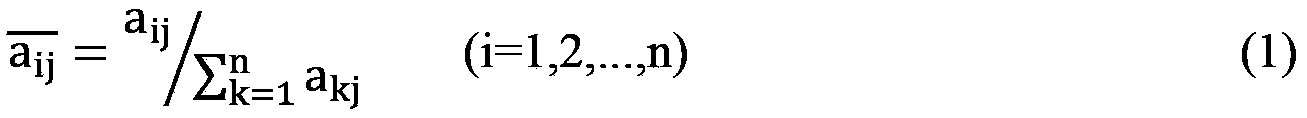Patents
Literature
62 results about "Software assets" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Asset management software is a software product designed to help people keep track of their assets. This software can be used by both businesses and individuals. A number of software companies make programs of this nature, including versions designed for special applications.
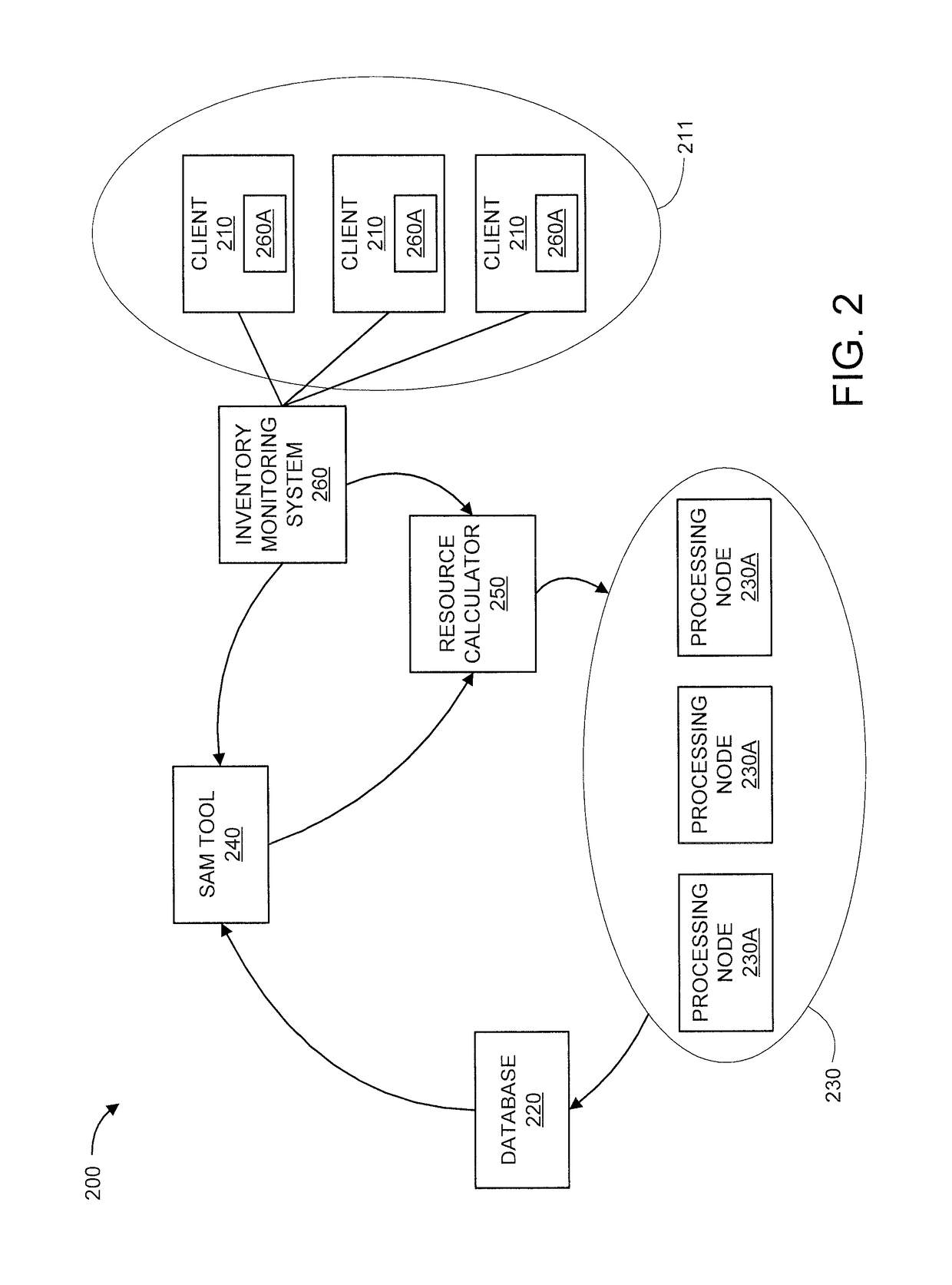
Web-based system for managing software assets
InactiveUS7197466B1Avoid litigationAvoid fineData processing applicationsComputer security arrangementsSoftware development processManagement process
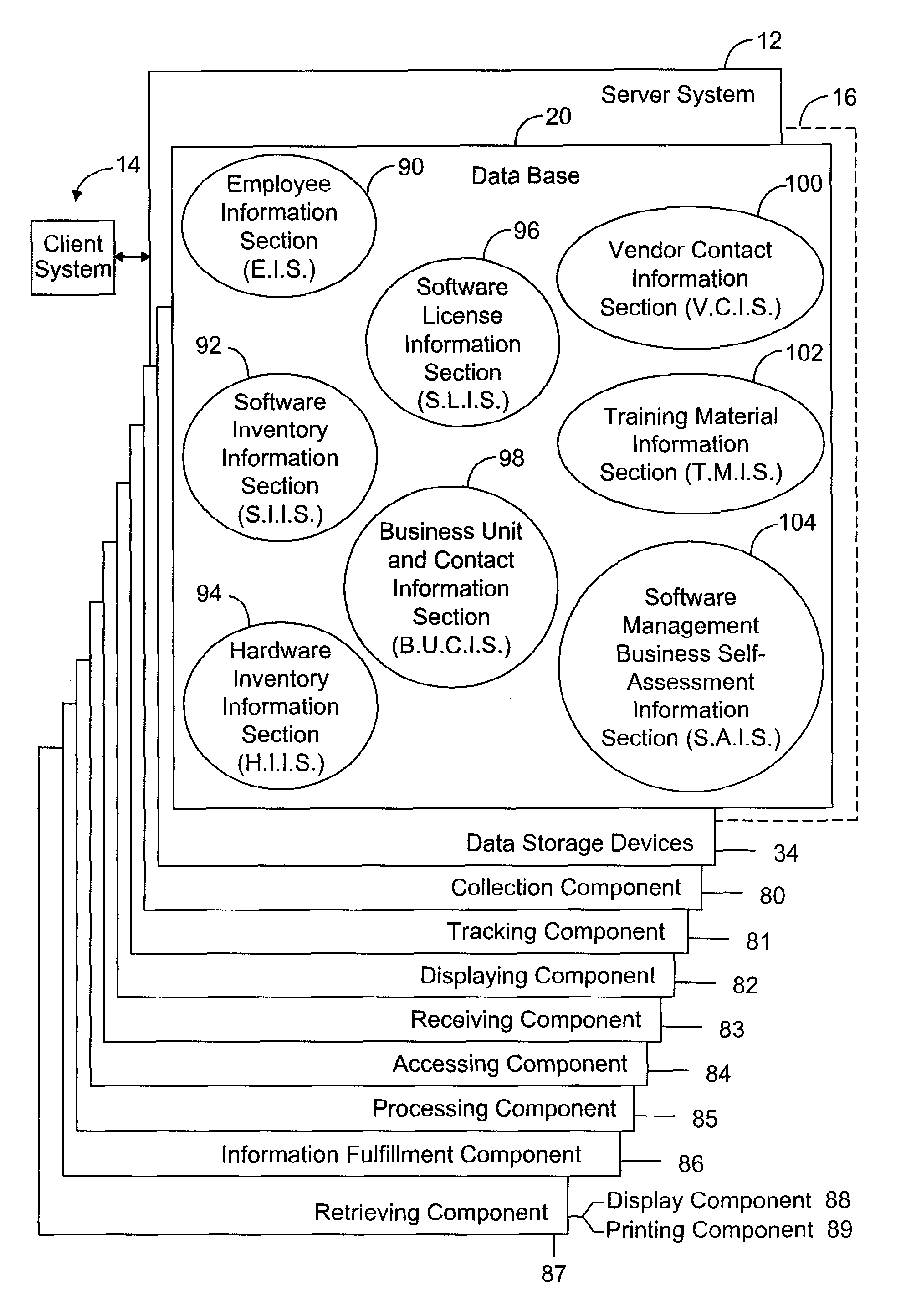
The disclosed invention is a software license management system (SLMS) utilizing a web-based interactive database to automate a software management process (SWMP) for managing software assets, measuring compliance requirements, and tracking / reporting status as necessary to assure proficiency and adherence to implementation requirements of the software management process. The SWMP is a process consisting of five different phases. The five steps of the SWMP involve identification of various solution alternatives, acquisition, deployment, maintenance and software retirement. The SWMP establishes high-level software management process to avoid litigation and penalties, maximize software asset utilization through tighter inventory control, and capitalize on the software procurement process.
Owner:GE CAPITAL US HLDG INC +1
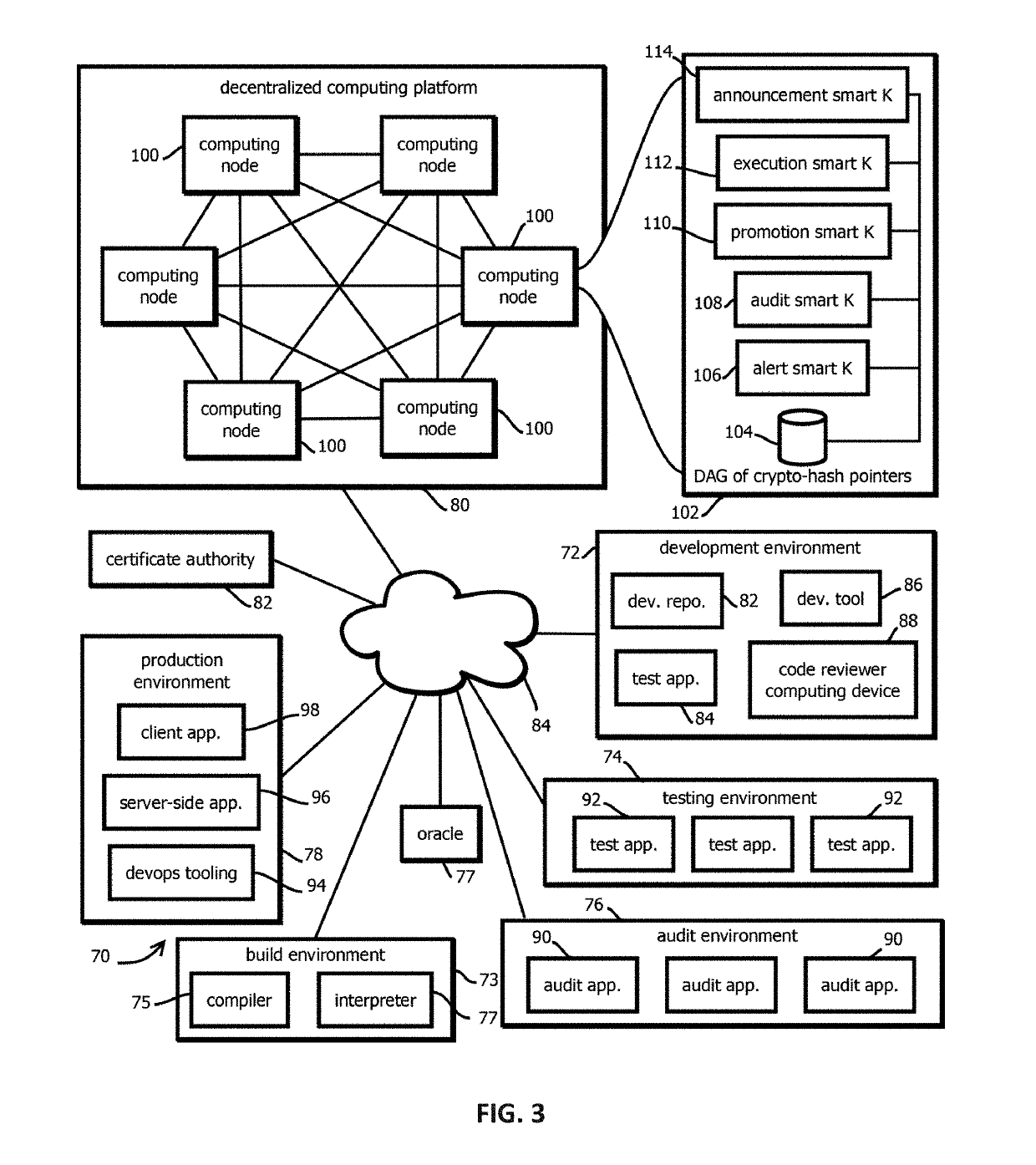
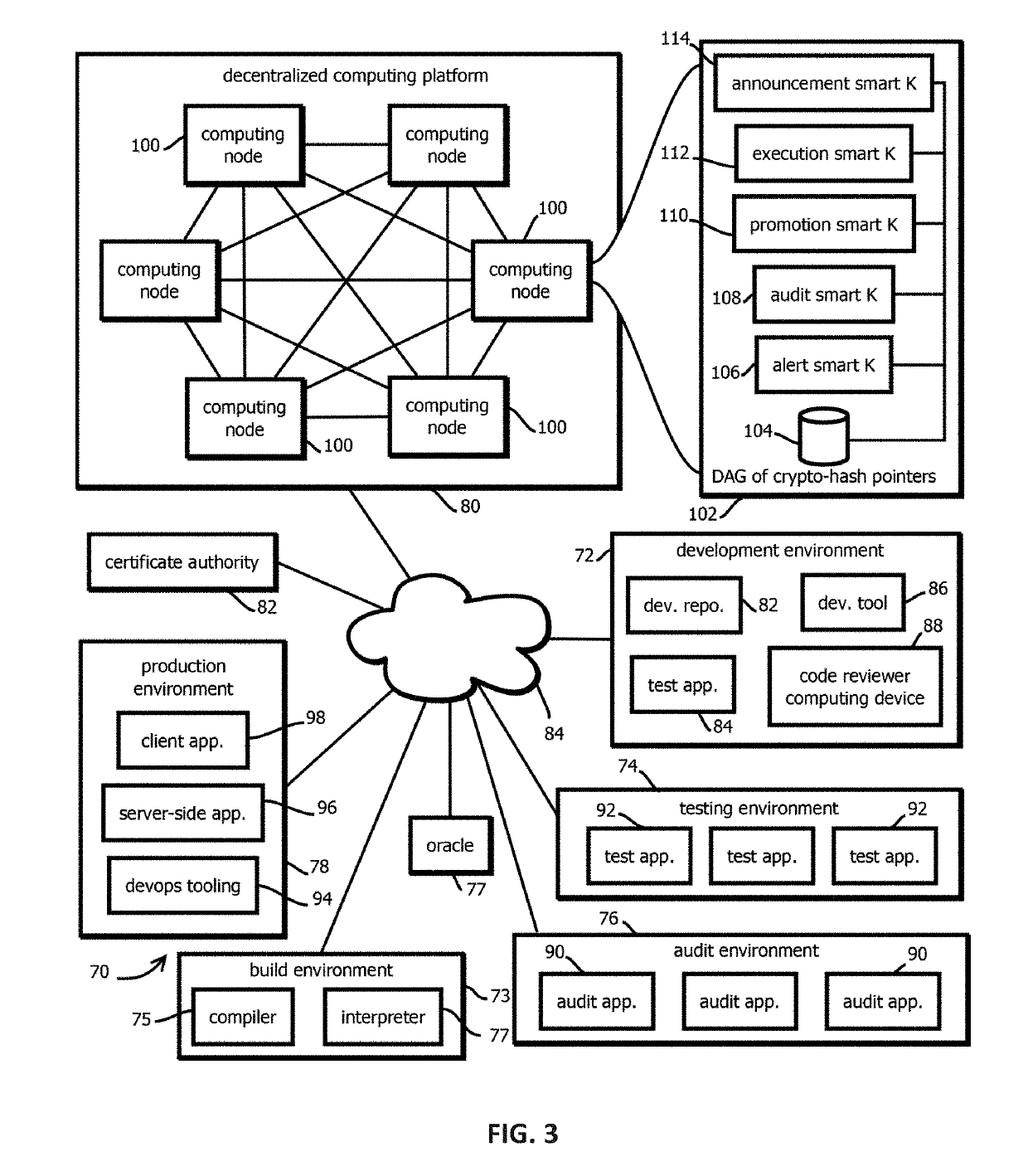
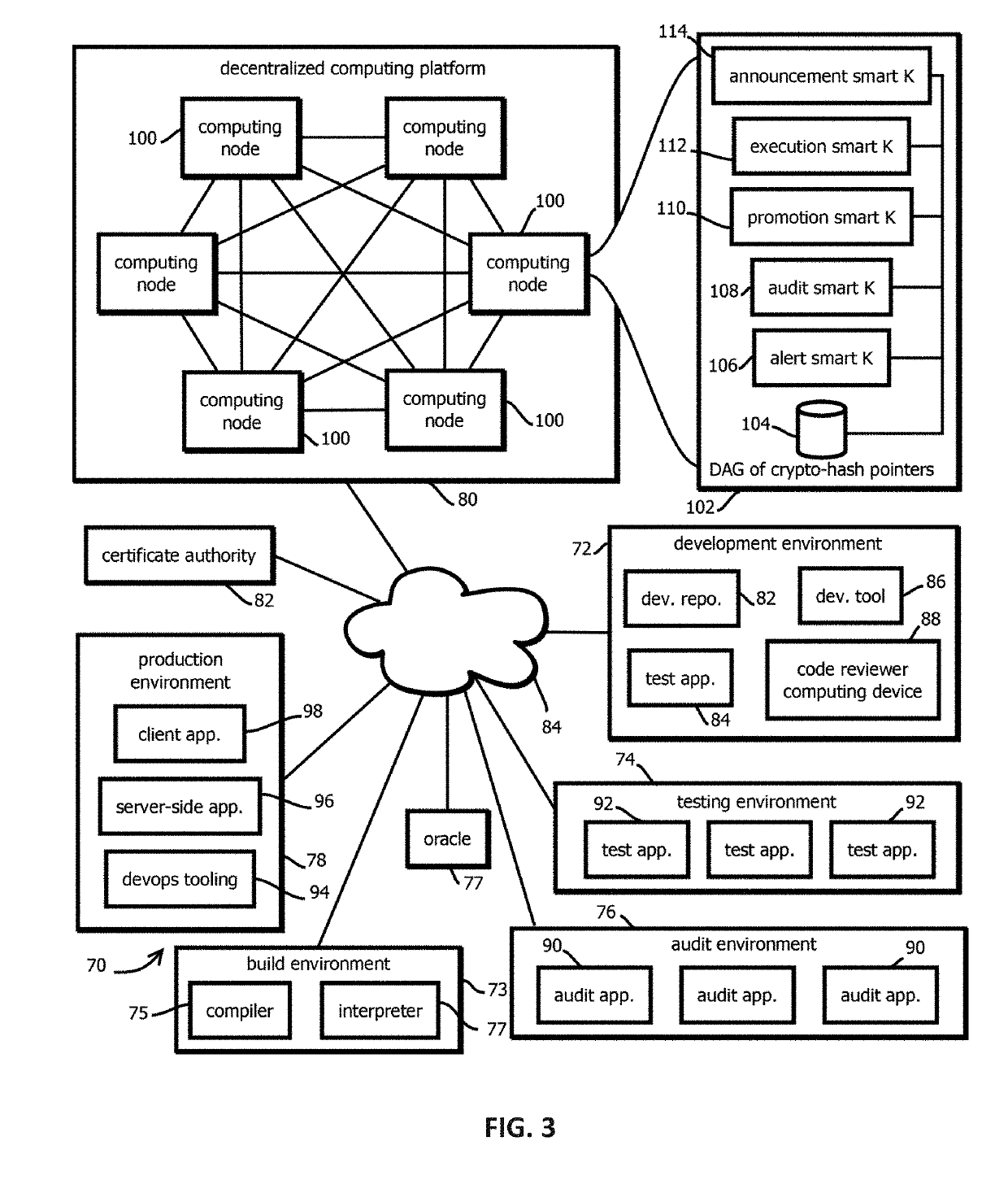
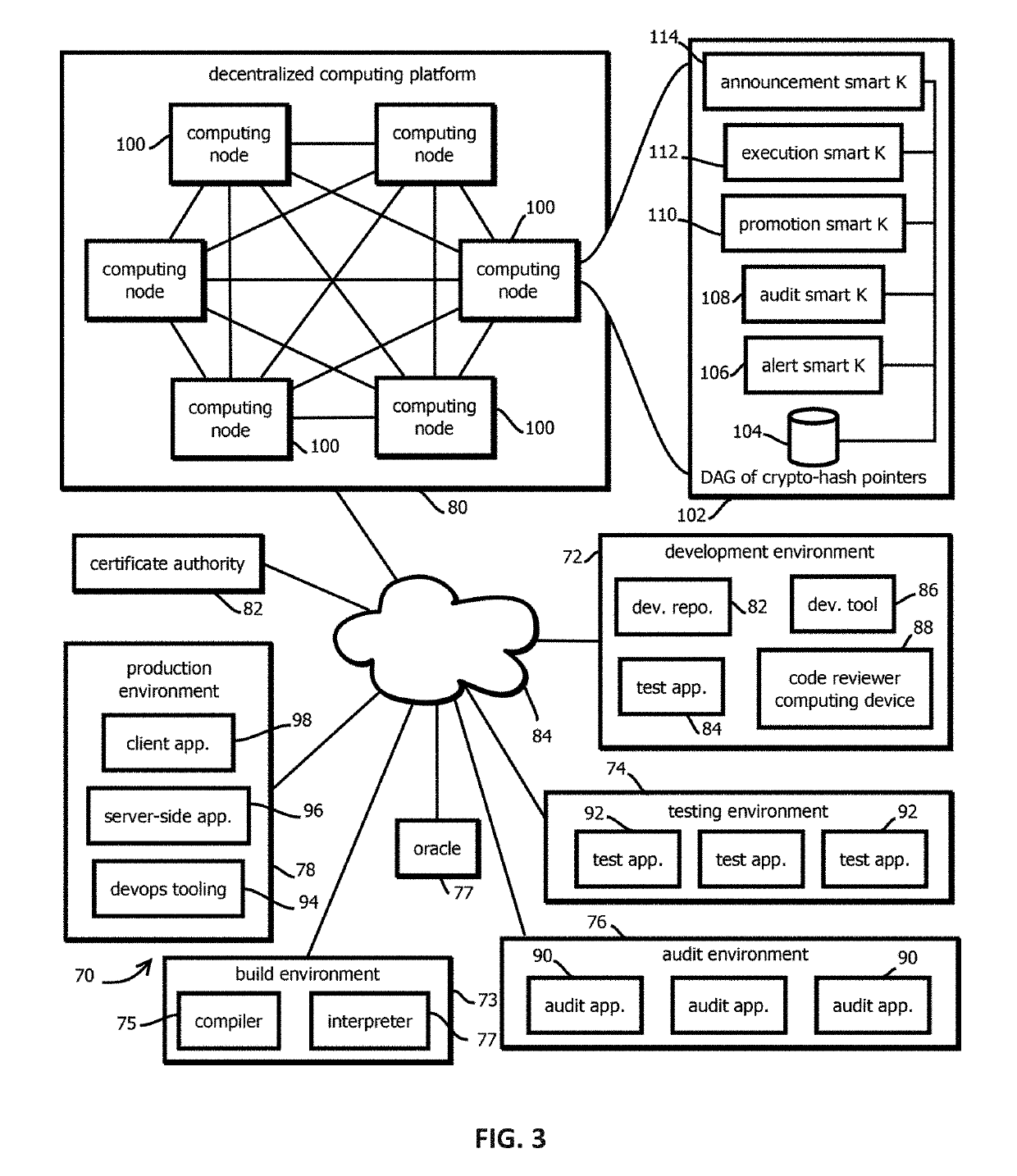
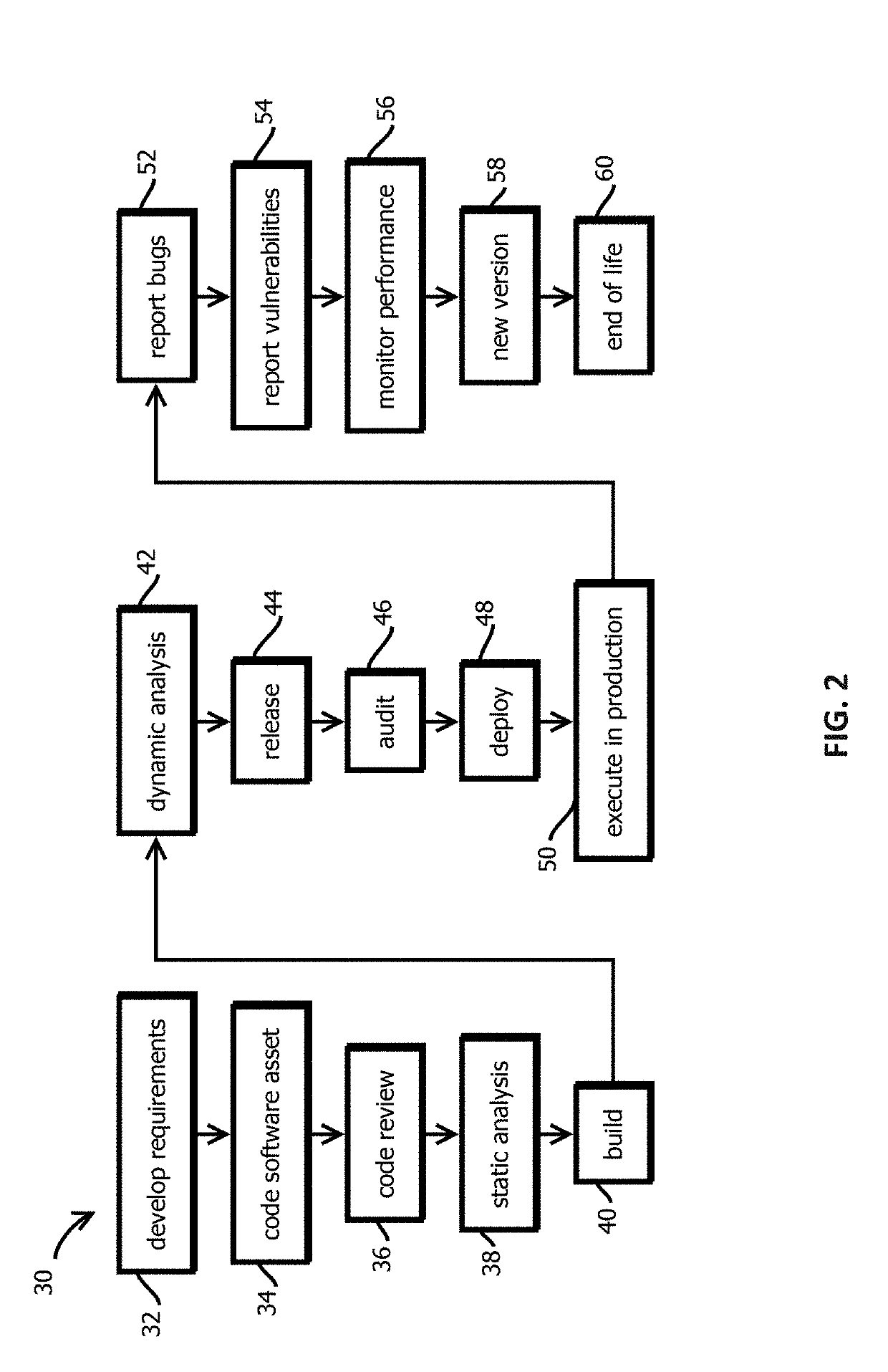
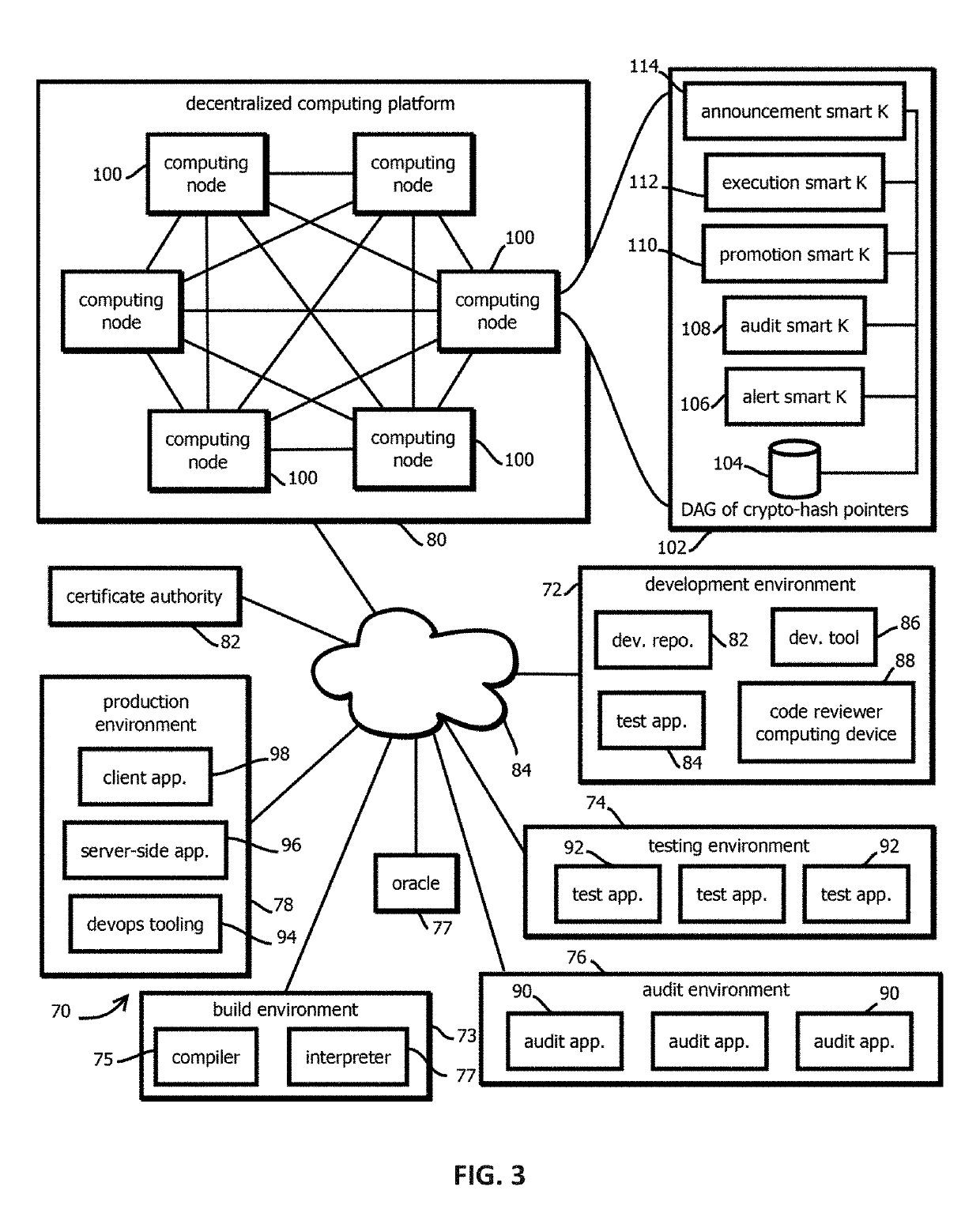
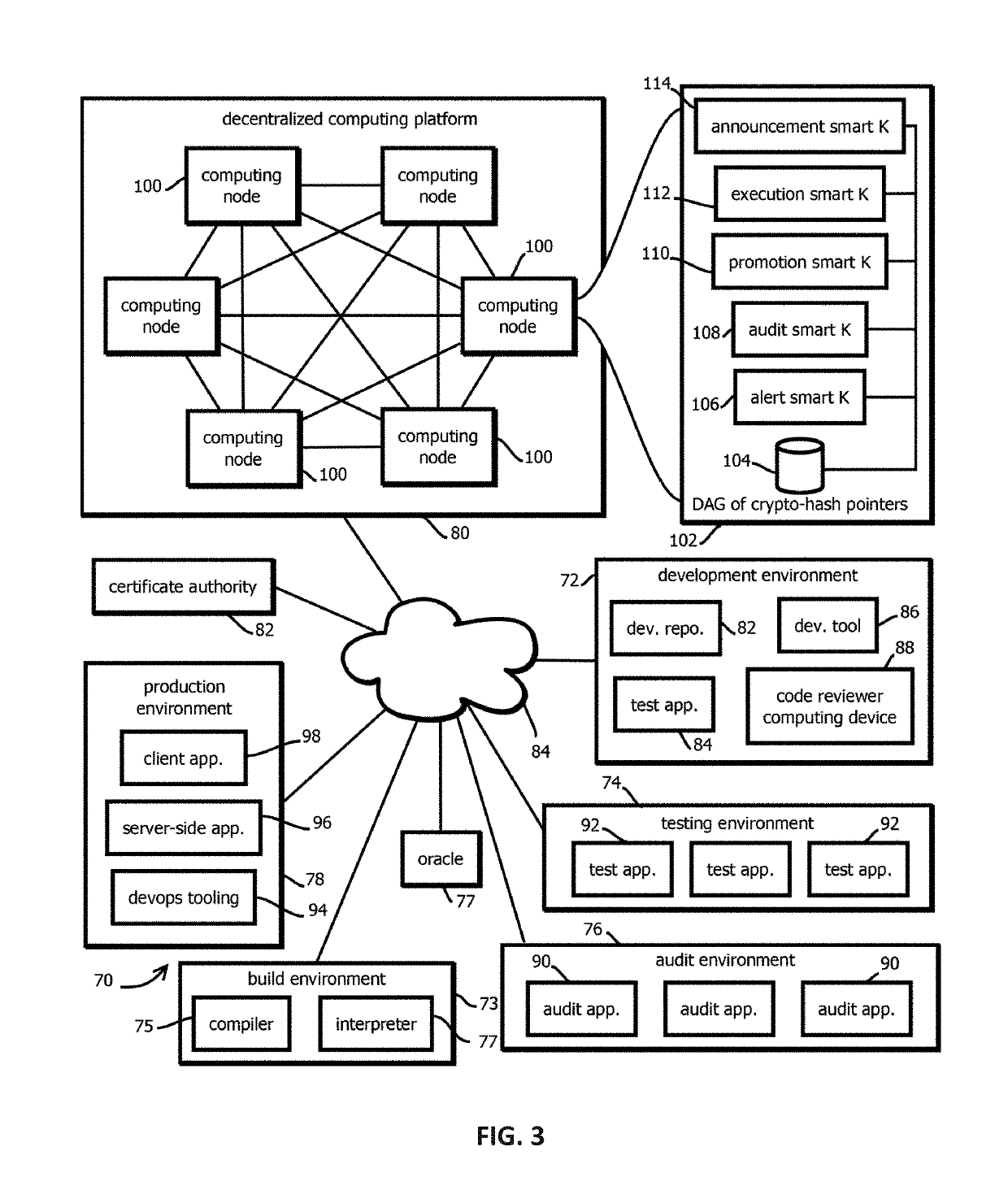
Execution smart contracts configured to establish trustworthiness of code before execution
InactiveUS20190305957A1User identity/authority verificationProgram documentationSmart contractTrustworthiness
Provided is a process that includes: determining whether to execute a software asset based on trust records documenting provenance of the software asset published to a blockchain, wherein determining whether to trust the software asset comprises: accessing the trust record, verifying the trust record has not been tampered with subsequent to publishing, verify that a hash digest based on the software asset matches a hash digest associated with the trust record and published to the blockchain; verifying that trust assertions of the trust record are cryptographically signed by trusted entities specified by entity criteria, and verifying that the trust assertions satisfy execution criteria.
Owner:CA TECH INC
Promotion smart contracts for software development processes
InactiveUS20190303623A1Version controlUser identity/authority verificationSoftware development processSoftware engineering
