Method and system for identifying network attack
A technology for identifying network and attacking data, which is applied in the field of communication, and can solve problems such as network security products and methods are difficult to deal with, difficult to operate and maintain, and huge business traffic
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0021] In order to make the purpose, technical solutions and advantages of the embodiments of the present invention clearer, the present invention will be further described in detail below in conjunction with the accompanying drawings.
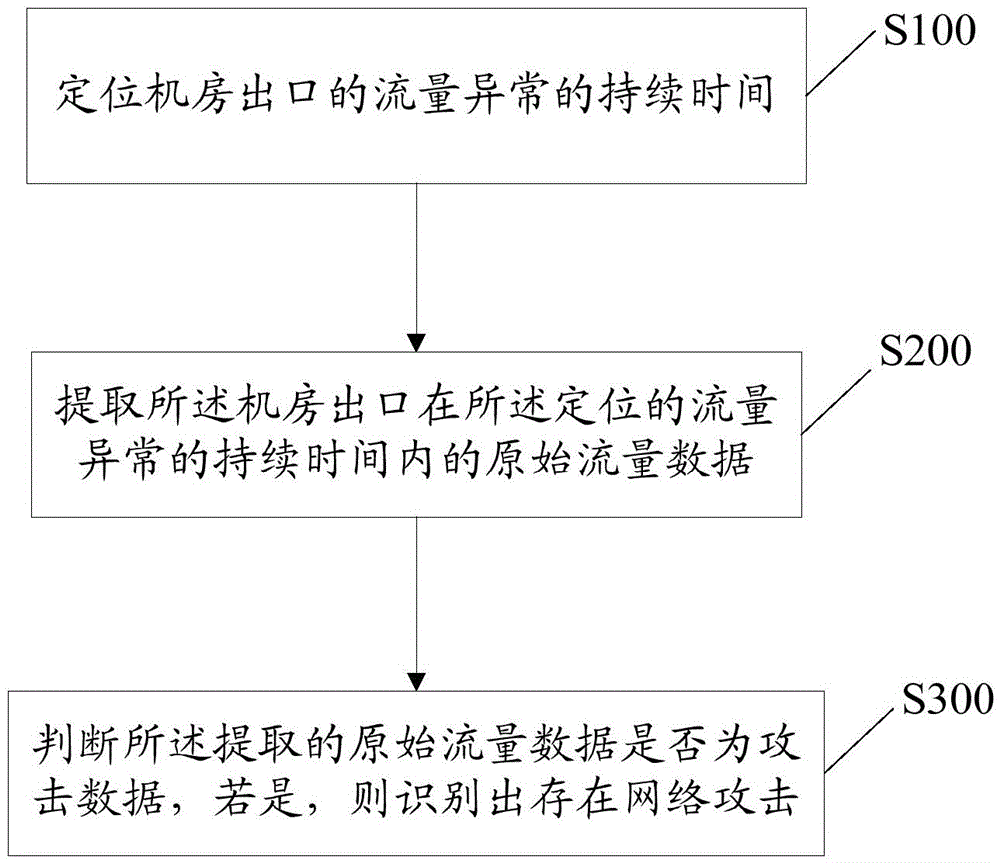
[0022] figure 1 is a flowchart of a method for identifying a network attack according to an embodiment of the present invention. see figure 1 , the method includes:
[0023] S100: Locate the duration of abnormal flow at the exit of the equipment room.
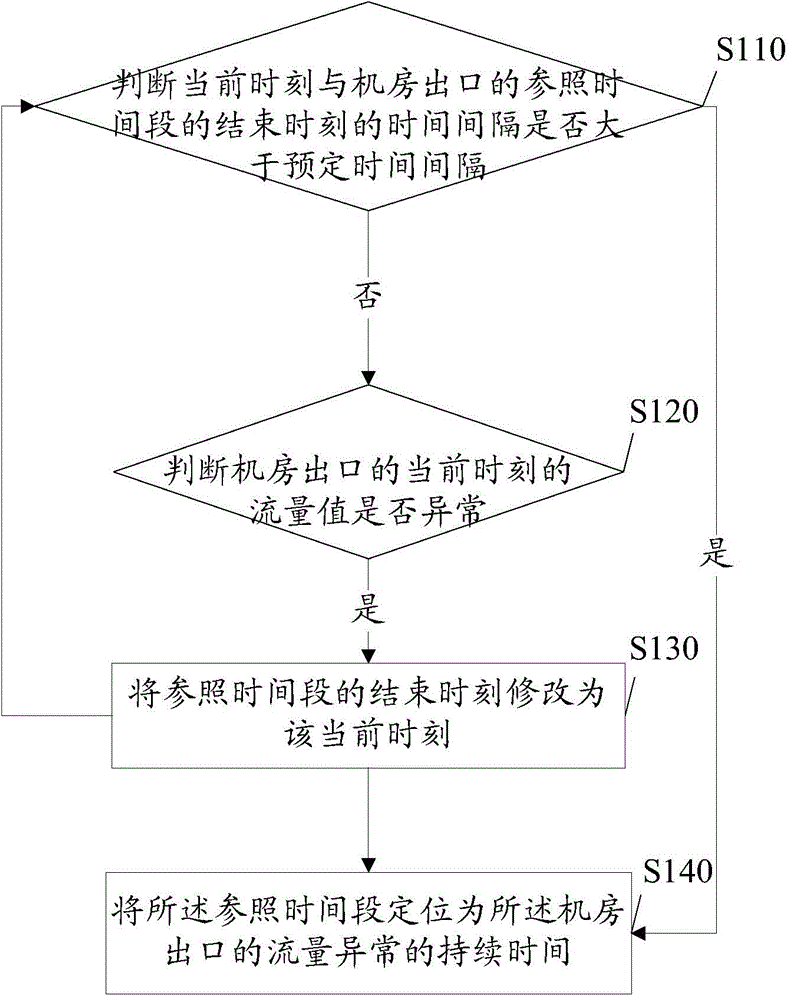
[0024] Among them, such as figure 2 As shown, in the implementation manner of the present invention, step S100 can be realized through the following steps:
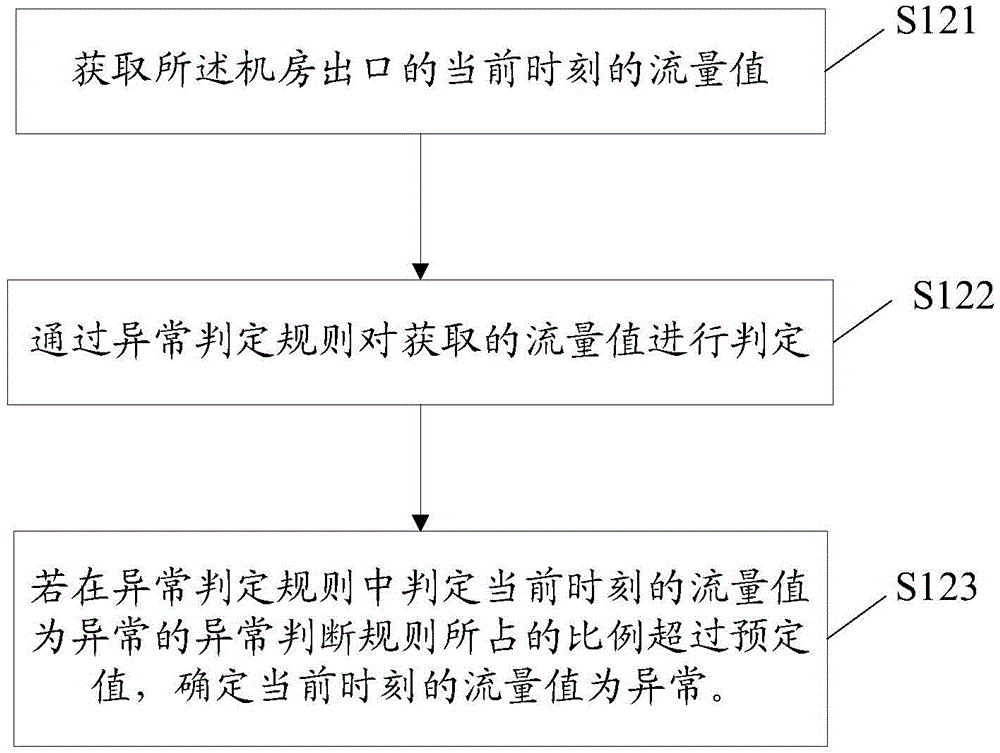
[0025] S110: Judging whether the time interval between the current time and the end time of the reference time period (abnormal time period closest to the current time in the time dimension) of the exit of the computer room is greater than a predetermined time interval (such as 10 minutes, certainly not limited thereto, according to ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com