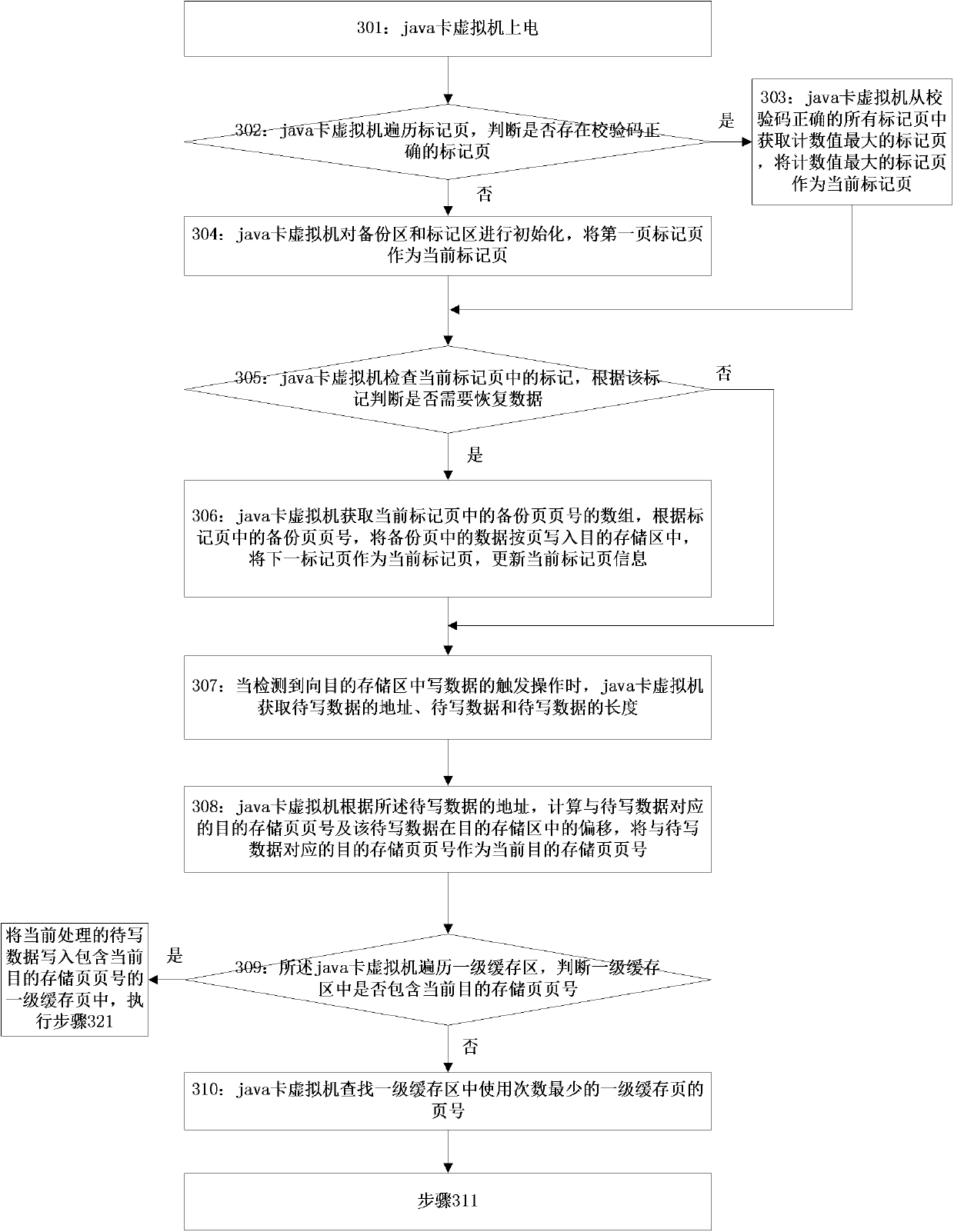
Cache-based java card transaction processing method
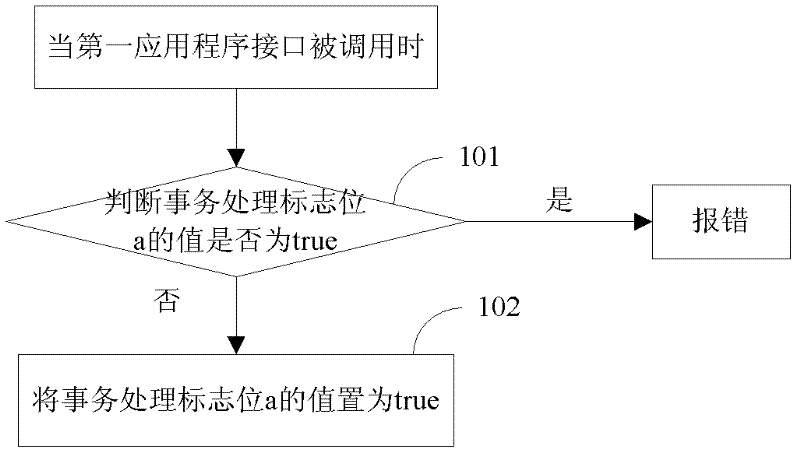
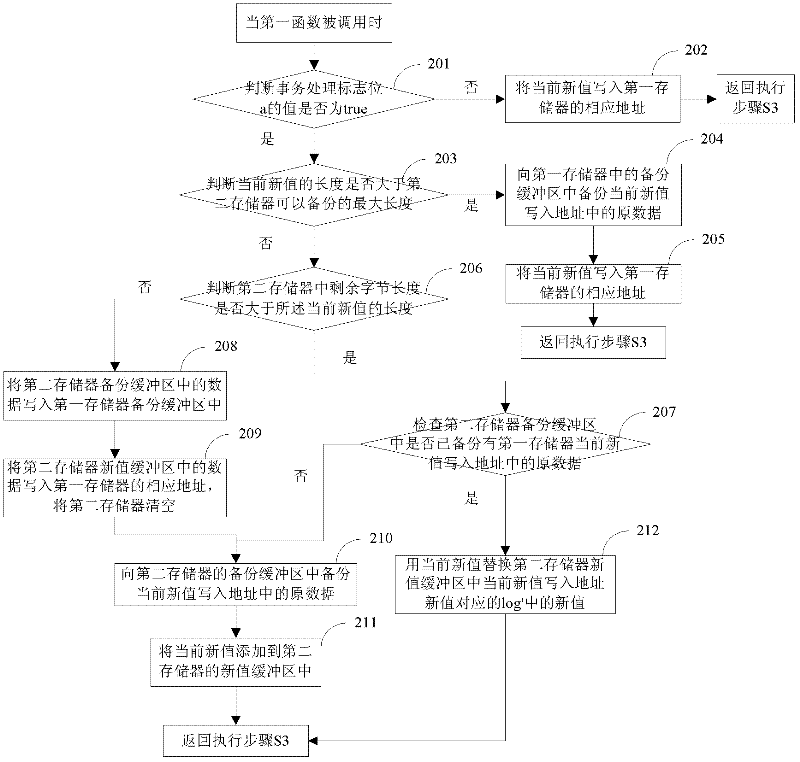
ActiveCN102495754AReduce stepsKeep power-down protection functionMultiprogramming arrangementsRedundant operation error correctionApplication programming interfaceApplication software
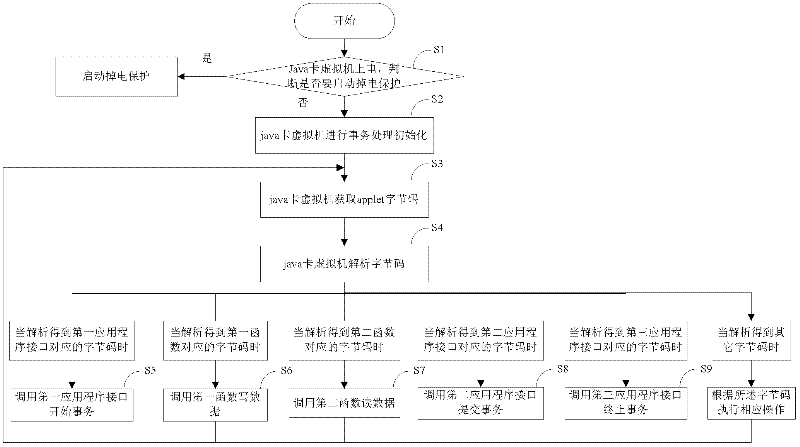
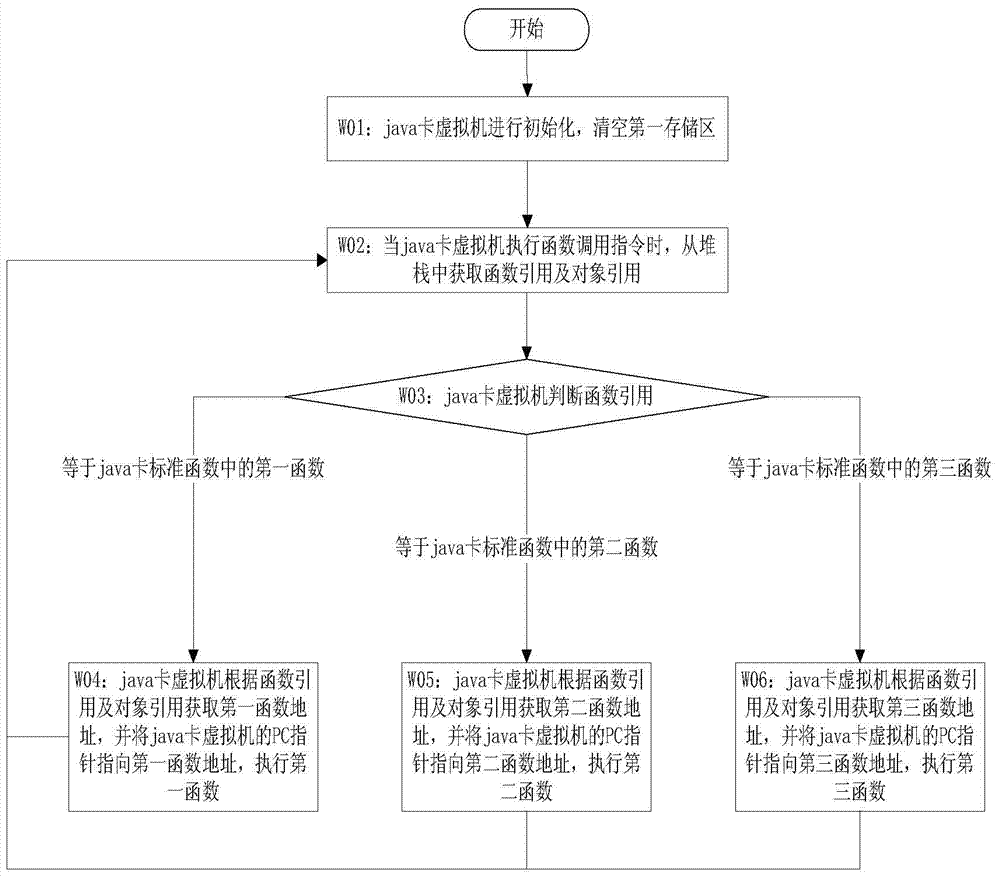
The invention discloses a cache-based java card transaction processing method and belongs to the field of information safety. The method comprises the following steps of: 1, energizing a java card virtual machine, judging whether a power-failure protection function is required to be started, if so, starting the power-failure protection function and directly executing the step 3, otherwise, executing the step 2; 2, performing transaction processing initialization; 3, acquiring an applet byte code; and 4, analyzing the applet byte code, if the applet byte code is a byte code which corresponds to a first application program interface, calling the first application program interface and executing the step 3, if the applet byte code is the byte code which corresponds to a first function, calling the first function and executing the step 3, if the applet byte code is the byte code which corresponds to a second function, calling the second function and executing the step 3, if the applet byte code is the byte code which corresponds to a second application program interface, calling the second application program interface and executing the step 3, if the applet byte code is the byte code which corresponds to a third application program interface, calling the third application program interface and executing the step 3, and if the applet byte code is other byte codes, executing corresponding operation according to the byte code and executing the step 3.
Owner:FEITIAN TECHNOLOGIES
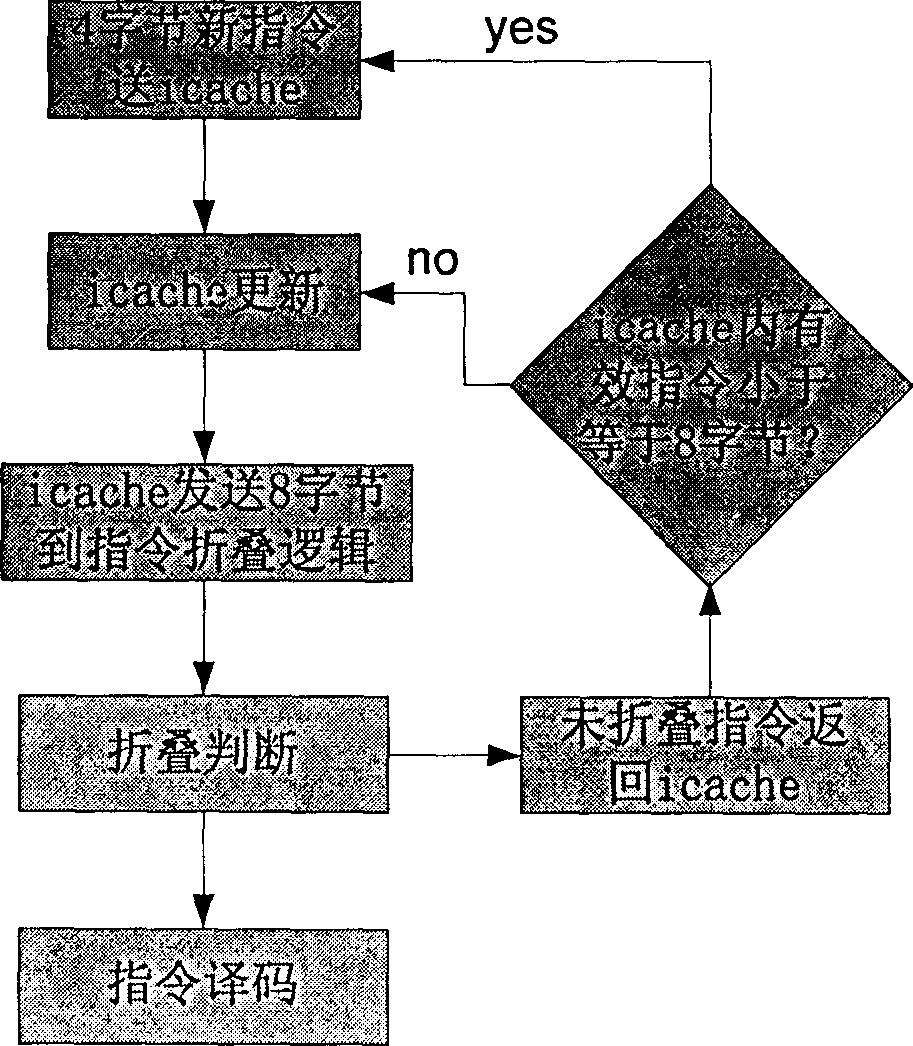
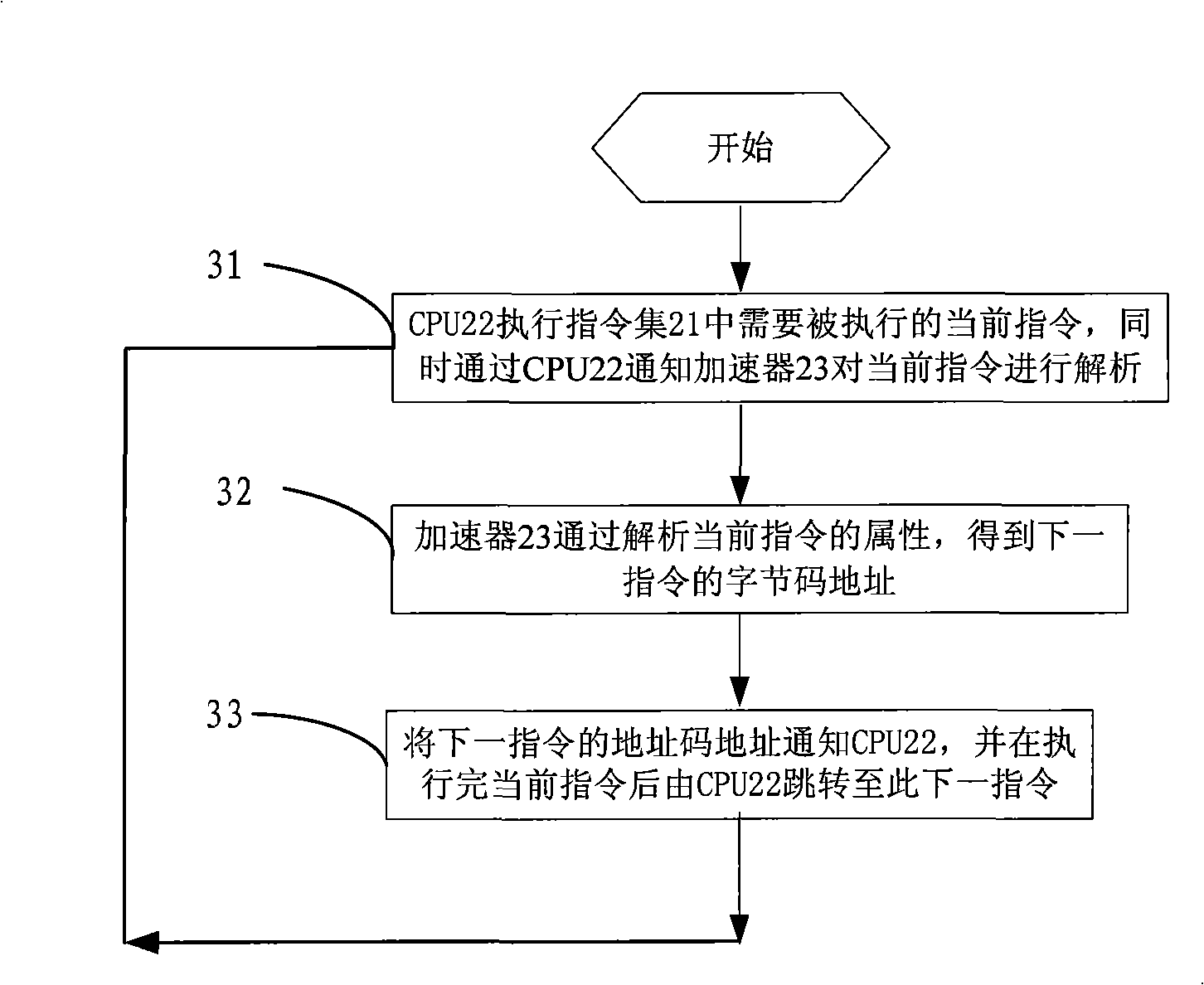
Instruction execution method of Java card virtual machine
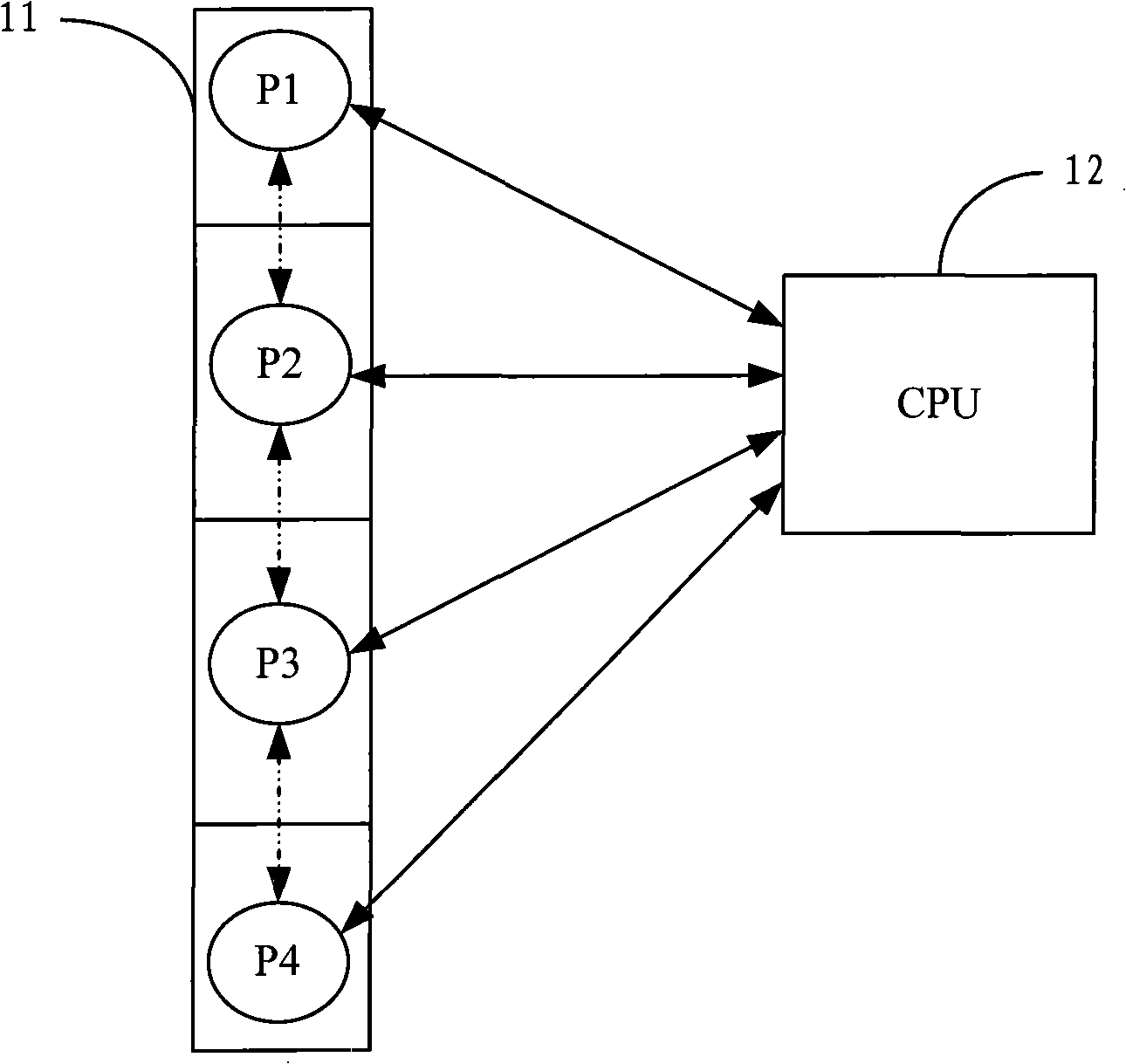
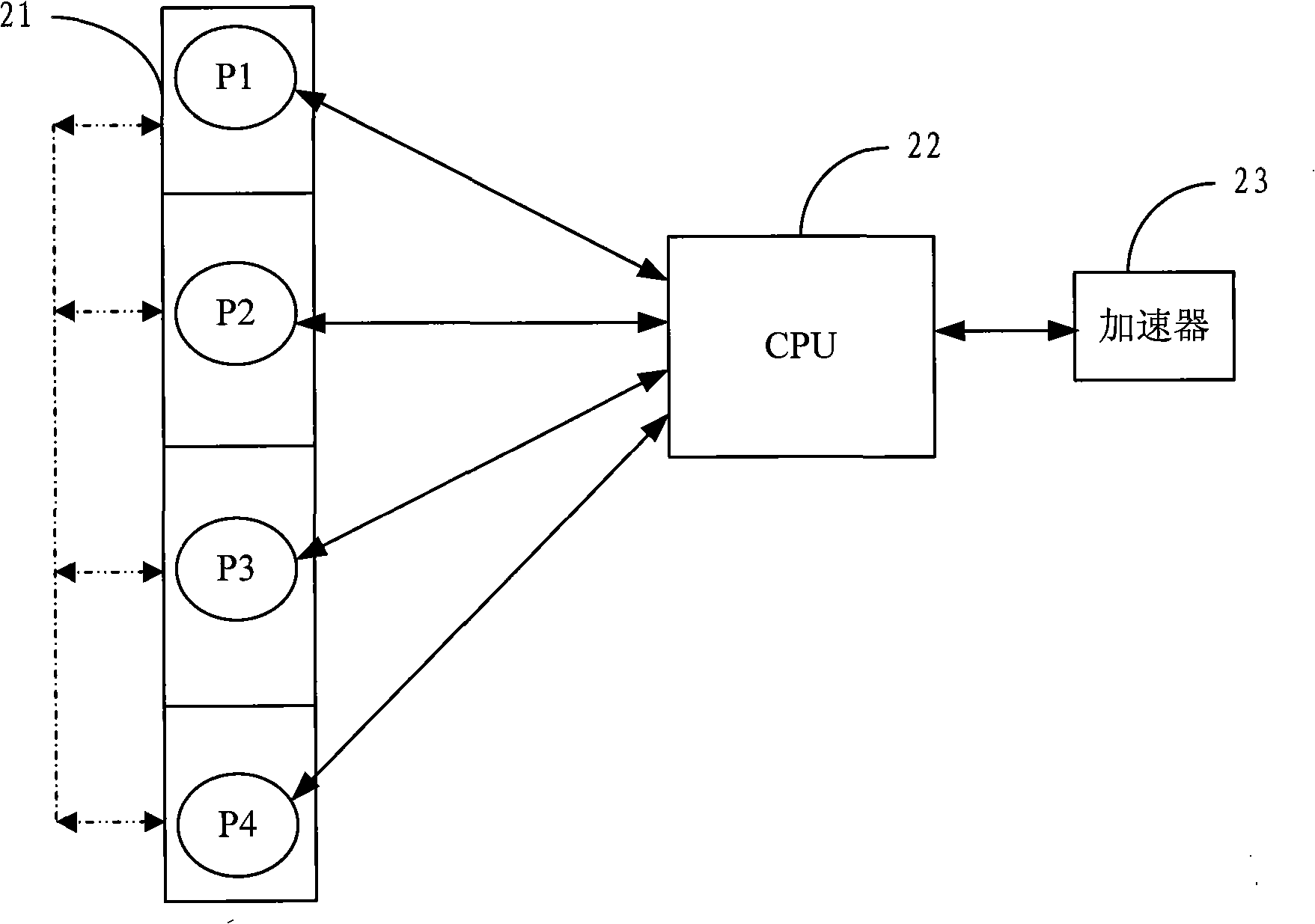
InactiveCN101295239AImprove stabilityAvoid wasting timeMachine execution arrangementsJava card virtual machineInstruction set
The invention relates to an instruction execution method for a Java card virtual machine, comprising the steps as follows: step one, a processor executes the current instruction which is required to be executed in an instruction set; meanwhile, an accelerator is informed by the processor to analyse the current instruction; step 2, the accelerator analyses the property of the current instruction and obtains the byte code address of the next instruction; steps 3, the processor is informed of the byte code address of the next instruction and jumps to the next instruction after completing the execution of the current instruction. The instruction execution method for the Java virtual machine provided by the invention carries out the analysis of the current instruction by the accelerator and obtains the byte code address of the next instruction, leads the processor to directly jump to the next instruction required to be executed immediately after completing the execution of the current instruction and has the advantages of high efficiency and high stability.
