Authentication method, device and system
A technology of identity authentication and authentication server, applied in the field of devices and systems, and identity authentication methods, can solve problems such as poor security, insecure user accounts, and easy malicious use by others, so as to improve security and authentication efficiency effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
no. 1 example
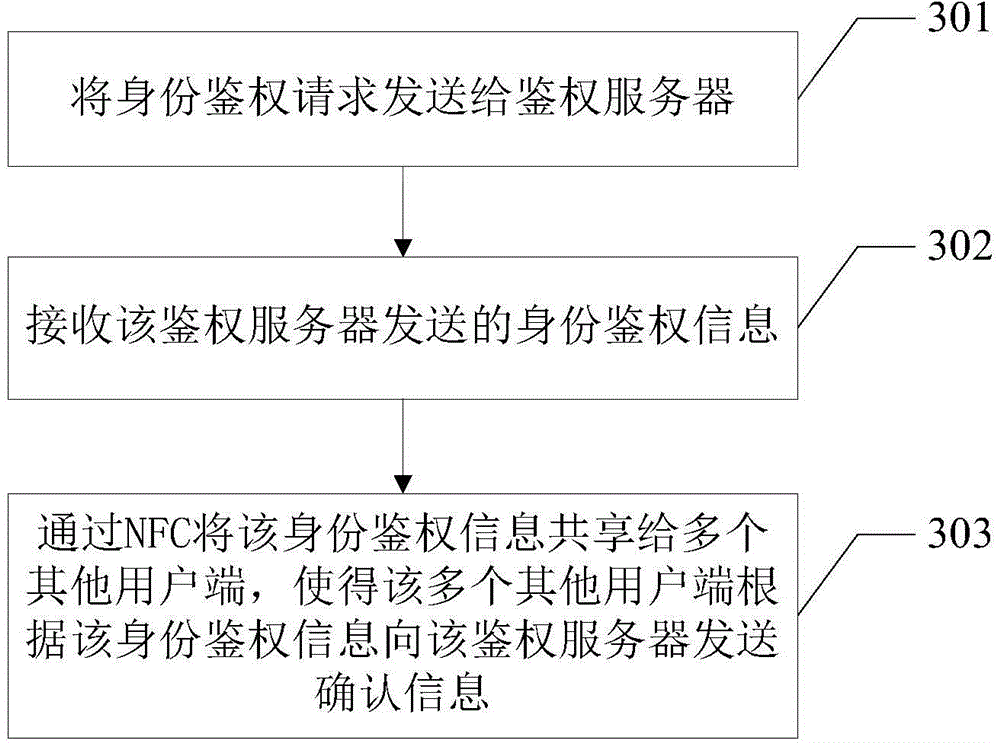
[0050] refer to image 3 , the method of this embodiment includes the following steps:
[0051] Step 301, sending the identity authentication request to the authentication server;
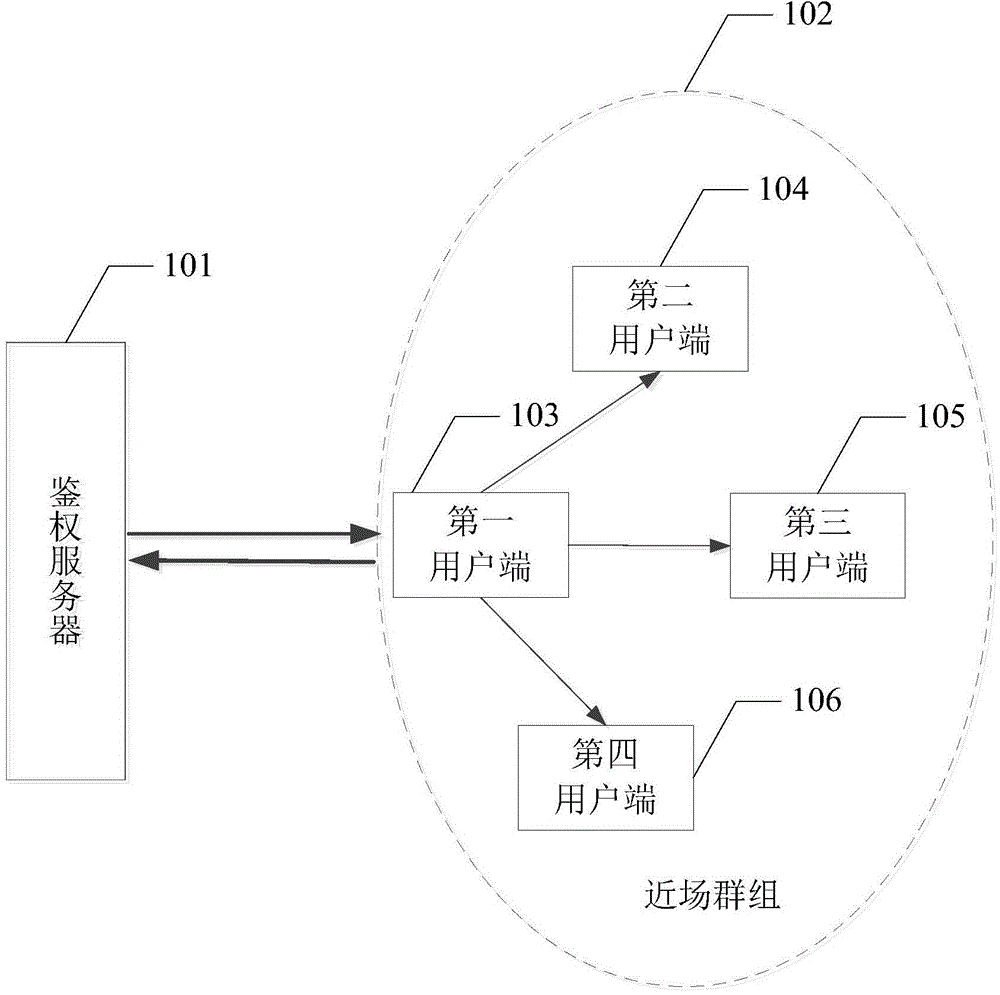
[0052] When the user wants to obtain a certain authorization, he needs to request the authorization from the authentication server 101, and after receiving the user's request, the first client 103 sends the identity authentication request to the authentication server 101, and requests the authentication server 101 to The user side performs identity authentication.
[0053] Step 302, receiving the identity authentication information sent by the authentication server;
[0054] After the authentication server 101 receives the identity authentication request sent by the first client 103, it sends identity authentication information to the first client 103, and the identity authentication information may be to request the authenticator to return a confirmation for identity authentication information,...
no. 2 example
[0059] see Figure 4 , Figure 4 is a schematic diagram of the second embodiment of the identity authentication method in the embodiment of the present invention, and image 3 The difference of the first embodiment of the shown identity authentication method is that, in step 303, sharing the identity authentication information to multiple other clients via NFC includes:
