Free stream trading system and free stream trading method for guaranteeing information security of on-board tag
A technology of information security and on-board tags, which is applied in transmission systems, electrical components, instruments, etc., can solve problems such as illegal use of on-board tags, and achieve the effect of ensuring information security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
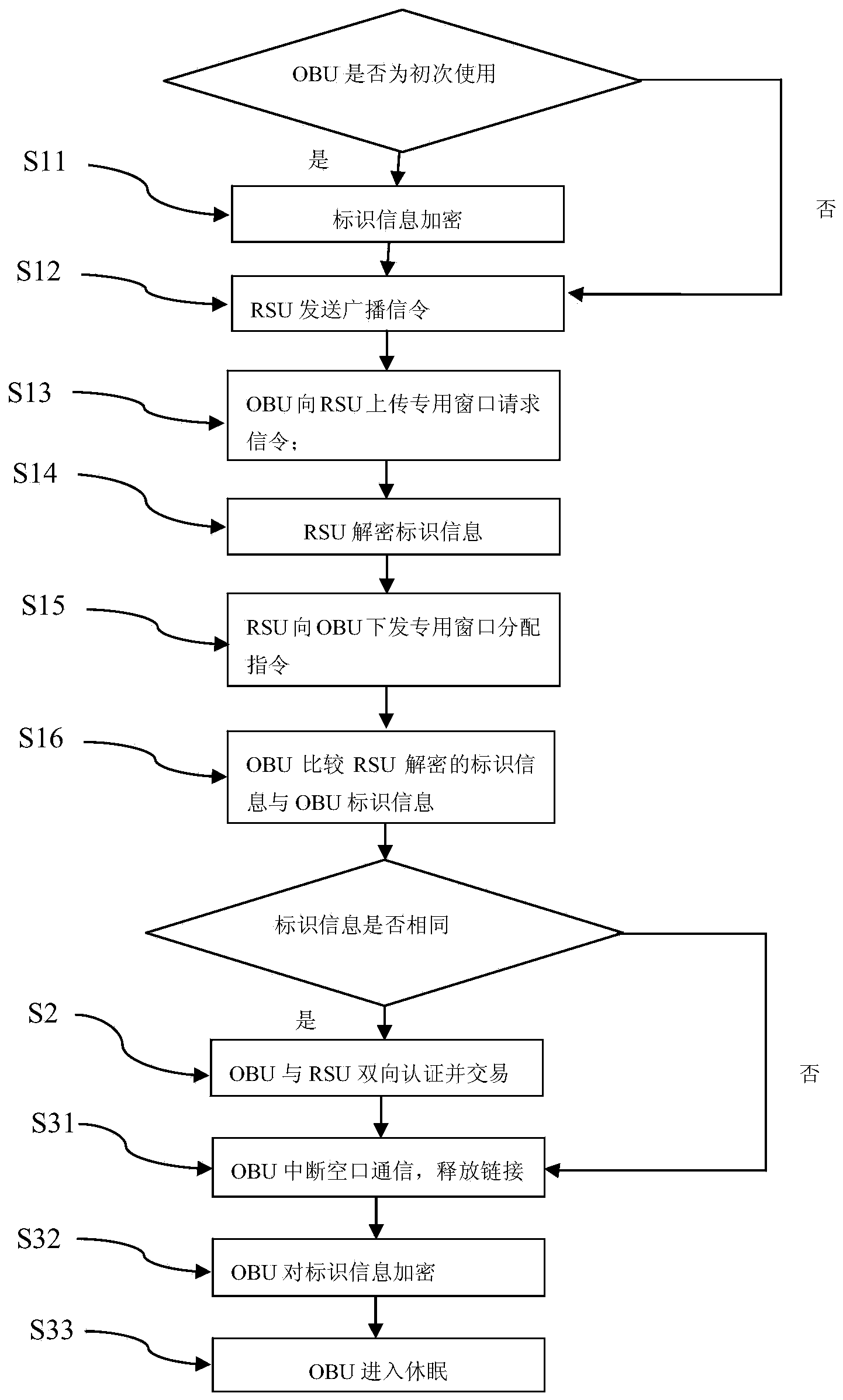
[0042] The invention provides a free flow transaction system and method for ensuring the security of vehicle label information.