Owner:EASTCOMPEACE TECH
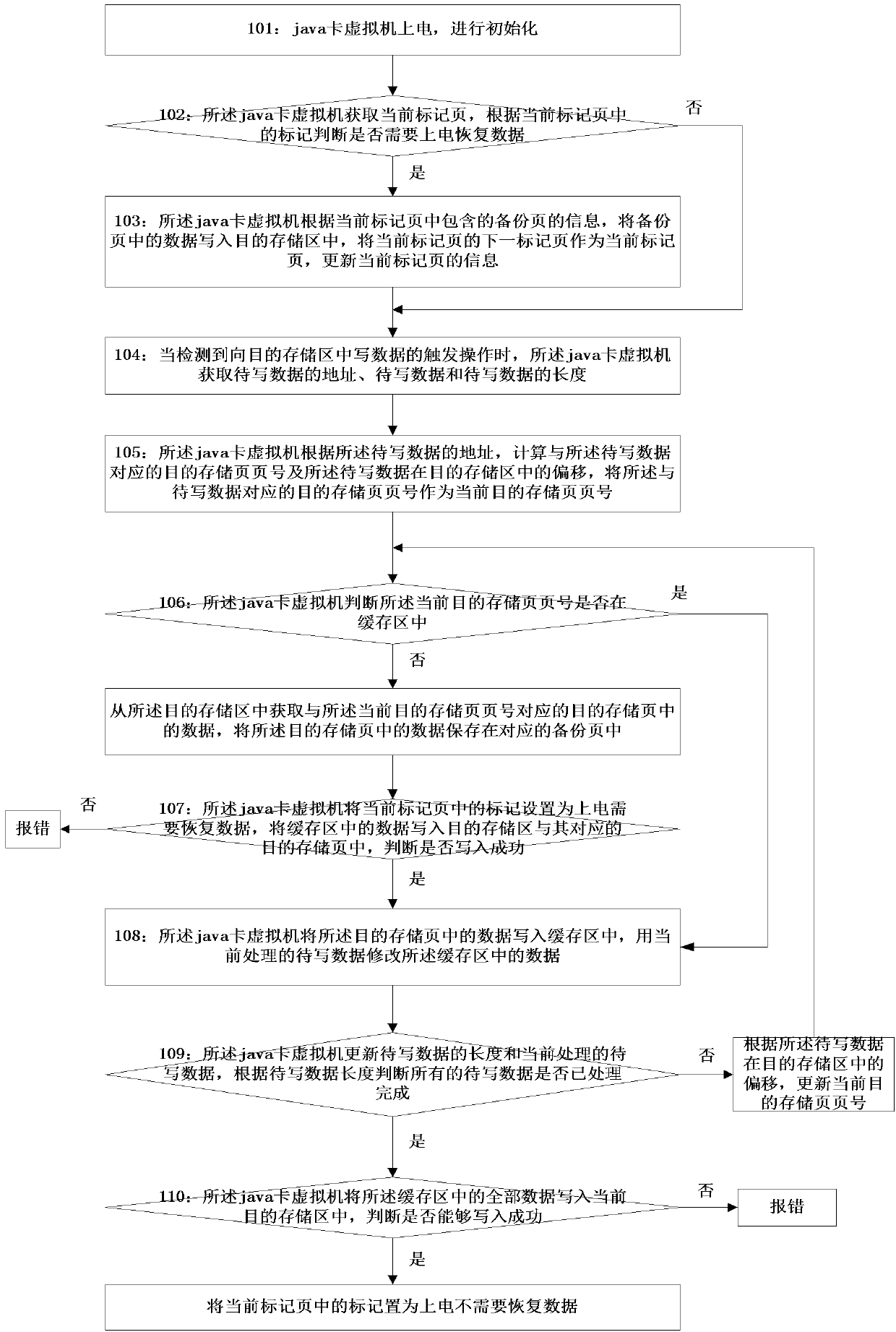
Data protection method for preventing power down
ActiveCN103793337AEnsure safetyMemory loss protectionMemory adressing/allocation/relocationElectricityOriginal data
The invention discloses a data protection method for preventing power down, and belongs to the field of information safety. The method includes A, powering on a java card virtual machine, judging whether power on and data recovery are necessary or not, if so, writing backup page data into a target storing area, and executing B; if not, executing B directly; B, when triggered operation for writing data to the target storing area is detected, acquiring a current target storage page number according to address computing of data to be written; C, judging whether the current target storage page number exists in cache or not, if so, using the data to be written to modify cache data, and executing D; if not, writing target storage page data in a backup page firstly, then writing in the cache, using the data to be written to modify the cache data, and executing D; D, when the data to be written is processed completely, writing the cache data into the target storing area, and data recovery is omitted while powering on. By adopting the technical scheme, when power down occurs in unknown conditions, original storage area data can be recovered and safety of the original data is guaranteed.
Owner:FEITIAN TECHNOLOGIES
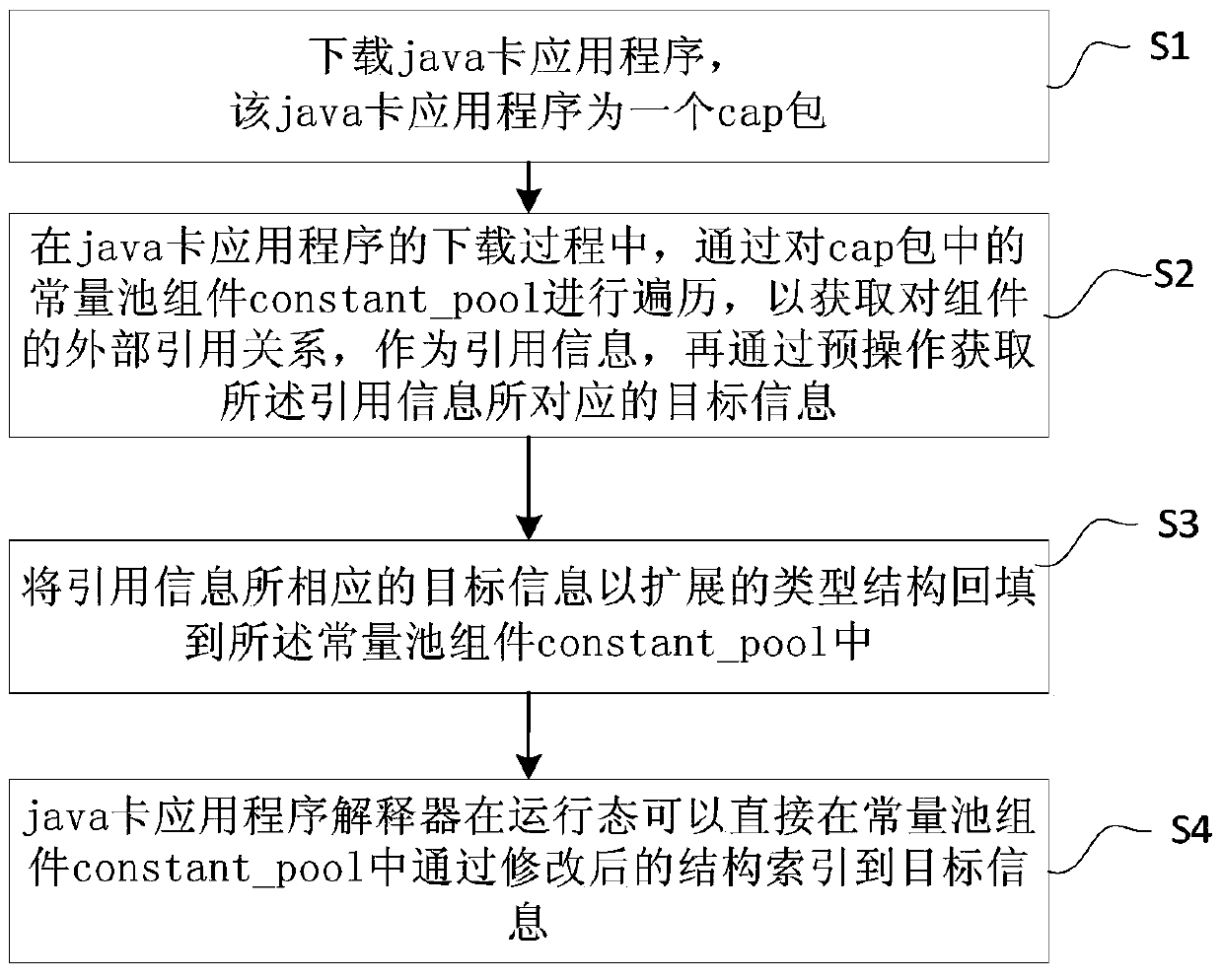
Method and system for optimizing virtual machines of java cards
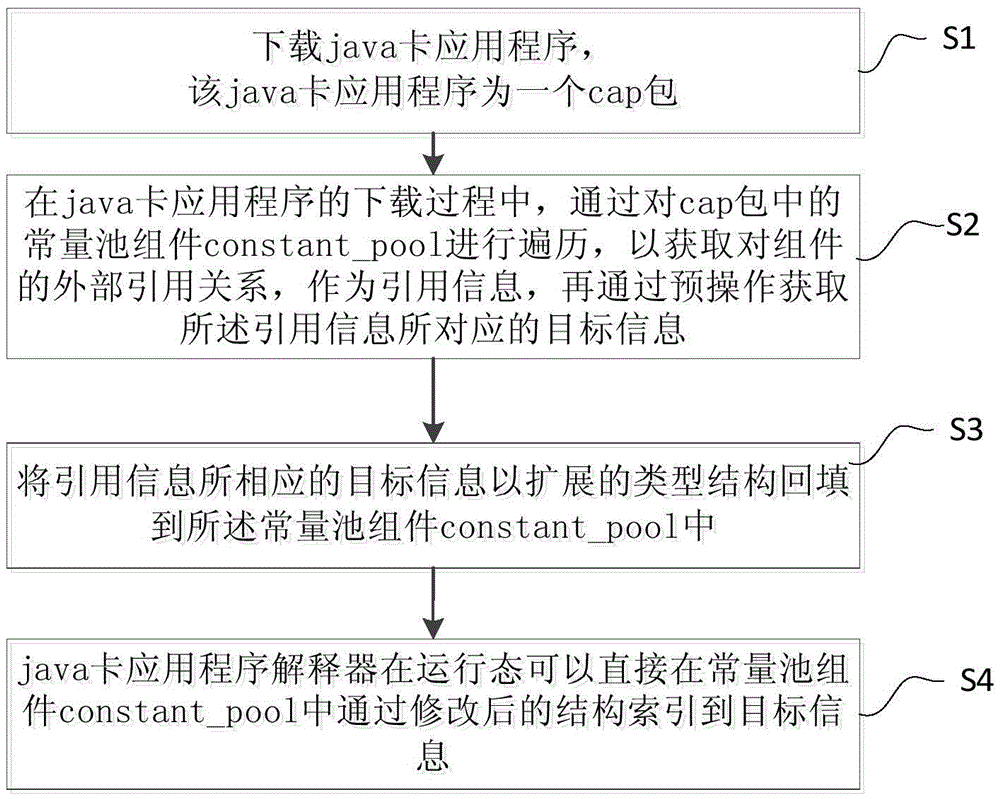
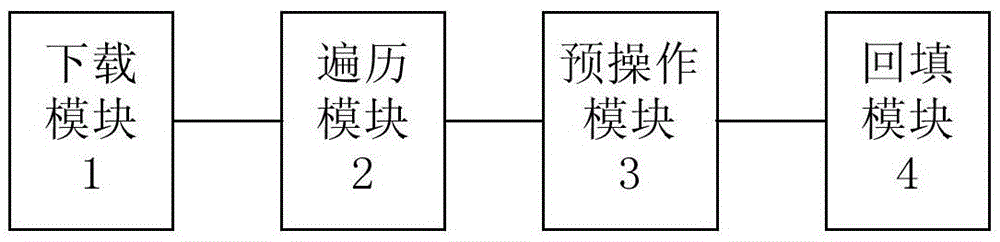
ActiveCN105653351AImprove operational efficiencyOmit internal jumpsSoftware simulation/interpretation/emulationStructure of Management InformationApplication software
The invention discloses a method and system for optimizing virtual machines of java cards. The method comprises the following steps: downloading a java card application program, wherein the java card application program is a cap package, and the cap package comprises components and a constant pool component which is used for indexing the components; in the downloading process of the java card application program, traversing the constant pool component in the cap package and carrying out a pre-operation so as to obtain target information corresponding to quotation information; backfilling the target information corresponding to the quotation information and an extended type structure into the constant pool component; and directly indexing the target information from the constant pool component through the modified structure by a java card application program interpreter. According to the method and system, a large number of internal skipping and external traversing are not required through the original method, so that the running efficiency of the java cards can be improved.