Provided is a smart contract that specifies a routine to be executed by a plurality of the computing nodes of a blockchain-based, decentralized computing platform, wherein the promotion smart contract is configured to determine whether a pre-release software asset satisfies software quality criteria required to advance the pre-release software asset to a next stage, and the promotion smart contract is configured to cause an assertion indicating whether software quality criteria are satisfied to be published to a blockchain storing trust records in response to determining whether the software quality criteria are satisfied.
Owner:CA TECH INC
Auditing smart contracts configured to manage and document software audits
InactiveUS20190303541A1Encryption apparatus with shift registers/memoriesUser identity/authority verificationSmart contractSoftware assets
Provided is a process that includes: calling an audit smart contract with a request to indicate whether an audit requirement has been satisfied for a software asset, wherein: the audit smart contract is configured to access a trust record published in a blockchain to determine whether the audit requirement has been satisfied, the trust record is caused to be published to the blockchain by an auditing entity that performed the audit, the trust record contains a cryptographically signed indication of an identity of an auditing entity that performed the audit, a result of the audit that specifies whether the audit was passed by the software asset, and a hash digest of the software asset upon which the audit was performed, wherein the audit smart contract is configured to determine whether the trust record establishes that the audit requirement has been satisfied.
Owner:CA TECH INC
Method and apparatus for technology resource management
InactiveUS7660731B2Multiprogramming arrangementsResourcesService-level agreementHuman resource management
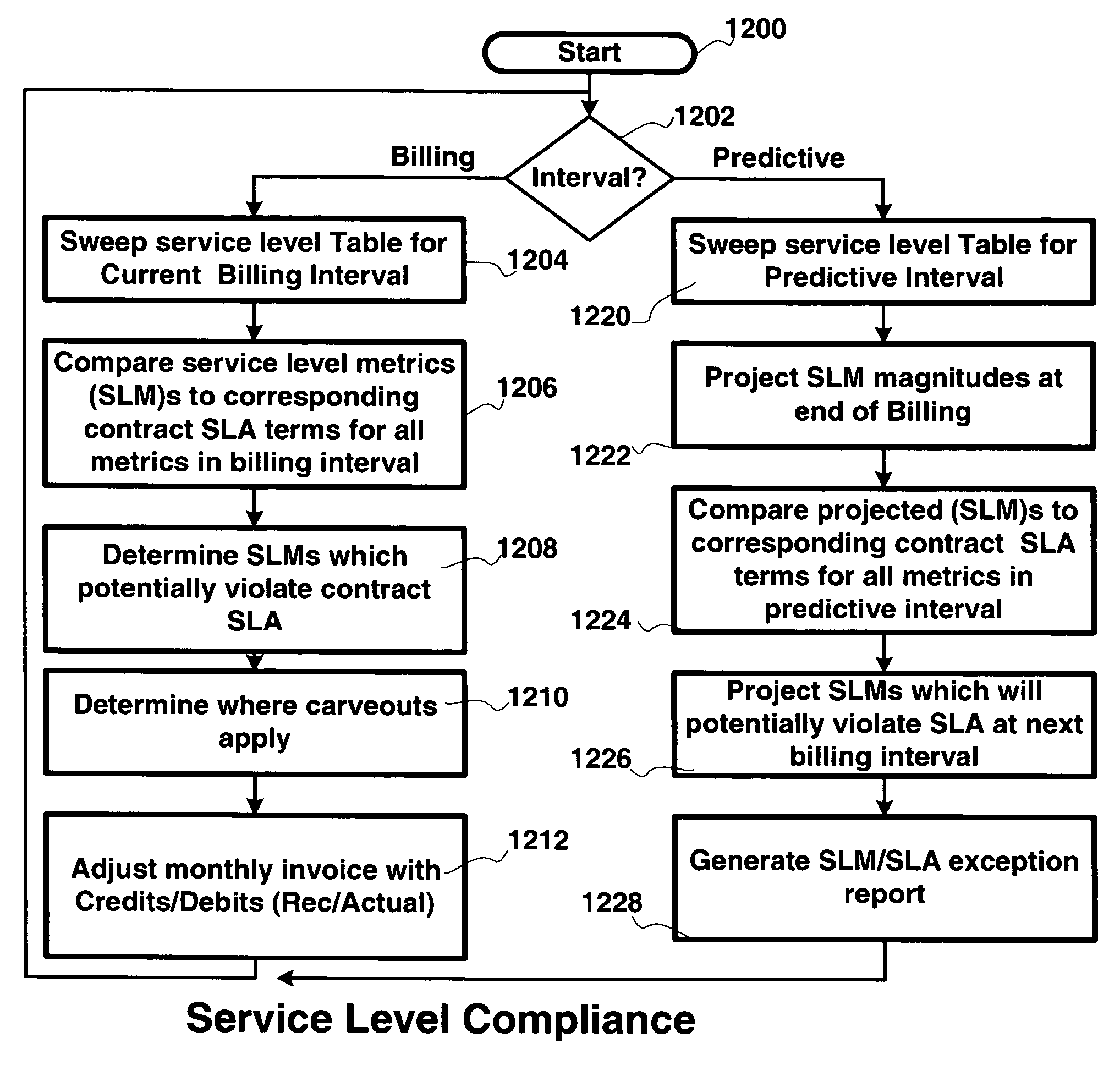
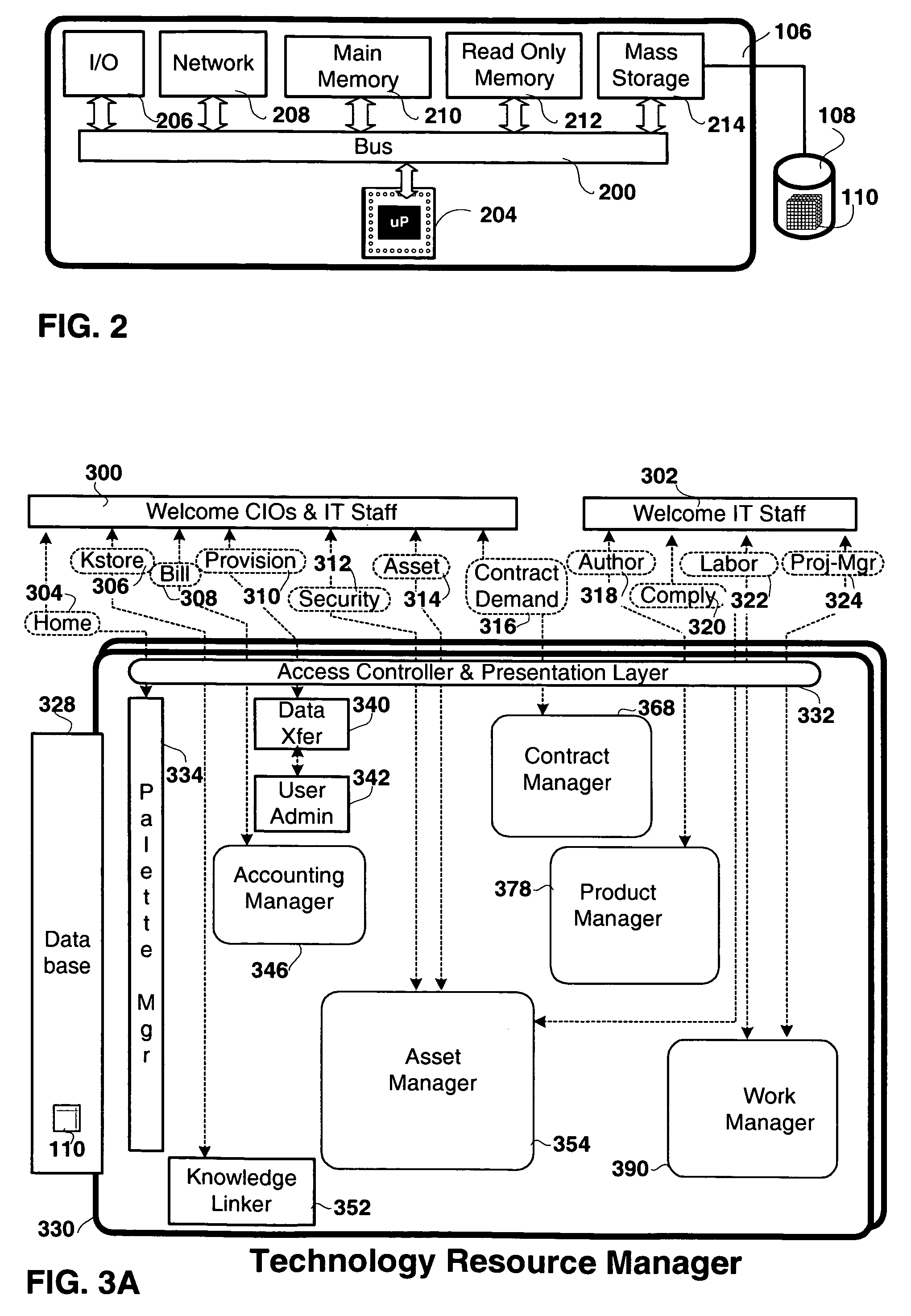
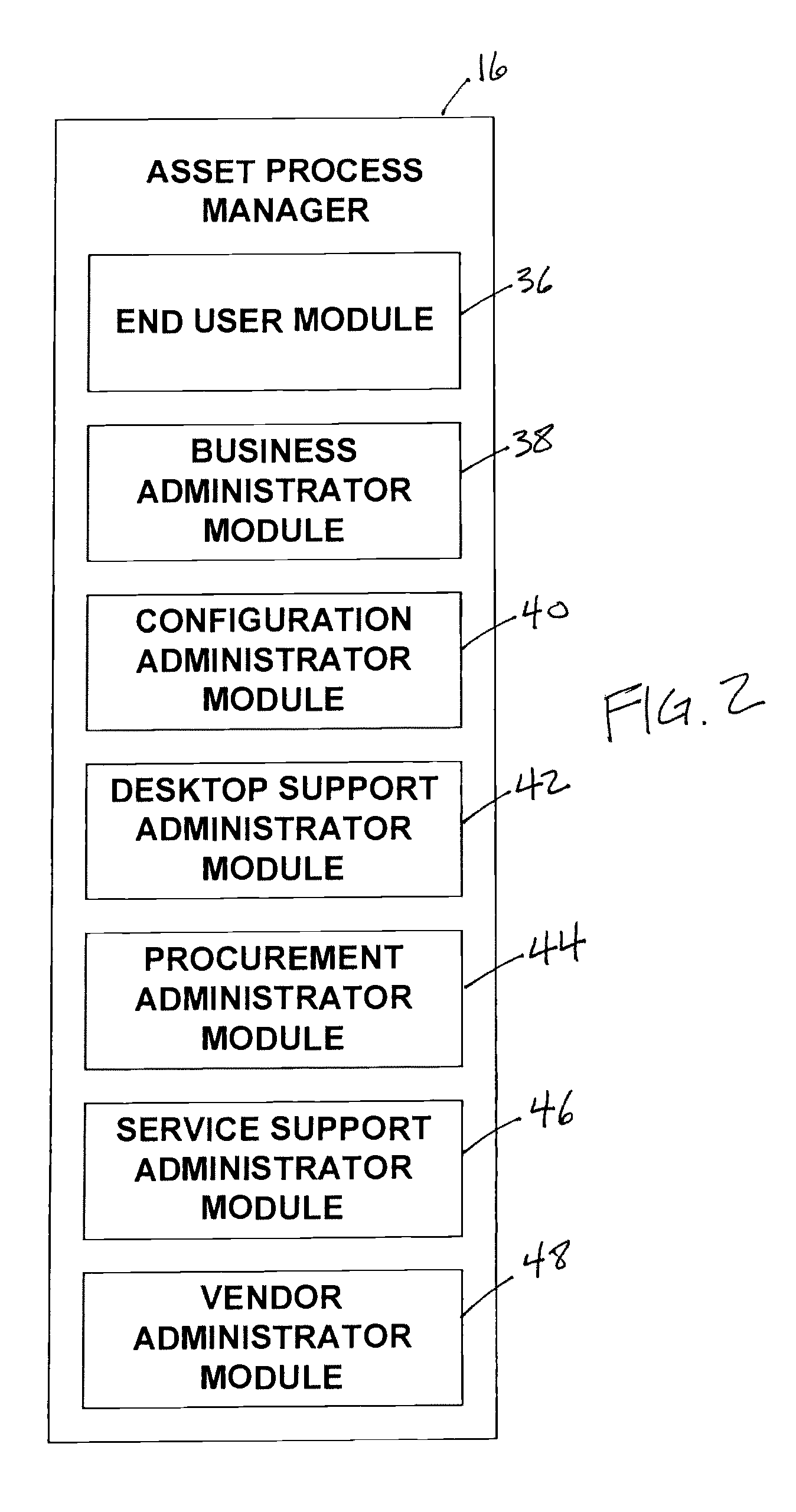
Apparatus and methods to manage demand, service level agreements, hardware and software assets, projects, labor, knowledge and provisioning resources in hosted applications. An asset manager coupled to host servers and a network, manages the host servers and software to determine the demand for new assets and allocate available assets to meet the demand; determine assets not in compliance with existing software licenses; determine and compare actual service level metrics with the target service level metrics; and determine availability of a patch or upgrade for selected software and instances of the selected software among the assets. The asset manager may be coupled to other managers, e.g., contract, product, work and / or accounting managers, to monitor service level metrics and / or costs.
