Boundary checking method of JAVA card frame
A border check and card frame technology, applied in the field of smart cards, can solve problems such as illegally obtaining card storage data, and achieve the effect of improving security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0018] The present invention will be further described below in conjunction with the accompanying drawings and specific embodiments.
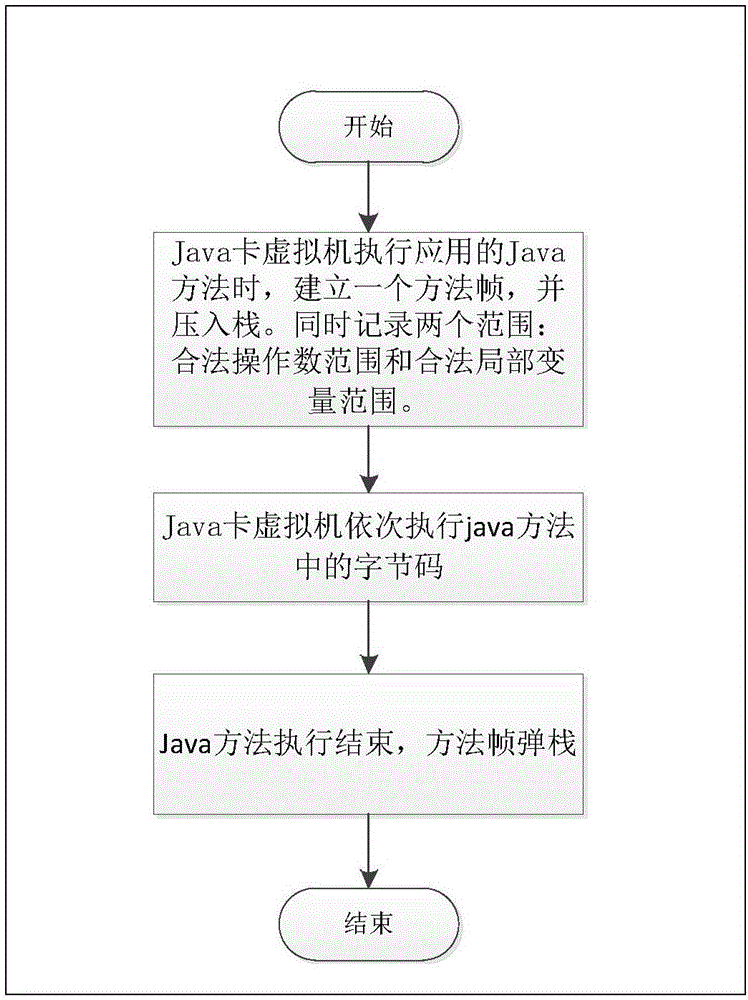
[0019] figure 1 It points out the execution flow of a java method on the java card virtual machine. When the Java Card virtual machine executes the method, it will create a method frame for it, push it onto the stack, and record the start address of the method frame. Two ranges are recorded at the same time: the legal operand range and the legal local variable index range. Then execute the bytecode in the java method in turn. Until the execution of the java method ends, the method frame is popped from the stack.
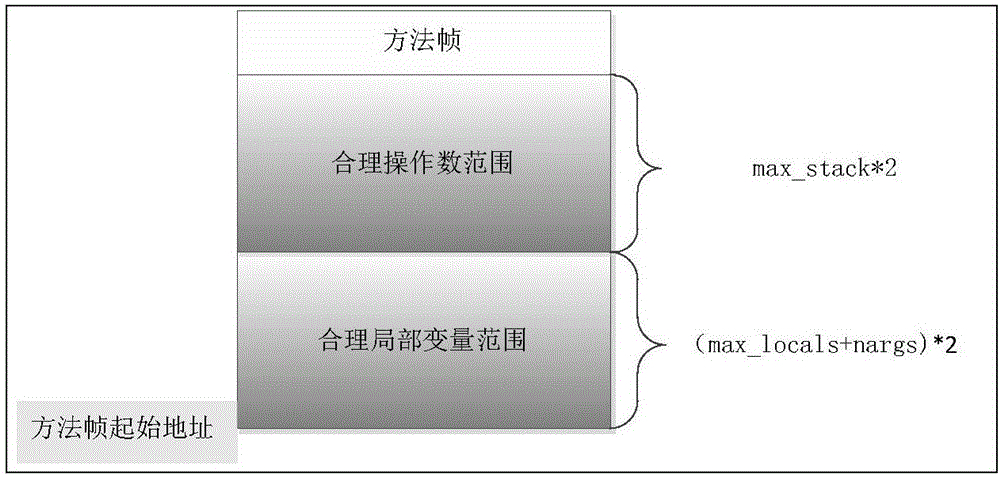
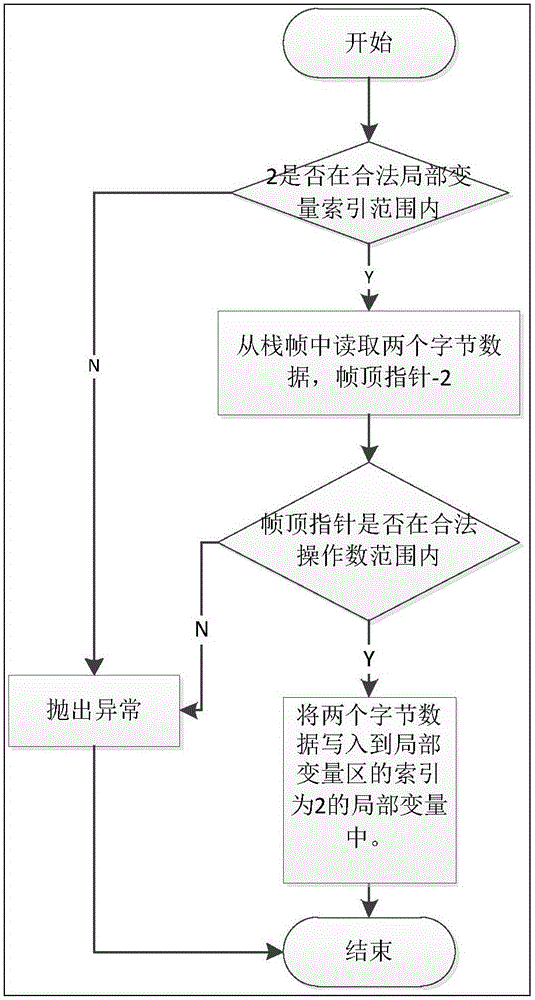
[0020] figure 2 A schematic diagram of where the legal operand ranges and the legal local variable index ranges are indicated. Starting from the start address of the method frame is the local variable area. Therefore, the legal range of local variables is from the start address of the method frame to ((max_locals+nargs)*2). Th...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com