A Location Privacy Preservation Method Based on False Location and Geometry in Location Services
A location service and fake location technology, applied in the field of information security, can solve the problems of not considering the correlation between location and query content and query time, slow convergence speed, and inability to apply anonymity, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
[0050] This embodiment specifically adopts the following technical solutions:
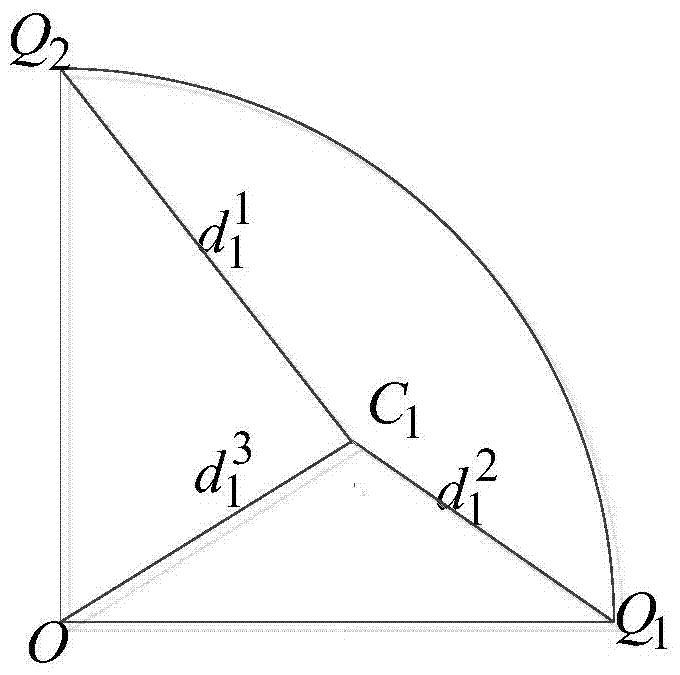
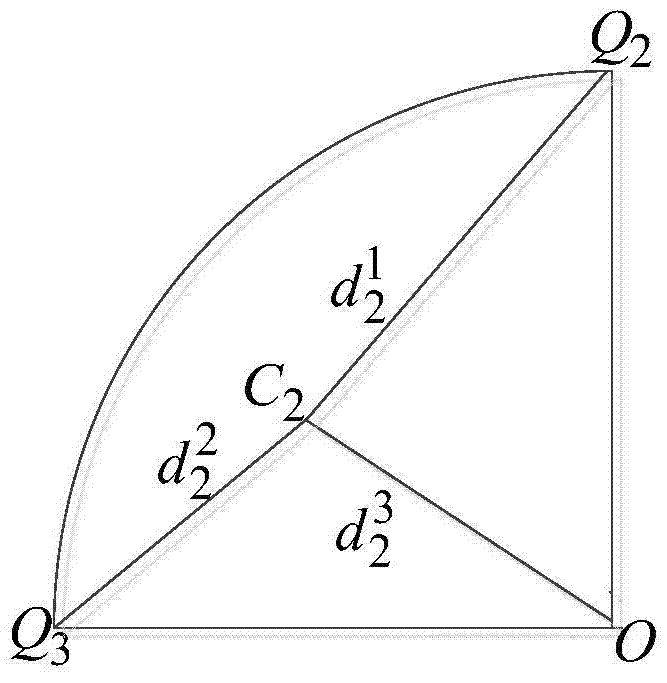
[0051] A location privacy protection method based on pseudo location and geometry in location services, the specific process is as follows figure 1 shown, including the following steps:
[0052] Step 1. Initialization: In this method, the LBS server is a service provider, which stores the database of all services and is responsible for updating service data; when the user sends an LBS service request, the LBS server is responsible for receiving the user's service query request, and in the database Search for the corresponding service data in , and then feed back the search results to the user;
[0053] At the same time, in the area served by the LBS server, the LBS server is responsible for classifying each location according to its location attributes (such as restaurants, shopping malls, schools, etc.) The historical request probability of each location), and the LBS server can publish the hist...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com