Owner:北京博思汇众科技有限公司
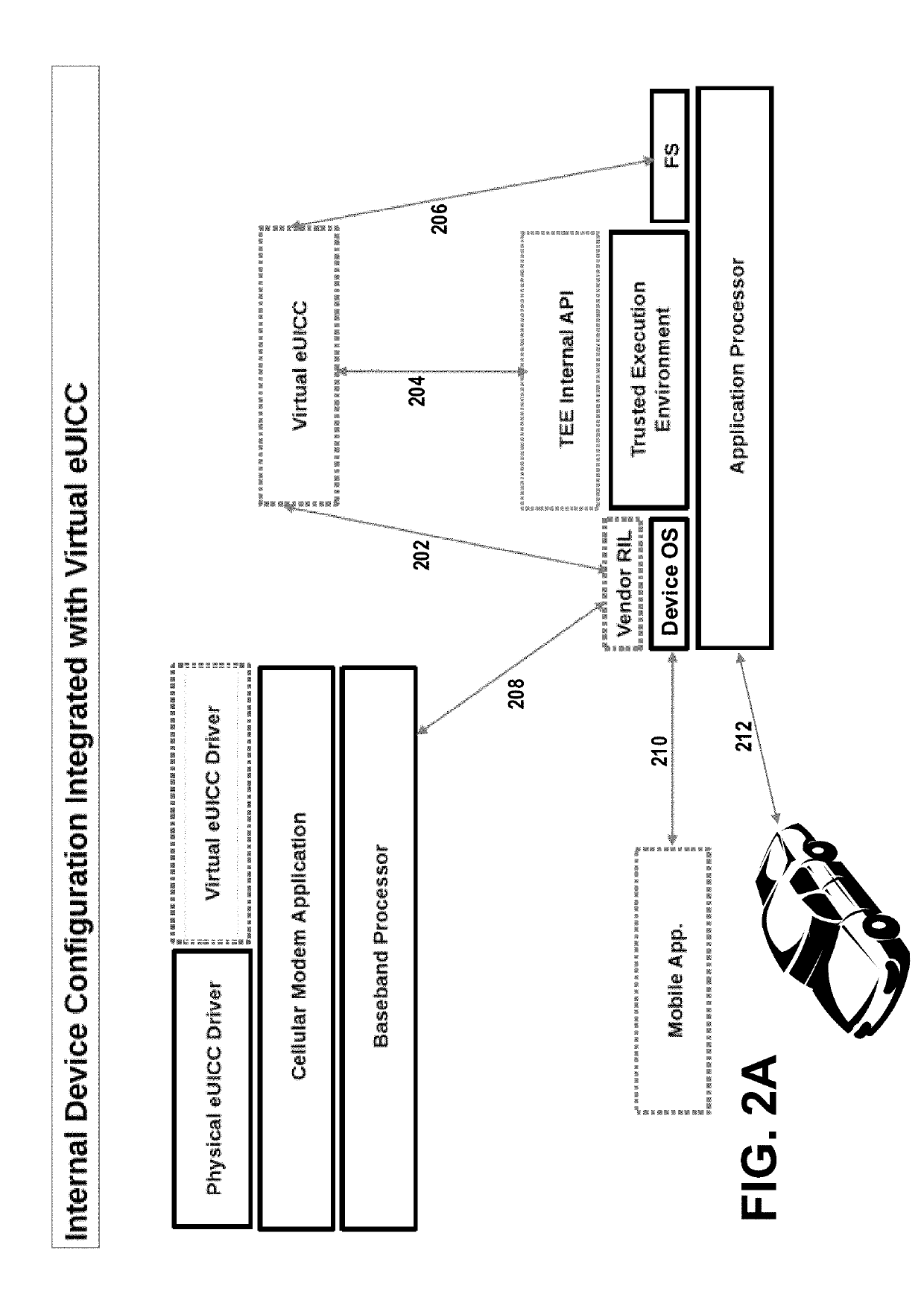
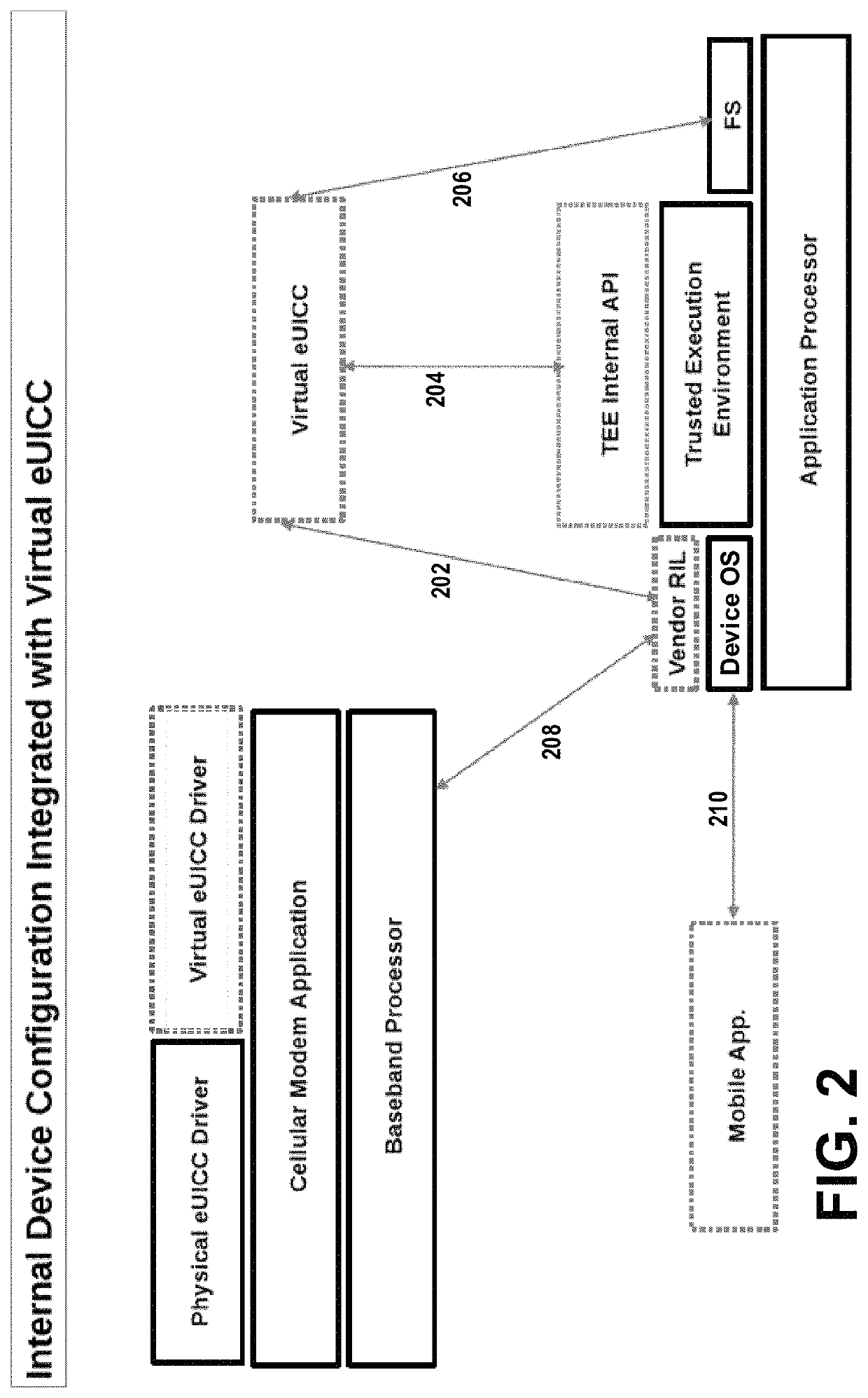
Apparatuses, methods, and systems for configuring a trusted JAVA card virtual machine using biometric information
ActiveUS20190230496A1Rapidly and cost-effectively supportFacilitates secure transmissionDigital data protectionInternal/peripheral component protectionModem deviceJava card virtual machine
Apparatuses, methods, and systems are provided for securely configuring a Java Card virtual machine operating on a cellular device's application processor. In one embodiment, a connected device with an integrated cellular modem, a virtual universal integrated circuit chip and an integrated fingerprint scanner are used. In another embodiment, the cellular device's built-in camera is used, instead of an integrated fingerprint scanner, to capture the user's facial image.
Owner:GIGSKY
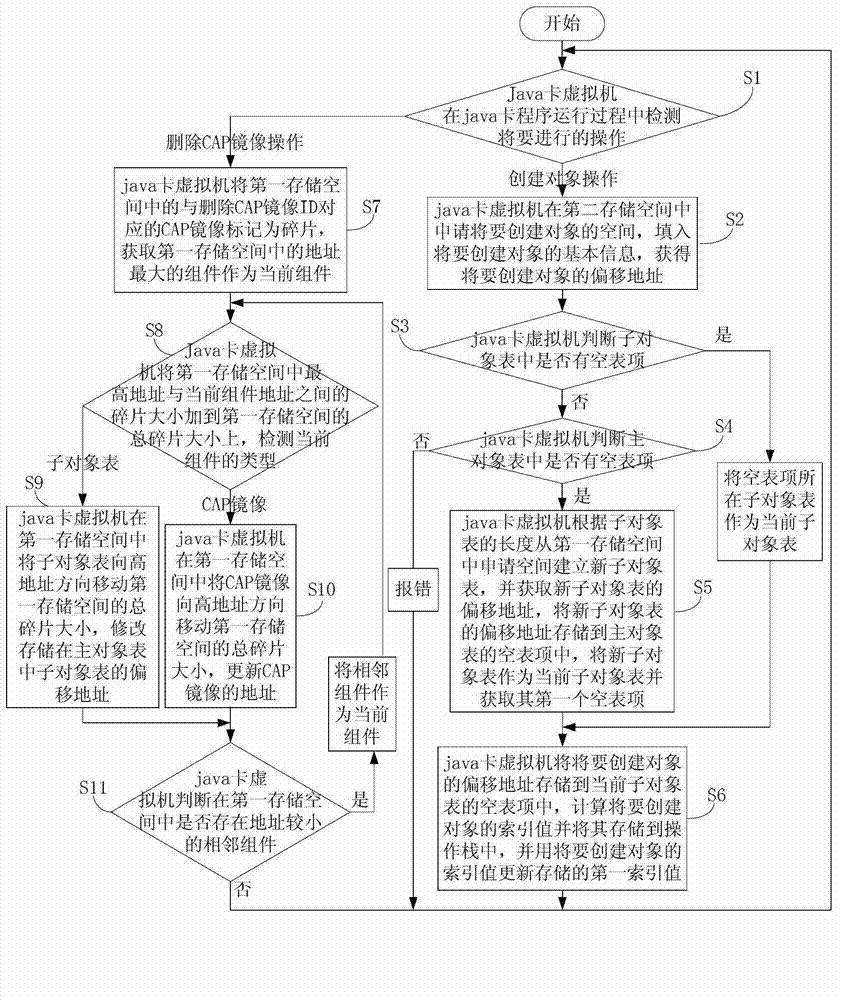
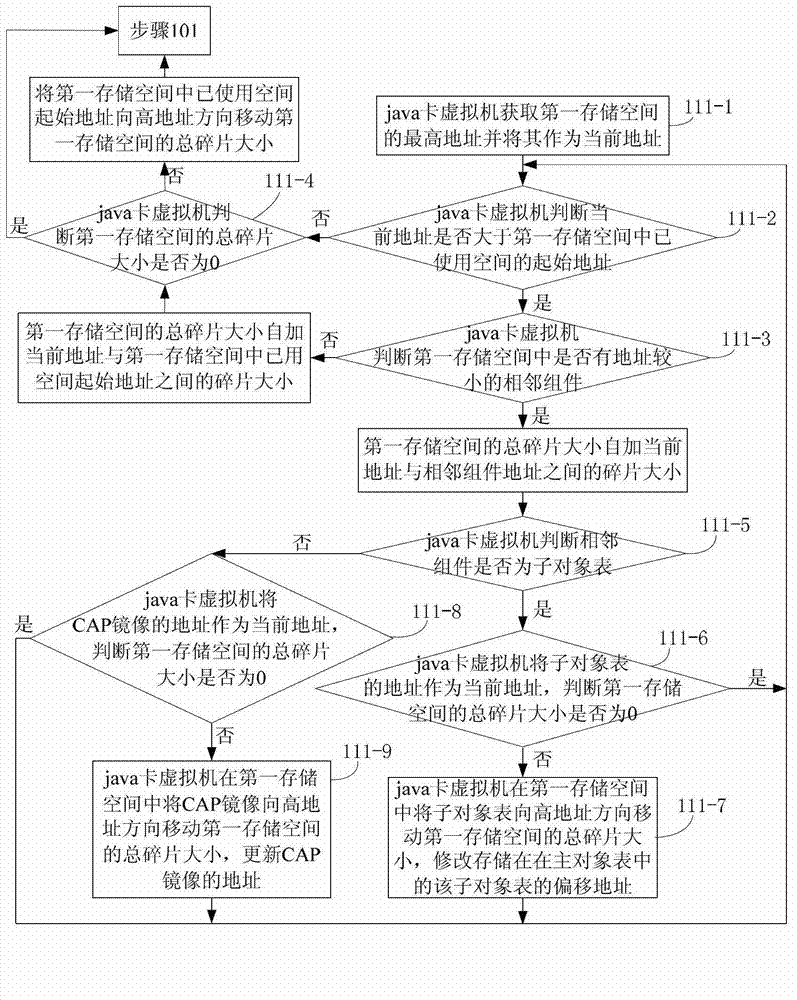
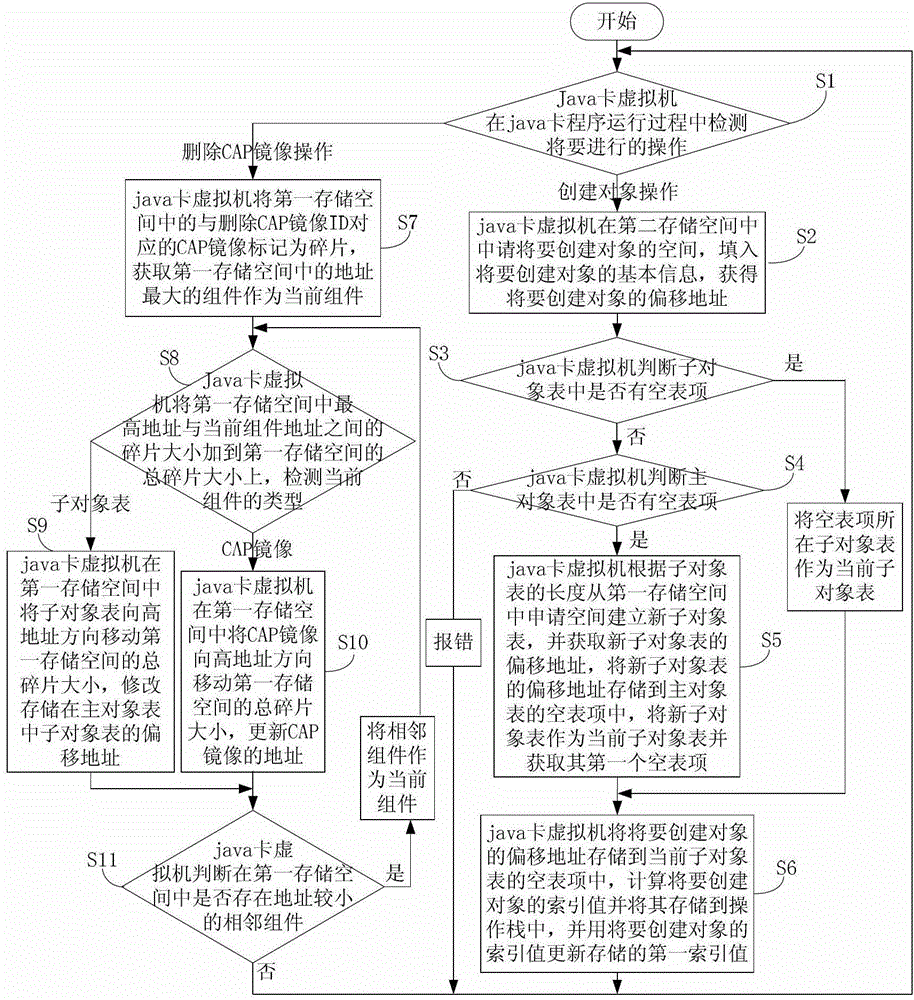
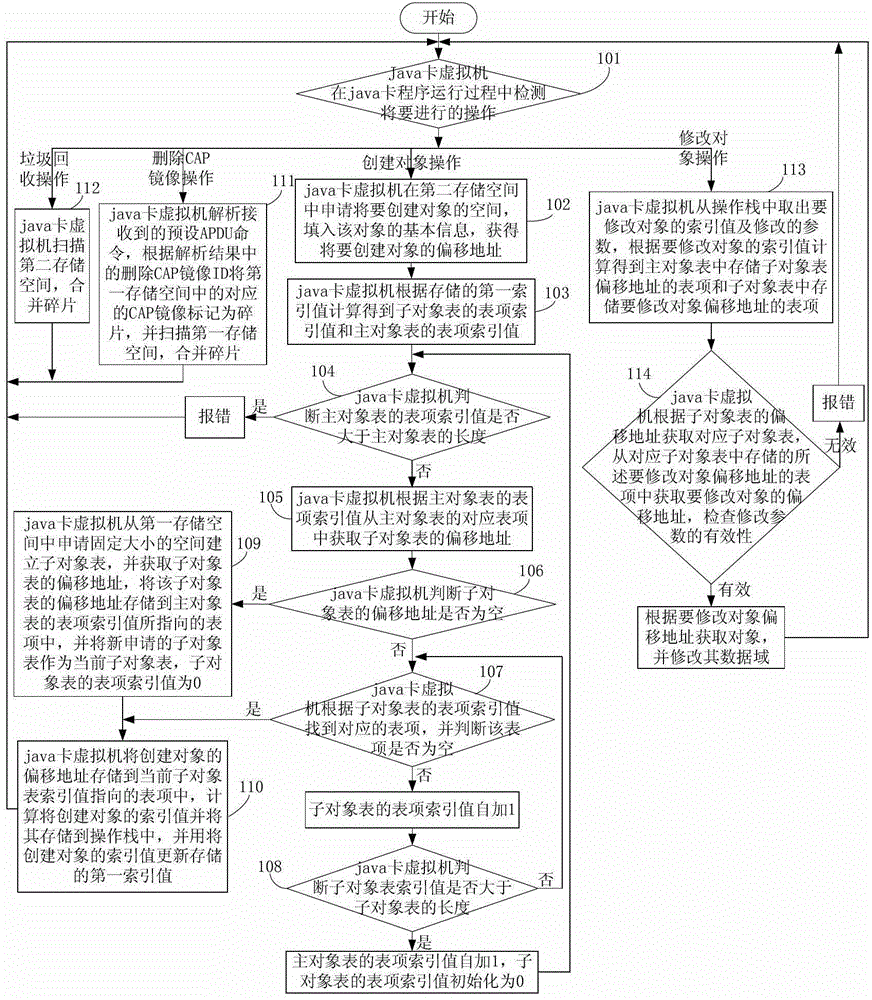
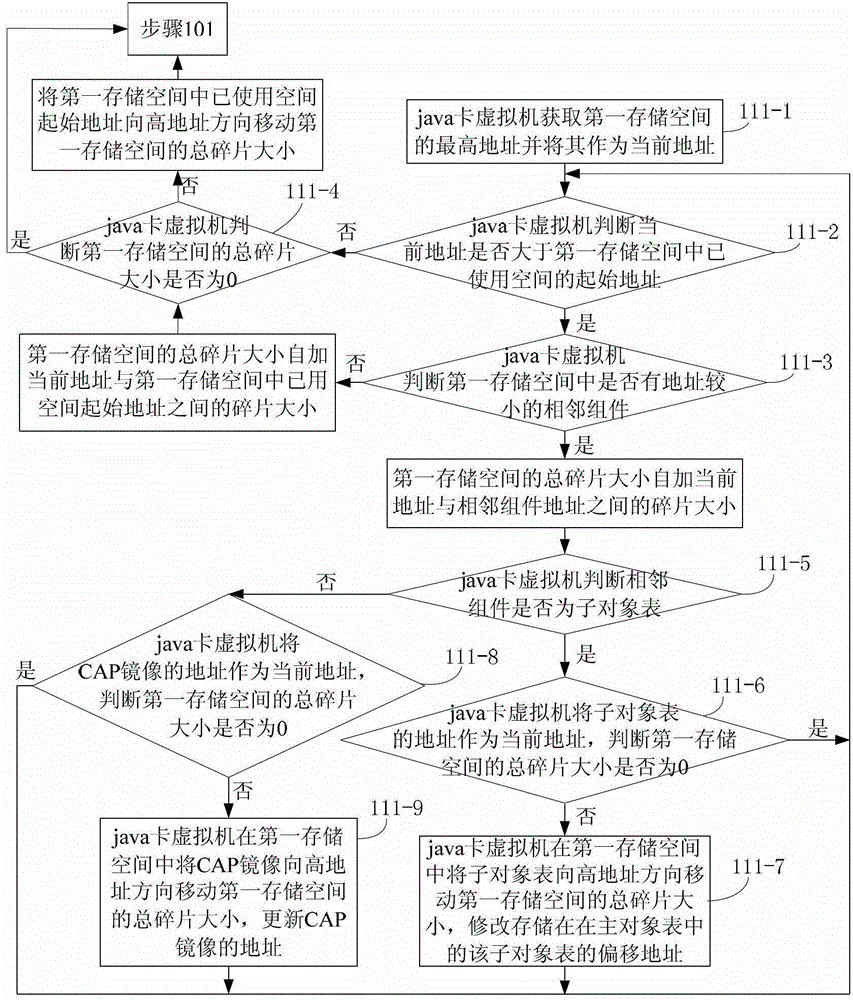
Object management method based on java card virtual machine
ActiveCN103116518ASave spaceEasy to operateMemory adressing/allocation/relocationSoftware simulation/interpretation/emulationManagement objectComputer-aided
The invention discloses an object management method based on a java card virtual machine. The object management method based on the java card virtual machine comprises that the java card virtual machine can detect an establishing object operation, and the basic information of the establishing object can be filled into a second memory space. An offset address of the to-be-established object can be obtained and stored in a blank table item of a sub object table. An index value of the to-be-established object can be calculated and used for replacing a first index value, wherein the first index value is stored. Deleting computer-aided production (CAP) image operation can be detected. A CAP image which is stored in a first memory space and corresponds to an identification (ID) of a deleting CAP image can be marked as a fragment. Types of assembly of the first memory space can be detected in sequence. When the type is the sub object table, the sub object table can be move to a high address direction. The offset address of the sub object table can be modified, wherein the sub object table is stored in a main object table. When the type is the CAP image, the CAP image can be moved to the high address direction and the CAP image address can be replaced. According to the object management method based on the java card virtual machine, a sub object and a main object can be used for managing objects so as to be easy and convenient. In addition, resources are saved.