Owner:IBM CORP
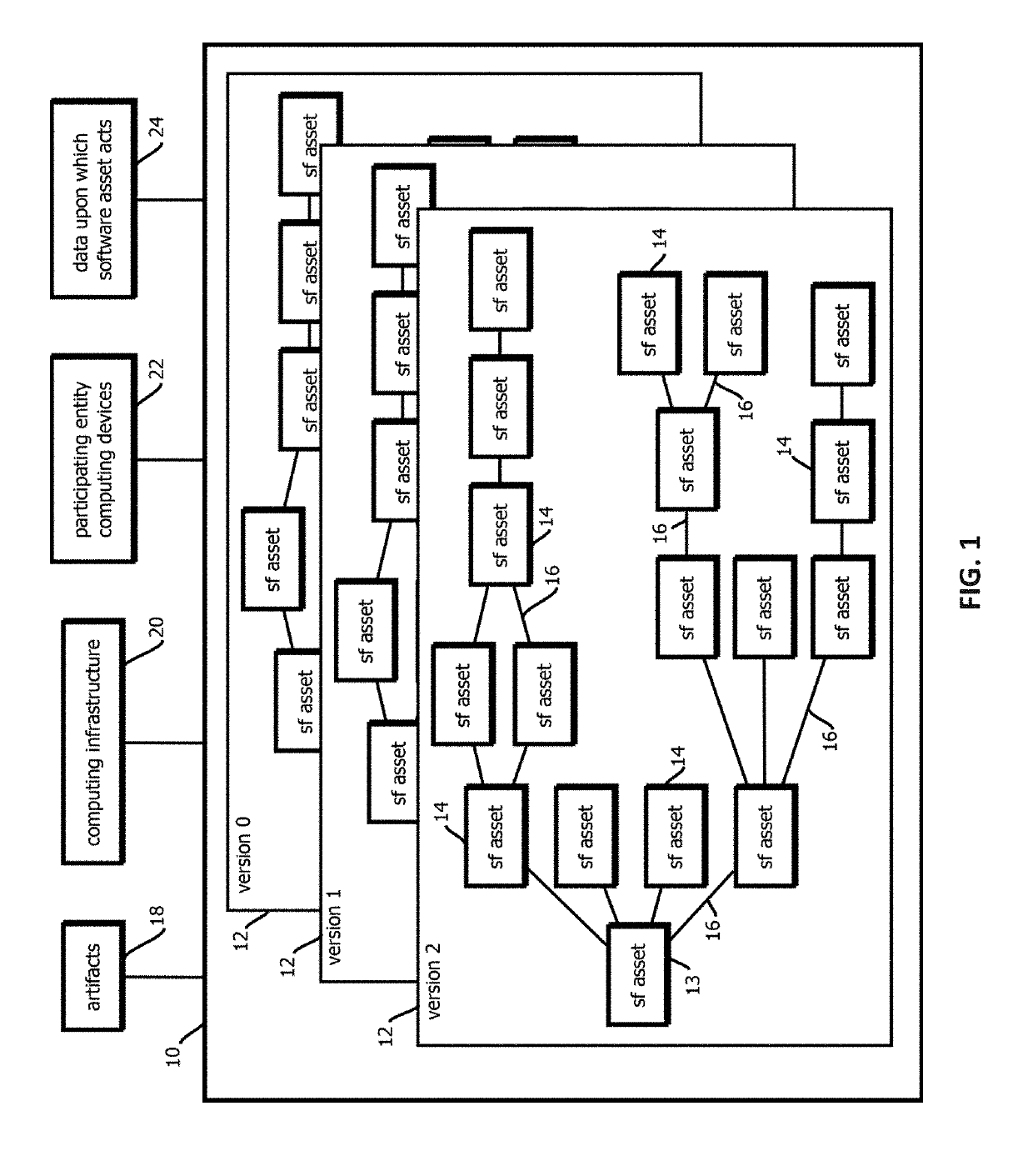
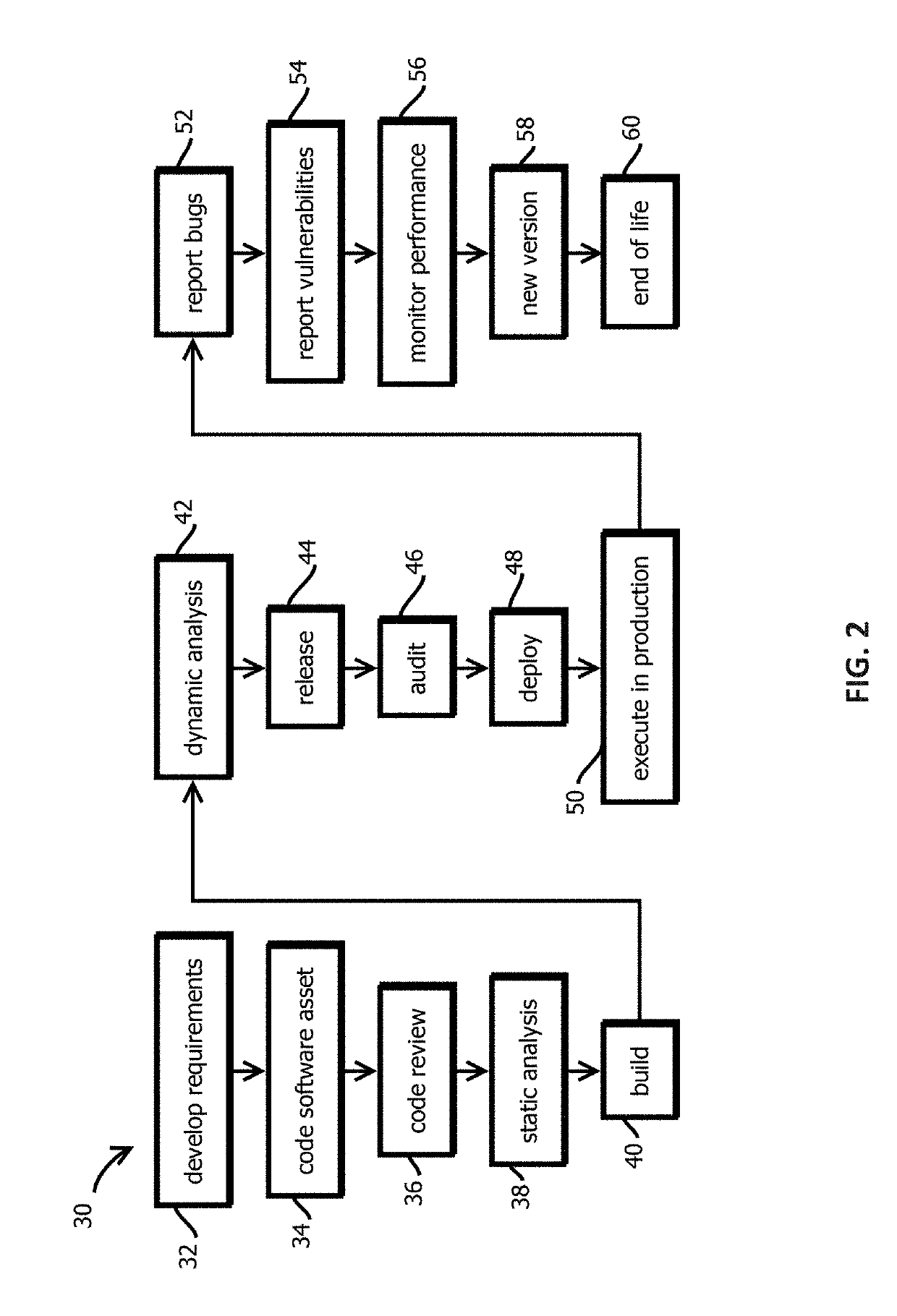
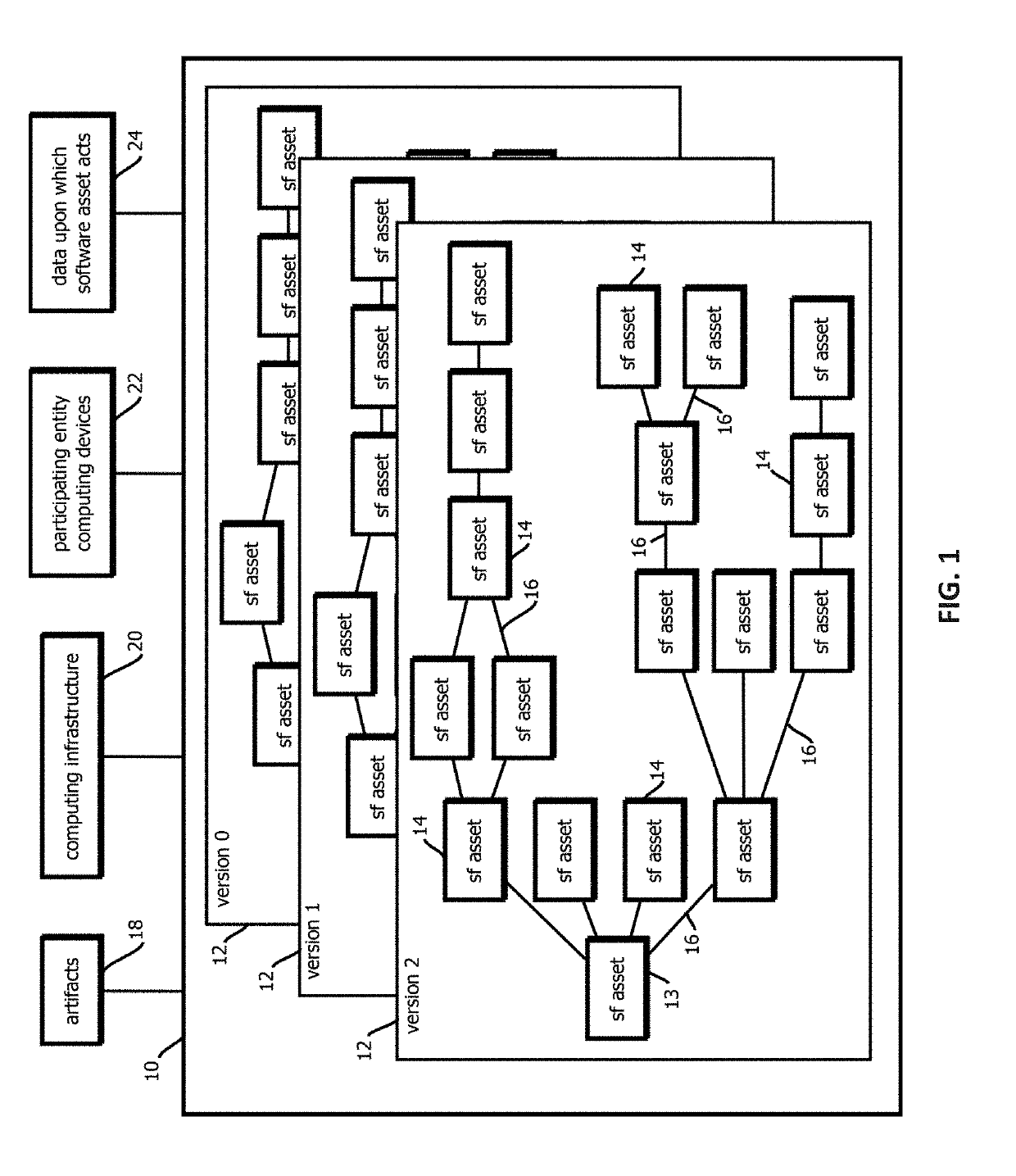
Decentralized, immutable, tamper-evident, directed acyclic graphs documenting software supply-chains with cryptographically signed records of software-development life cycle state and cryptographic digests of executable code
InactiveUS20190303579A1User identity/authority verificationPlatform integrity maintainanceSoftware developmentData storing
Owner:CA TECH INC
Alert smart contracts configured to manage and respond to alerts related to code
InactiveUS20190306173A1Encryption apparatus with shift registers/memoriesError detection/correctionSmart contractDecentralized computing
Provided is a process that includes: calling an alert program configured to execute on a decentralized computing platform and access records on a blockchain, wherein: the decentralized computing platform is configured to execute multiple instances of the program to produce multiple instances of candidate results, the decentralized computing platform is configured to determine an output of the alert program in response to the call with a first consensus algorithm, the alert program is configured to verify a cryptographic signature of the call and determine whether an alerting entity is authorized to issue the alert, and the alert program is configured to publish the information about the software asset to alert recipients or to the blockchain upon verifying the cryptographic signature and determining that the alerting entity is authorized to issue the alert.
Owner:CA TECH INC
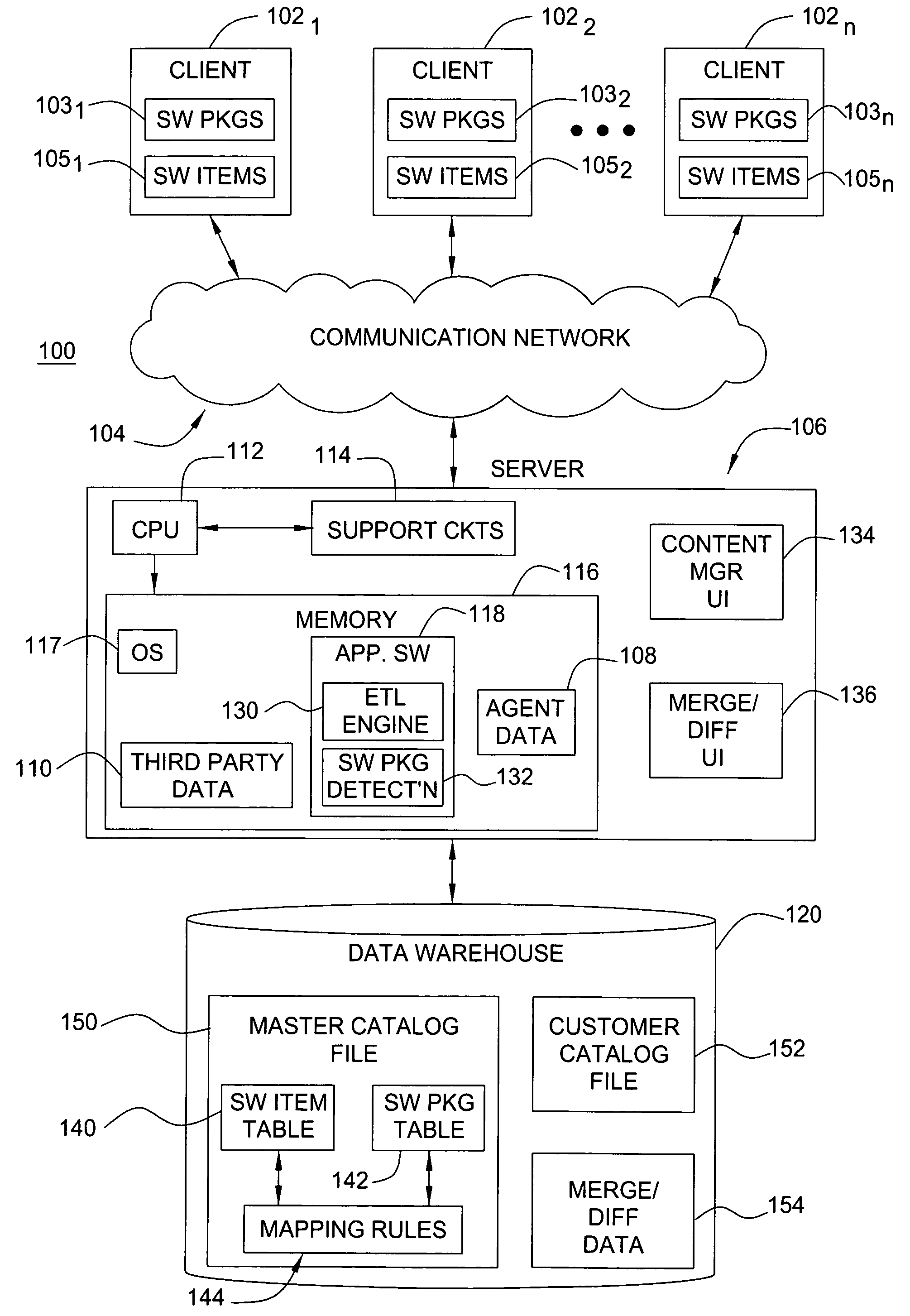
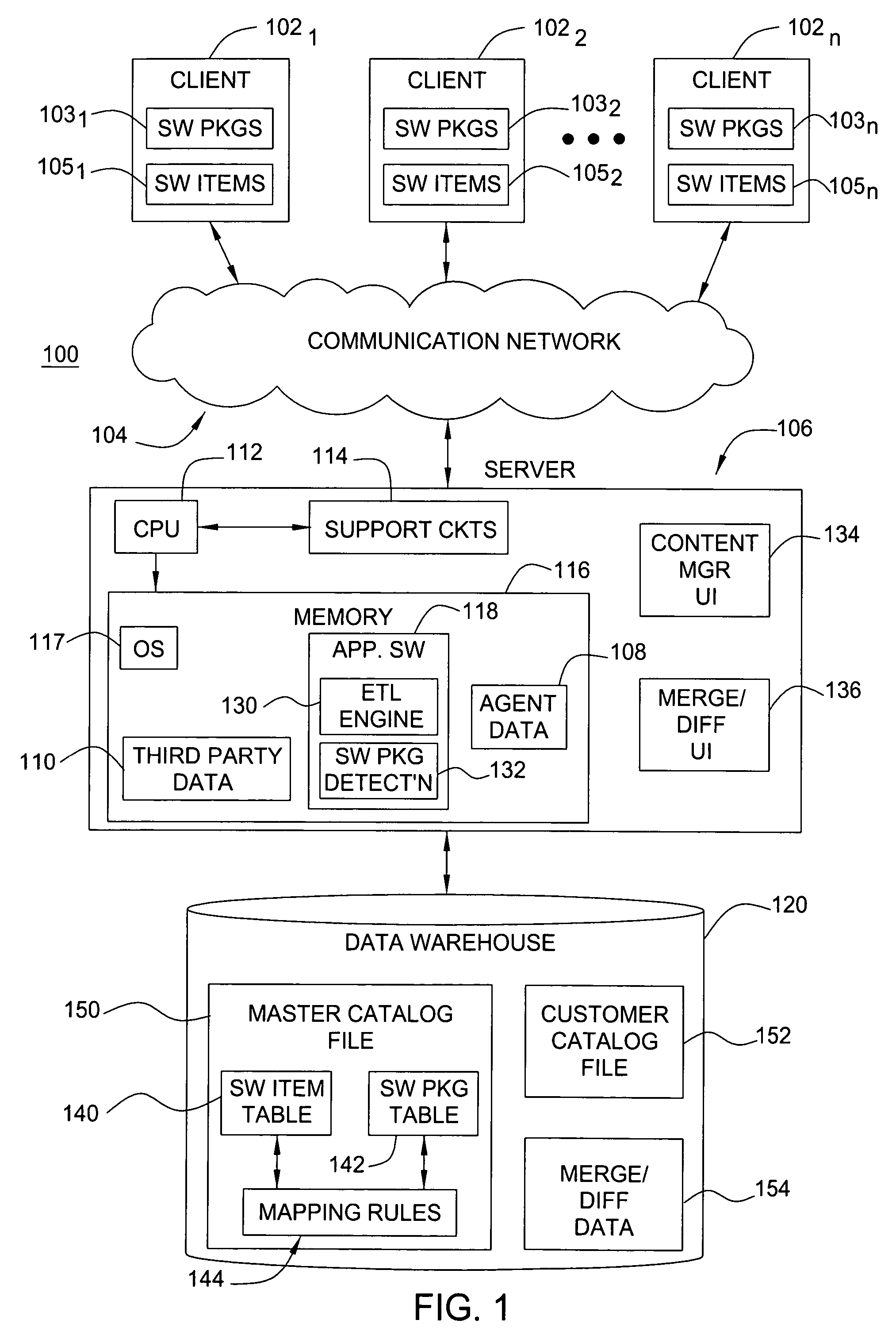
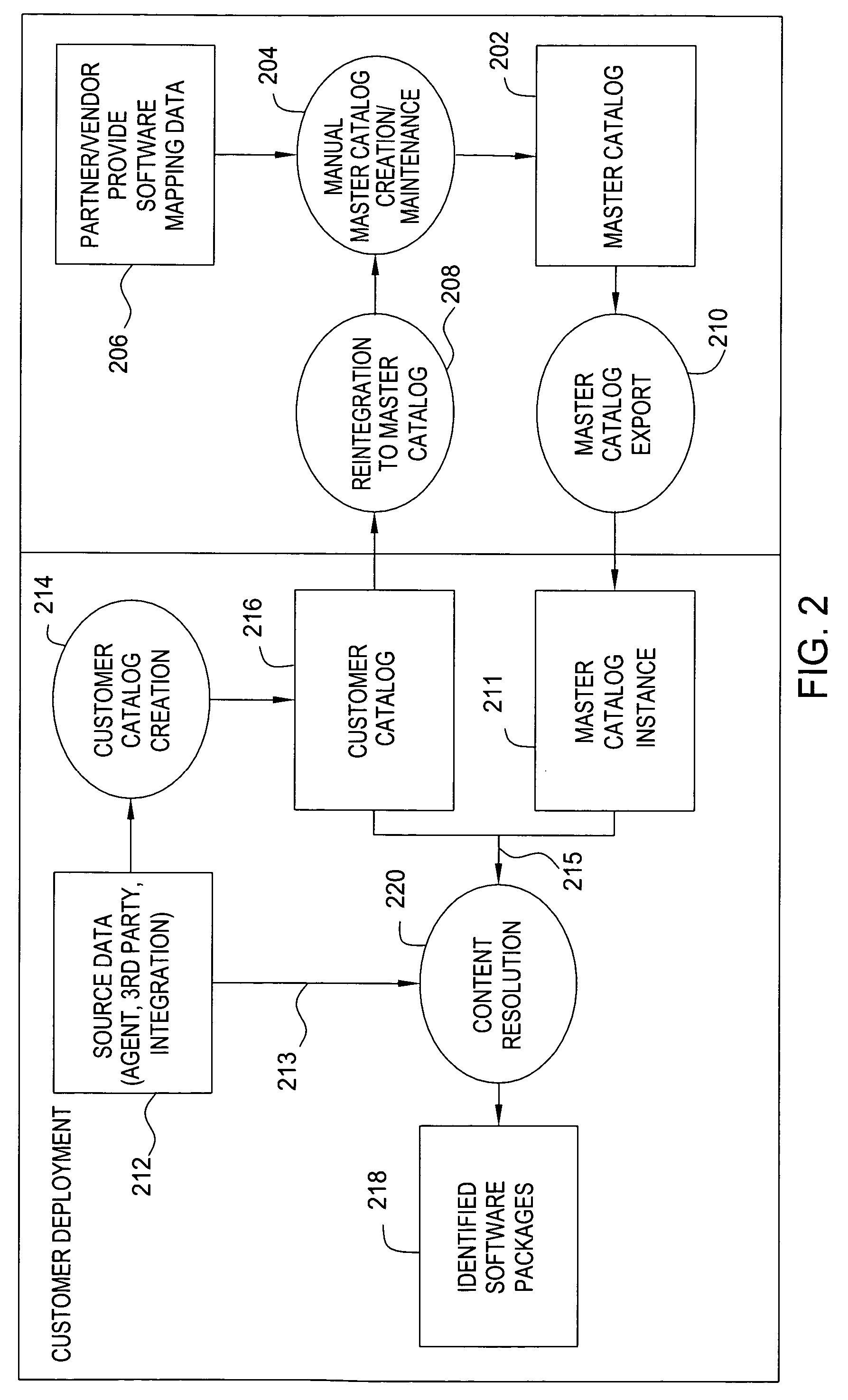
Method and apparatus for identifying and cataloging software assets
A method and apparatus are disclosed for identifying and cataloging software assets contained on a networked computer. In accordance with one embodiment, there is provided a method comprising providing a data warehouse including a master catalog file. The master catalog file comprises a software items table of attributes, a software packages table of attributes, and a mapping rules table for mapping certain software item entries to certain software package entries.
