Terminal security access control method
A technology for access control and terminal security, applied in transmission systems, electrical components, etc., can solve problems such as lack of access control and failure to eliminate potential safety hazards in time
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
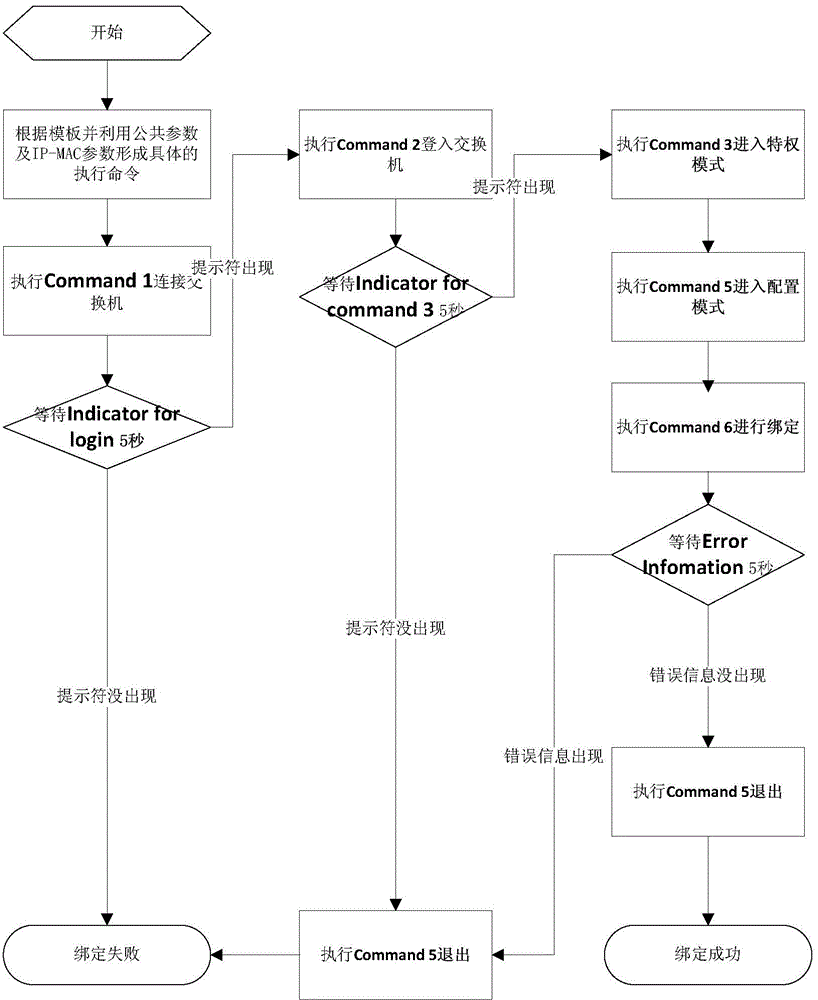
[0083] Embodiment: Switch operation method based on command template
[0084] In order to support the ARP table control of various models of switches from different manufacturers, this method analyzes the operation modes of various models of switches from Cisco, Huawei, H3C and Nortel, and provides a switch ARP table operation based on command templates method. The method establishes a general exchange ARP table operation command sequence template, adapts parameters to different types of exchanges, obtains specific exchange execution commands, and completes the operation on the ARP form through a telnet or SSH channel.
[0085] 1. Template definition
[0086] The ARP table operation command sequence that this method adopts is as follows:
[0087] command serial number
Excuting an order
illustrate
①
connect
Use telnet or ssh to connect to the switch
②
password input
Enter switch password
③
privileged mode
Enter ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com