Information processing method, client, and server
An information processing method and server technology, applied in electrical components, transmission systems, etc., can solve the problems of inability to perform authentication normally, the authentication process is time-consuming, and the authentication response is not timely enough, so as to reduce the pressure on servers and bandwidth costs, Time-saving, highly reliable results
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
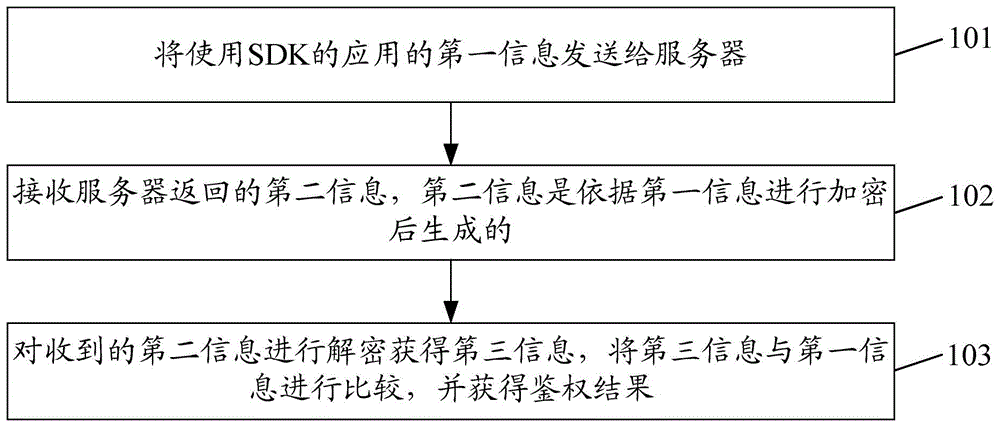
[0063] An information processing method provided by Embodiment 1 of the present invention is applied to a client requesting to use the SDK, such as: a client of a third-party application developer requesting to use the SDK, etc.; figure 1 As shown, the method mainly includes:
[0064] Step 101, sending the first information of the application using the SDK to the server; wherein, the first information is used to uniquely identify the application, and the first information is used by the server to determine the legality.
[0065] Since the method in Embodiment 1 of the present invention is applied to a client requesting to use the SDK, step 101 can also be described as: the client sends the first information of its own application using the SDK to the server.
[0066] Every application that needs to use the SDK must pass the authentication of the authentication system, and the authentication needs to provide the first information of the application.
[0067] In a preferred emb...
Embodiment 2
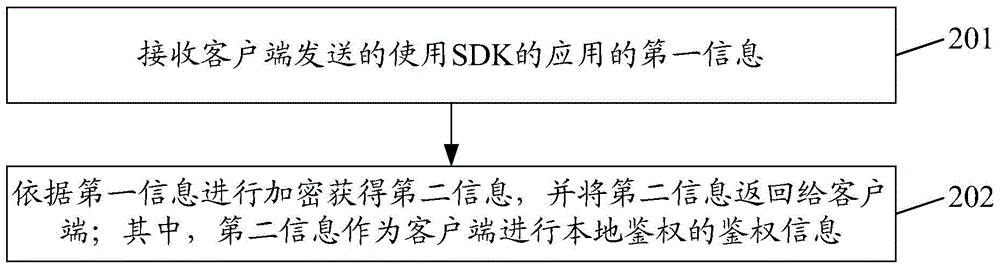
[0110] An information processing method provided by Embodiment 2 of the present invention is applied to the background server of the SDK provider, such as figure 2 As shown, the method mainly includes:
[0111] Step 201, receiving the first information of the application using the SDK sent by the client; wherein, the first information is used to uniquely identify the application, and the first information is used as the basis for the server to determine the legality of the application .
[0112] Since the method in Embodiment 1 of the present invention is applied to the background server of the SDK provider, step 201 can also be described as: the server receives the first information of the application using the SDK sent by the client.
[0113] Every application that needs to use the SDK must pass the authentication of the authentication system, and the authentication needs to provide the first information of the application to the background server of the SDK provider.
[...
Embodiment 3
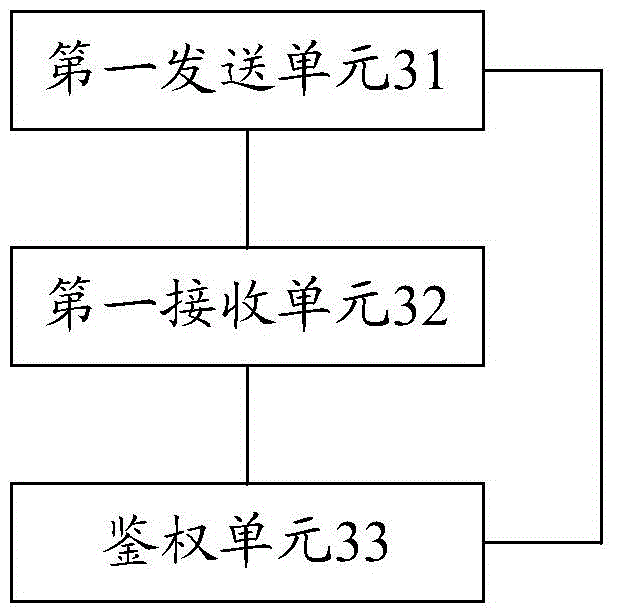
[0138] Corresponding to the method in Embodiment 1 of the present invention, Embodiment 3 of the present invention also provides a client, such as image 3 As shown, it mainly includes: a first sending unit 31, a first receiving unit 32 and an authentication unit 33; wherein,
[0139] The first sending unit 31 is configured to send the first information of the application using the SDK to the server; wherein, the first information is used to uniquely identify the application, and the first information is used by the server to perform legal sex identification;
[0140] The first receiving unit 32 is configured to receive the second information returned by the server when the first information is determined to be legal, and the second information is generated after being encrypted according to the first information; wherein, the second information is used as a client local authentication;
[0141] The authentication unit 33 is configured to decrypt the received second informat...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com