Owner:BLAZENT INC
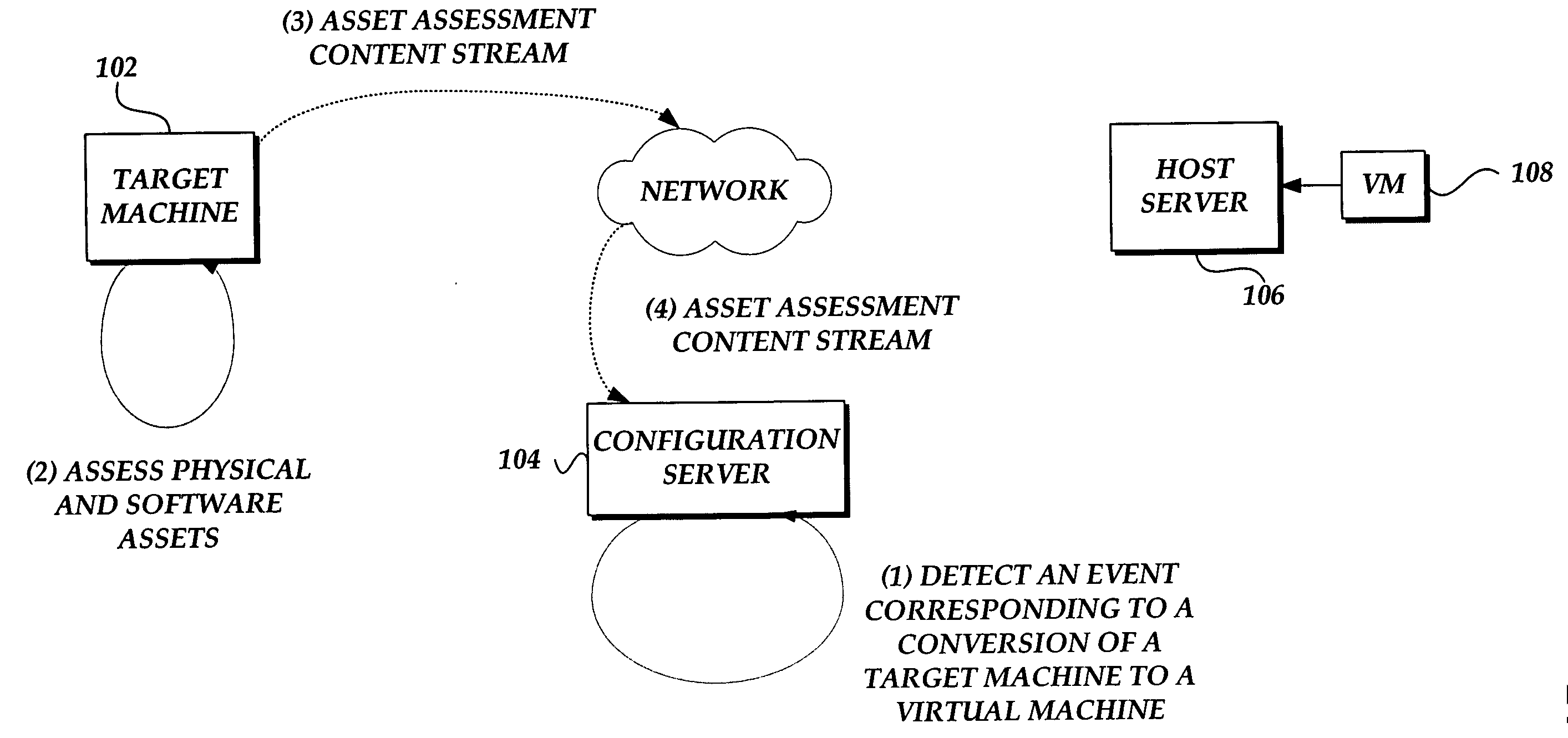
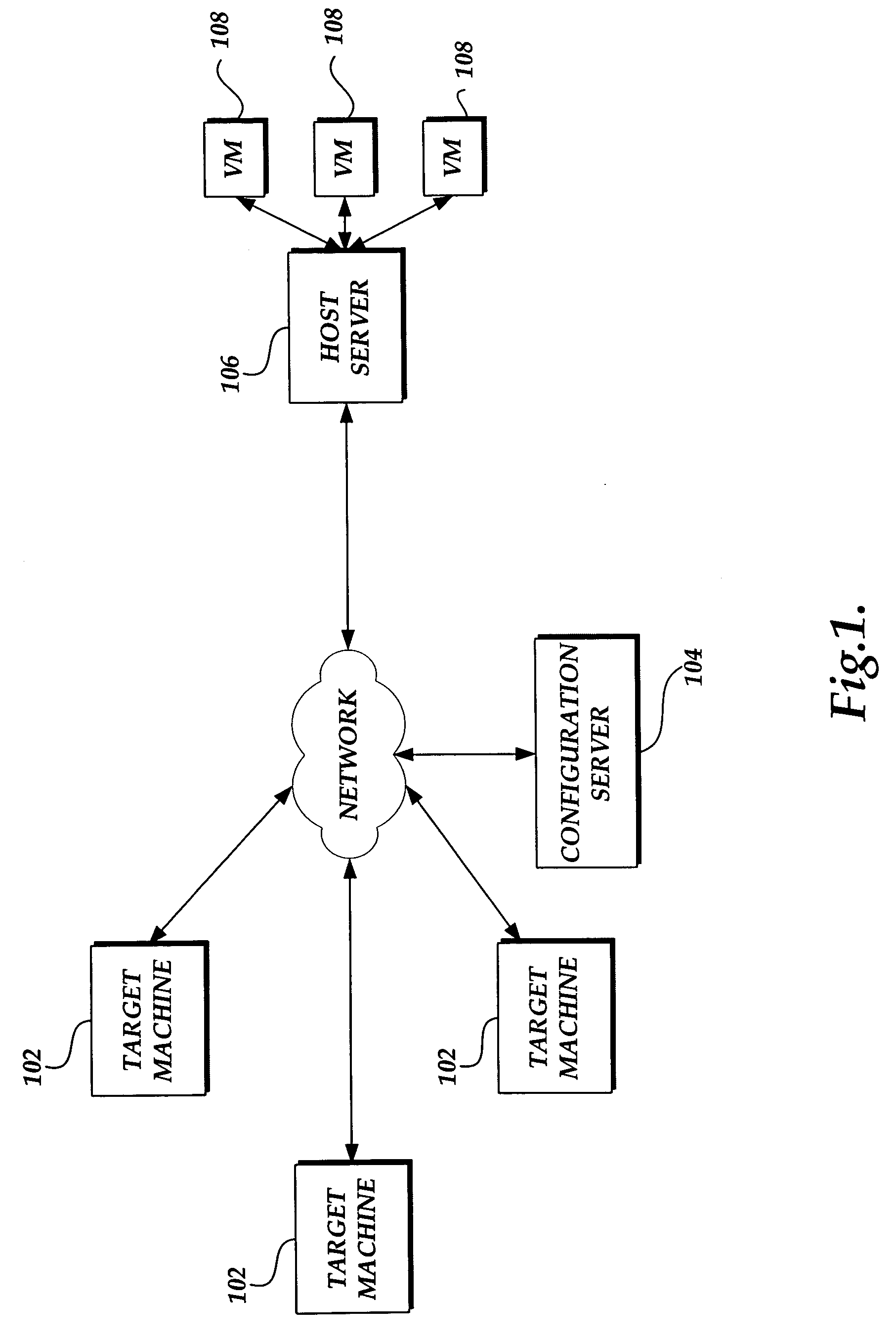
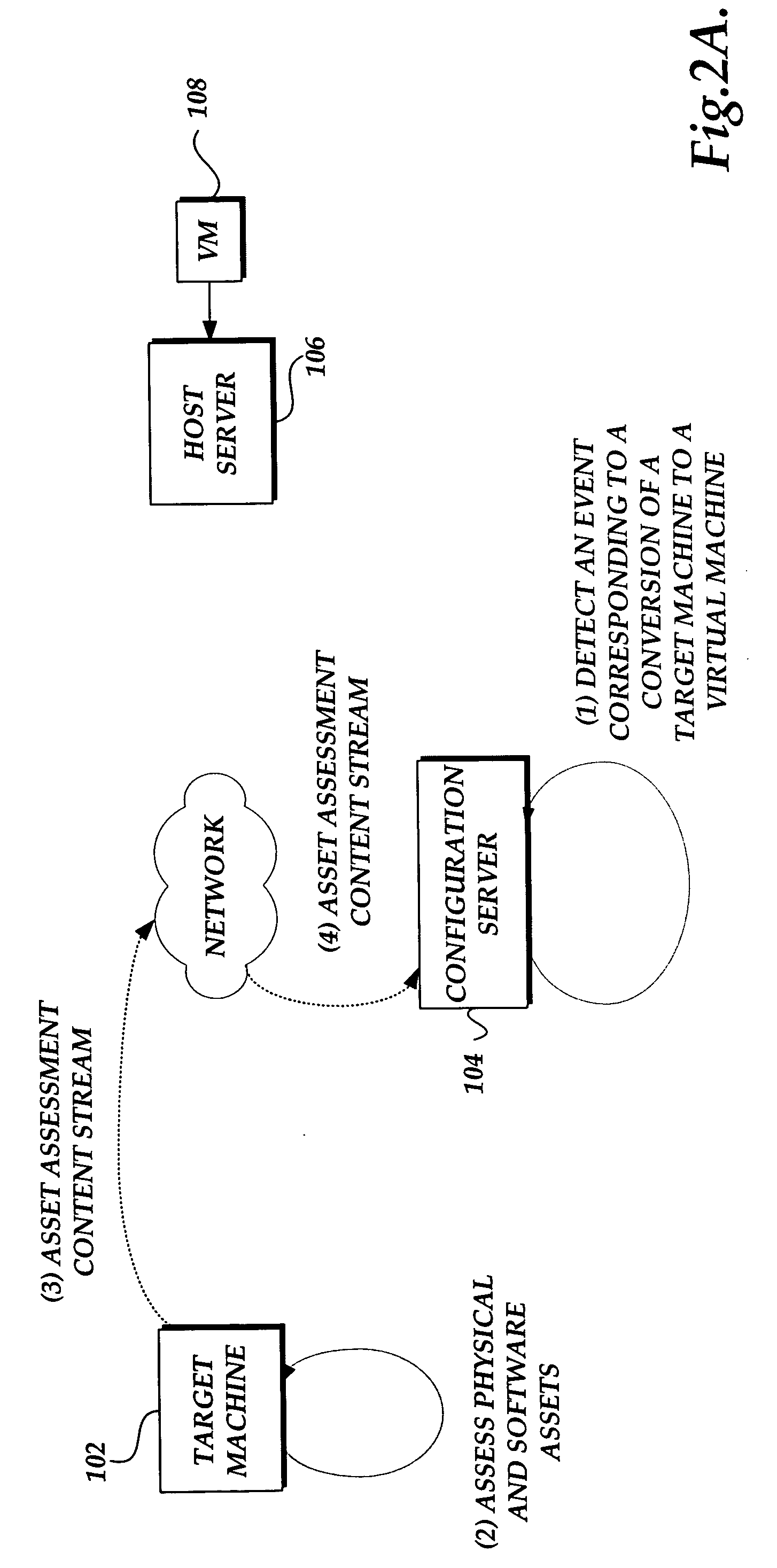
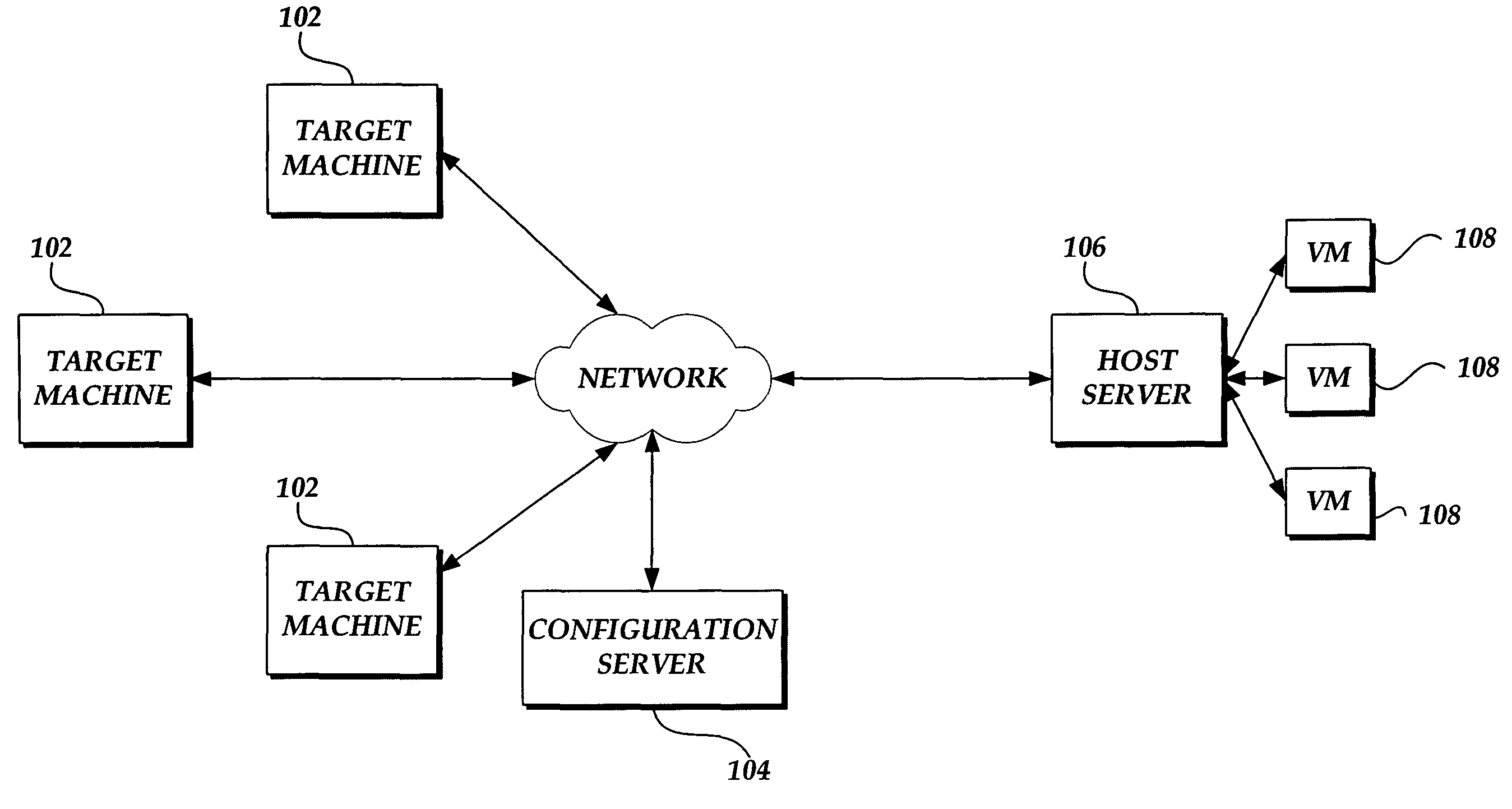
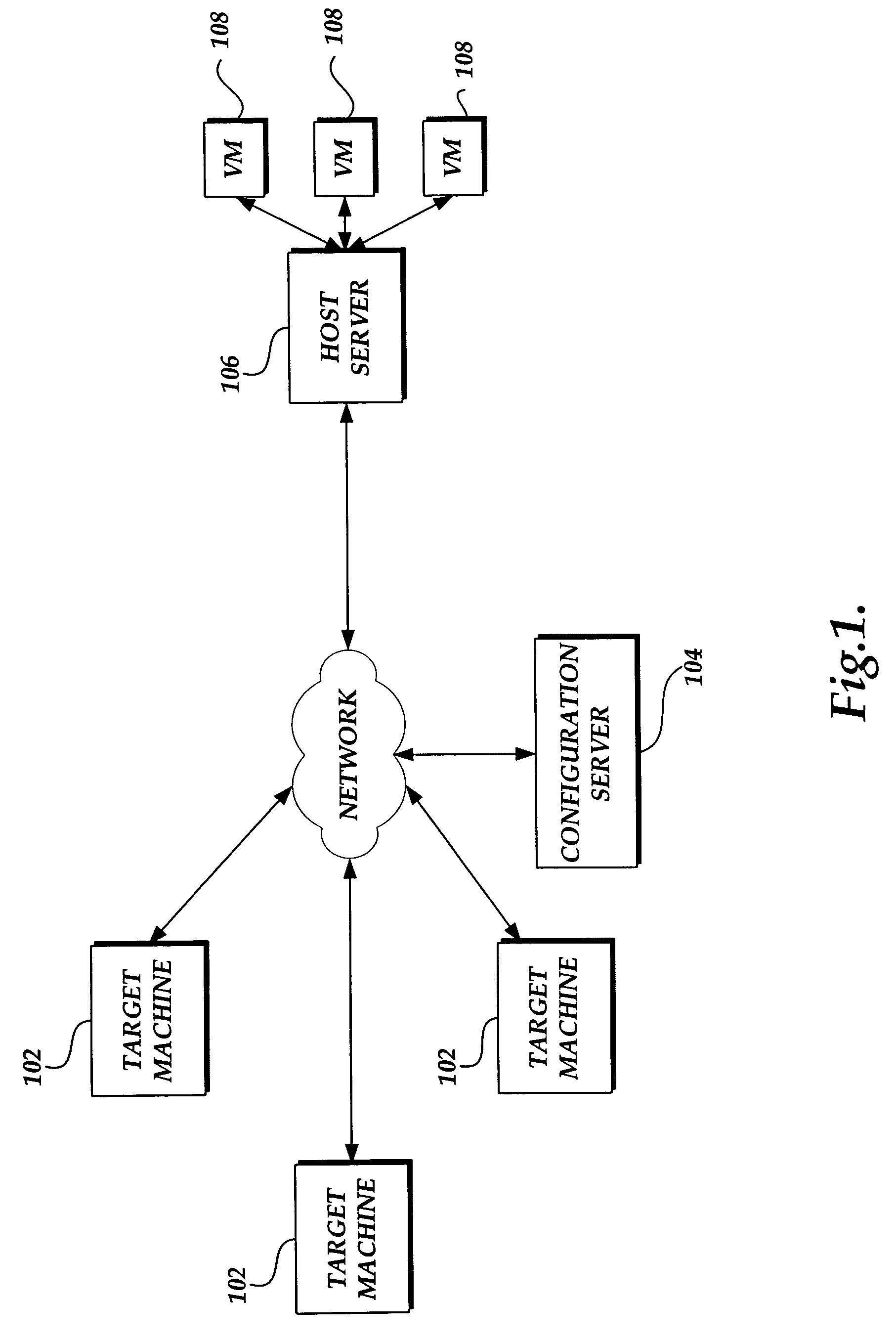
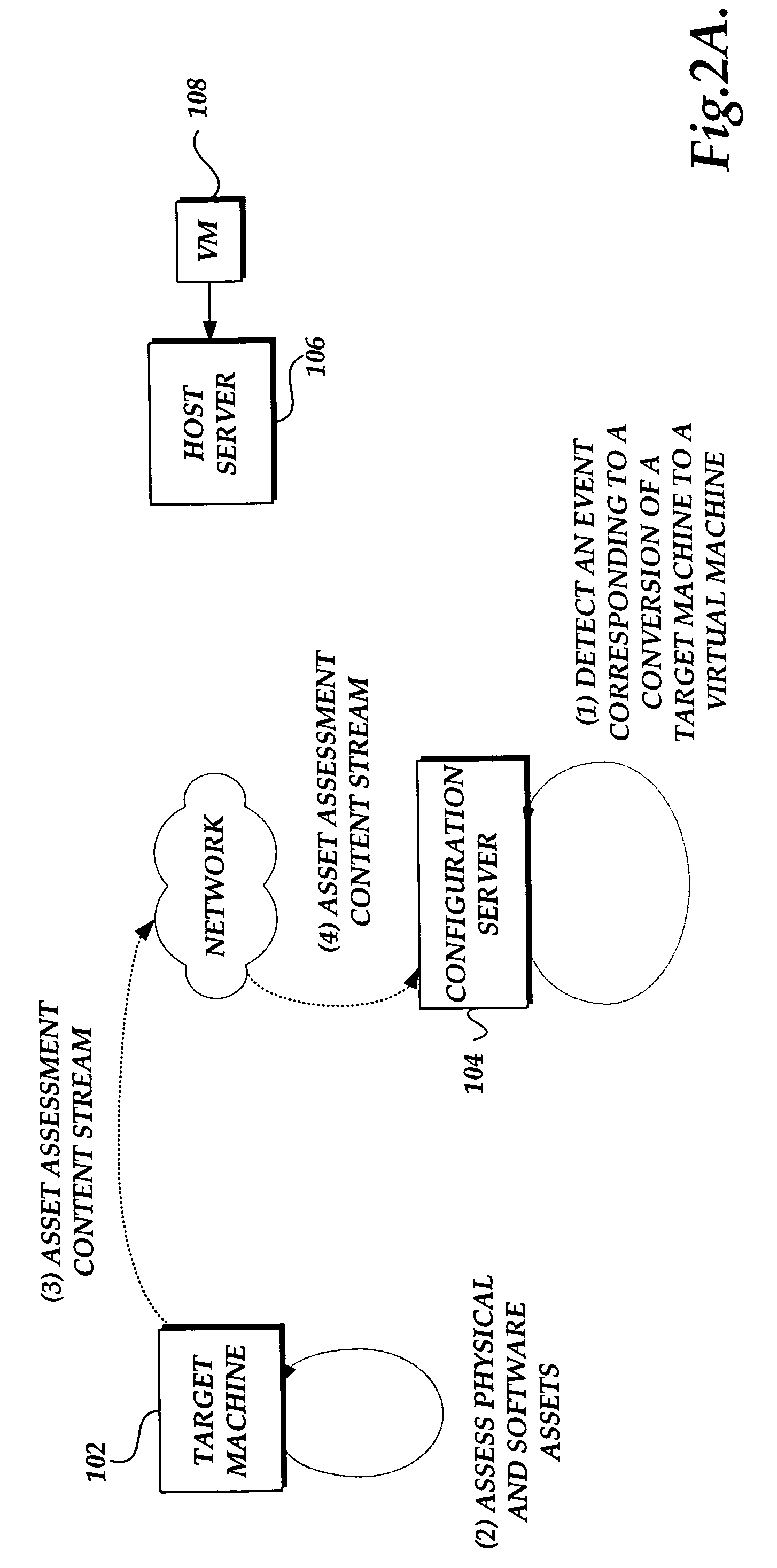
System and method for converting a target computing device to a virtual machine in response to a detected event
ActiveUS20060294516A1Digital computer detailsSoftware simulation/interpretation/emulationVirtual machineSoftware assets
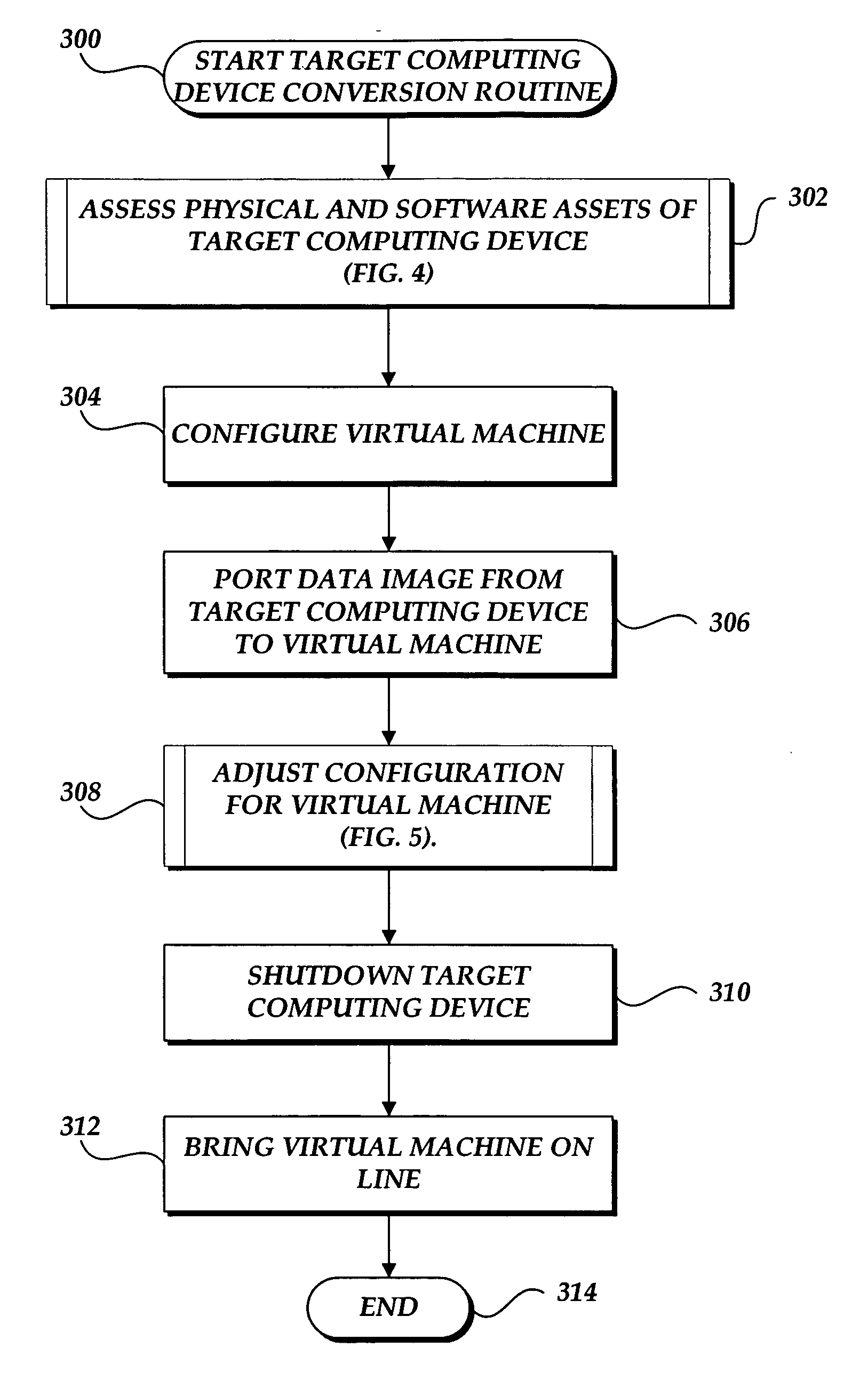
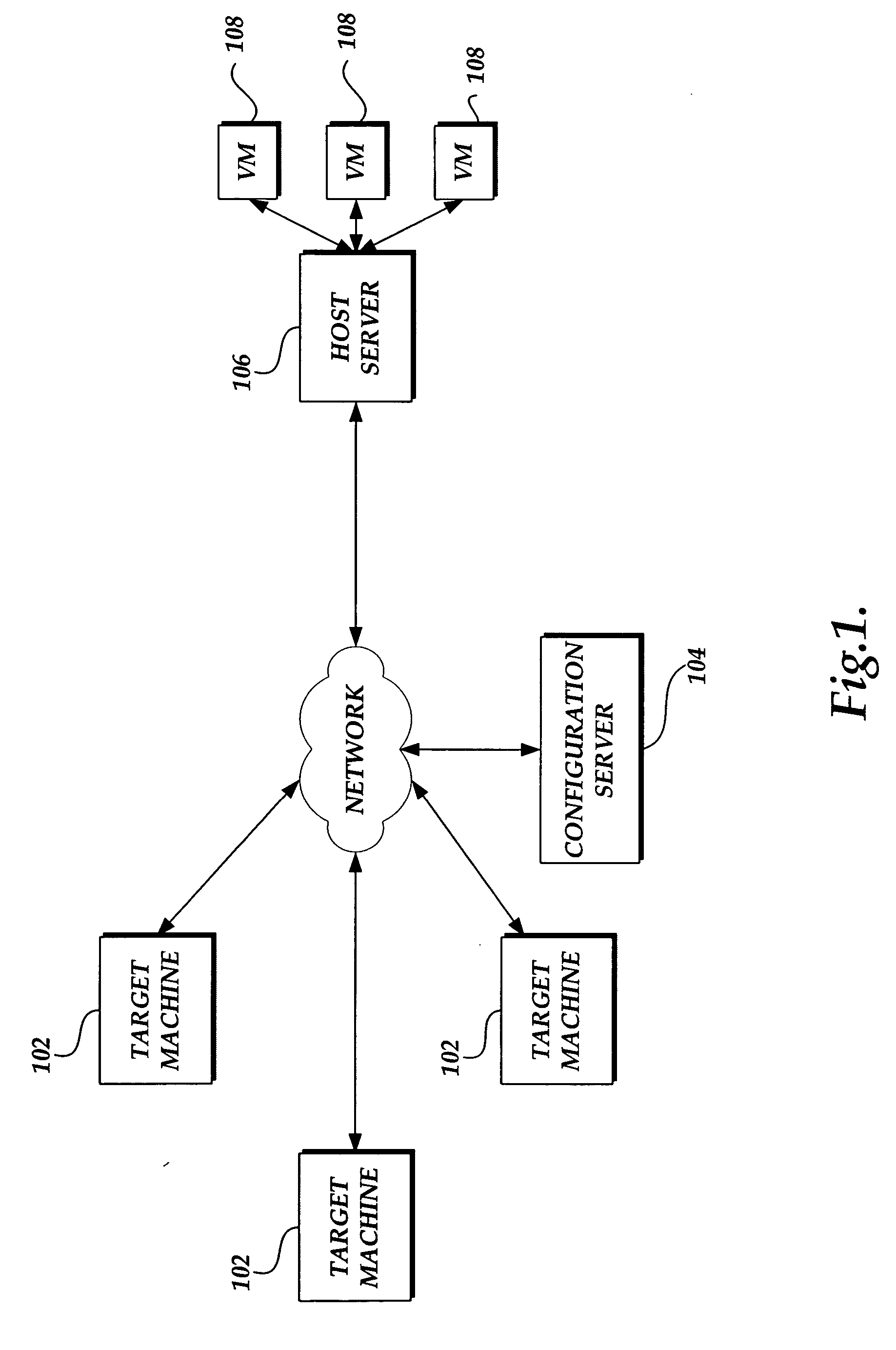
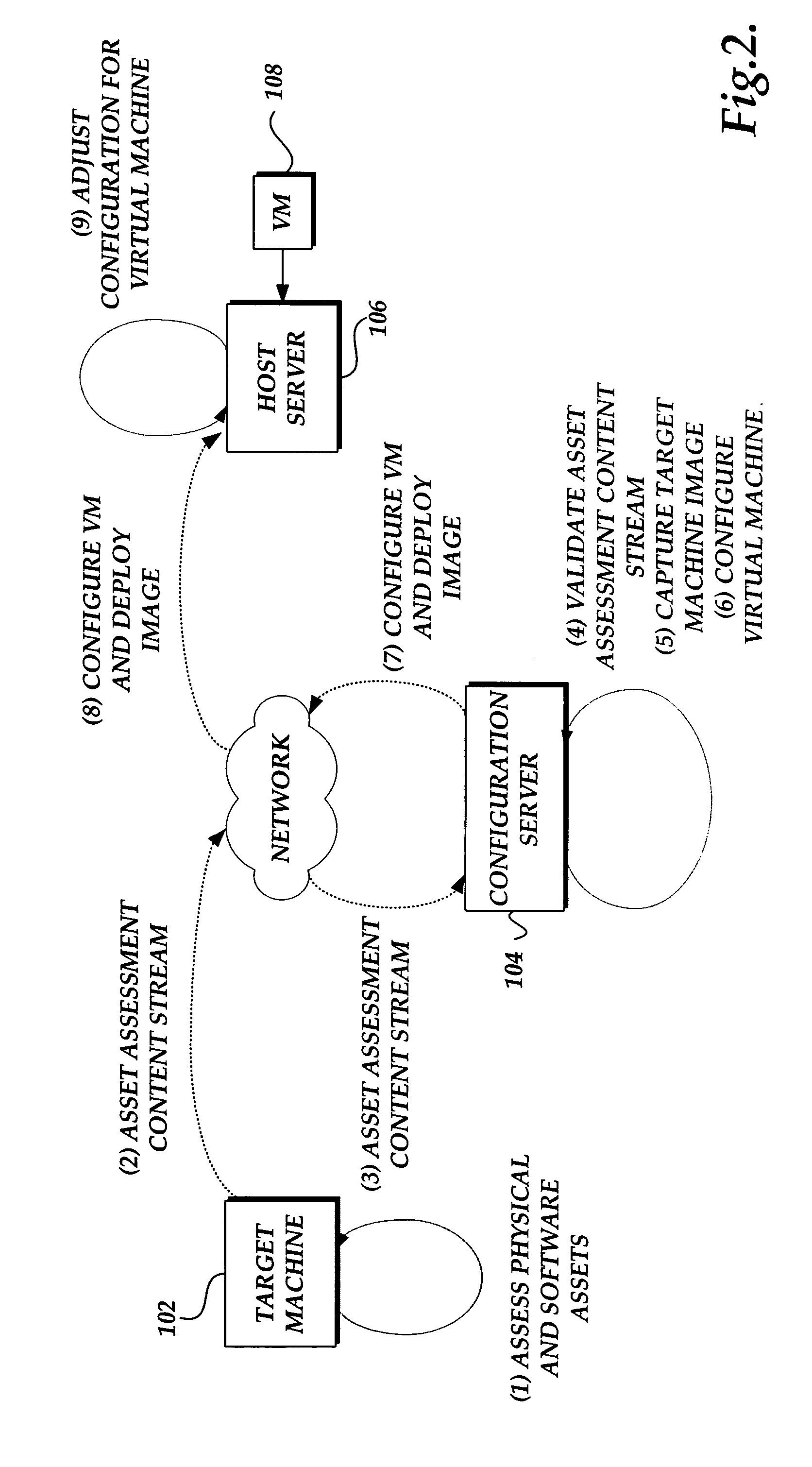
A system and method for converting a target computing device to a virtual machine are provided. A conversion event is detected to initiate a conversion of a target computing device to a virtual machine. An assessment of the physical and software assets of a target computing device are obtained. A data image of the target computing device is deployed on an instance of a virtual machine. The virtual machine adjusted to correspond to the physical and software assets of the target computing device.
Owner:SERVICENOW INC
Development System with Improved Methodology for Creation and Reuse of Software Assets
ActiveUS20090210855A1Easy to createVersion controlReverse engineeringApplication softwareImproved method
A development system with improved methodology for creation and reuse of software assets is shown and described. In one embodiment, for example, in a development system, a method is described for facilitating creation of a reusable application, the method comprises steps of: during development of the application, capturing knowledge and intent of the application's original developer alongside source code created for the application; producing