Owner:FEITIAN TECHNOLOGIES
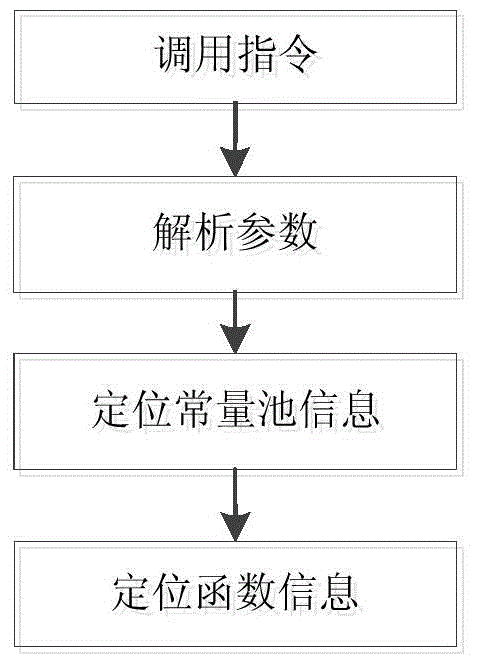
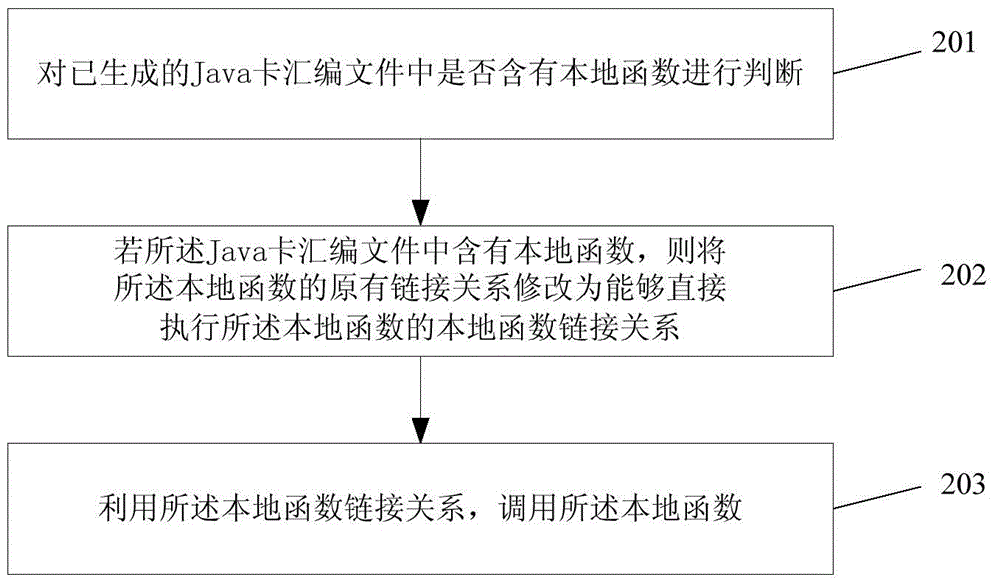
Method and apparatus for calling local function in Java card virtual machine
InactiveCN105005497AImprove execution efficiencySave the search processSoftware simulation/interpretation/emulationMemory systemsLocal functionJava card virtual machine
The invention discloses a method and apparatus for calling a local function in a Java card virtual machine and relates to a Java card virtual machine system. The method comprises: determining whether a generated Java card assembly file comprises a local function or not; if the Java card assembly file comprises a local function, changing an original link relationship of the local function to a local function link relationship that can directly execute the local function; and calling the local function by using the local function link relationship. According to the invention, local function execution efficiency of the Java card virtual machine is improved, and storage space of a Java card is reduced as well.
Owner:ZHONGCHAO CREDIT CARD IND DEV
Smart card and application data processing method
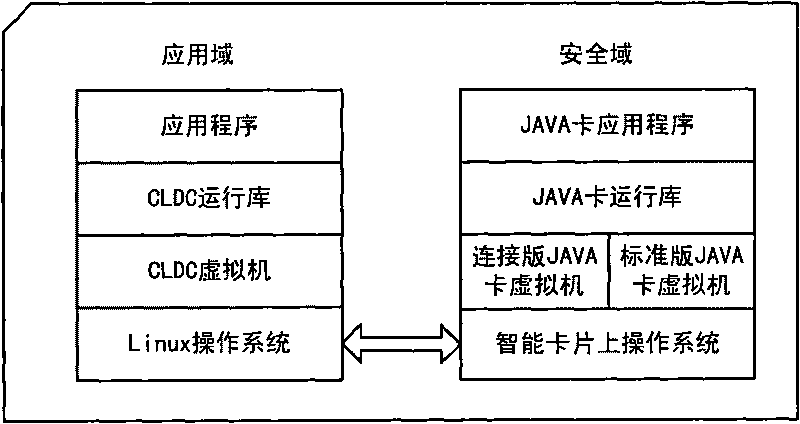
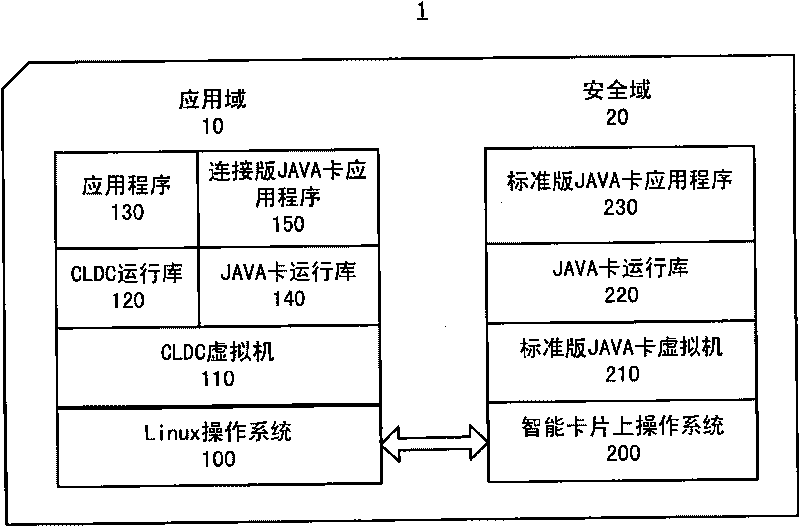
InactiveCN101739246AGood application effectShorten the timeInterprogram communicationRecord carriers used with machinesOperational systemChip operating system
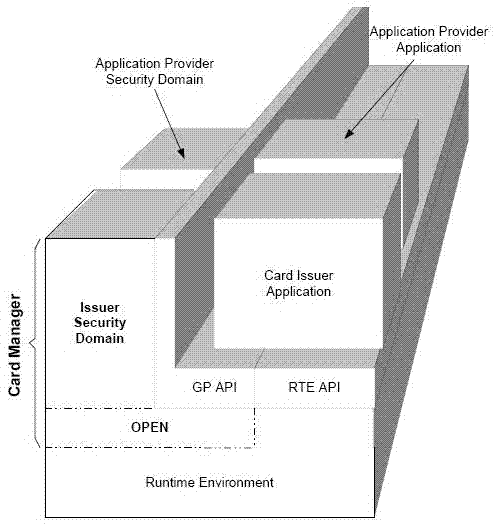
The invention relates to a smart card and an application data processing method. The smart card comprises a security domain and an application domain, wherein the security domain comprises an on-chip operating system, a standard-version JAVA card virtual machine operated on the on-chip operating system, a JAVA card runtime library and a standard-version JAVA card application program; and the application domain comprises an operating system, a virtual machine operated on the operating system, a JAVA card runtime library and a connection-version JAVA card application program. The smart card and the application data processing method can reduce the transmission waiting time and the communication delay of application data and improve the application performance of the smart card under the condition that the system safety of the smart card is not reduced and an extra cost is not increased.
Owner:爱思开电讯投资(中国)有限公司
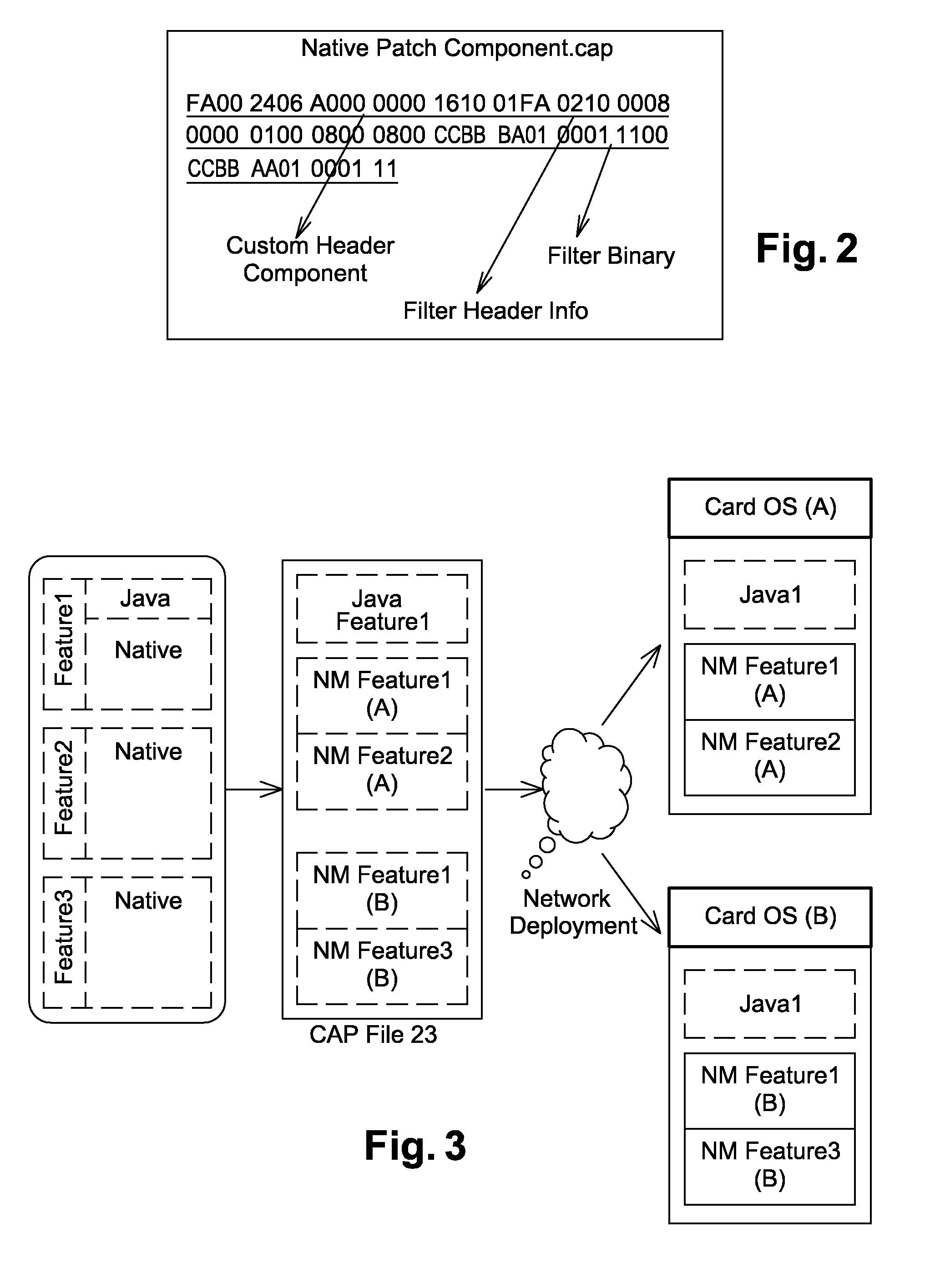
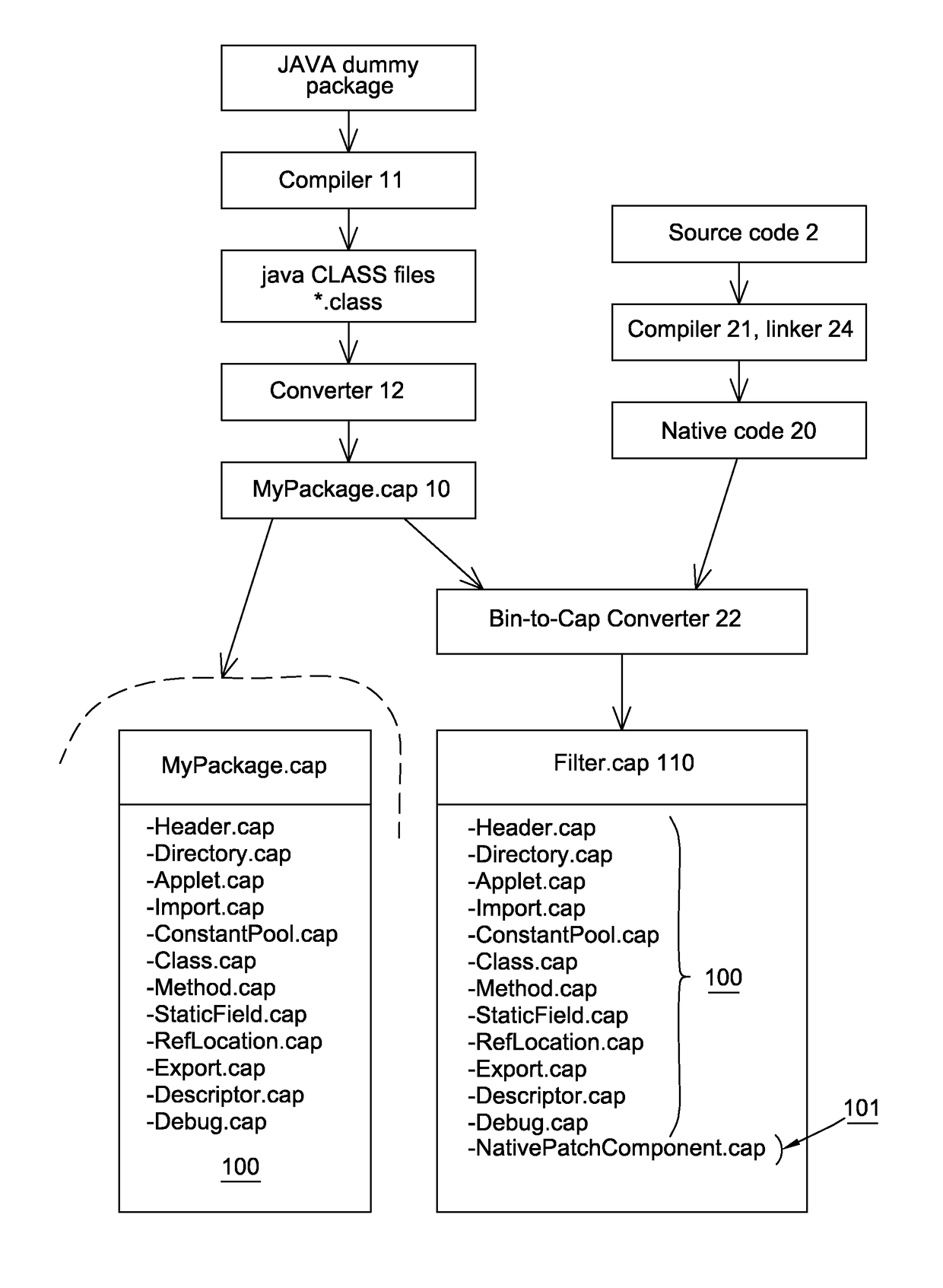
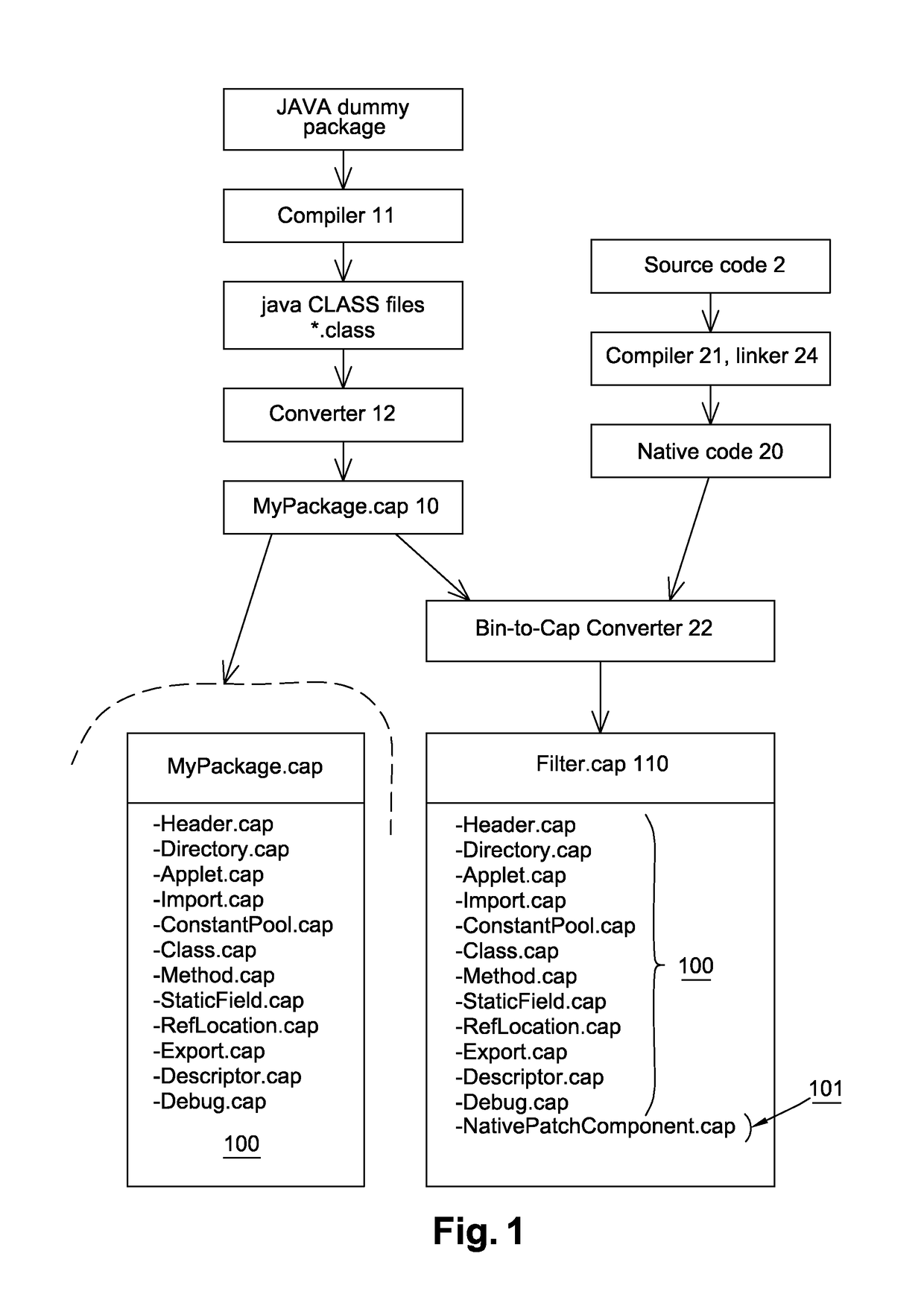
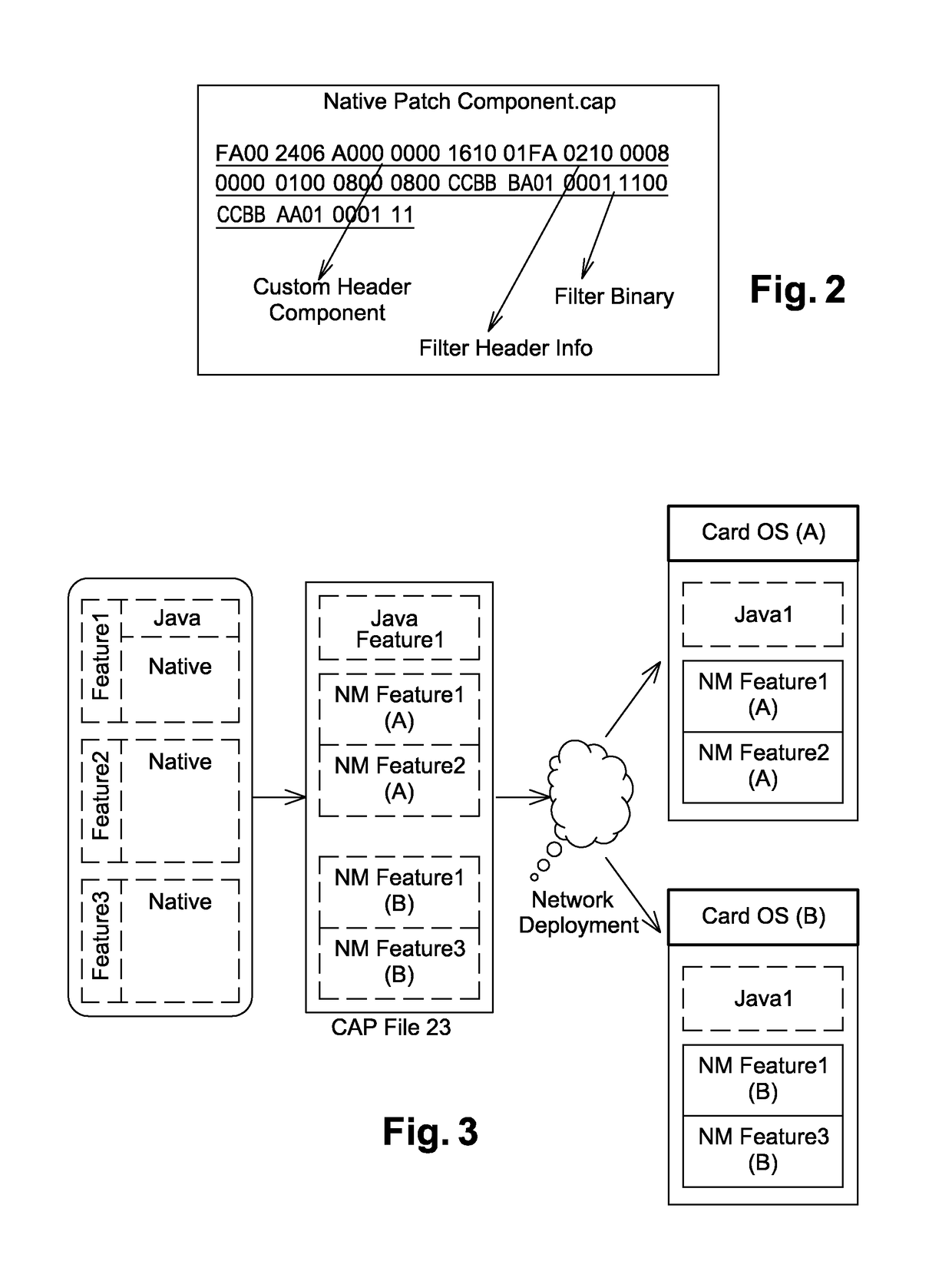
Method for loading a native code on a secure element
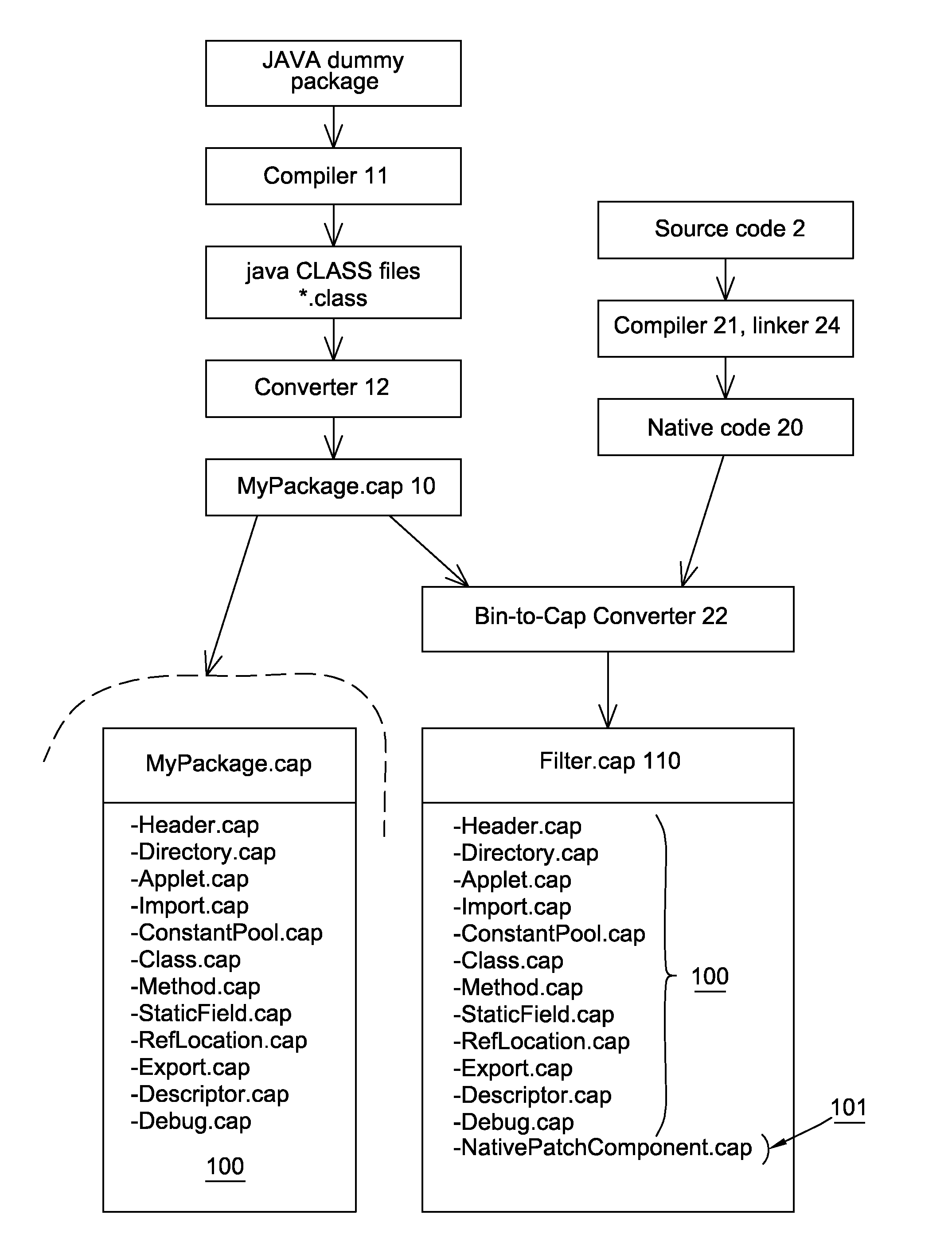
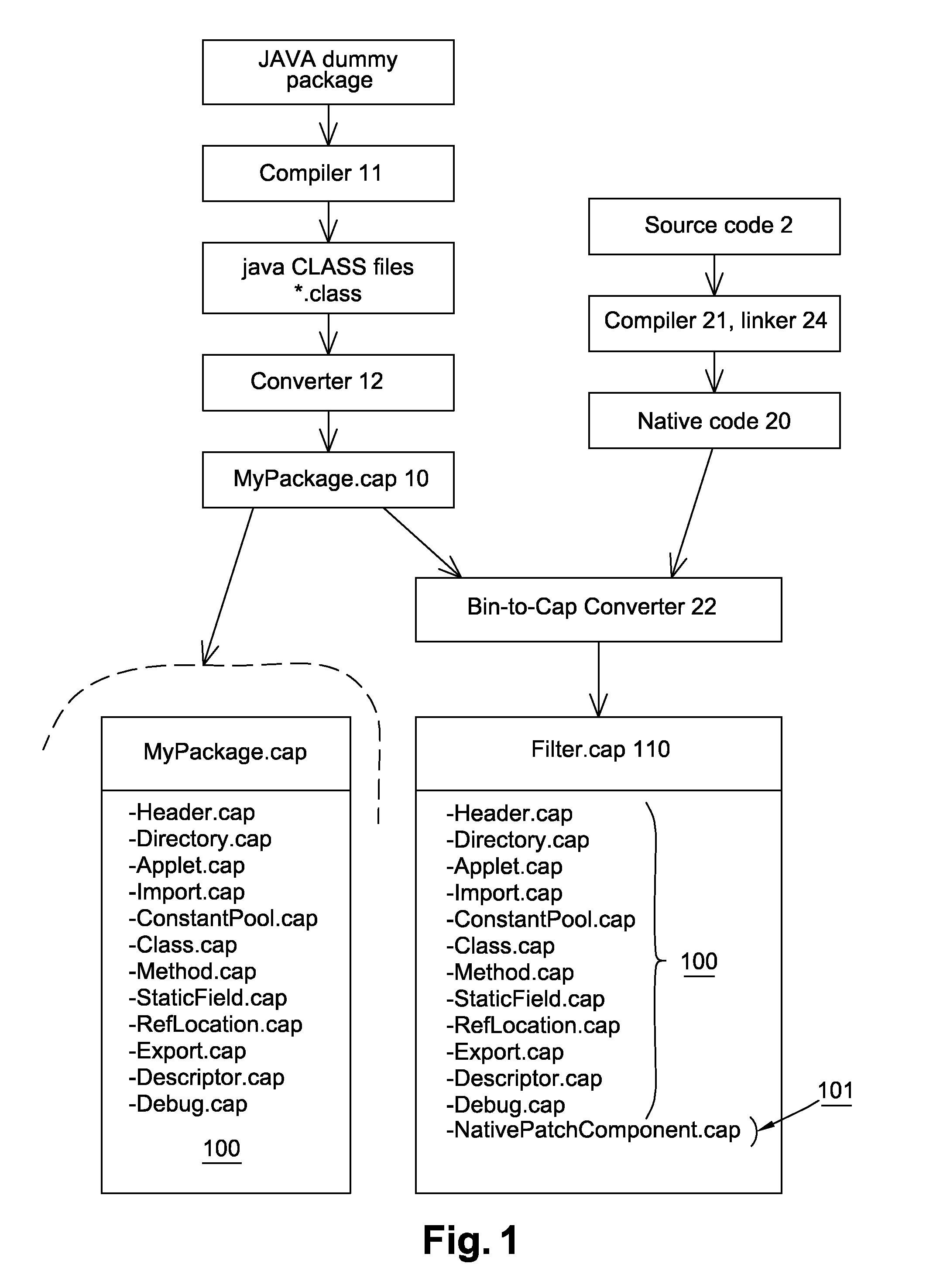
ActiveUS20160299832A1Easy to correctEasy to deploySoftware testing/debuggingInternal/peripheral component protectionProgramming languageJava card virtual machine
The invention relates to a method for loading at least one native code on at least one target secure element comprising a java card virtual machine, said method comprising the following steps: providing a modified CAP file composed of at least one custom CAP component comprising a native code; extracting said native code from the custom CAP component; installing said native code in the target secure.
Owner:GEMPLU
32-bit embedded microprocessor adopting double instruction set
InactiveCN1216327CIncrease the areaImprove execution efficiencyConcurrent instruction executionProcessor registerJava card virtual machine
The invention is a kind of 32 bits embedded micro-processor which uses the new structure; it can process the local RISC instruction and Java virtual machine instruction. It is made up of instruction taking unit, instruction cache, instruction coding circuit, instruction replicating circuit, universal register group, data calculating unit, memory unit, promoting circuit and abnormity processing unit. The injunction cache and injunction replicating circuit is useful only in executing the Java virtual machine, at the same time, the universal register group is mapped into stack cache. The inventions have two instructions repertories, they can be switches seamlessly, but the circuit area increases only no more than 20% compared with the old.
