Formalized modeling based software security requirement acquisition method
A formal modeling and software security technology, applied in electrical digital data processing, instruments, platform integrity maintenance, etc., can solve problems only for security experts, general users, unsatisfactory degree of standardization and ease of use, etc. problem, to achieve the effect of strong universality and improved accuracy
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0018] The present invention will be described in detail below in conjunction with the accompanying drawings and specific embodiments, but the implementation scope of the present invention is not limited thereto.
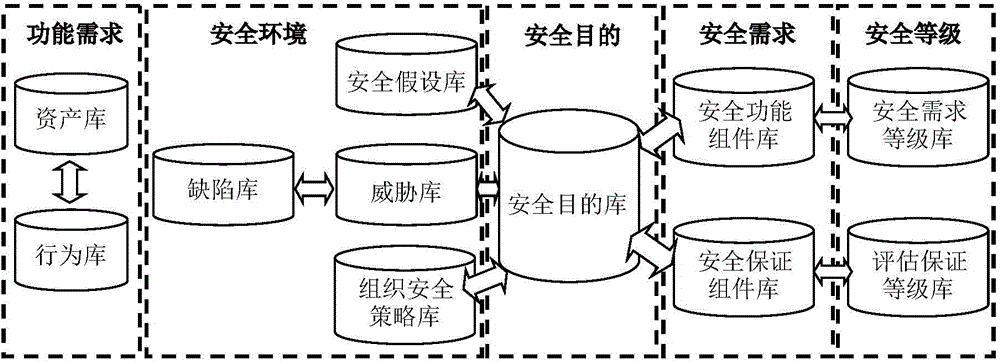
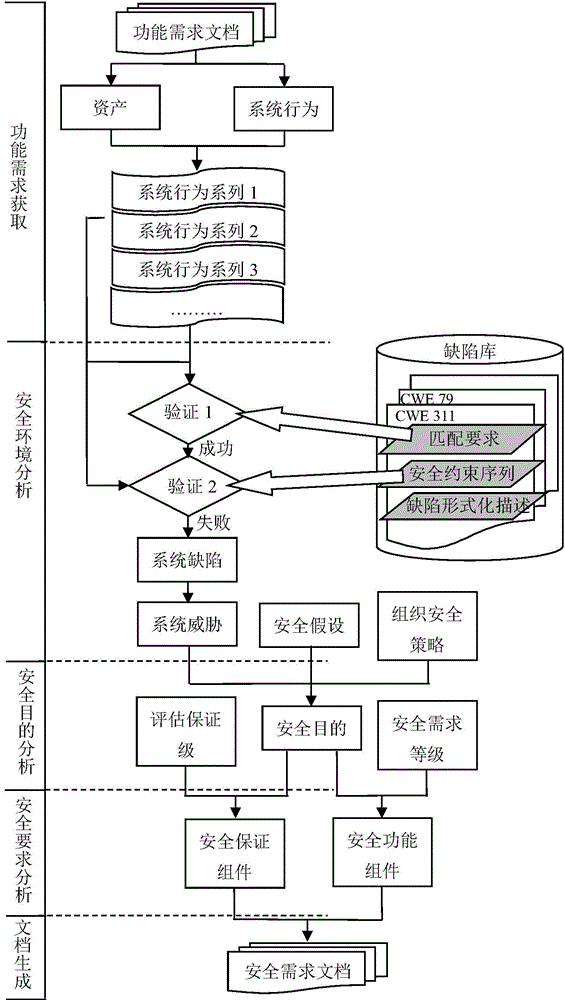
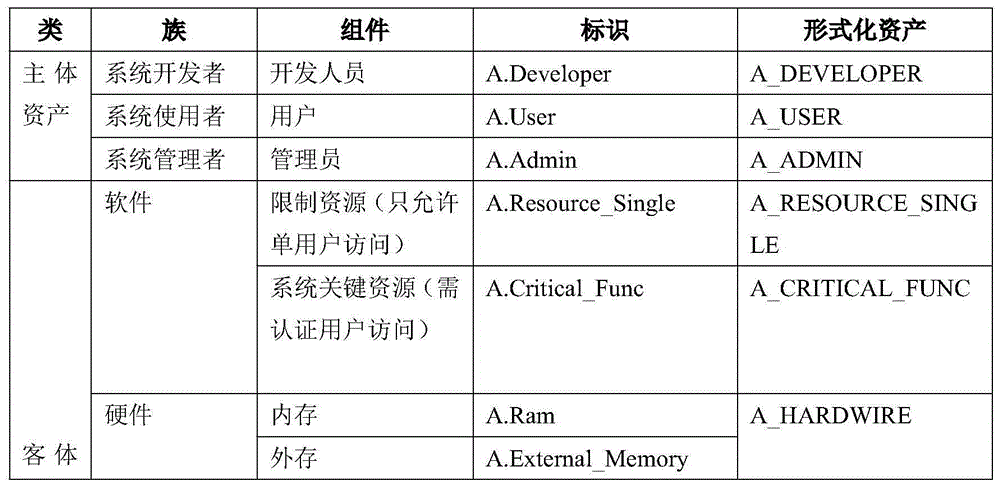
[0019] Based on CWE, CAPEC and other international common vulnerability and threat information databases, the present invention uses formal language to describe system assets, behaviors and defects, and establishes a set of comprehensive assets, system behaviors, defects, threats, security objectives, A security knowledge base of security policies, security assumptions, security requirement levels, security assurance levels, security functional requirements, and security assurance requirements.
[0020] The present invention mainly has three parts. Firstly, the system behavior sub-library is added to the knowledge base, and the mapping relationship between each sub-library is constructed. At the same time, assets, defects and system behaviors are formalized to obtain...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com