Encryption method and device and terminal
An encryption method and technology of an encryption device, applied in the field of communication, can solve problems such as low security and single encryption key, and achieve the effect of enhancing security and avoiding simplification
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
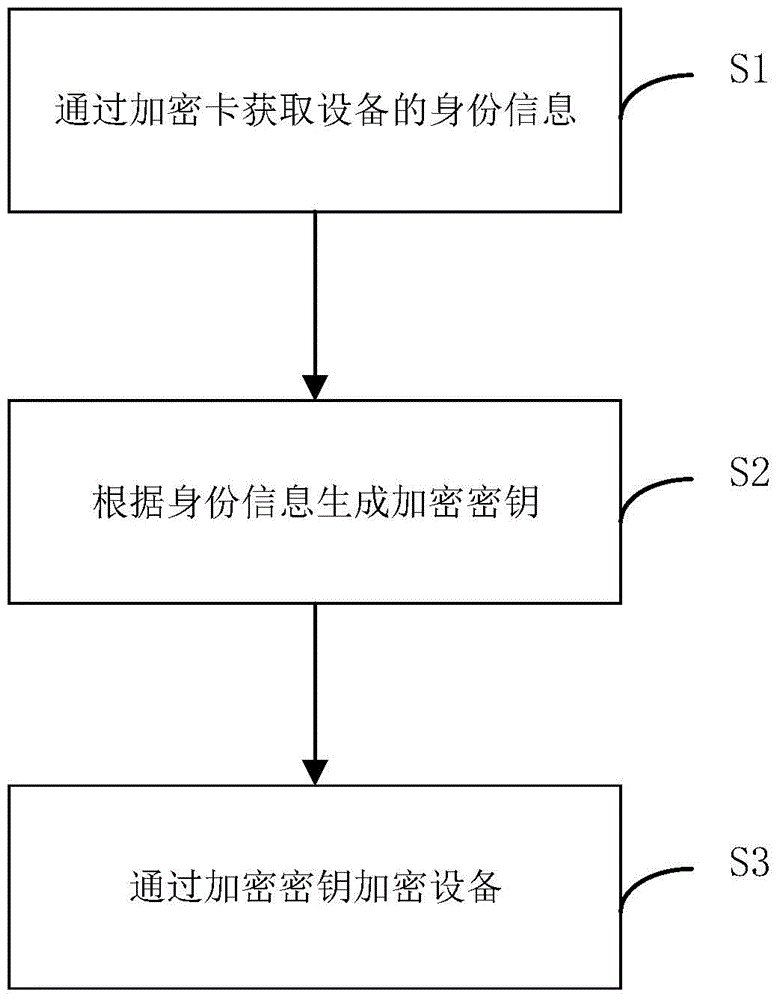
[0055] figure 1 It is a flow chart of the encryption method proposed by the present invention. The method includes:
[0056] S1, obtain the identity information of the device through the encryption card.
[0057] Specifically, the encryption card used in this embodiment is equipped with independent functional modules, such as a microprocessor module, an encryption module, a decryption module, a communication module, and a storage module. The encryption card used in this embodiment may be the same size as the SD memory card of the smart device, compatible with the SD card slot and the corresponding interface. The encryption card used in this embodiment may also be a card with a specific size and a specific interface.
[0058] Specifically, a device using the encryption card for unlocking operation is provided with a card slot matching the encryption card. It can be understood that an interface contact piece or an interface pin for establishing a communication link with the ...
Embodiment 2
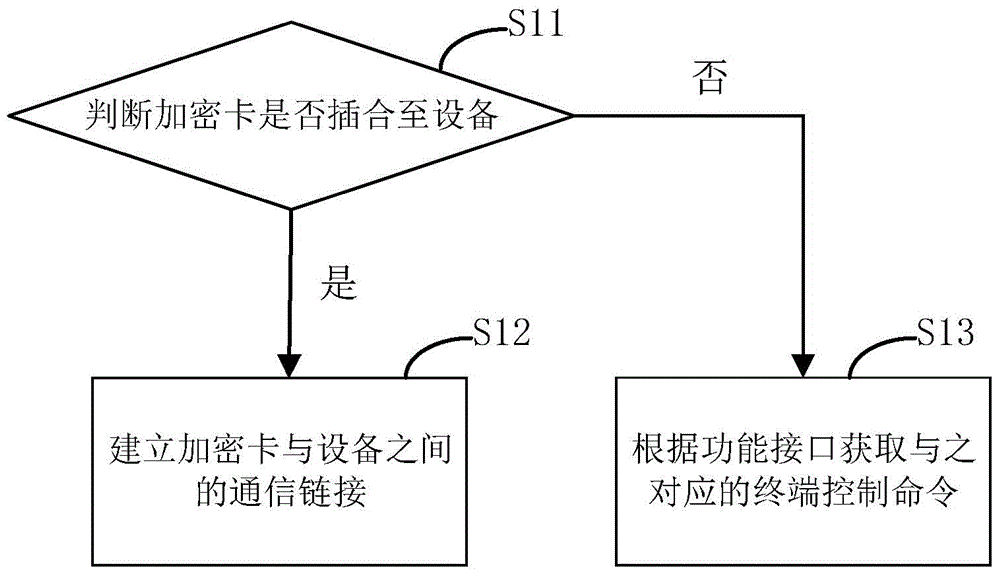
[0072] figure 2 It is a flow chart of the encryption method proposed by the second preferred embodiment of the present invention. Based on the above embodiment, obtaining the identity information of the device through the encryption card further includes:
[0073] S11, judging whether the encryption card is inserted into the device. Whether the encryption card is inserted into the device is judged by the interface contact piece or the interface pin set in the card slot that establishes the communication link with the encryption card. Valid connection range.