an archival module storing the source code for the application together with metadata capturing the knowledge and intent of the original developer, the metadata including at least one script guiding subsequent developers in use and modification of the source code for the application; and consuming the archival module by a follow-on developer, including executing the at least one script for facilitating creation of a reusable version of the application.
Owner:EMBARCADERO TECHNOLOGIES
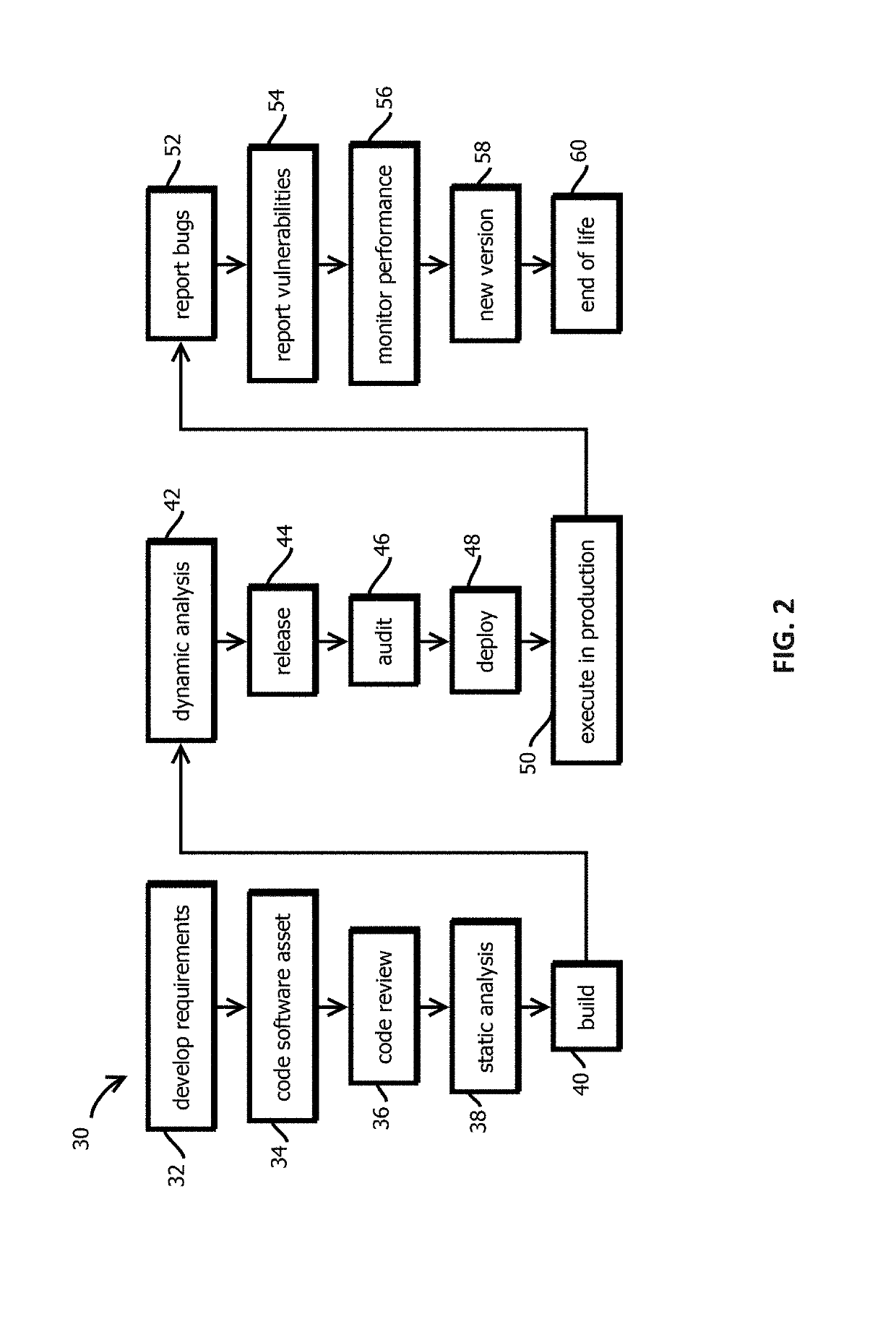
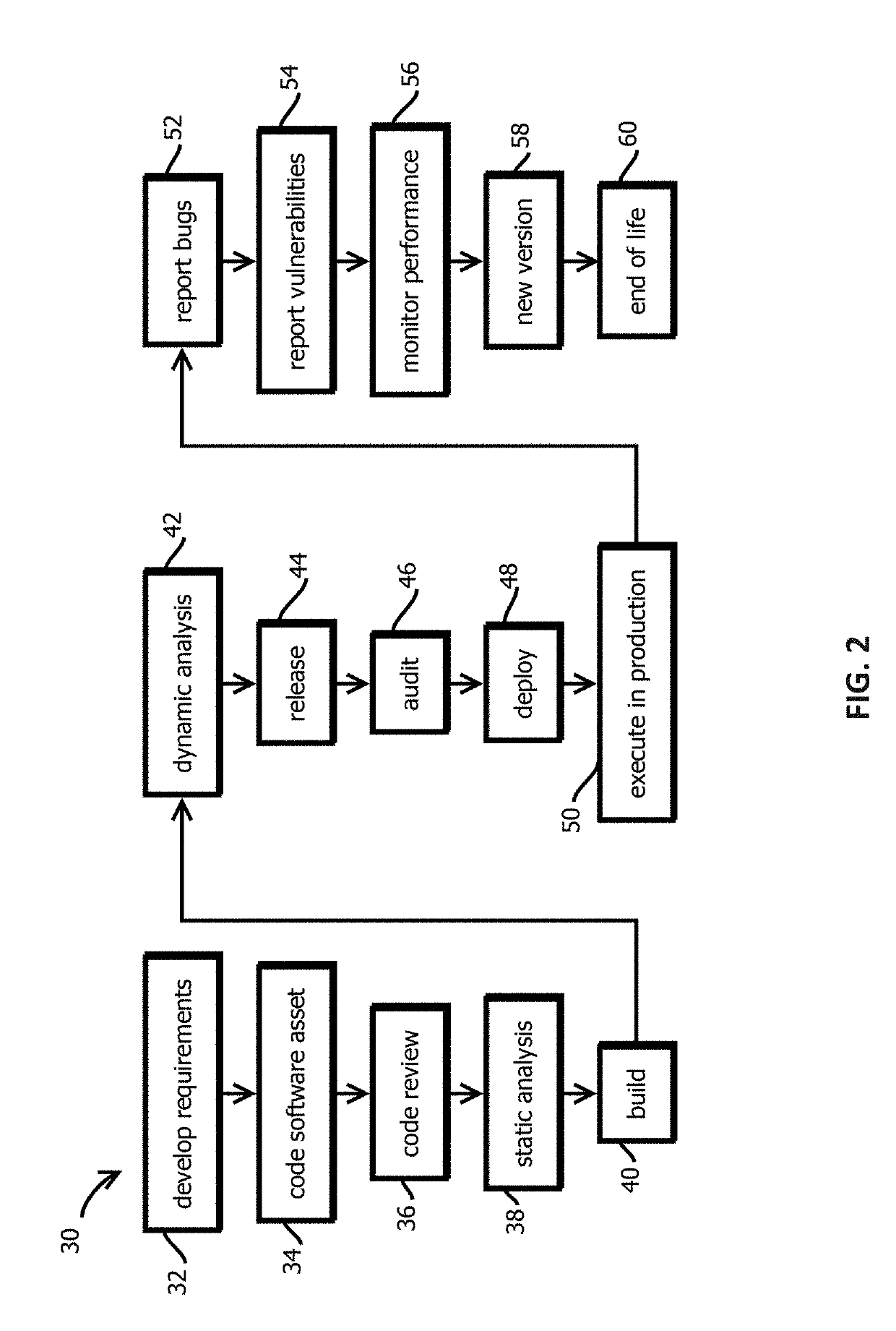
Announcement smart contracts to announce software release
InactiveUS20190305959A1User identity/authority verificationVersion controlDocumentation procedureCryptographic nonce
Provided is a process that includes: calling a program executed on a decentralized computing platform configured to persist state to a blockchain, the call requesting the program to release the software asset to the production environment, wherein: respective instances of the program are configured to publish release documentation by which provenance of the software asset is verifiable to the blockchain, respective instances of the program are configured to verify a cryptographic signature associated with the software asset, the cryptographic signature establishes that the software asset being released has not been tampered with subsequent to signing, the cryptographic signature establishes that the releasing entity or a proxy of the releasing entity has access to a cryptographic key by which the cryptographic signature was formed, and the decentralized computing platform is configured to reach a consensus verification determination among verification results from the replicated instances of the program.