[0060] Step 403, identifying the target client end with the NFC function turned on;
[0061] After the first user terminal 103 enables the NFC function, it can identify a target user terminal with the NFC function enabled, and the target user terminal is the user terminal with the NFC function enabled.
[0062] Step 404, establishing a client group for all identified target clients;
[0063] Within a certain distance, the first user terminal 103 can identify multiple target user terminals through NFC, and establish a user terminal group for all the identified target user terminals. For example, if the cli...
no. 3 example
[0068] see Figure 5 , Figure 5 is a schematic diagram of the third embodiment of the identity authentication method in the embodiment of the present invention, and image 3 The difference of the first embodiment of the identity authentication method shown is that this embodiment may further include:
[0069] Step 504, sending confirmation information for identity authentication to the authentication server for user identity authentication.
[0070] The first client terminal 103 sends confirmation information for identity authentication to the authentication server 101 for user identity authentication.
[0071] The execution sequence of step 504 in this embodiment is not limited by the description of the embodiment, and may be executed before sharing the identity authentication information with multiple other client terminals through NFC.
[0072] In the embodiment of the present invention, a user terminal shares the identity authentication information sent by the authenti...
PUM
 Login to view more
Login to view more Abstract
Description
Claims
Application Information
 Login to view more
Login to view more - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap