Cache-based java card transaction processing method
A transaction processing and transaction technology, applied in the field of information security, can solve the problem of low performance of smart cards
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0134] The embodiment of the present invention provides a cache-based java card transaction processing method, including starting a transaction, executing a transaction, submitting a transaction, terminating a transaction and a power-down protection process, wherein executing a transaction includes an operation of reading data and an operation of writing data.
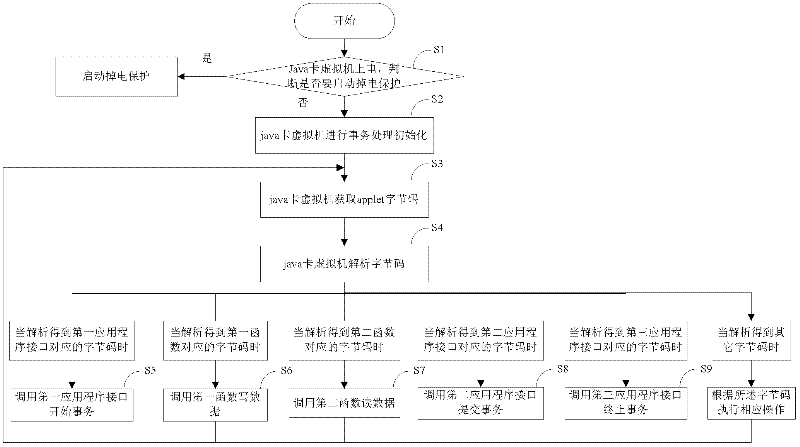
[0135] see figure 1 , the specific expression of the cache-based java card transaction processing method is as follows:
[0136] Step S1: Power on the java card virtual machine, judge whether to activate power-down protection, if so, activate power-down protection, execute step S3 after executing power-down protection, otherwise execute step S2;
[0137] Step S2: the java card virtual machine performs transaction processing initialization;
[0138] Specifically, in this embodiment, step S2 specifically includes: clearing the data in the second memory backup buffer and the new value buffer, setting the transaction proc...
Embodiment 2
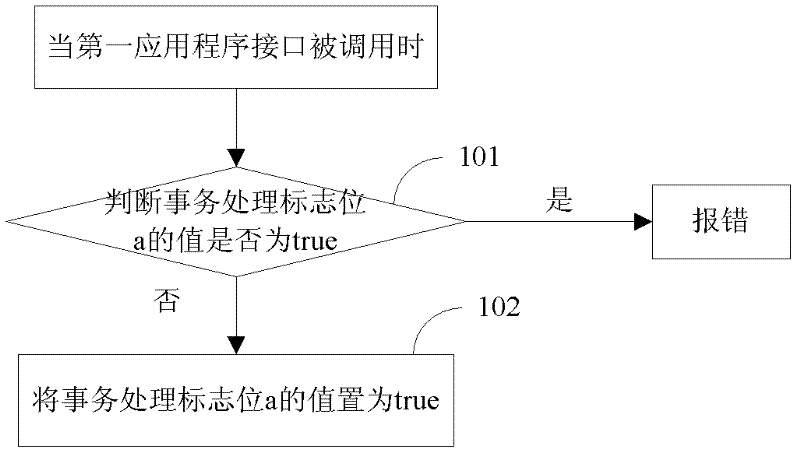
[0185] see figure 1 , in the transaction processing mechanism, the transaction starts when the first API is called, and the specific steps are as follows:
[0186] Step 101: When the first application program interface of the java card is called, judge whether the value of the transaction processing flag a is true, if yes, report an error, otherwise execute step 102;
[0187] Preferably, in this embodiment, the first application program interface is specifically a begin transaction (begintranscation) interface.
[0188] Step 102: Set the value of the transaction processing flag a to true.
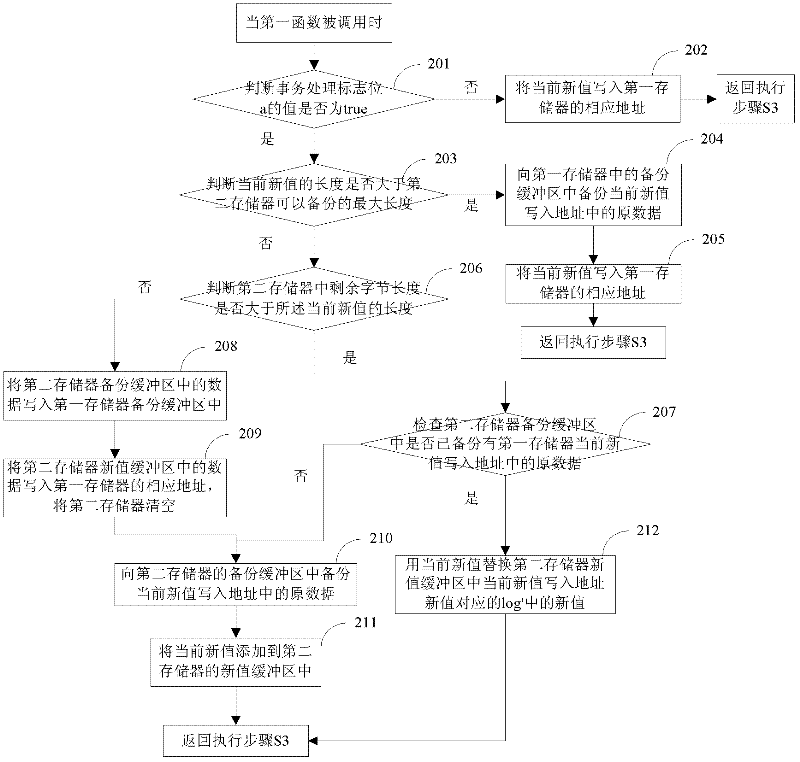
[0189] see figure 2 , in the transaction processing mechanism, when the first function is called, the write data operation is performed:
[0190] Step 201: When the first function is called, judge whether the value of the transaction flag a is true, if yes, execute step 203, otherwise execute step 202;
[0191] Preferably, in this embodiment, the first function is specifically a write ...
Embodiment 3
[0282] see Figure 7 In the embodiment of the present invention, the first new value is written to the address starting at 0x4000 in the first memory, the second new value is written to the address starting at 0x4050 in the first memory, and the second new value is written to the address starting at 0x4200 in the first memory. A cache-based Java transaction processing method flow is provided as an example for writing the third new value in the starting address, wherein the first new value is 40 bytes of data (5, 6, 7, 8. .., 45), the second new value is 90 bytes of data (5, 6, 7, 8, ..., 95), and the third new value is 130 bytes of data (5 , 6, 7, 8, ..., 135), the size of the first memory backup buffer is 2560 bytes, the size of the second memory backup buffer is 128 bytes, the size of the second memory new value buffer The size is 128 bytes.
[0283] Specific steps are as follows:
[0284] 1. Call the first API to start the transaction;
[0285] 2. Call the first functio...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com