Owner:CA TECH INC
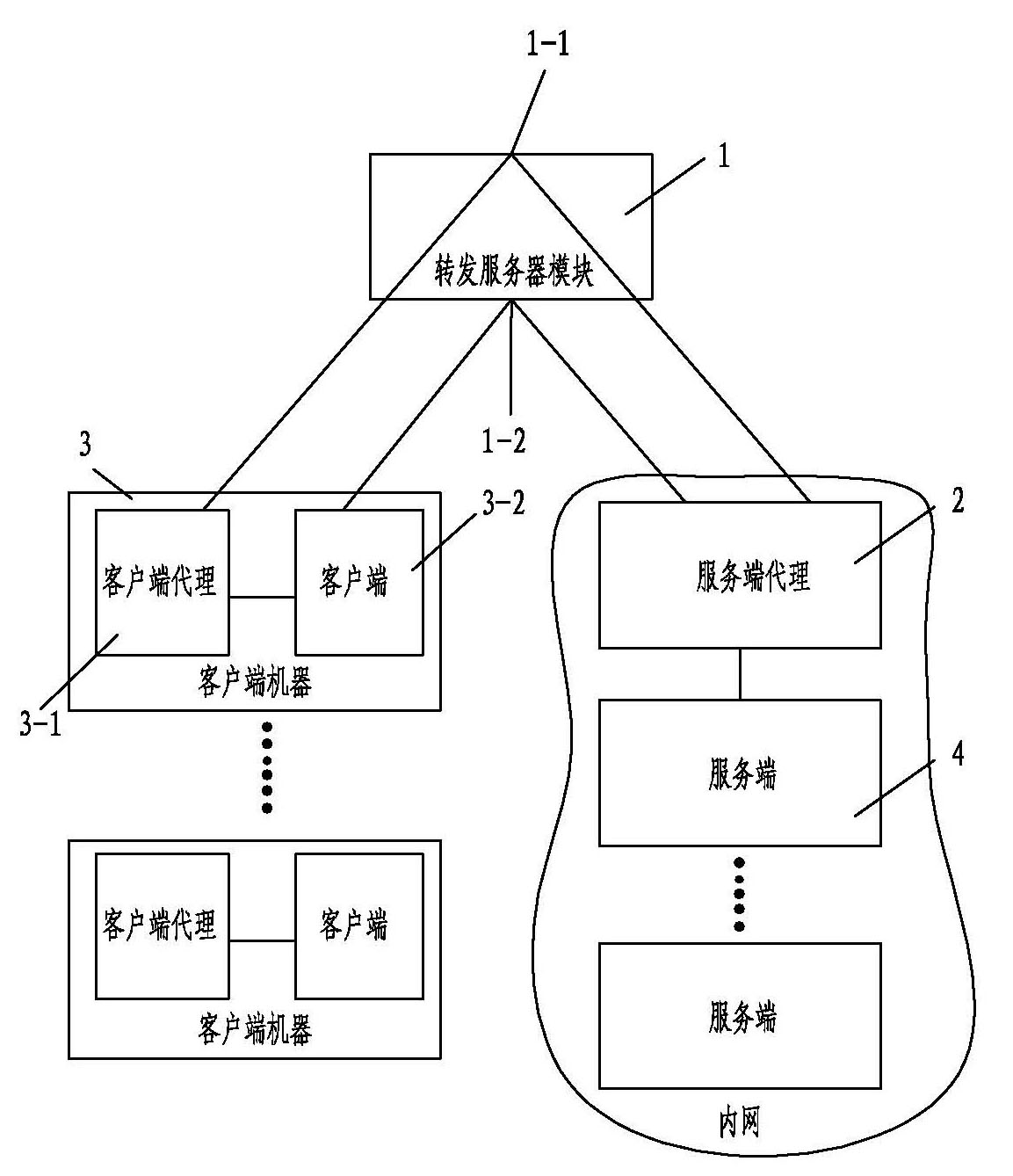
Method for converting TCP network communication server into client
The invention relates to a method for converting a transmission control protocol (TCP) network communication server into a client. The method comprises the following steps of: establishing a forwarding server providing data forwarding in a TCP network, and establishing connection between at least one internal network server machine and the forwarding server through a command port and a data port;establishing connection between at least one external network client machine and the forwarding server through the command port and the data port; and setting the internet protocol (IP) address of the TCP network, the command port and the data port in the forwarding server, wherein the forwarding server monitors the command port and the data port all the time. The forwarding server is used for service registry, service query, communication relay and the like; the internal network server machine does not directly expose services for an external network, so the security of the internal network is improved, fixed IP configuration is not needed, and precious resource of fixed IP is reduced; and because the method is a TCP communication forwarding-based general realization method, the conventional server software and client software do not need modifying, and the conventional software assets can be fully utilized.
Owner:BEIJING DAYANG TECH DEV
Consistent Method System and Computer Program for Developing Software Asset Based Solutions
ActiveUS20080288944A1Highly flexible toolsBig economyMultiprogramming arrangementsVisual/graphical programmingReusable softwareUser input
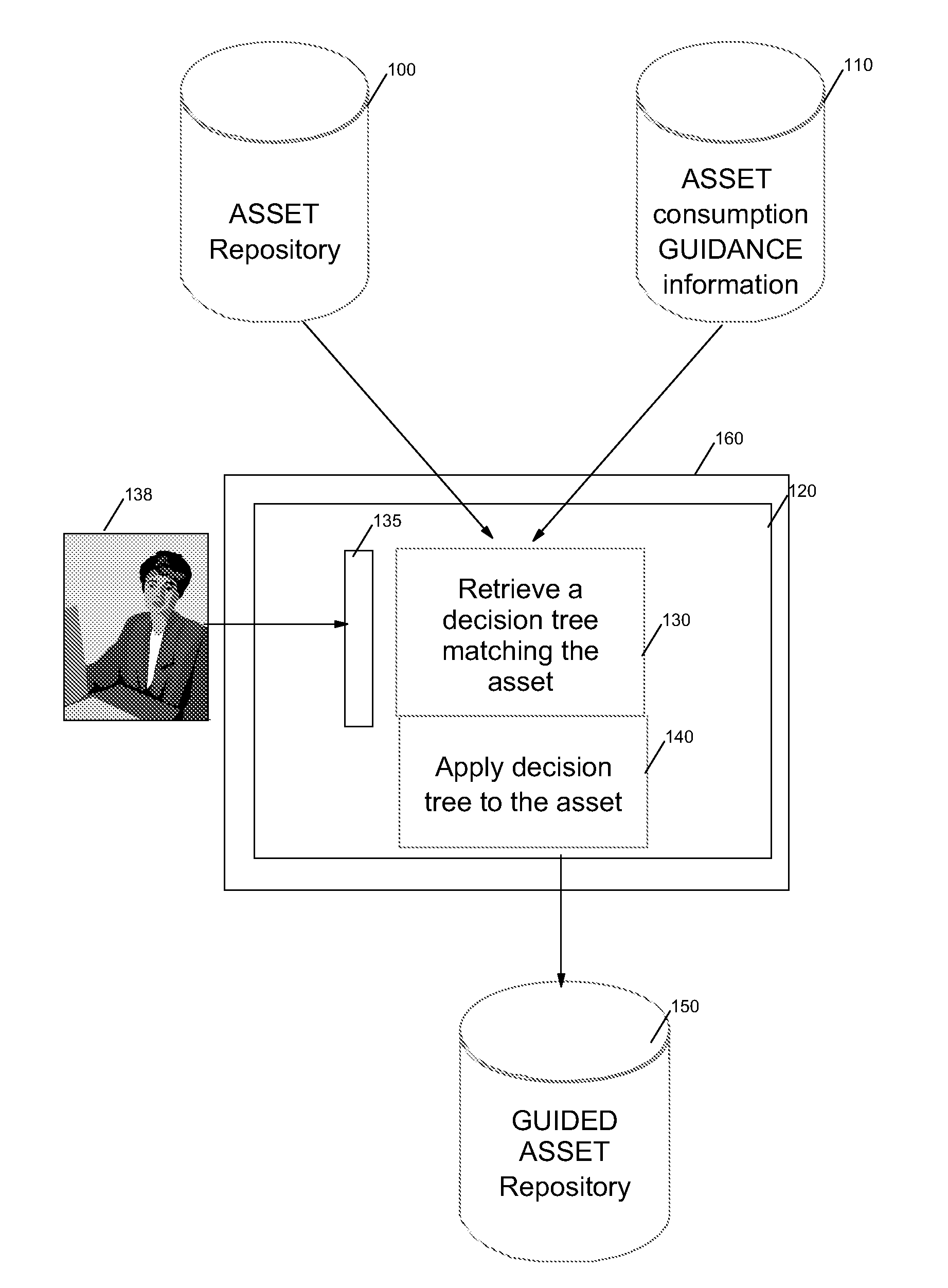
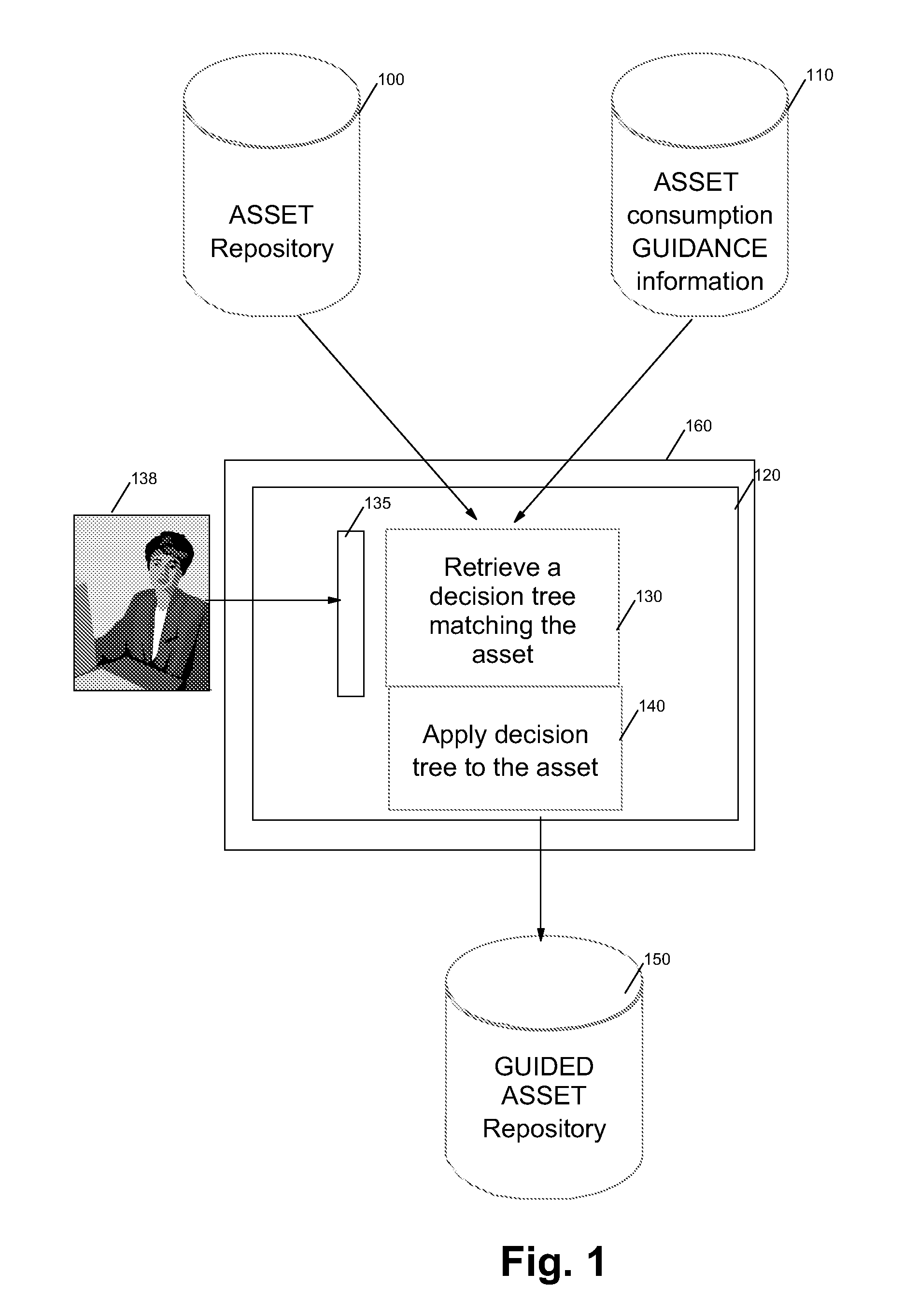
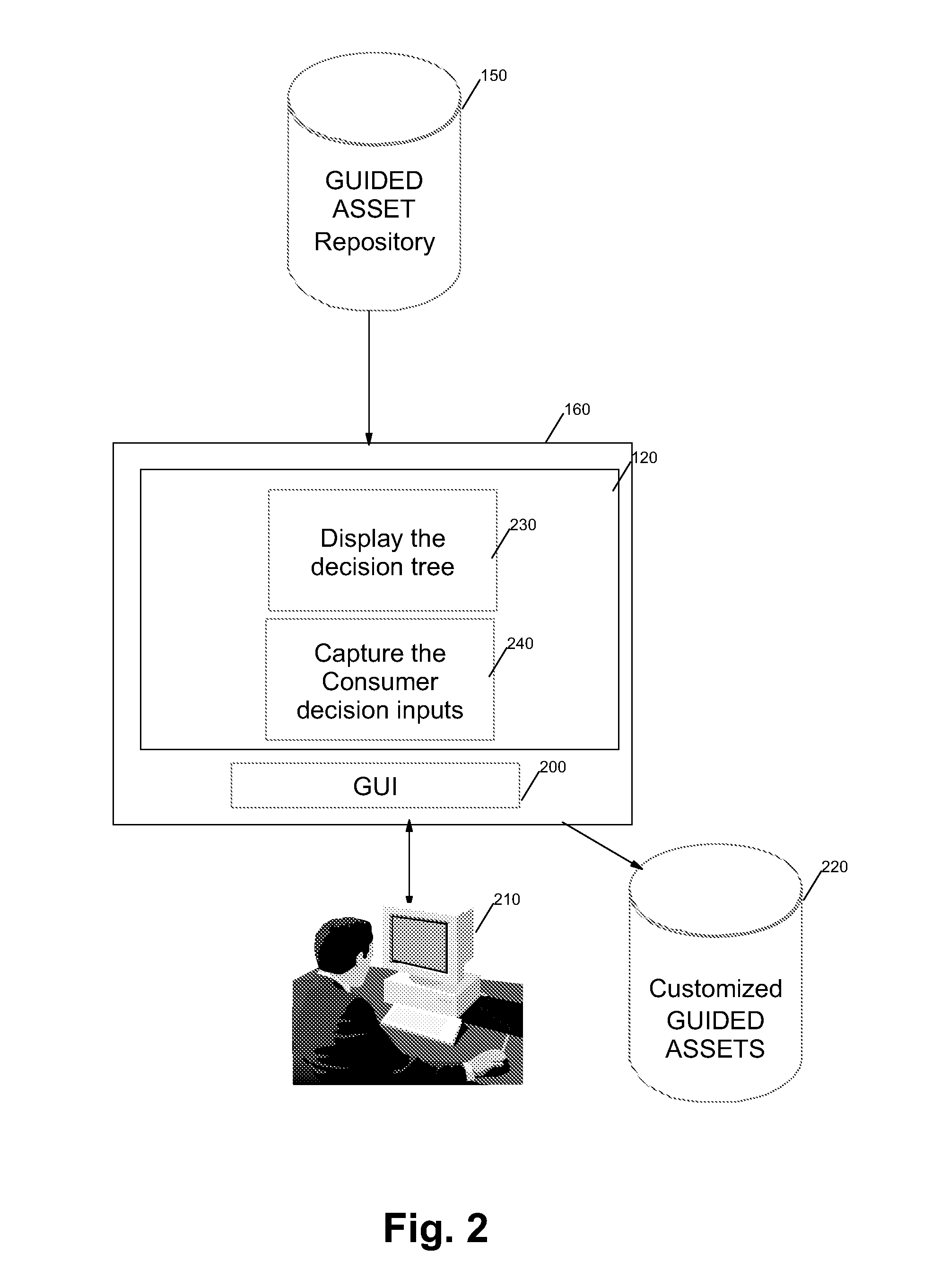
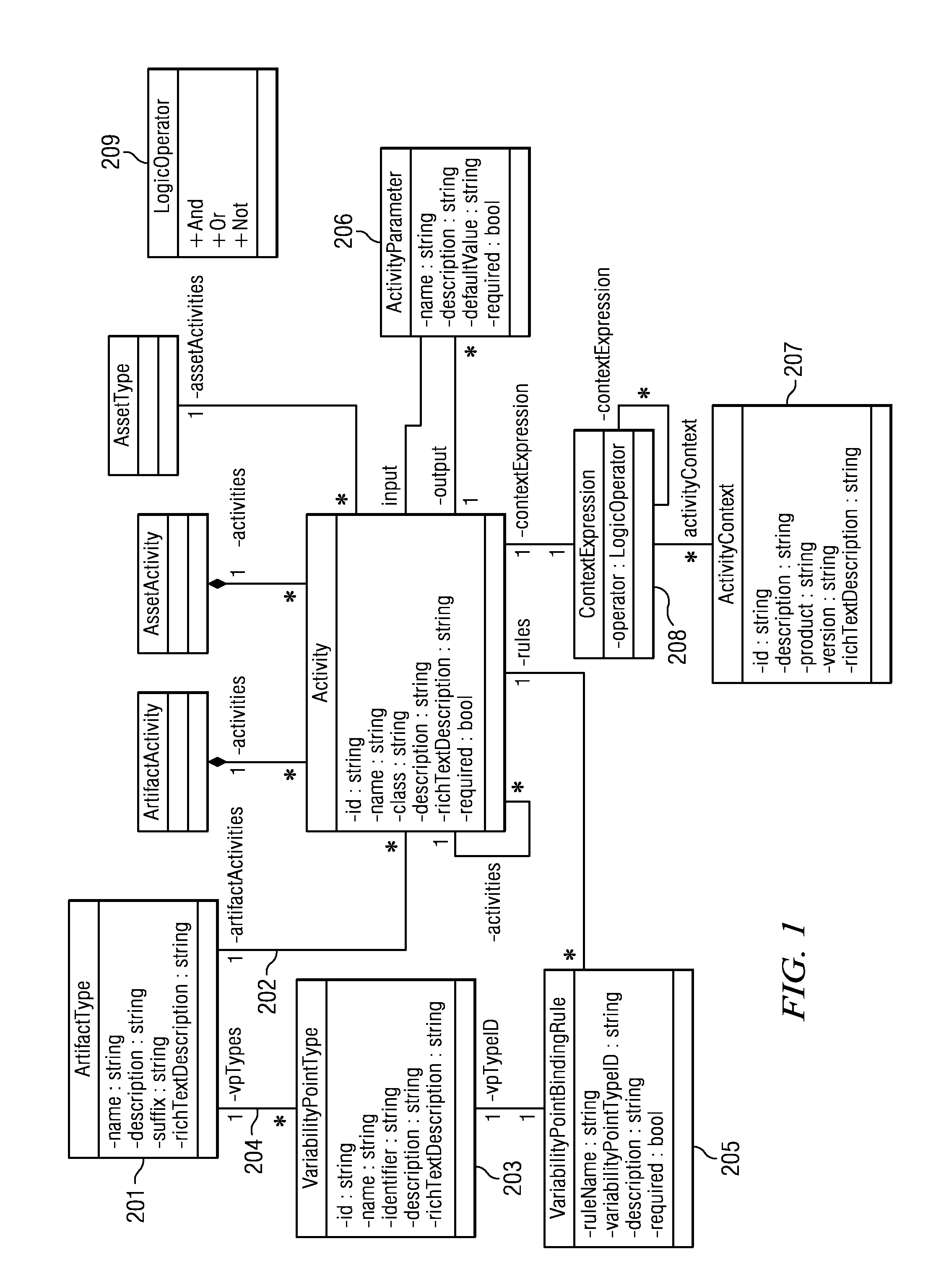
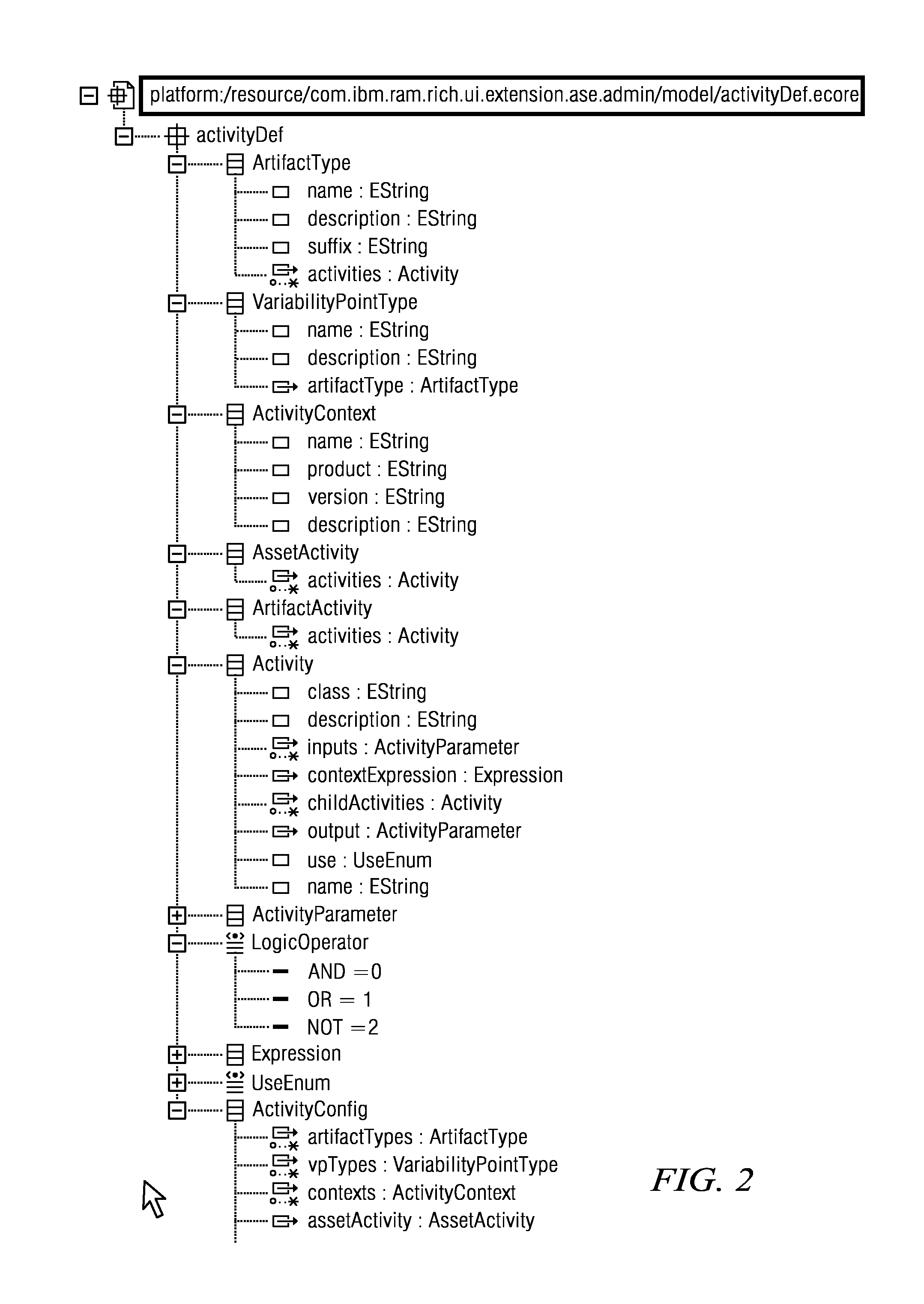
A method, computer program and system for consuming reusable software assets, said assets being described with elements and attributes, said assets containing at least one variable element (VPs) themselves containing at least one variant. The user executes a program on a computer by first choosing the asset to be consumed. A decision tree corresponding to the asset is traversed, each decision point corresponding to a variable element. The decision point is processed by asking the user inputs to modify the variants of the corresponding variable elements. The modified variable elements are stored. The dependency of the decision point is indicated by a dependency attribute in the variable element.The program can stop at the initiative of the user or when the decision tree is completely traversed. When the decision tree has been partially traversed, the program can be restart after the last decision point processed starting from the partially modified corresponding variable element.
Owner:IBM CORP
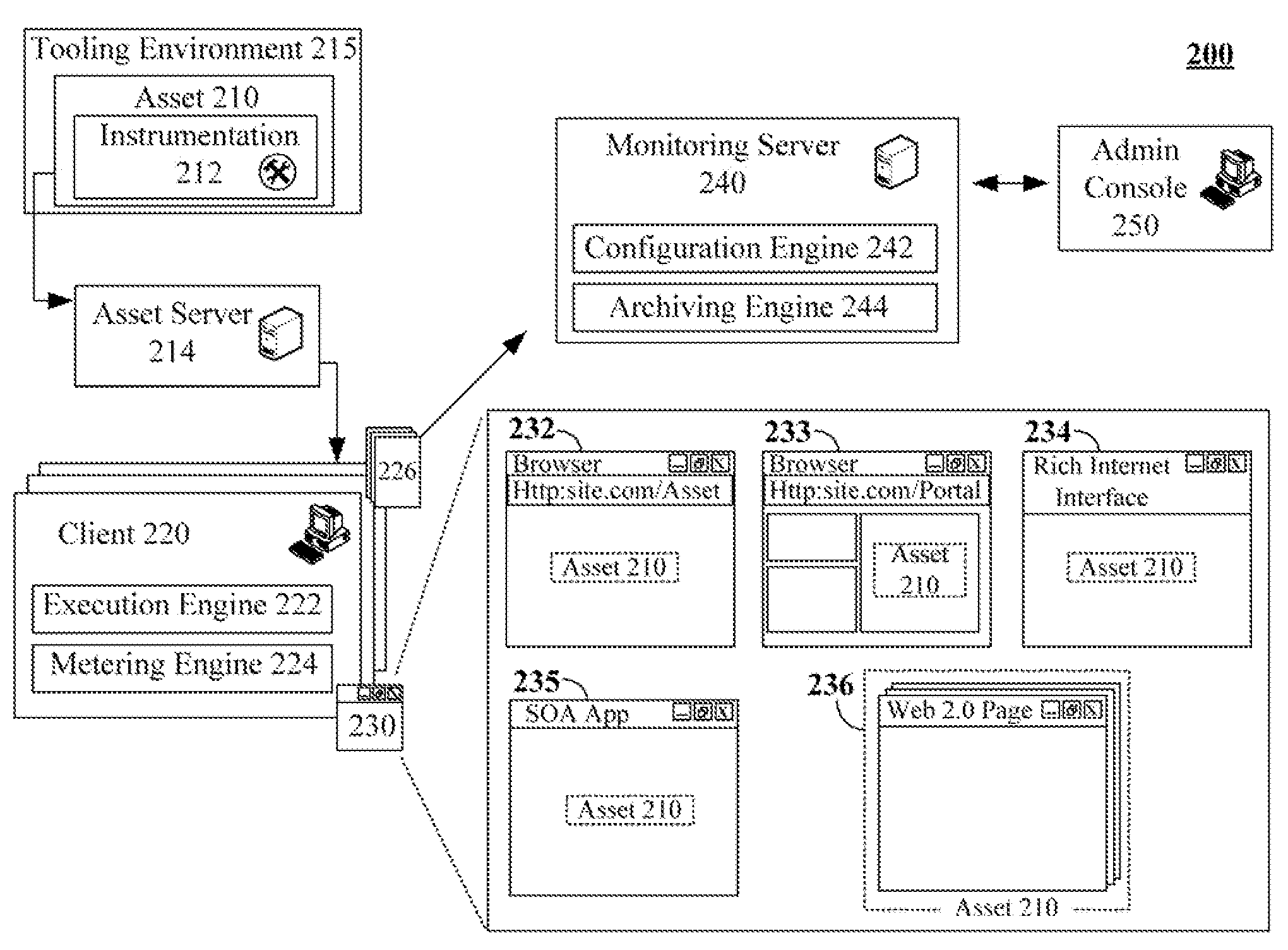
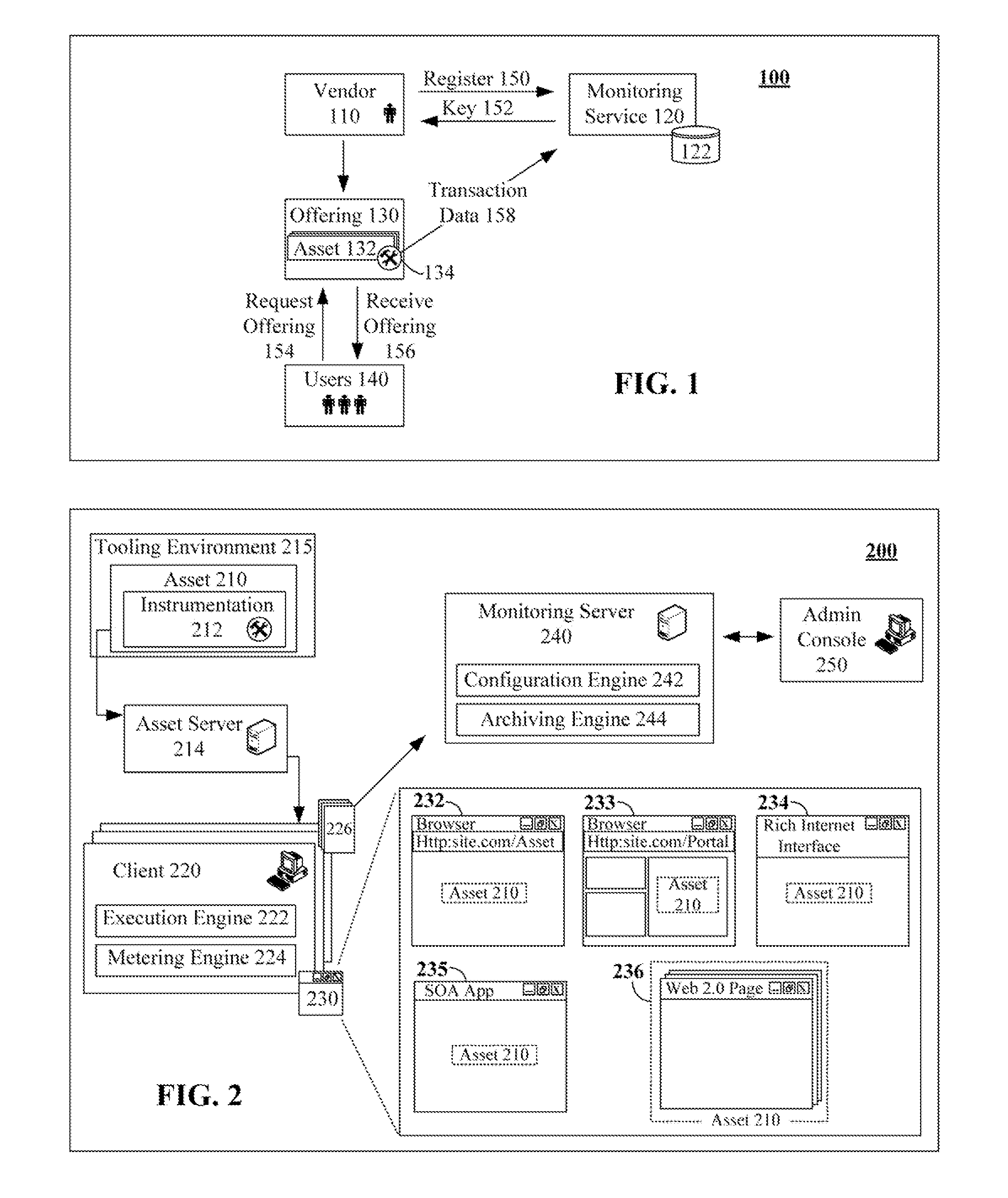
Non-intrusive asset monitoring framework for runtime configuration of deployable software assets
The present invention discloses a solution for metering, monitoring, and monetizing software assets. The solution can include a step of registering a software asset with a monitoring service. A unique identifying key for the software asset can be generated during registration. The software asset can then be instrumented for the monitoring service. The instrumentation can reference the software asset by the unique key. Specifics of the set of metrics that are to be monitored by the monitoring service for the software asset can be runtime, development time, and / or deployment time configurable. The instrumented software asset can convey transaction data to the monitoring server when used by clients. Analyzed results produced by the monitoring service pertaining to the software assets based upon the transaction data can be provided to authorize users of vendors associated with the software asset.
Owner:IBM CORP
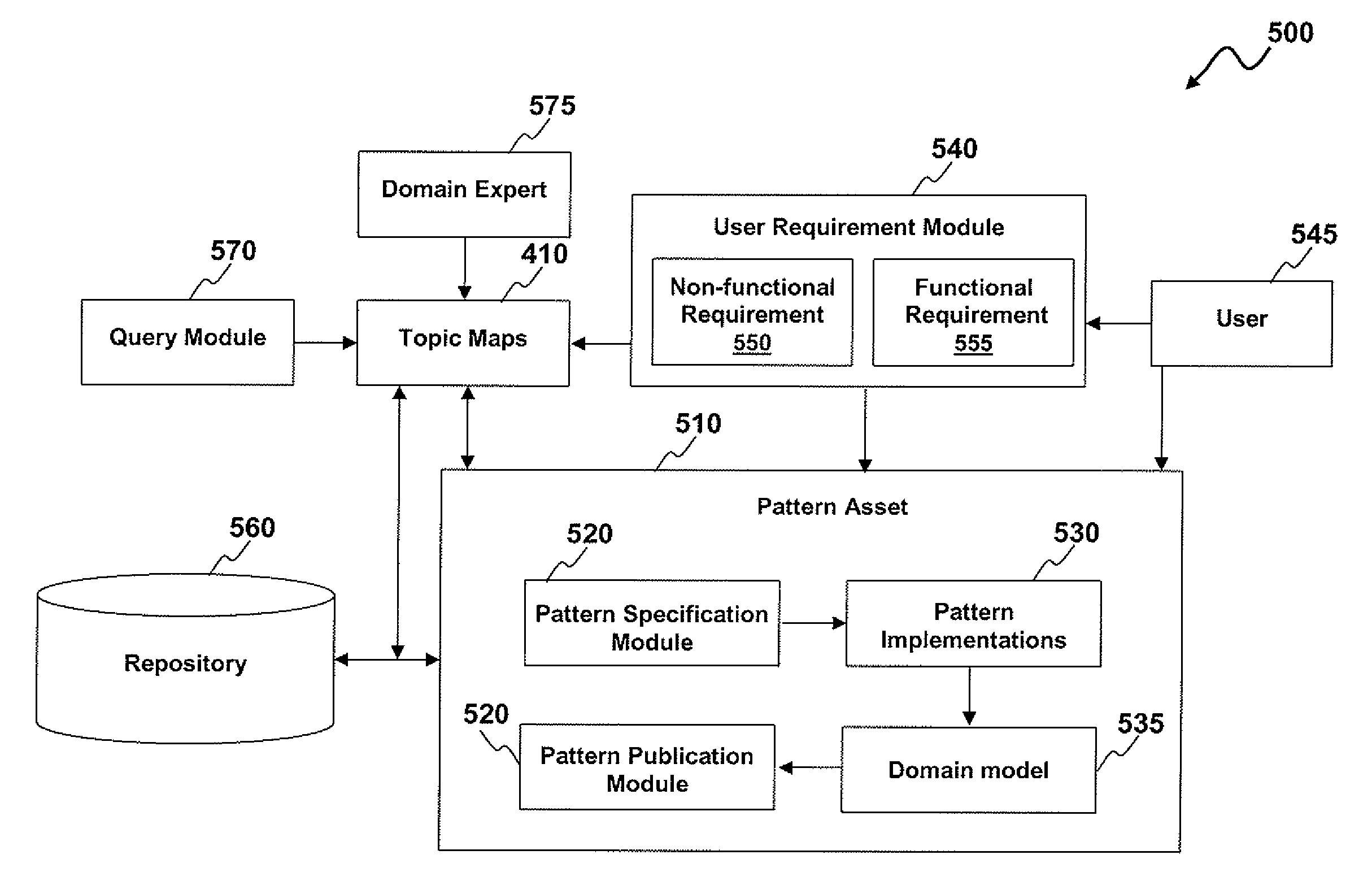
Asset adviser intelligence engine for managing reusable software assets
InactiveUS20090210390A1Software reuseSpecial data processing applicationsTopic MapsReusable software
A computer implemented method, system and computer program product for managing reusable software assets based on software requirements. A topic map can be expressed utilizing semantic web technology in order to model a relationship between a software requirement and a reusable software asset. The relationship includes the software assets needed to satisfy the software requirement, relationship between the software assets, and the location of the software assets. The semantic web representation can then leverage a standard web based query mechanism to allow meaningful queries to suggest best software assets to be utilized with the software requirement. The semantic web representation can also leverage standard XML (extensible markup language) tooling to provide consistence checking and inferencing of new data.
Owner:IBM CORP
System and method for managing IT assets
InactiveUS7747738B2Improve efficiencyReduce the amount requiredFinanceDigital computer detailsAmbulatory systemRelevant information
Owner:CA TECH INC
System and method for converting a target computing device to a virtual machine
InactiveUS20070006225A1Software simulation/interpretation/emulationMemory systemsVirtual machineSoftware assets
A system and method for converting a target computing device to a virtual machine are provided. An assessment of the physical and software assets of a target computing device are obtained. A data image of the target computing device is deployed on an instance of a virtual machine. The virtual machine adjusted to correspond to the physical and software assets of the target computing device.
Owner:MICROSOFT TECH LICENSING LLC
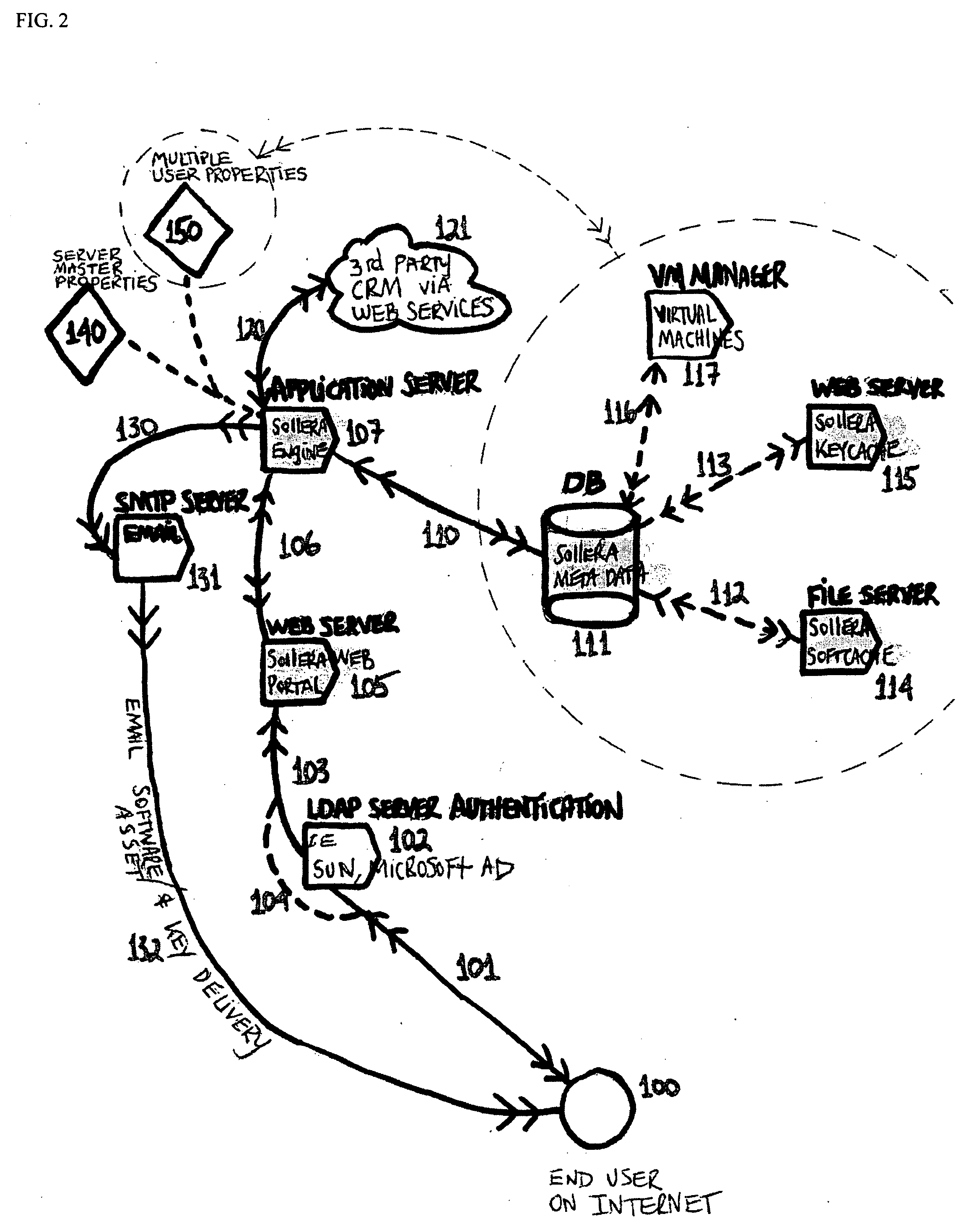
Software & license and physical/virtual machine asset management library application with check-out/check-in, front-end asset load, tracking, reporting, reconciliation and associated methods
InactiveUS20080028218A1Accurately knowManagement complexityUser identity/authority verificationComputer security arrangementsLibrary scienceManagement system
A method for providing software / license and physical / virtual machine management is disclosed for a specialized asset management system. The specialized asset management system aggregates physical and online software assets and their corresponding license(s), as well as physical and virtual machines into a unified library system wherein assets can be managed, used, reserved, tracked, reconciled, and reported on using a library check-out and check-in paradigm.
Owner:SIMON JONATHON BURTON
Identifying manner of usage for software assets in applications on user devices
InactiveUS20150172146A1Error detection/correctionDigital computer detailsUser deviceSoftware engineering
Owner:LOOKOUT MOBILE SECURITY
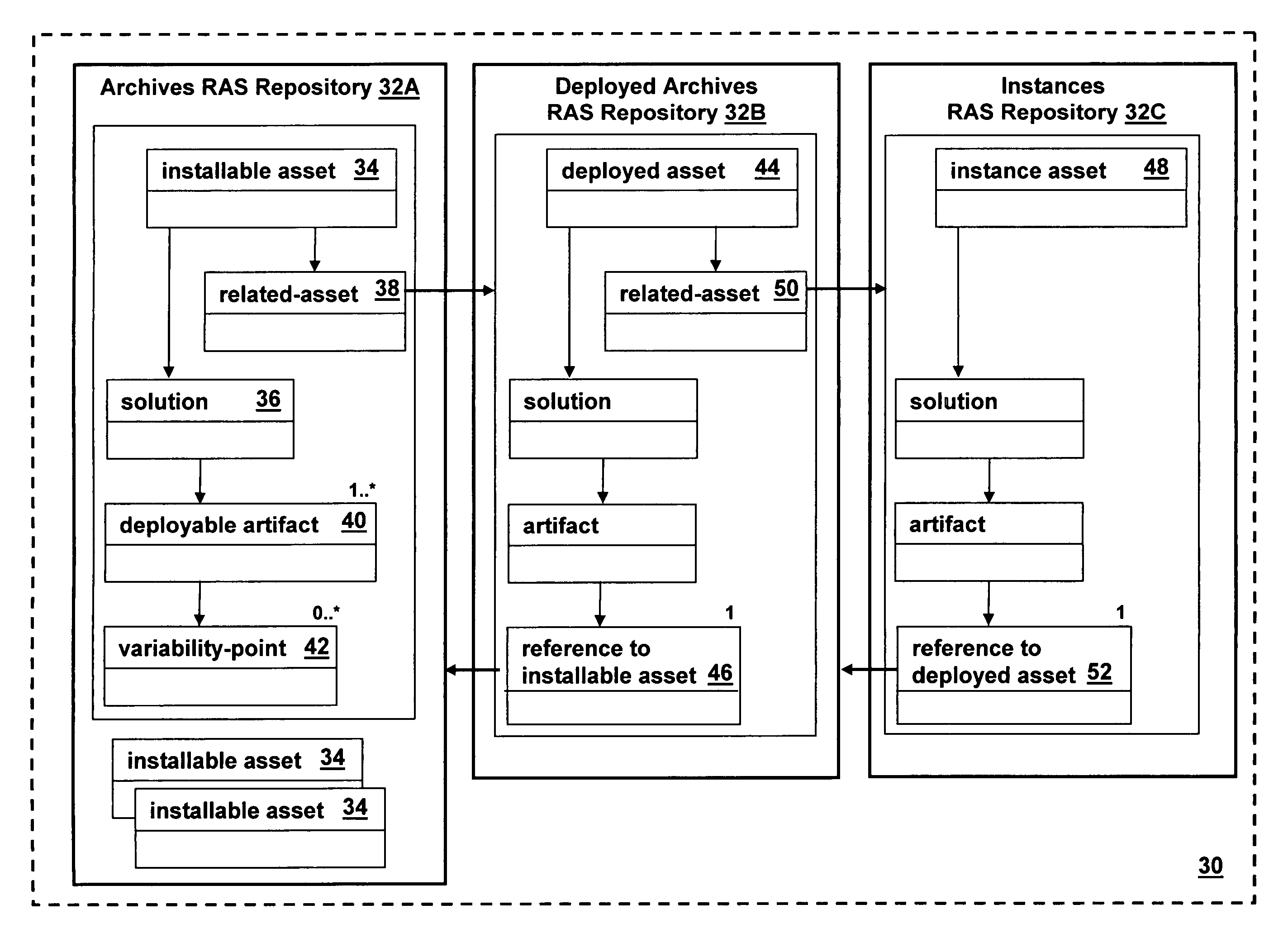
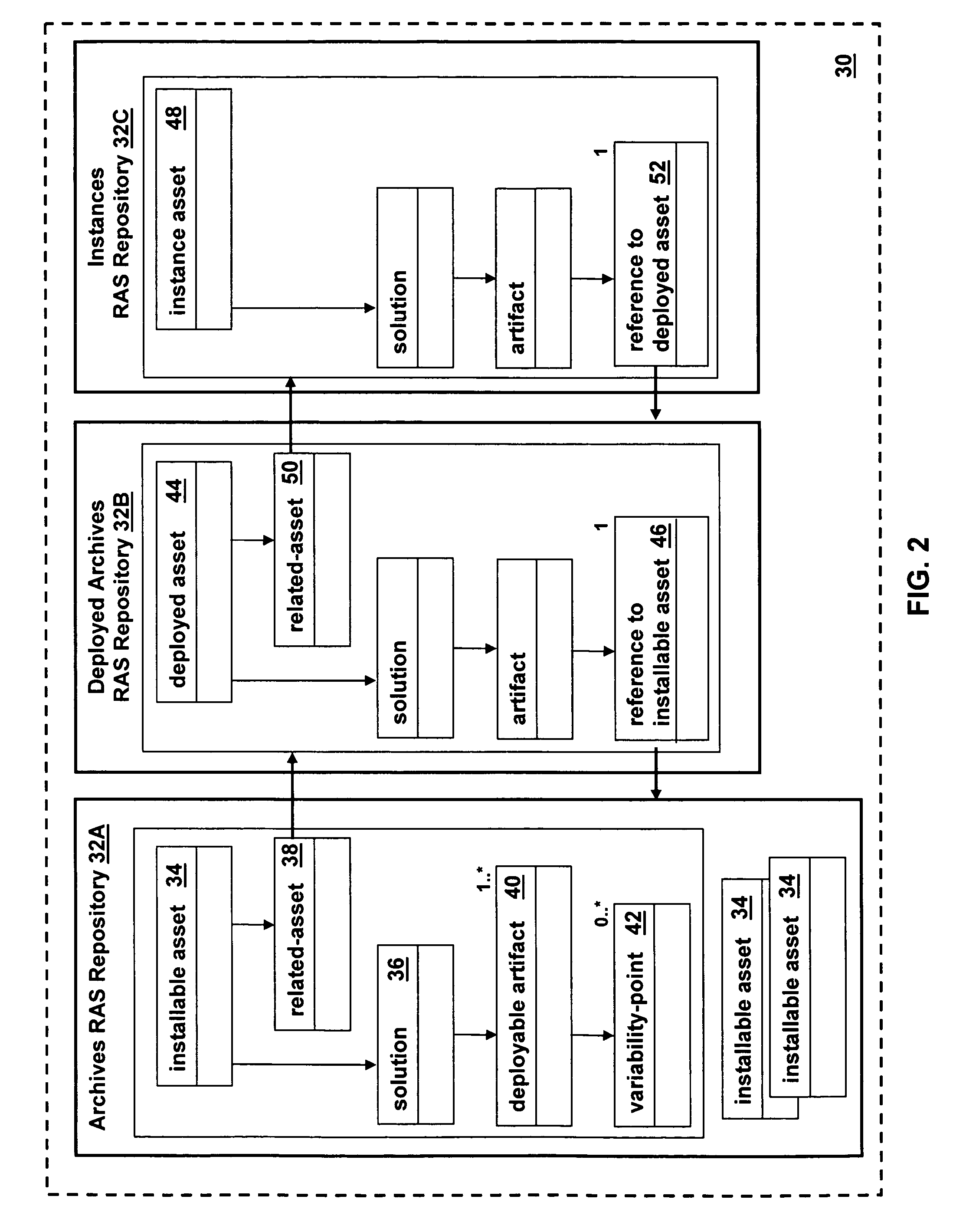
Virtual RAS repository
InactiveUS20070156764A1Software reuseSpecific program execution arrangementsSoftware engineeringComputer science
The present invention provides a virtual Reusable Asset Specification (RAS) repository. A method in accordance with an embodiment of the present invention includes: providing RAS assets for each different lifecycle phase of a software asset; and linking the RAS assets together using RAS related-assets.