[0043] like figure 1 As shown, a free flow transaction method to ensure the security of vehicle label information includes the following steps:
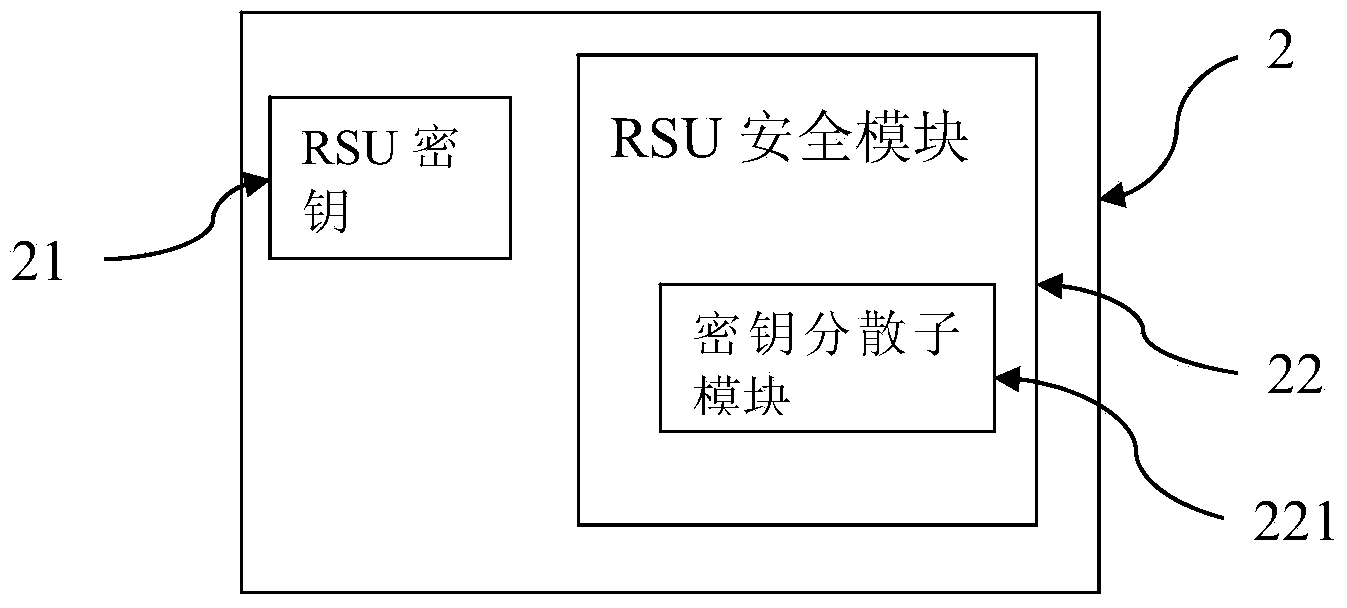
[0044] S1. The roadside unit RSU2 allocates a dedicated uplink window to the on-board unit OBU1;
[0045] S2. OBU1 and RSU2 two-way authentication and transaction;
[0046] S3. RSU2 releases the link with OBU1.
[0047] S1 includes the following steps:
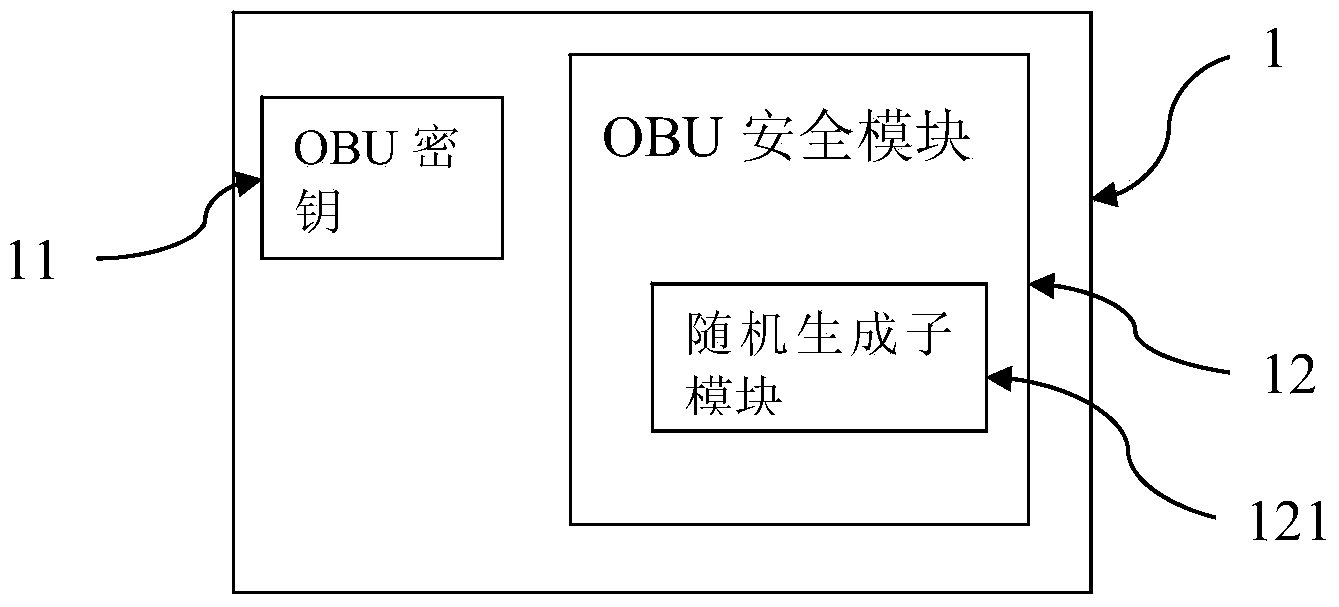
[0048] S11. If the OBU1 is used for the first time, the OBU security module 12 on the OBU1 uses the OBU key 11 to encrypt the identification information containing the OBU1 unique identifier OBUID and a group of random numbers to generate ciphertext;
[0049] S12.RSU2 sends broadcast signaling;
[0050] S13. After receiving the broadcast instruction from the RSU2, the OBU1 uploads the dedicated window request signaling carrying the ciphertext to the R...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com