Owner:FUDAN UNIV
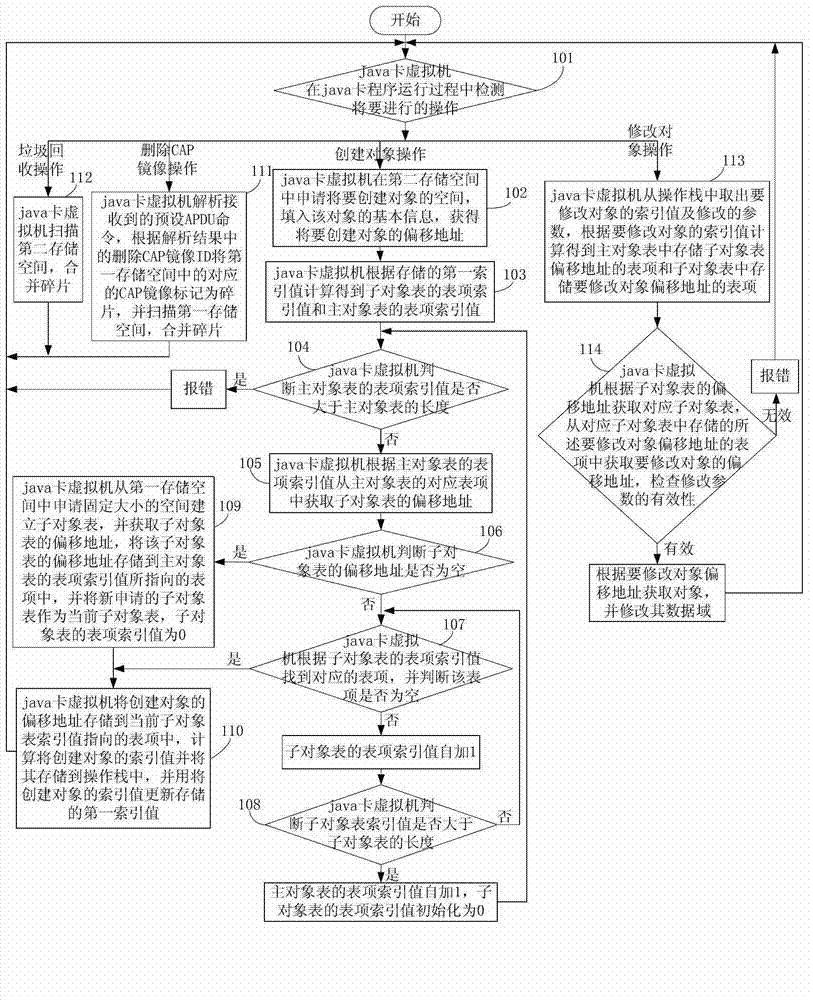
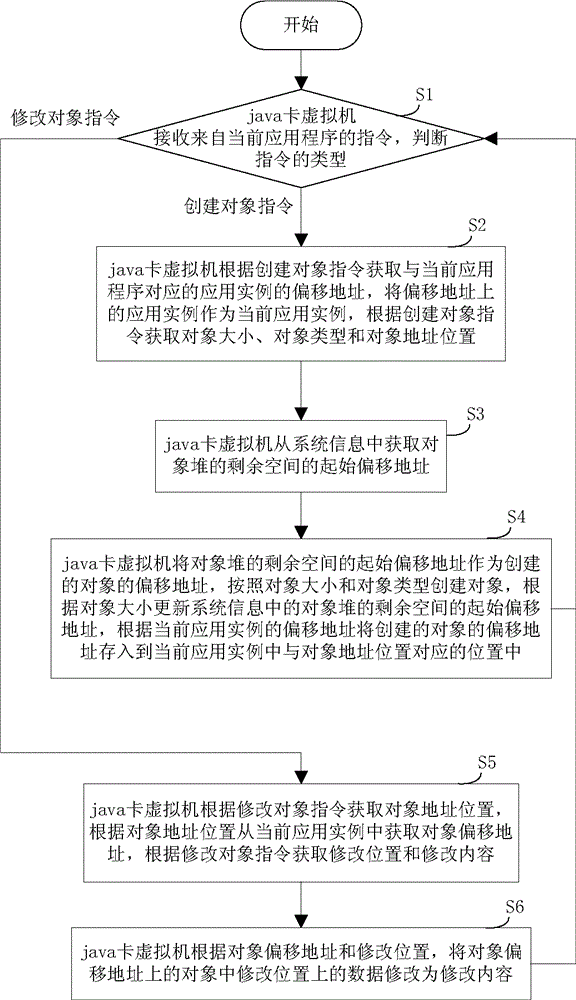
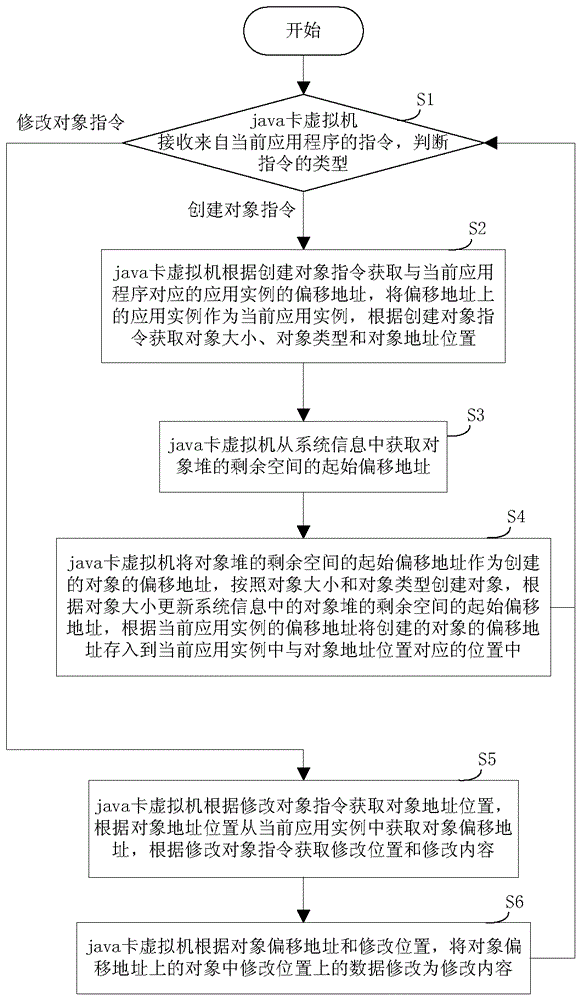
Method and device for efficient object management
ActiveCN103955395AEasy to operateImprove work efficiencySoftware simulation/interpretation/emulationJava card virtual machineComputer science
The invention discloses a method and device for efficient object management. The method comprises the following steps: 1, receiving an instruction from a present application program through a java virtual machine, performing step 2 if the instruction is an object establishment instruction, and performing step 5 if the instruction is an object modification instruction; 2, acquiring a present application case, the object size, the object type and the object address position according to the object establishment instruction; 3, acquiring the initial deviation address of the residual space of an object heap from system information; 4, establishing an object according to the object size and the object type, updating the initial deviation address of the residual space of the object heap, storing the deviation address of the established object into the present application case, and returning to the step 1; 5, acquiring an object deviation address, the modification position and the modification content according to the object modification instruction; 6, modifying data in the modification position of the object on the object deviation address into the modification content, and returning to the step 1.
Owner:FEITIAN TECHNOLOGIES
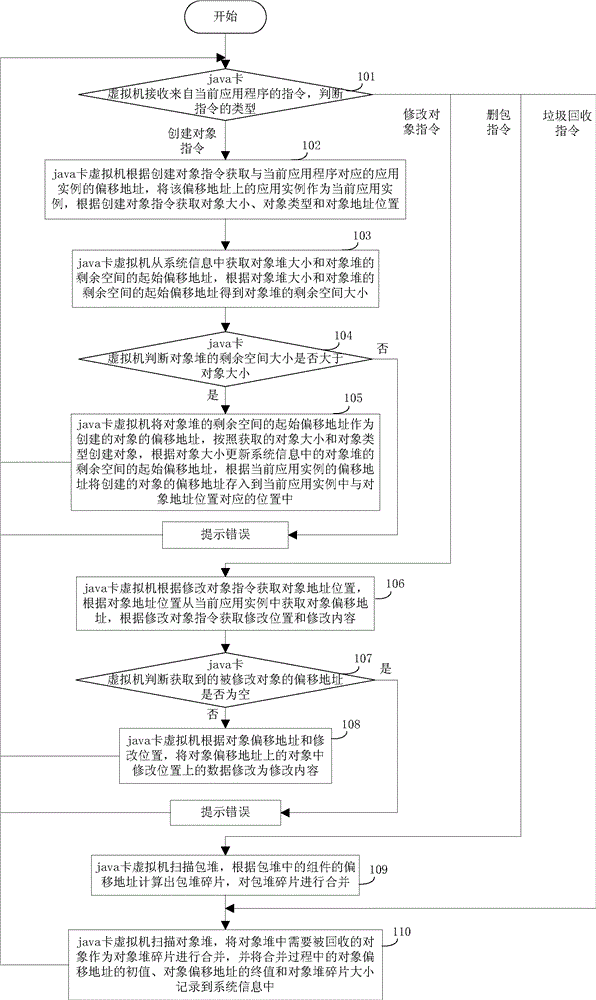
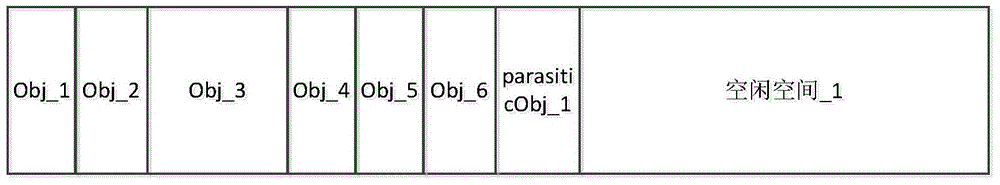
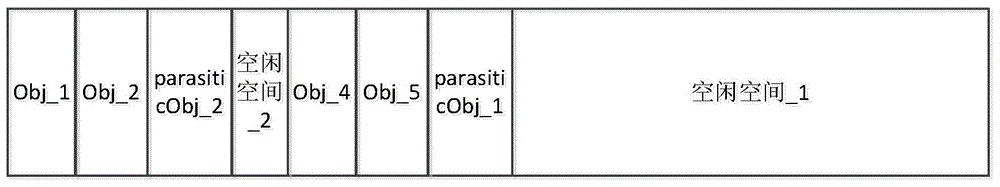
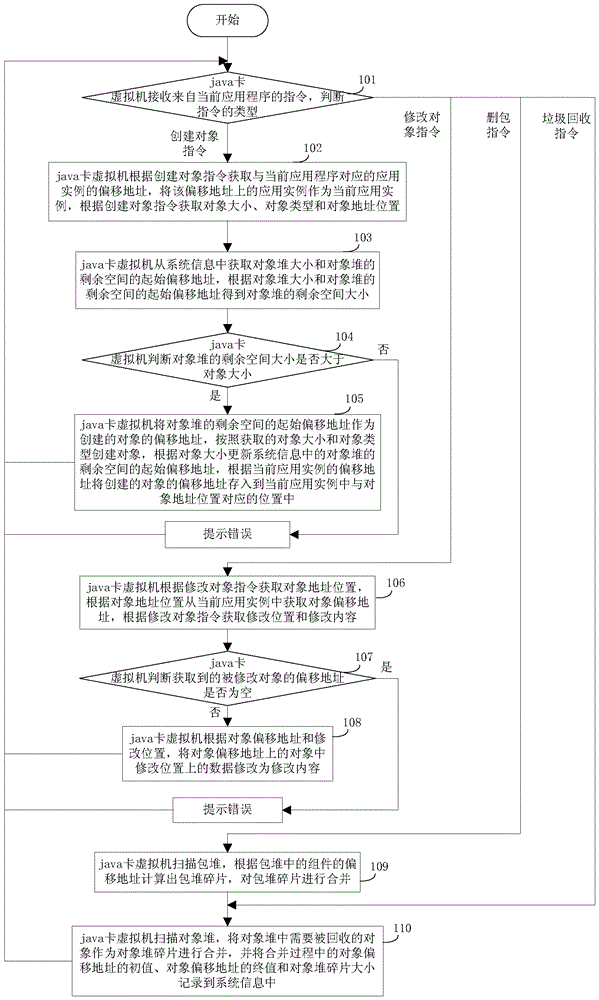
Method and device for managing object heap by using parasitic object
ActiveCN103559076AImprove space utilizationEfficient managementSoftware simulation/interpretation/emulationApplication programming interfaceManaged object
The invention discloses a method and a device for managing an object heap by using a parasitic object. According to the method and the device, a free space in the object heap is marked by using the parasitic object and a space is applied for an object to be established in the object heap according to the parasitic object so as to effectively manage the free space in the object heap and improve the space utilization rate of the object heap; after package deletion or application deletion operation is carried out and after detecting a pre-set API (Application Programming Interface) corresponding to java card application program calling and garbage recycling, only a dummy instruction needs to be operated and the garbage recycling does not need to be carried out through moving the established object in the object heap, so that moving times of the established object are reduced and the time consumption caused by moving the object is reduced, the working efficiency of a Java card virtual machine is improved and the abrasion balance is reached to a certain extent.
Owner:FEITIAN TECHNOLOGIES
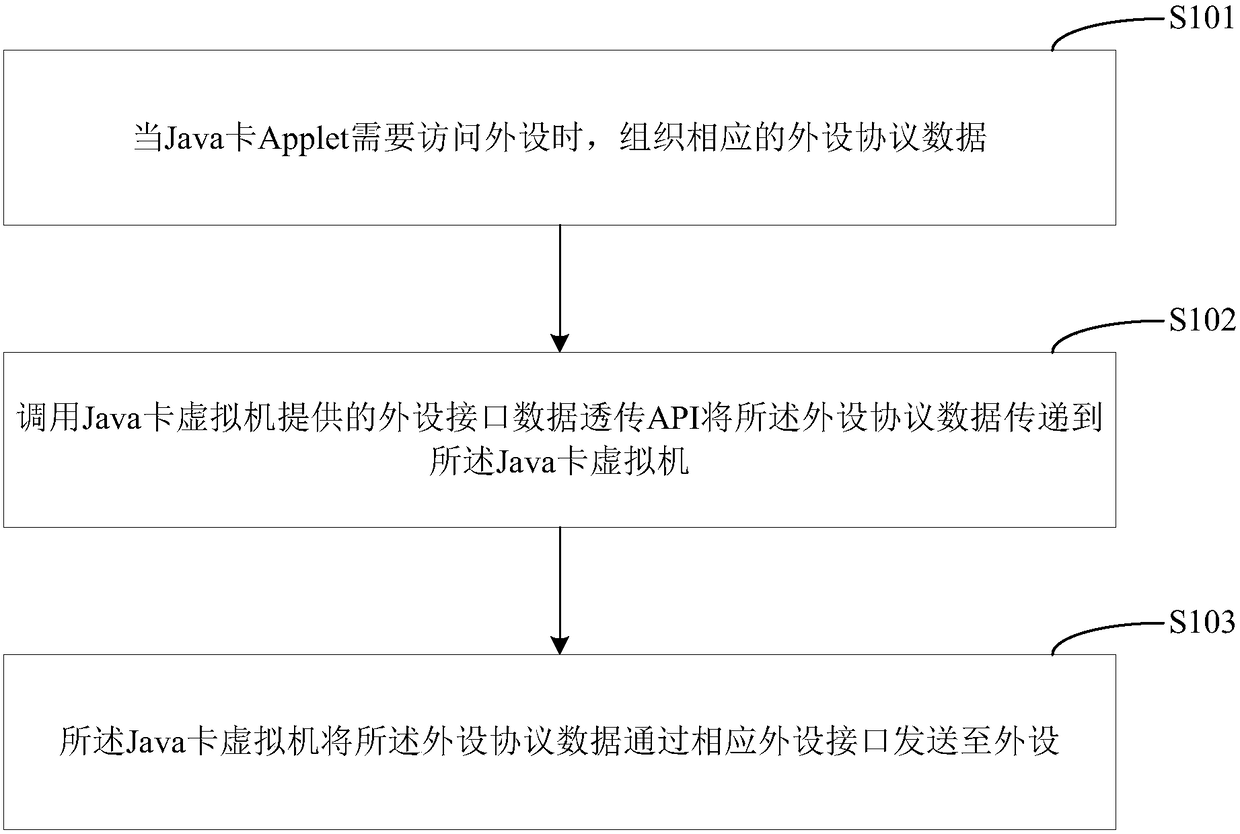
Java card peripheral access method and Java card virtual machine
ActiveCN108595245AImprove scalabilityShorten the development cycleSoftware simulation/interpretation/emulationComputer hardwareExtensibility
The invention is suitable for the technical field of Java cards, and provides a Java card peripheral access method and a Java card virtual machine. The method comprises the steps of organizing corresponding peripheral protocol data when a Java card Applet needs to access a peripheral; calling a peripheral interface data unvarnished transmission API provided by the Java card virtual machine to transmit the peripheral protocol data to the Java card virtual machine; and sending the peripheral protocol data to the peripheral through a corresponding peripheral interface by the Java card virtual machine. Through the method, the expandability of the Java card virtual machine can be improved; the development cycle of a Java card can be shortened; and the product stability can be improved.
Owner:SHENZHEN EXCELSECU DATA TECH
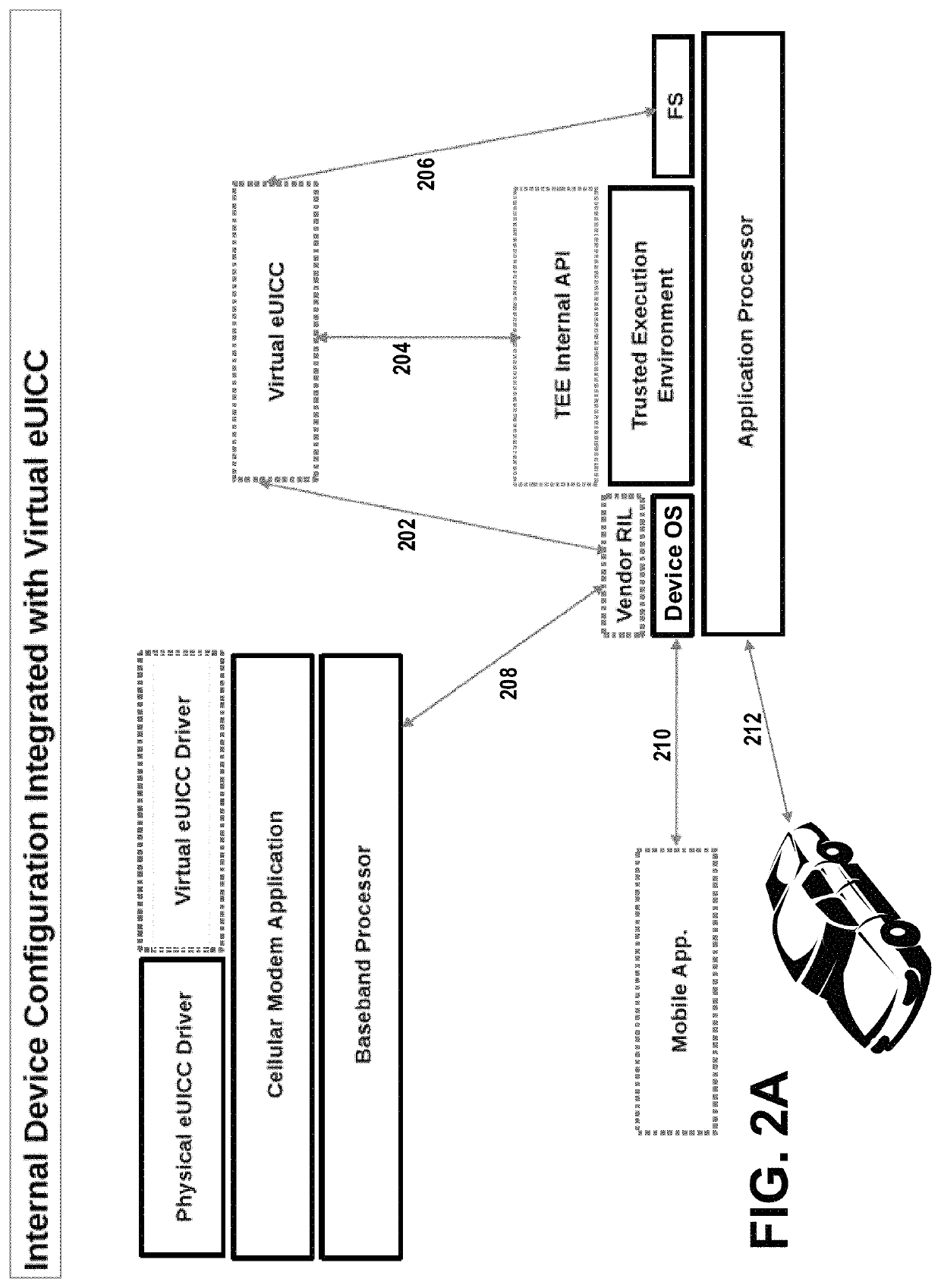
Apparatuses, methods, and systems for configuring a trusted java card virtual machine using biometric information
ActiveUS11172352B2Rapidly and cost-effectively supportFacilitate transmissionDigital data protectionInternal/peripheral component protectionModem deviceJava card virtual machine
Apparatuses, methods, and systems are provided for securely configuring a Java Card virtual machine operating on a cellular device's application processor. In one embodiment, a connected device with an integrated cellular modem, a virtual universal integrated circuit chip and an integrated fingerprint scanner are used. In another embodiment, the cellular device's built-in camera is used, instead of an integrated fingerprint scanner, to capture the user's facial image.
