Controlling a mobile device in a telecommunications network
A technology for telecommunications networks and telecommunications equipment, applied in electrical components, wireless communications, electrical digital data processing, etc., can solve problems such as heavy, uncertain mobile phones that can be trusted, and equipment that cannot be trusted, and achieve the effect of reducing time
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
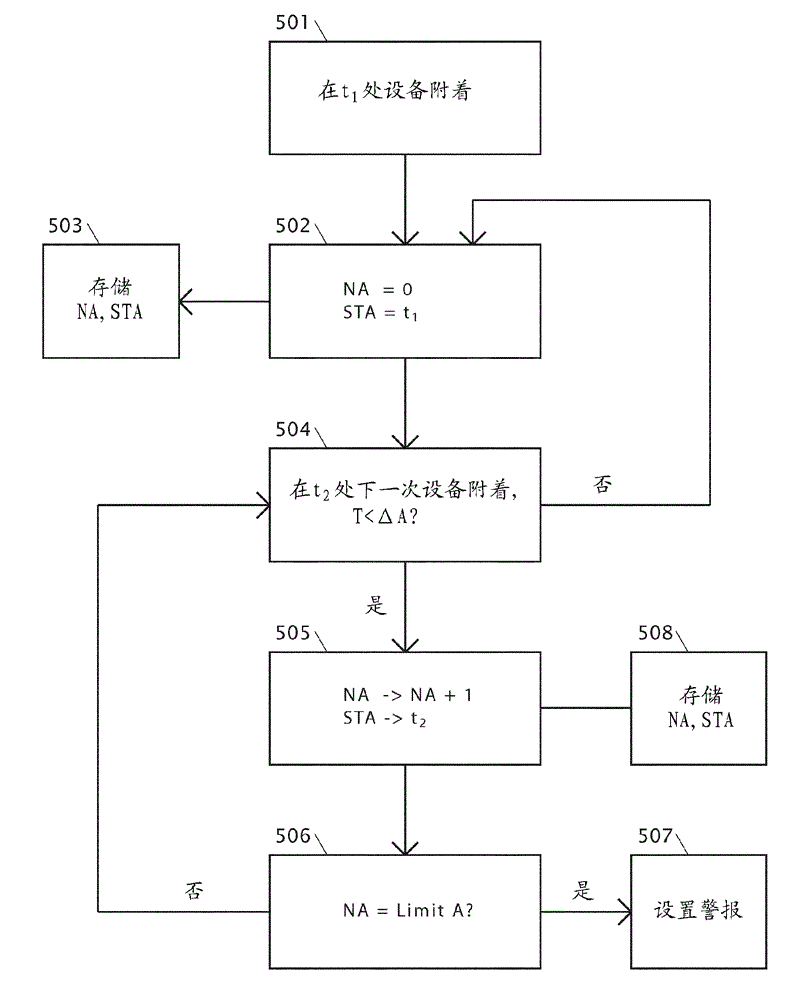
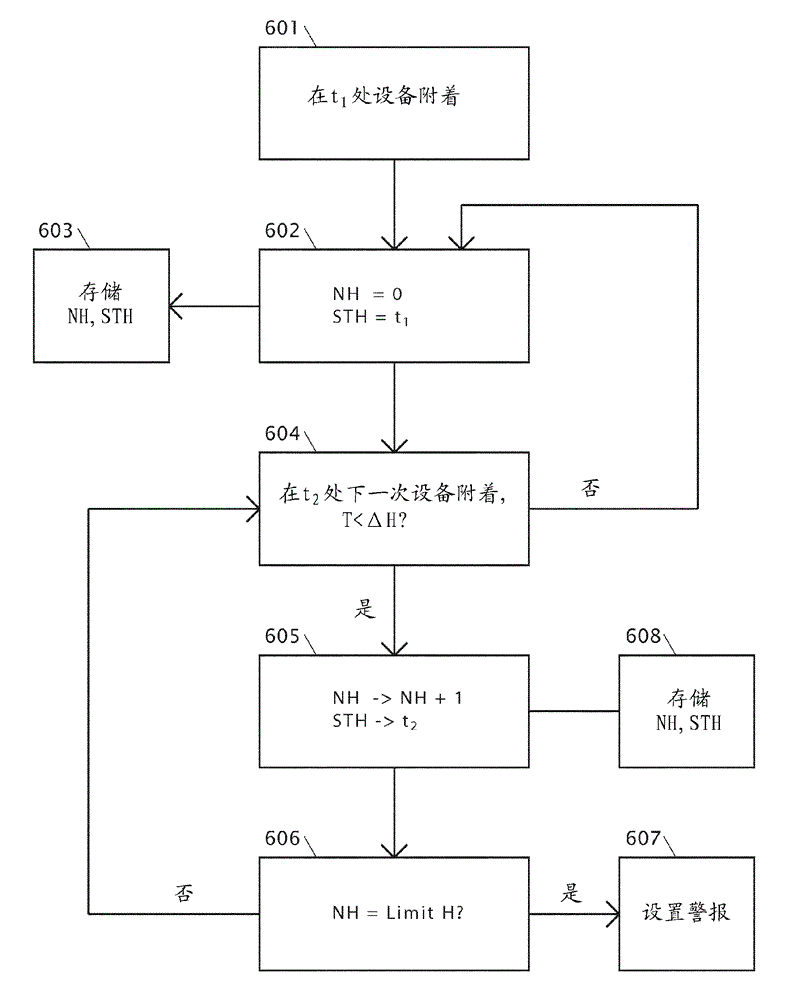
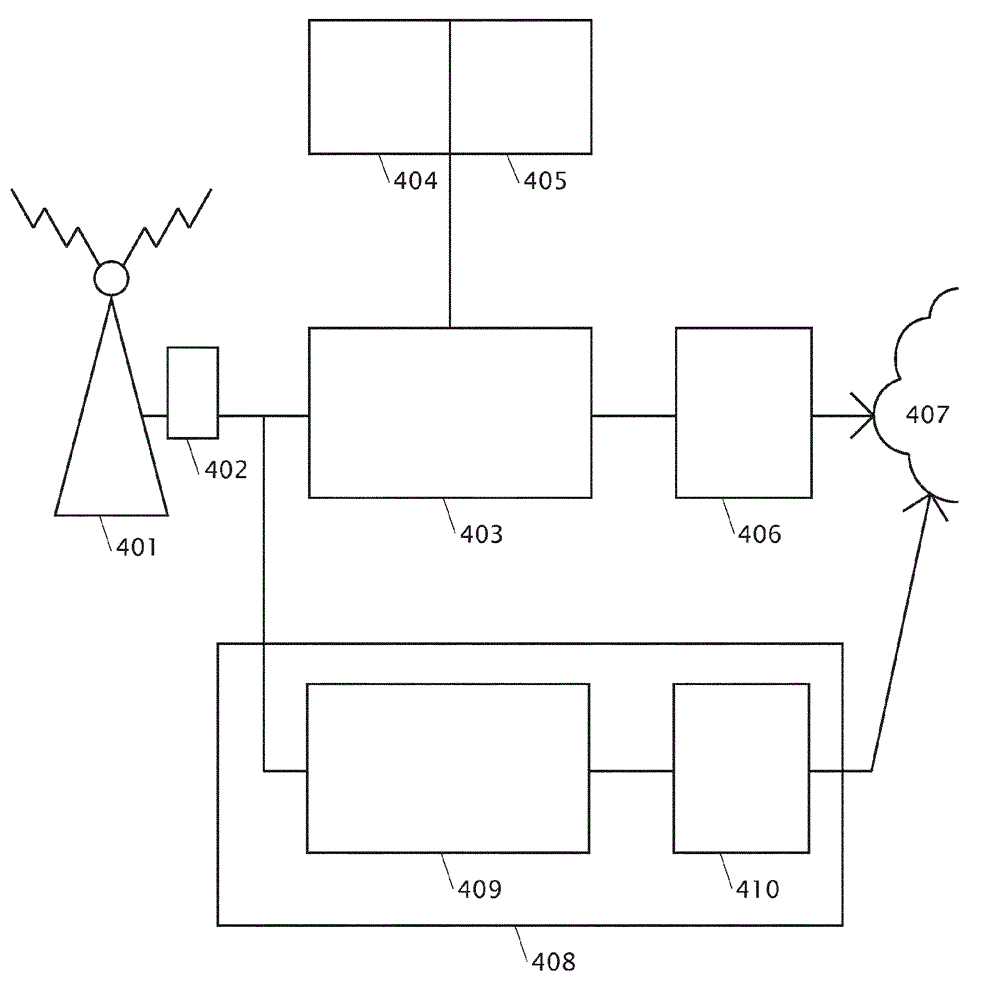
[0061] figure 1 A telecommunications network is shown in which malicious behavior can be detected. As is known to those skilled in the art, there are a number of technologies described by the various telecommunication standards that define telecommunication systems. Typically they include the following layout, although those skilled in the art know and appreciate that there may be small variations and differences in the way the system works.
[0062] The telecommunications network comprises a transmitter 101 . This is commonly referred to as a base station, cell tower or in LTE networks as an eNodeB. The transmitter is controlled by a base station controller 102, although in eg a UMTS network this would be a radio network controller 102 and eg in an LTE network the control functions of the base station controller 102 may be contained in the eNodeB. Radio signals from handheld mobile devices are received at the transmitter 601, processed into signals and transmitted to the c...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com