[0074] S12, if the encryption card has been inserted into the device, establish a communication link between the encryption card and the device. It can be understood that the communication link between the encryption card and the device may be an NFC communication link, a Bluetooth communication link, a WiFi communication link, or the like.
[0075] S13, if the encryption card is separated from the device, clear the ...
Embodiment 3
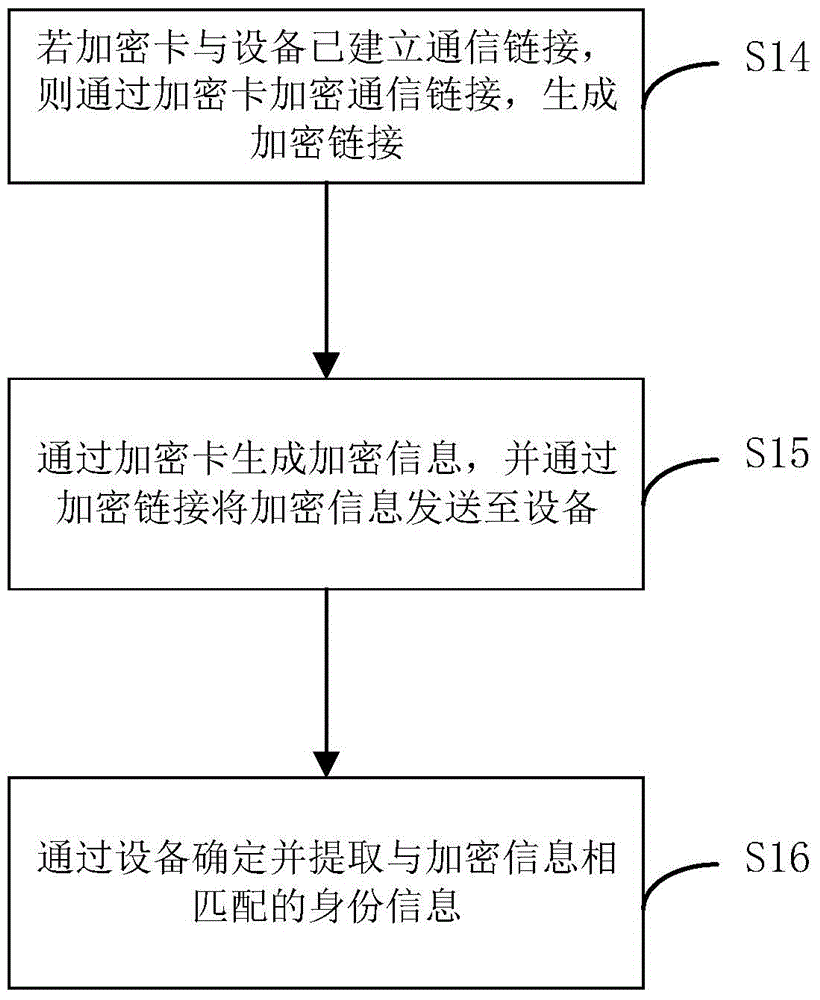
[0078] image 3 This is a flow chart of the encryption method proposed by the third preferred embodiment of the present invention. Based on the above embodiment, acquiring the identity information of the device through the encryption card further includes:
[0079] S14, if a communication link has been established between the encryption card and the device, the communication link is encrypted by the encryption card to generate an encrypted link.
[0080] It can be understood that the encryption module is not set on the device side, but the encryption module is built into the encryption card. The beneficial effect of this is that the encryption module operates independently, so that the encryption key generated by the encryption card exists independently and is not disturbed. At the same time, other devices do not have the right to read the encryption card, thus ensuring the security of the encryption card.
[0081] Further, by encrypting the communication link between the en...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com