Owner:GIGSKY
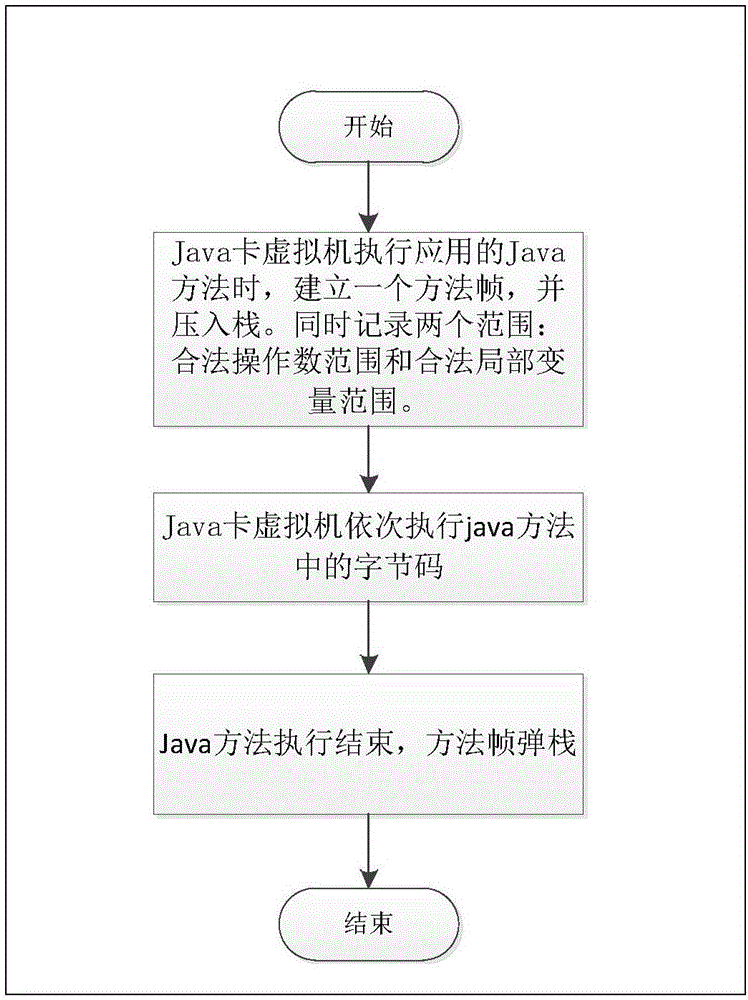
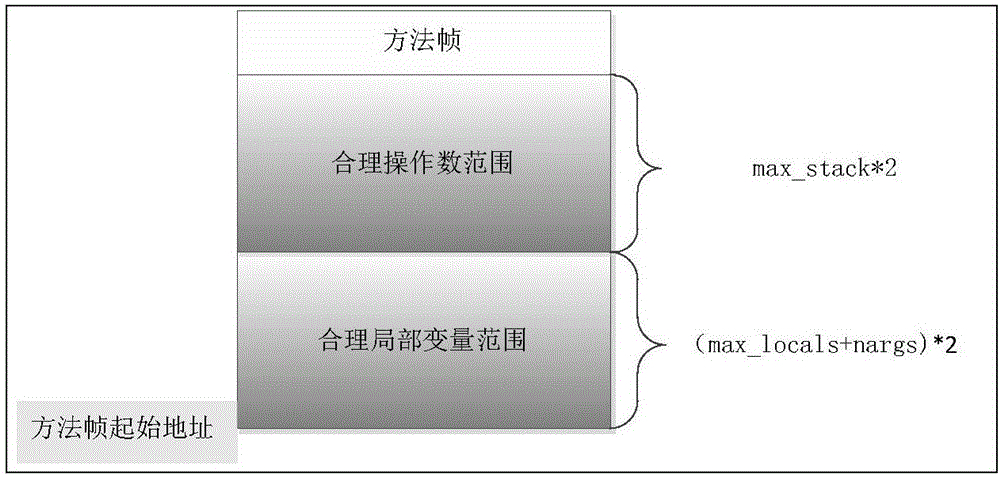
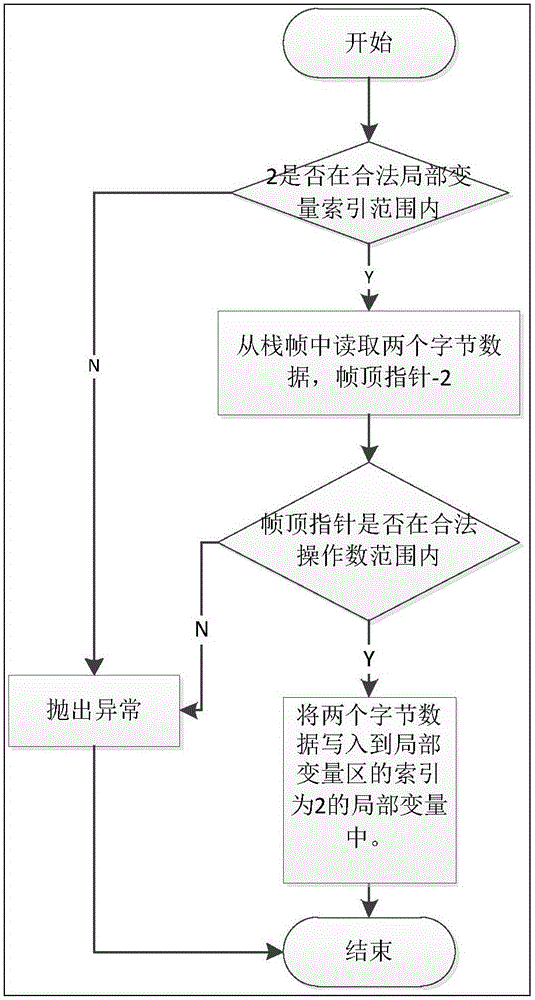
Boundary checking method of JAVA card frame
InactiveCN106845225AImprove securityPlatform integrity maintainanceSoftware simulation/interpretation/emulationLocal variableSmart card
The invention discloses a boundary checking method of a JAVA card frame and belongs to the technical field of smart cards. The boundary checking method includes the steps that when a Java card virtual machine executes a Java method of an application, a method frame is established, a stack is pressed into the frame, and a starting address of the method frame is recorded; meanwhile, two ranges are recorded and include a legal operand range and a legal local variable indexing range; when the Java card virtual machine executes inner byte codes of the Java method of the application, and the stack data type operated by the machine is obtained; if current operating data is local variables, whether local variable indexes are in the legal local variable indexing range or not is judged, if yes, the operation is permitted, and if not, abnormity is prompted; if the current operating data is operands, whether operand addresses are in the legal operand range or not is judged, if yes, the operation is permitted, and if not, abnormity is prompted. The multi-application security management of the Java card is achieved.
Owner:BEIJING CEC HUADA ELECTRONIC DESIGN CO LTD
A method and device capable of efficient object management
ActiveCN103955395BEasy to operateImprove work efficiencySoftware simulation/interpretation/emulationJava card virtual machineComputer science
The invention discloses a method and device for efficient object management. The method comprises the following steps: 1, receiving an instruction from a present application program through a java virtual machine, performing step 2 if the instruction is an object establishment instruction, and performing step 5 if the instruction is an object modification instruction; 2, acquiring a present application case, the object size, the object type and the object address position according to the object establishment instruction; 3, acquiring the initial deviation address of the residual space of an object heap from system information; 4, establishing an object according to the object size and the object type, updating the initial deviation address of the residual space of the object heap, storing the deviation address of the established object into the present application case, and returning to the step 1; 5, acquiring an object deviation address, the modification position and the modification content according to the object modification instruction; 6, modifying data in the modification position of the object on the object deviation address into the modification content, and returning to the step 1.
Owner:FEITIAN TECHNOLOGIES
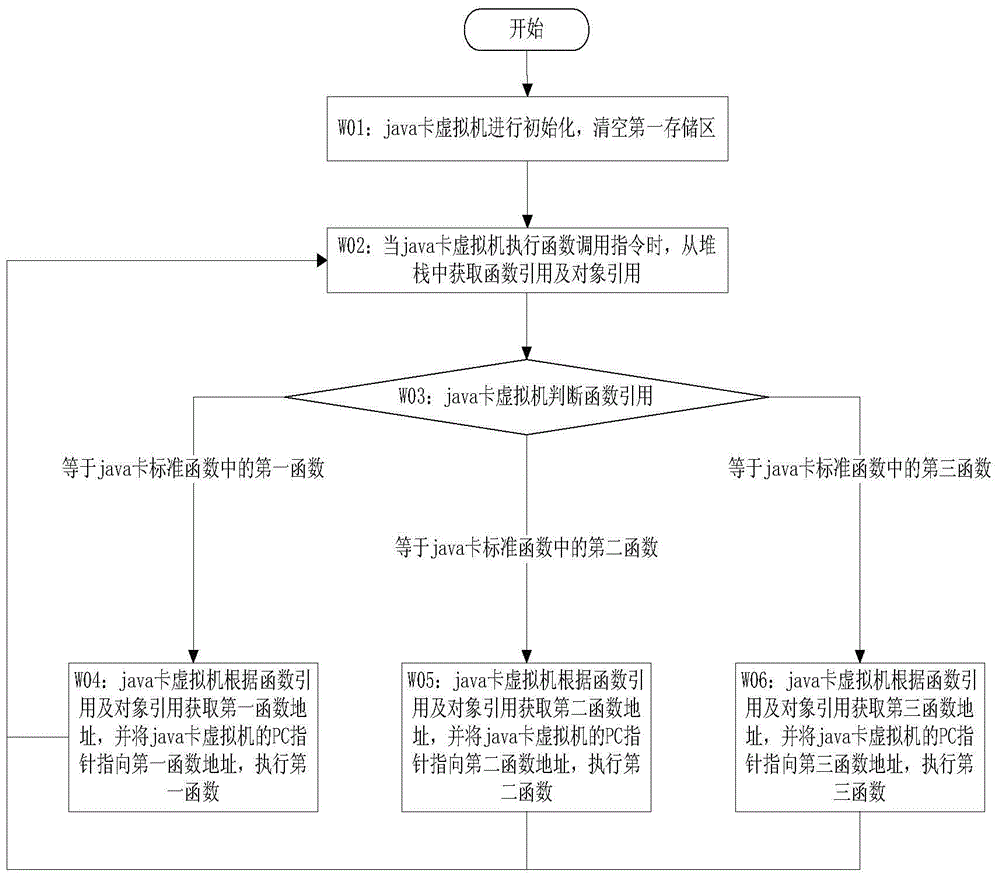
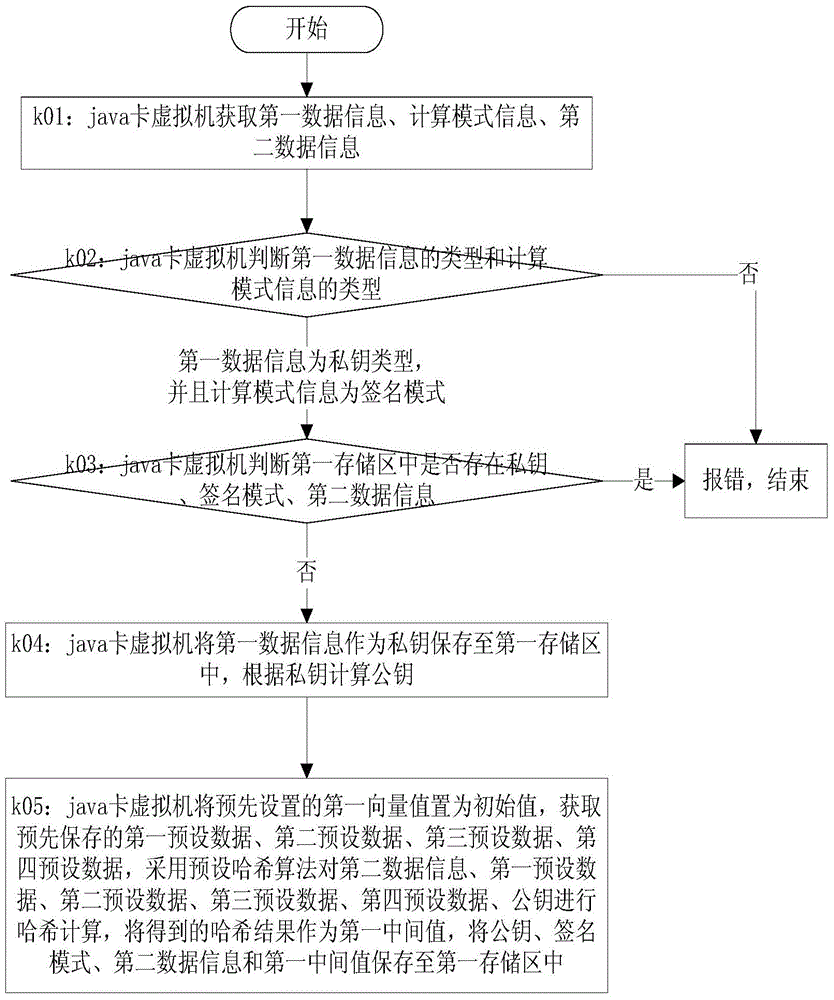
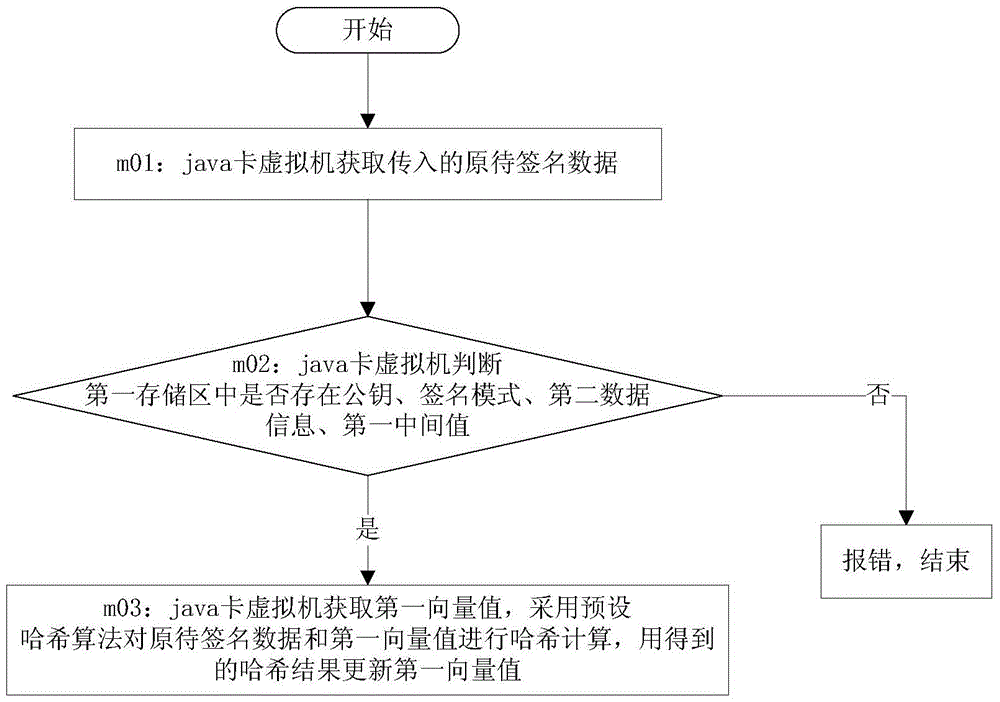
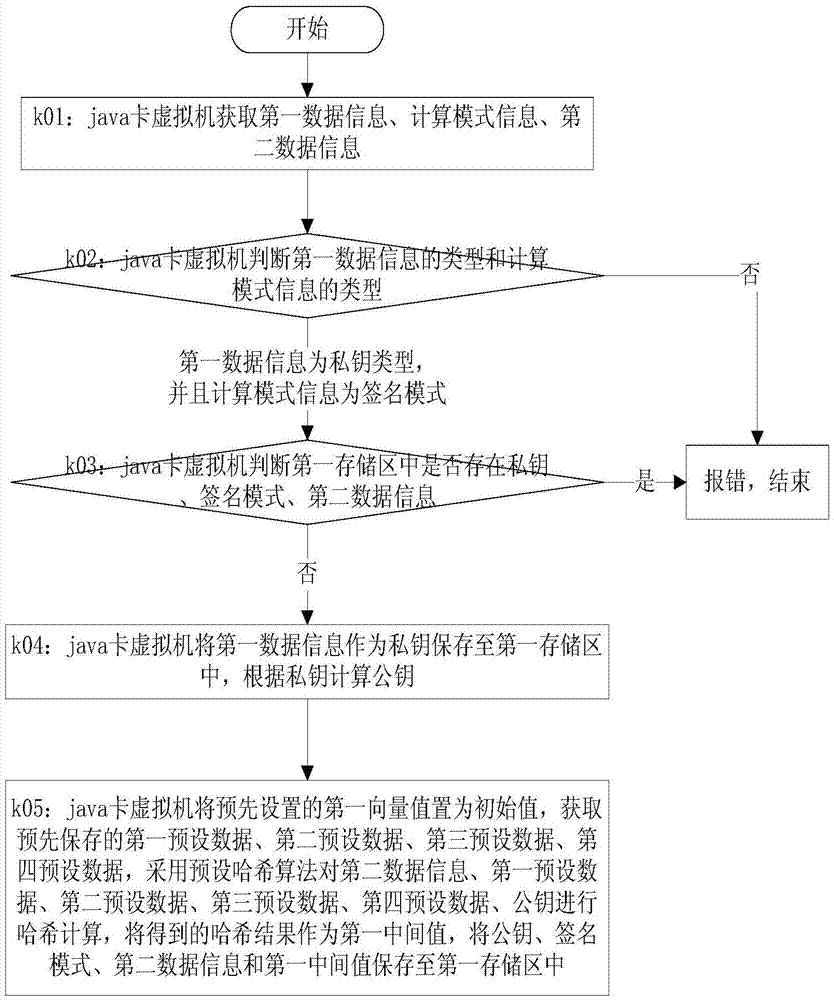
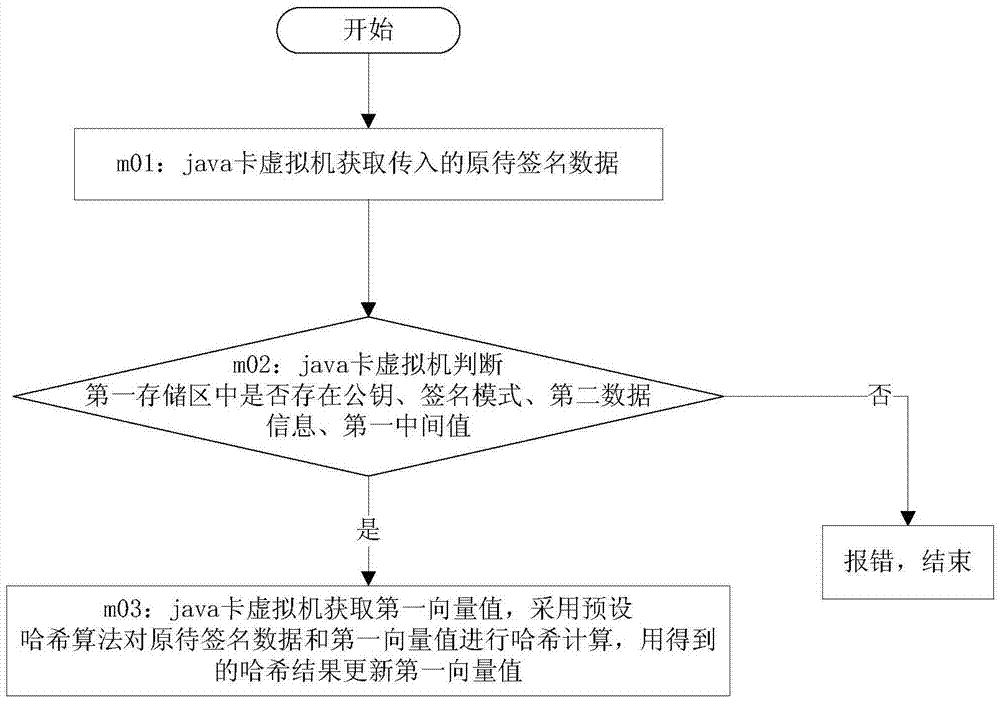
A Java Card Realization Method Supporting Data Signature
ActiveCN104331657BImprove securityDigital data protectionDigital data authenticationOriginal dataDigital signature
The invention provides a java card realization method supporting digital signature, and belongs to the field of information security. The adopted method comprises the following steps that a java card virtual machine executes a called function according to a function calling instruction; through the execution of the first function, transmitted first data information is stored as a private key, a public key is calculated according to the private key, second data information and the public key are subjected to Hash calculation, the obtained Hash result is used as a first middle value, calculation mode information is stored as a signature mode, and the public key, the transmitted second data information and the first middle value are stored; a first vector value is updated through the execution of a second function; through the execution of a third function, a storage region is allocated, the first vector value and transmitted original data to be signed are subjected to Hash calculation to obtain a second middle value, the private key is obtained, the second middle value and the private key are signed, the obtained signature result is stored into the storage region, the length of the signature result is calculated, and the length of the signature result is returned.
