Decision method for access control and equipment
An access control strategy and access control technology, applied in the field of communication
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
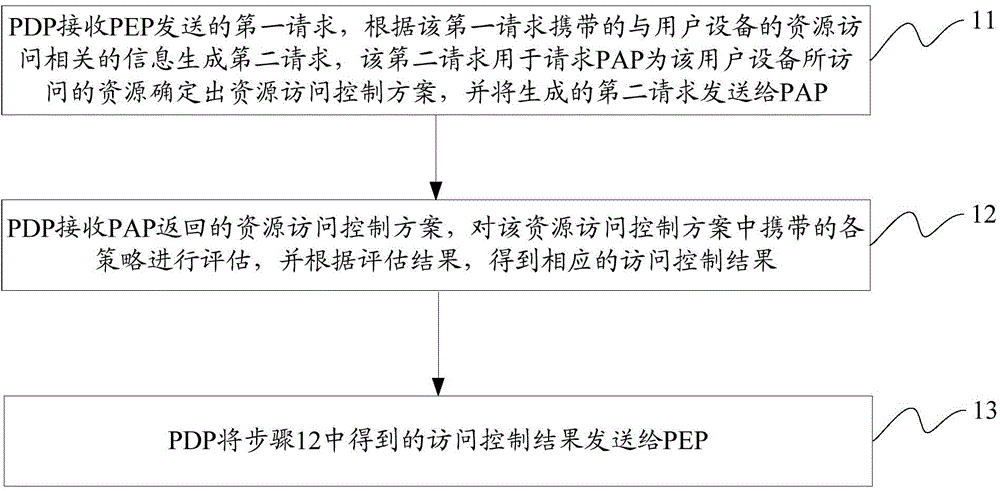
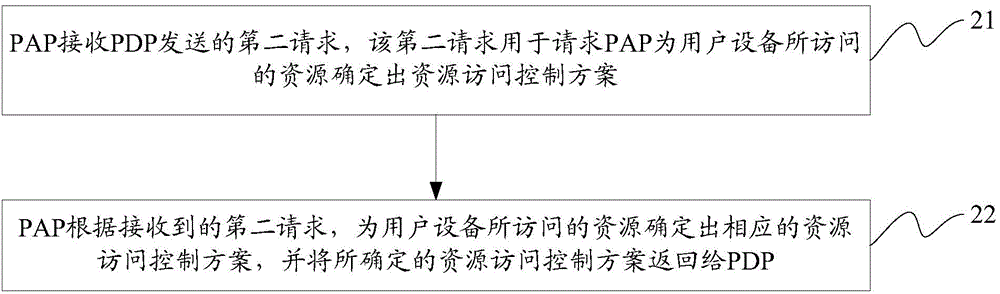
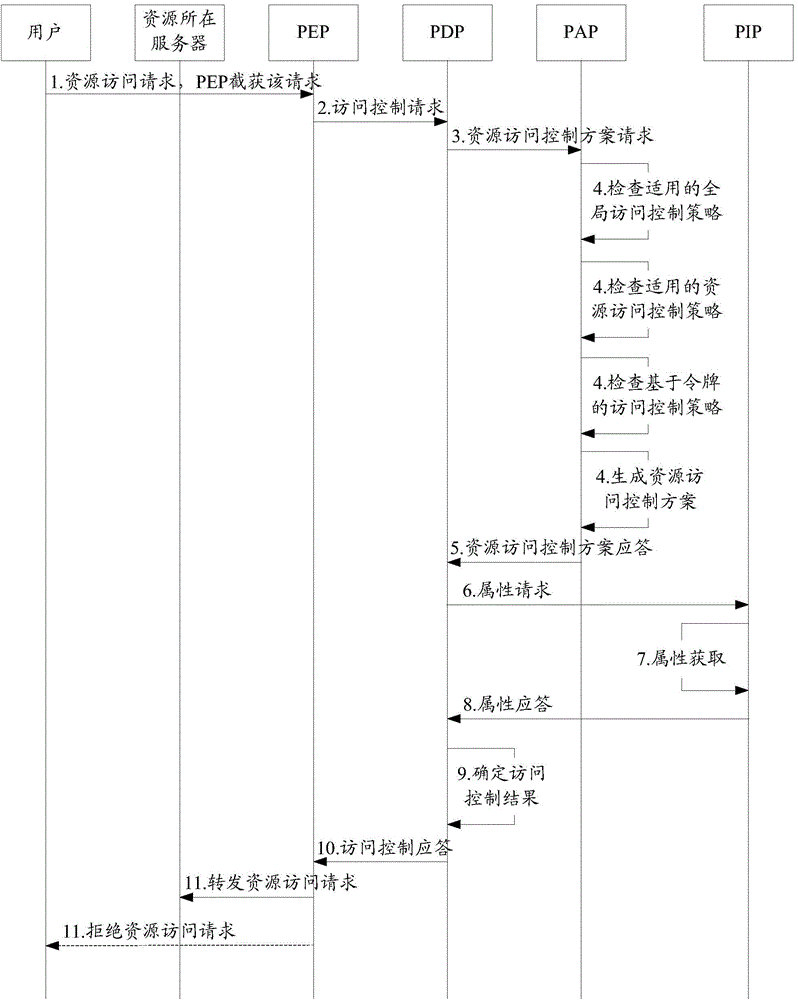
[0252] Embodiment 1. This embodiment will cover three methods of policy acquisition in practical applications: (1) Acquisition is used by an access control system (that is, a system including PEP, PDP, PAP, PIP, etc.) decision) centrally managed global access control policy, (2) obtain the resource access control policy directly associated with the resource accessed by the visitor (that is, the user device), (3) obtain the resource access control policy carried in the access control token provided by the visitor The access control policy related to this resource access.
[0253] In this embodiment, three different policy description methods will be used to describe three different access control policies respectively, and how to deal with the evaluation and integration of heterogeneous policies will be introduced accordingly.
[0254] The application scenarios of this embodiment are as follows:
[0255] The address of the resource in the oneM2M system that the user Alice requ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com