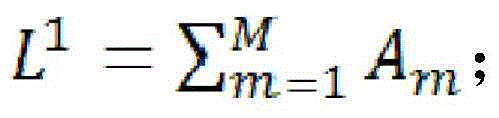Method for authenticating identity of mobile terminal and constructing safety channel
A security channel and identity authentication technology, which is applied in the field of mobile identity authentication and secure channel establishment, can solve the problems of cumbersome generation and distribution of public and private keys, and achieve high effectiveness and prevent attacks
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0051] The present invention will be further described in detail below in conjunction with the examples.
[0052] The present invention comprises the following steps: step 1) identity authentication,
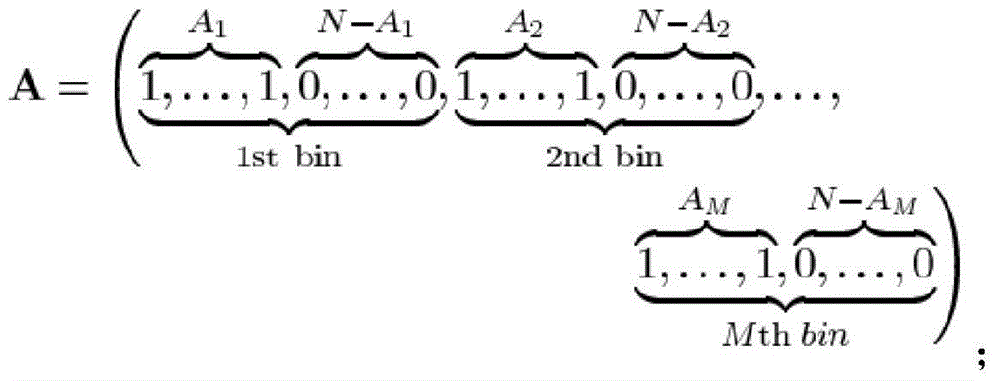
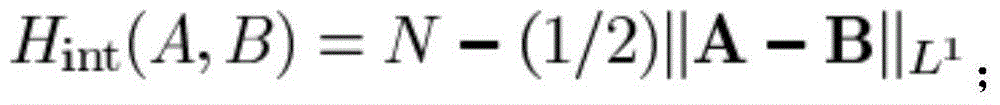
[0053] The two sides of the data transmission use the front and rear cameras of the smart terminal to shoot each other, extract the feature values of the image captured by the front camera of the first user and the image captured by the rear camera of the second user, and perform the first image matching. When the matching is successful; When the first image matching is successful, the second matching is performed: the two sides of the data transmission switch the front and rear cameras to shoot each other, and respectively extract the feature values of the second image captured by the smart terminals of both parties for the second image matching. When the matching is successful, then Go to the next step. Image feature values can be grayscale or brightness.
[0054] Iden...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com