Owner:FEITIAN TECHNOLOGIES
Method for loading a native code on a secure element
ActiveUS10120780B2Easy to correctEasy to deploySoftware testing/debuggingInternal/peripheral component protectionProgramming languageJava card virtual machine
The invention relates to a method for loading at least one native code on at least one target secure element comprising a java card virtual machine, said method comprising the following steps: providing a modified CAP file composed of at least one custom CAP component comprising a native code; extracting said native code from the custom CAP component; installing said native code in the target secure.
Owner:THALES DIS FRANCE SA
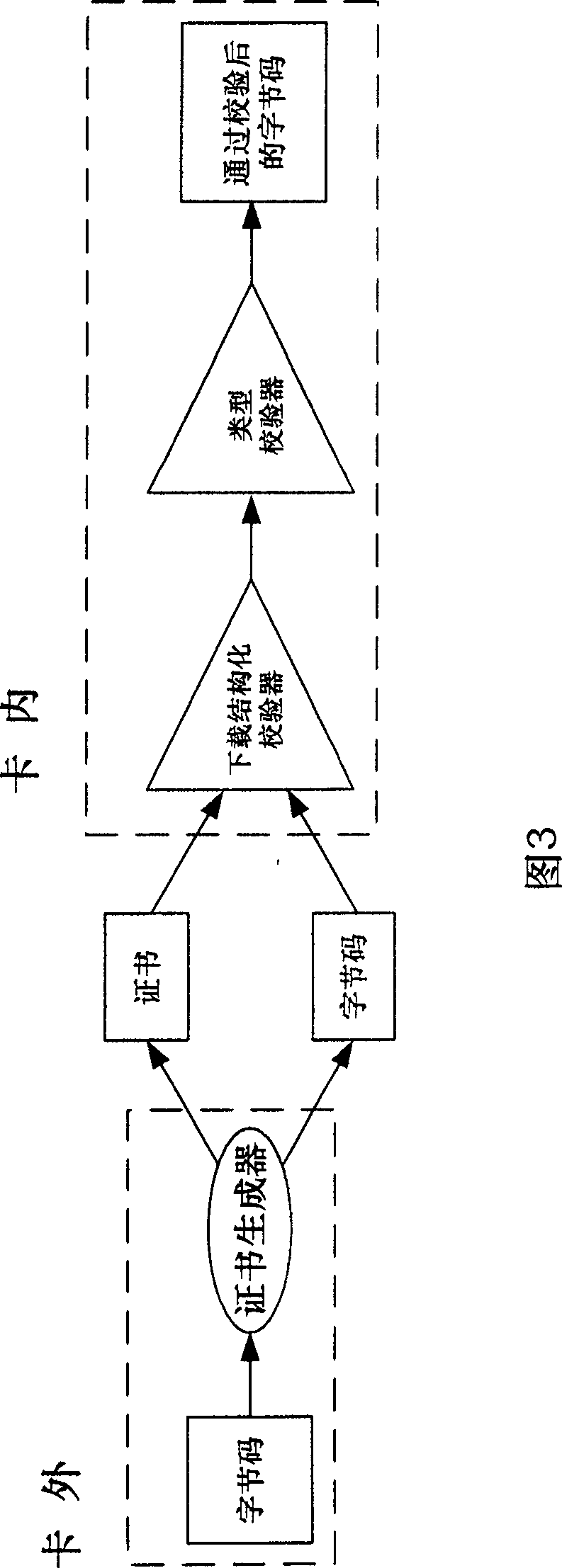
Smart card safety environment control method
InactiveCN100462890CAvoid Single Points of Security FailureLower requirementDigital data processing detailsProgram controlDigital signatureSmart card security
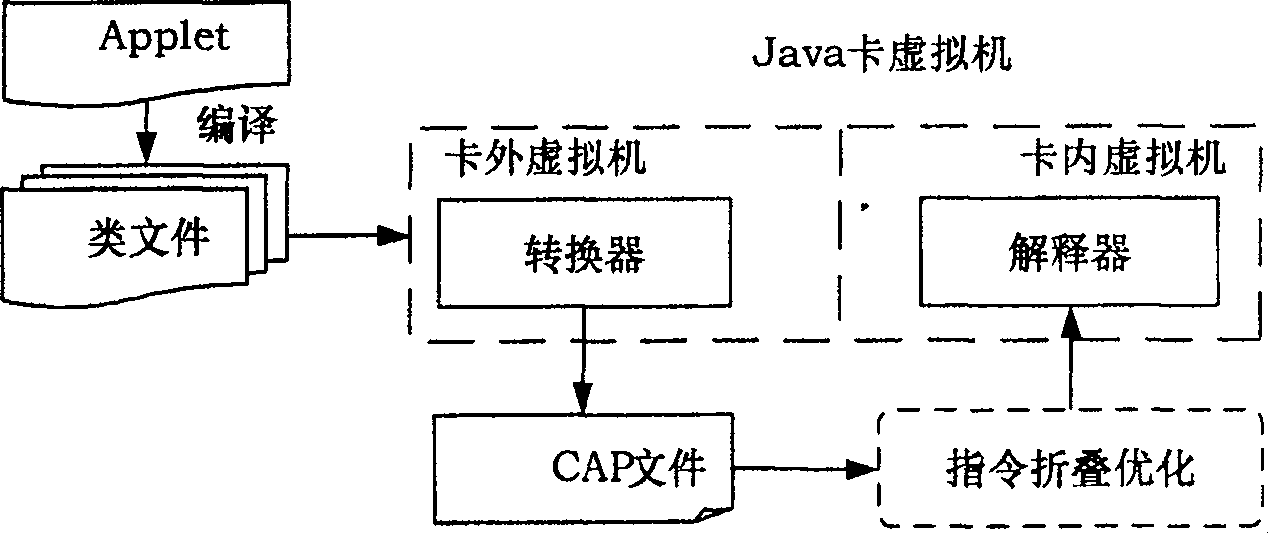
The invention discloses a method for controlling the safety environment of an intelligent card. The downloaded application program in the intelligent card generates byte code sequence of instruction set of a Java card virtual machine after complied and converted, and the byte code sequence is operated by the Java card virtual machine; the Java card virtual machine comprises an in-card virtual machine and an out- card virtual machine, where the out-card virtual machine converts the complied file to generate a CAP file and the in-card virtual machine executes the byte code sequence in the CAP file; in controlling the in-card safety environment, firstly delimiting the types of the byte code sequence outputted by the converter of the out-card virtual machine so as to obtain the first check type and the second check type; then adopting a check rule to make safety check on the said check types. On the basis of the structures of the in-Java card and out-Java card virtual machines, the invention has designed and implemented the generating method for the digital signature of elliptical curve and the out-card code certificate as well as the safety check of the in-card byte code sequence.
Owner:BEIHANG UNIV
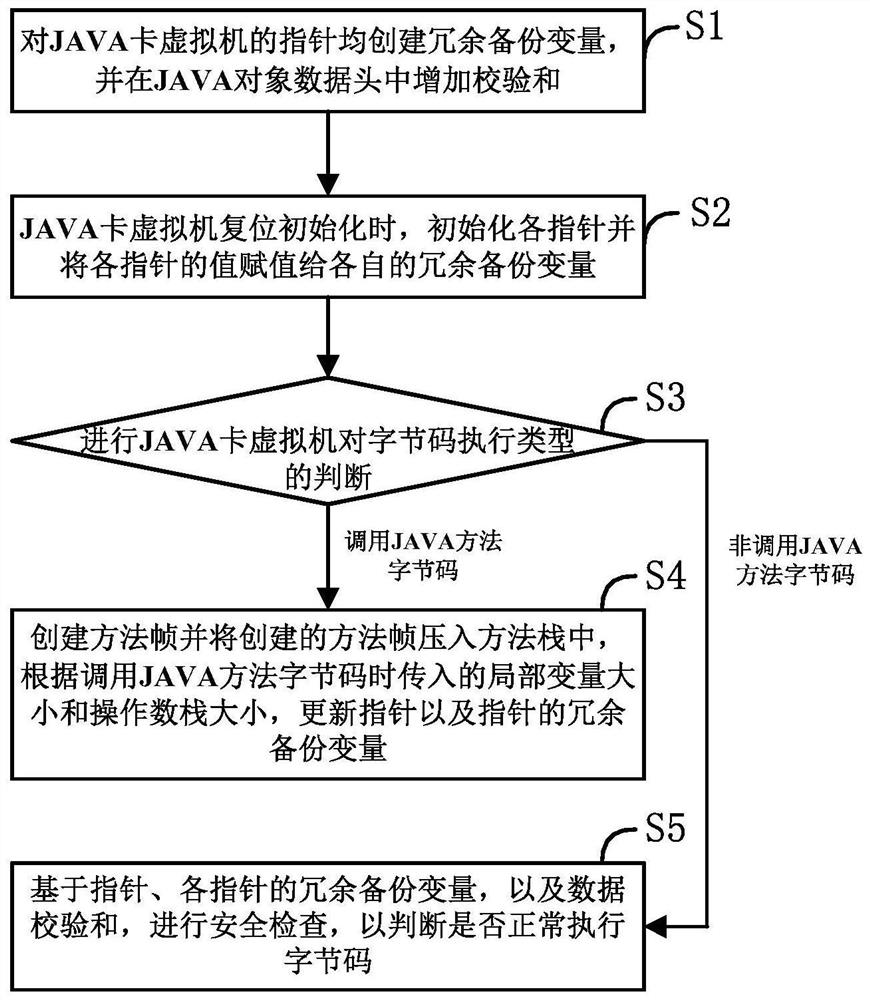
Security protection method for JAVA card virtual machine
PendingCN113434247ARealize redundant protectionImprove the protective effectPlatform integrity maintainanceSoftware simulation/interpretation/emulationSoftware engineeringChecksum
The invention discloses a security protection method for a JAVA card virtual machine, which relates to the technical field of intelligent cards and comprises the following steps of: creating redundant backup variables for pointers of the JAVA card virtual machine, and adding checksum in a JAVA object data head; when the JAVA card virtual machine is reset and initialized, initializing all pointers, and assigning values of all the pointers to respective redundant backup variables; carrying out the judgement of the execution type of byte codes by the JAVA card virtual machine: when the execution type is to execute the bytecode and operate stack data, and an execution object member accesses the bytecode or an execution method returns the bytecode, performing security check based on the pointers, the redundant backup variables of the pointers and the data checksum to judge whether the bytecode is normally executed or not. According to the method, the security protection capability of the virtual machine can be effectively enhanced, and the use security of the JAVA card virtual machine is enhanced.
Owner:WUHAN TIANYU INFORMATION IND
Method and system for optimizing java card virtual machine
ActiveCN105653351BImprove operational efficiencySoftware simulation/interpretation/emulationApplication softwareJava card virtual machine
The invention discloses a method and system for optimizing virtual machines of java cards. The method comprises the following steps: downloading a java card application program, wherein the java card application program is a cap package, and the cap package comprises components and a constant pool component which is used for indexing the components; in the downloading process of the java card application program, traversing the constant pool component in the cap package and carrying out a pre-operation so as to obtain target information corresponding to quotation information; backfilling the target information corresponding to the quotation information and an extended type structure into the constant pool component; and directly indexing the target information from the constant pool component through the modified structure by a java card application program interpreter. According to the method and system, a large number of internal skipping and external traversing are not required through the original method, so that the running efficiency of the java cards can be improved.
Owner:北京博思汇众科技有限公司
Multi-application Java smart card
ActiveCN102087716BMeet the requirements of the issuing partiesRecord carriers used with machinesSoftware simulation/interpretation/emulationProgrammable read-only memorySmart card
The invention discloses a multi-application Java smart card which comprises a Java Card virtual machine, a smart card operating system and a smart card chip. The multi-application Java smart card is characterized by further comprising a plurality of virtual cards mutually independent; each virtual card is corresponding to one application provider for providing application; each virtual card comprises a Card Manager for independently controlling the resource of the corresponding virtual card to provide the safety verification service of a terminal access corresponding to the virtual card; and each virtual card correspondingly manages the respective Electrically Erasable Programmable Read-Only Memory (EEPROM) for the content management of the virtual card. The smart card can realize that the issuer and the application provider of the smart card coexist on one physical card mutually and independently and have mutually equal status, thereby satisfying the requirement of each issuing party of co-branded cards.
Owner:WUHAN TIANYU INFORMATION IND
Java card realization method supporting digital signature
ActiveCN104331657AImprove securityDigital data protectionDigital data authenticationData informationDigital signature
The invention provides a java card realization method supporting digital signature, and belongs to the field of information security. The adopted method comprises the following steps that a java card virtual machine executes a called function according to a function calling instruction; through the execution of the first function, transmitted first data information is stored as a private key, a public key is calculated according to the private key, second data information and the public key are subjected to Hash calculation, the obtained Hash result is used as a first middle value, calculation mode information is stored as a signature mode, and the public key, the transmitted second data information and the first middle value are stored; a first vector value is updated through the execution of a second function; through the execution of a third function, a storage region is allocated, the first vector value and transmitted original data to be signed are subjected to Hash calculation to obtain a second middle value, the private key is obtained, the second middle value and the private key are signed, the obtained signature result is stored into the storage region, the length of the signature result is calculated, and the length of the signature result is returned.
Owner:FEITIAN TECHNOLOGIES
Program debugging method and device
ActiveCN103019941BRealize common debuggingSolve the convenienceSoftware testing/debuggingAdaptive responseJava card virtual machine
The invention provides a program debugging method and device, which relates to the field of software engineering. The problem that current debugging method is lower in debugging efficiency and maintenance convenience is solved. The method comprises the steps of: establishing a virtual thread of a Java card virtual machine; establishing a virtual character string object of the Java card virtual machine; and carrying out adaptive response of configuration information comprising the virtual character thread and the virtual character string object between the Java card virtual machine and a Java integrated debugging environment. The technical scheme provided by the invention is adaptive to synchronous debugging of Java language and C language, so that jointed debugging of virtual machine programs compiled by Java and C languages is realized.
Owner:DATANG MICROELECTRONICS TECH CO LTD
A Method of Object Management in Virtual Machine Based on Java Card
ActiveCN103116518BSave spaceEasy to operateMemory adressing/allocation/relocationSoftware simulation/interpretation/emulationManagement objectComputer-aided
The invention discloses an object management method based on a java card virtual machine. The object management method based on the java card virtual machine comprises that the java card virtual machine can detect an establishing object operation, and the basic information of the establishing object can be filled into a second memory space. An offset address of the to-be-established object can be obtained and stored in a blank table item of a sub object table. An index value of the to-be-established object can be calculated and used for replacing a first index value, wherein the first index value is stored. Deleting computer-aided production (CAP) image operation can be detected. A CAP image which is stored in a first memory space and corresponds to an identification (ID) of a deleting CAP image can be marked as a fragment. Types of assembly of the first memory space can be detected in sequence. When the type is the sub object table, the sub object table can be move to a high address direction. The offset address of the sub object table can be modified, wherein the sub object table is stored in a main object table. When the type is the CAP image, the CAP image can be moved to the high address direction and the CAP image address can be replaced. According to the object management method based on the java card virtual machine, a sub object and a main object can be used for managing objects so as to be easy and convenient. In addition, resources are saved.
Owner:FEITIAN TECHNOLOGIES
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com