Owner:IBM CORP
System and Method for Managing IT Assets
InactiveUS20080243921A1Improve efficiencyReduce the amount requiredFinanceDigital computer detailsRelevant informationTelenet
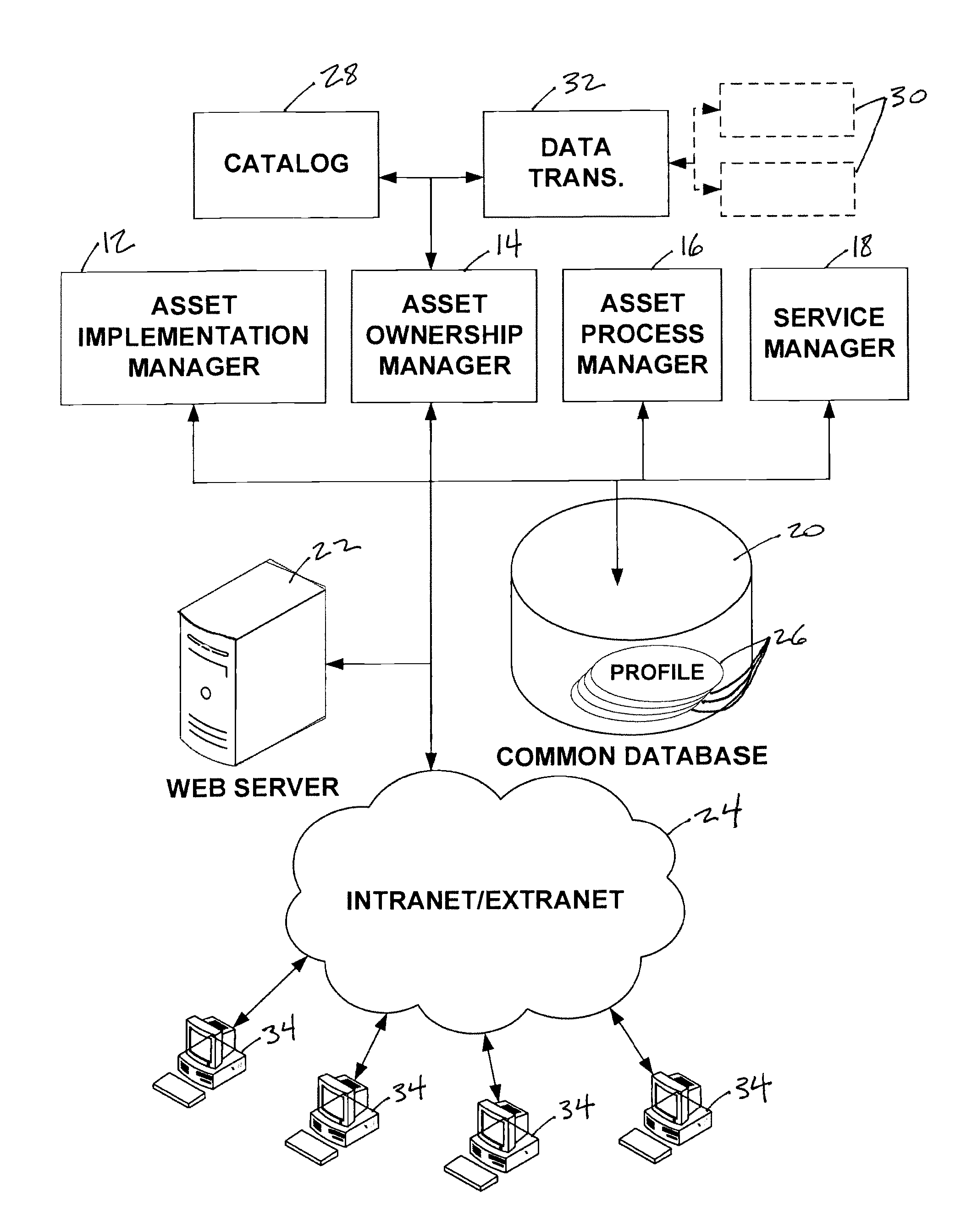
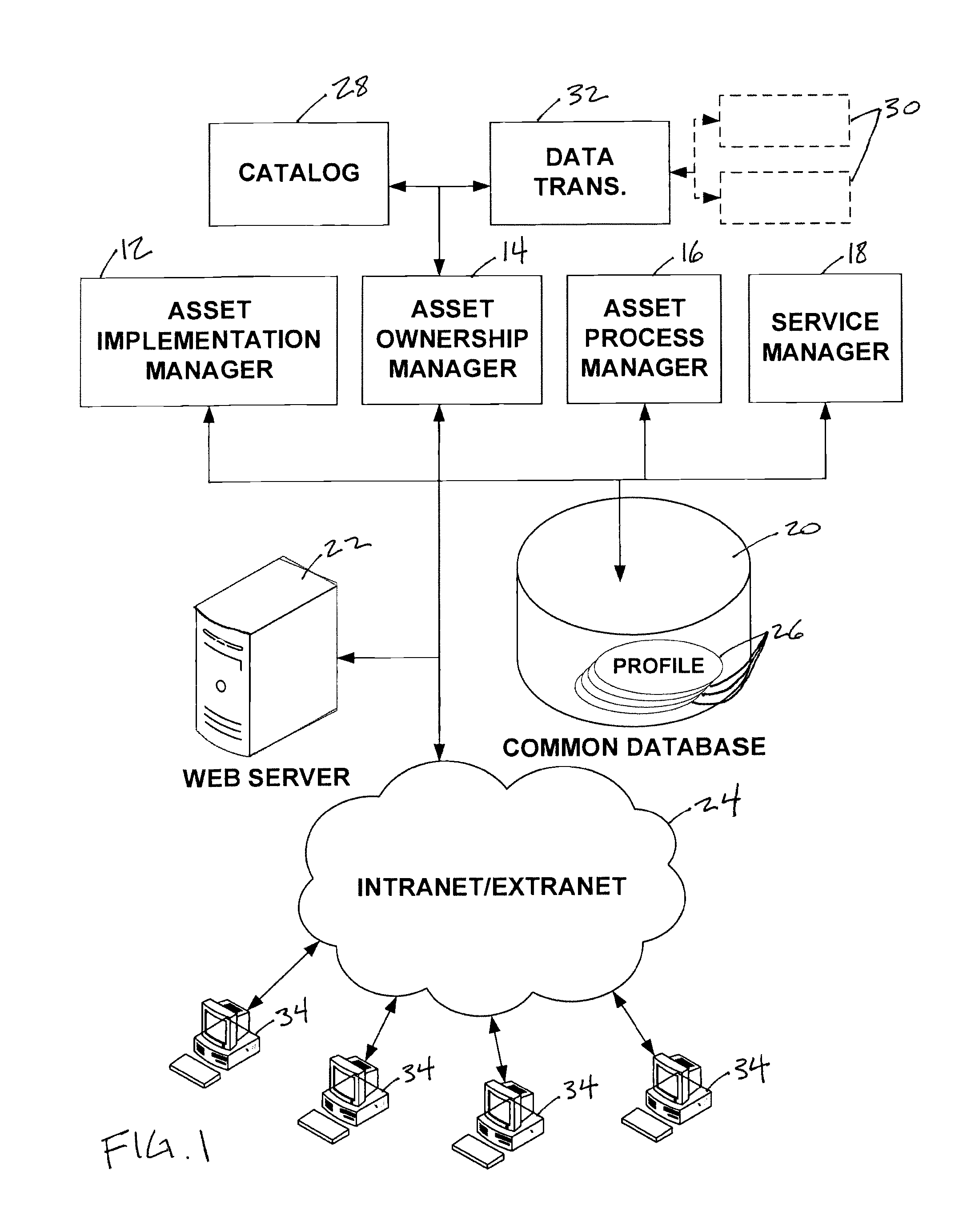
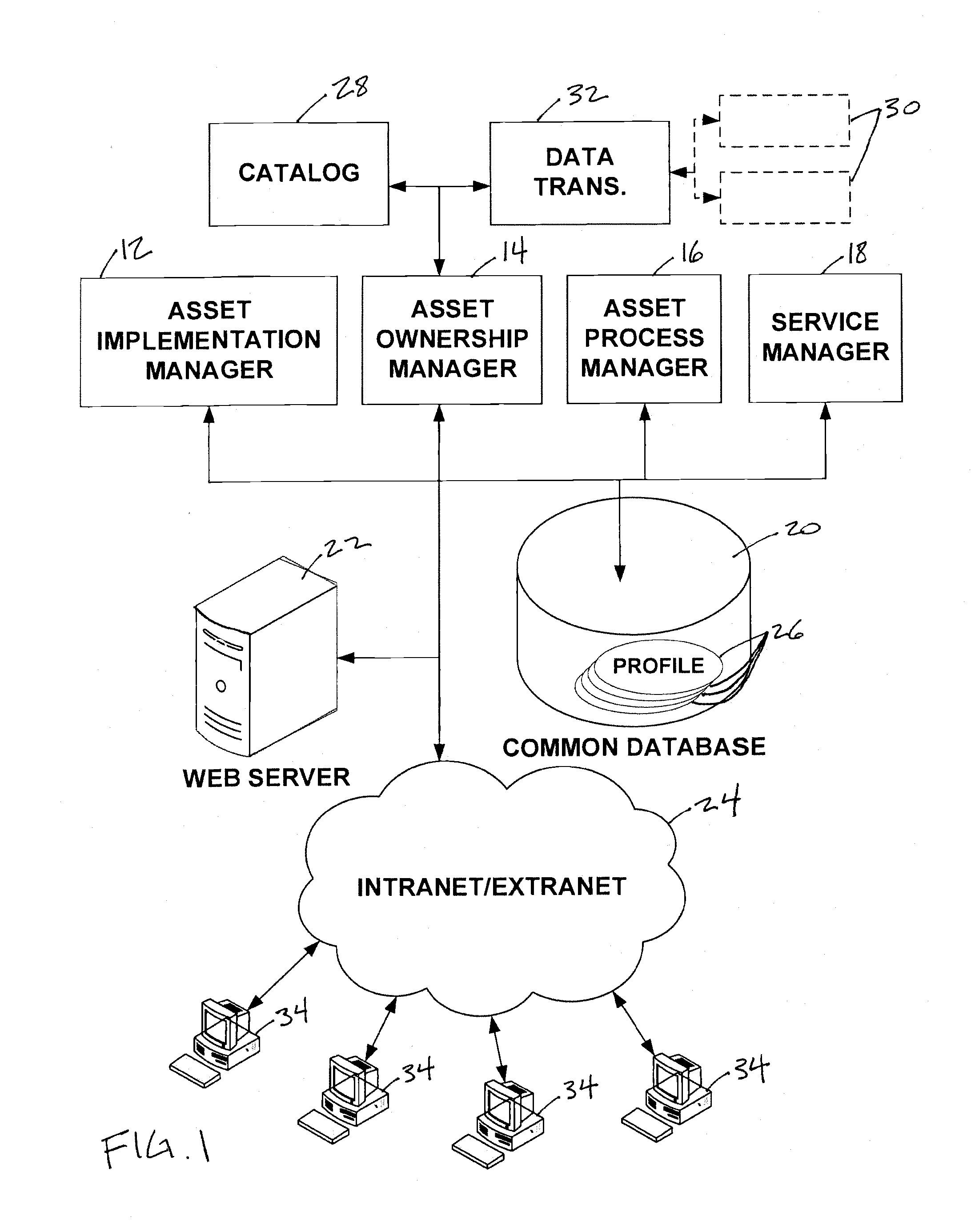
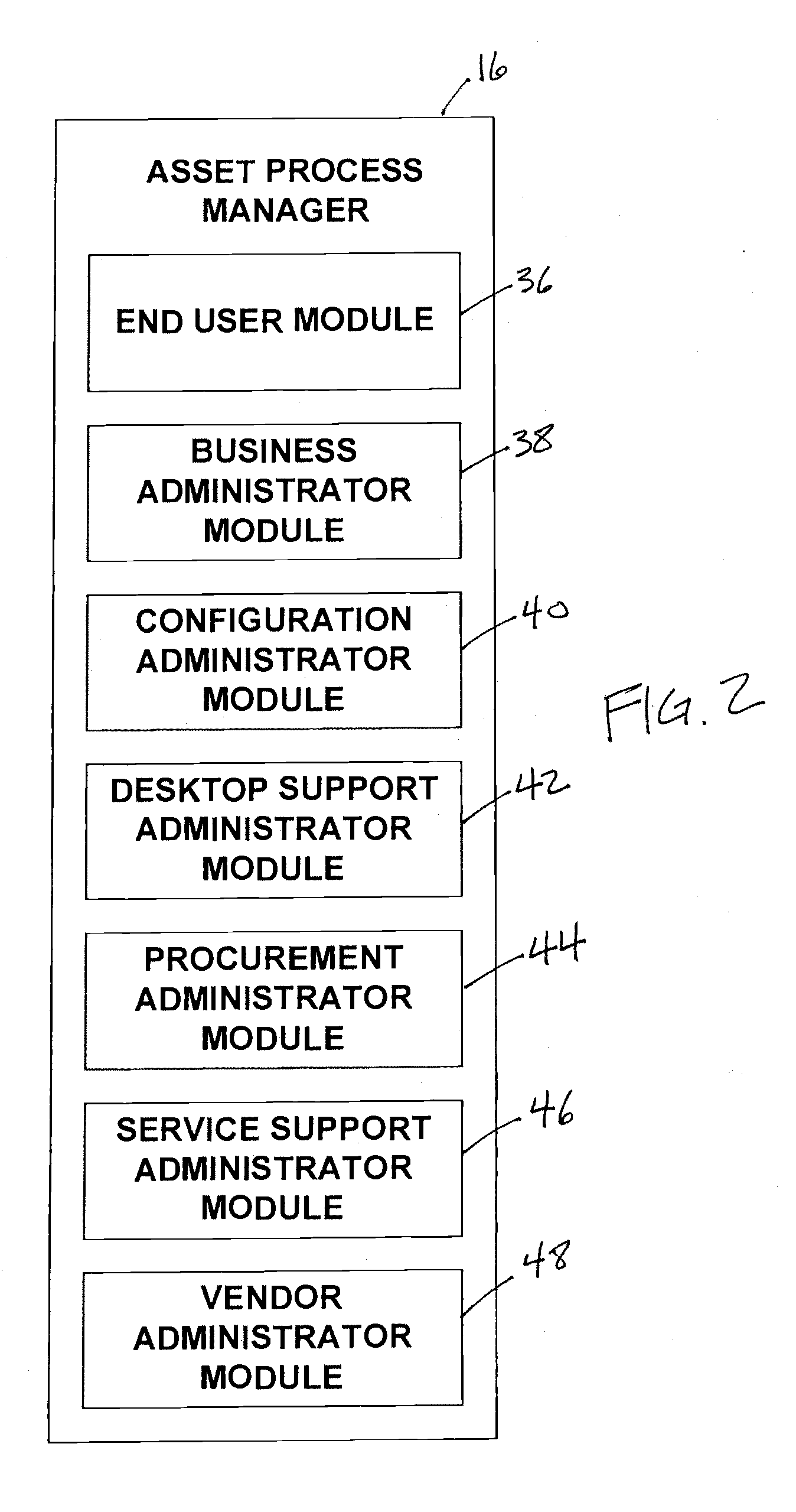
A system configured to manage IT assets associated with an entity (e.g., a company, an institution, etc.), in accordance with one or more embodiments of the invention. The IT assets may include hardware assets, software assets, telecommunications assets, and / or other IT assets. The system enables substantially all of the information relevant to the individual IT assets to be organized within a single repository throughout the life cycle of the IT assets (e.g., from order to disposal). By organizing the relevant information within a single repository, automation and dynamic system interaction may be leveraged during the life cycle of a given IT asset to track and / or monitor the given IT asset with an enhanced efficiency. In some embodiments, the system may include a common database, and an asset implementation manager, an asset ownership manager, an asset process manager, a service manager in operative communication with the common database.
Owner:CA TECH INC
Software Asset Packaging and Consumption Method and System
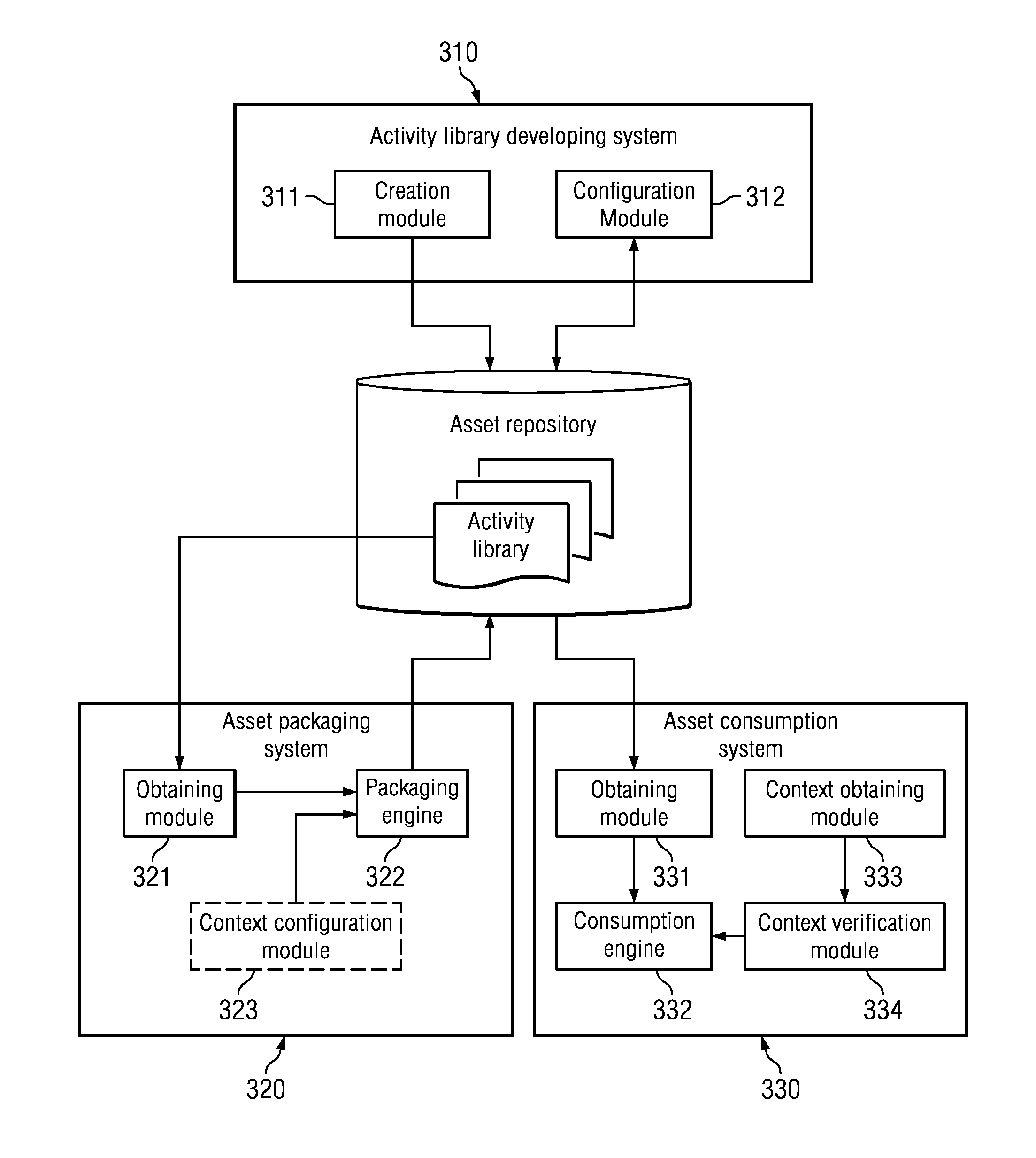
A reusable asset packaging and consumption method and system that support consumption activities and variability point instances associated with asset types or artifact types. Generic consumption activities and variability point types for different asset types or artifact types and developed and stored in a repository. When an asset packager packages an asset, a needed activity is selected from the activities associated with the type of the asset. The activity, a variability point instance bound with the activity, and the context constraints, together with the artifacts is packaged into the asset package, where the asset package is then stored in a repository. During consumption, the asset consumer obtains the asset package, verifies the context, and executes the activity packaged in the asset, while specifying variability point values for the bound variability instance.
Owner:IBM CORP
System and method for converting a target computing device to a virtual machine in response to a detected event
ActiveUS7831820B2Digital computer detailsSoftware simulation/interpretation/emulationVirtual machineSoftware assets
A system and method for converting a target computing device to a virtual machine are provided. A conversion event is detected to initiate a conversion of a target computing device to a virtual machine. An assessment of the physical and software assets of a target computing device are obtained. A data image of the target computing device is deployed on an instance of a virtual machine. The virtual machine adjusted to correspond to the physical and software assets of the target computing device.
Owner:SERVICENOW INC
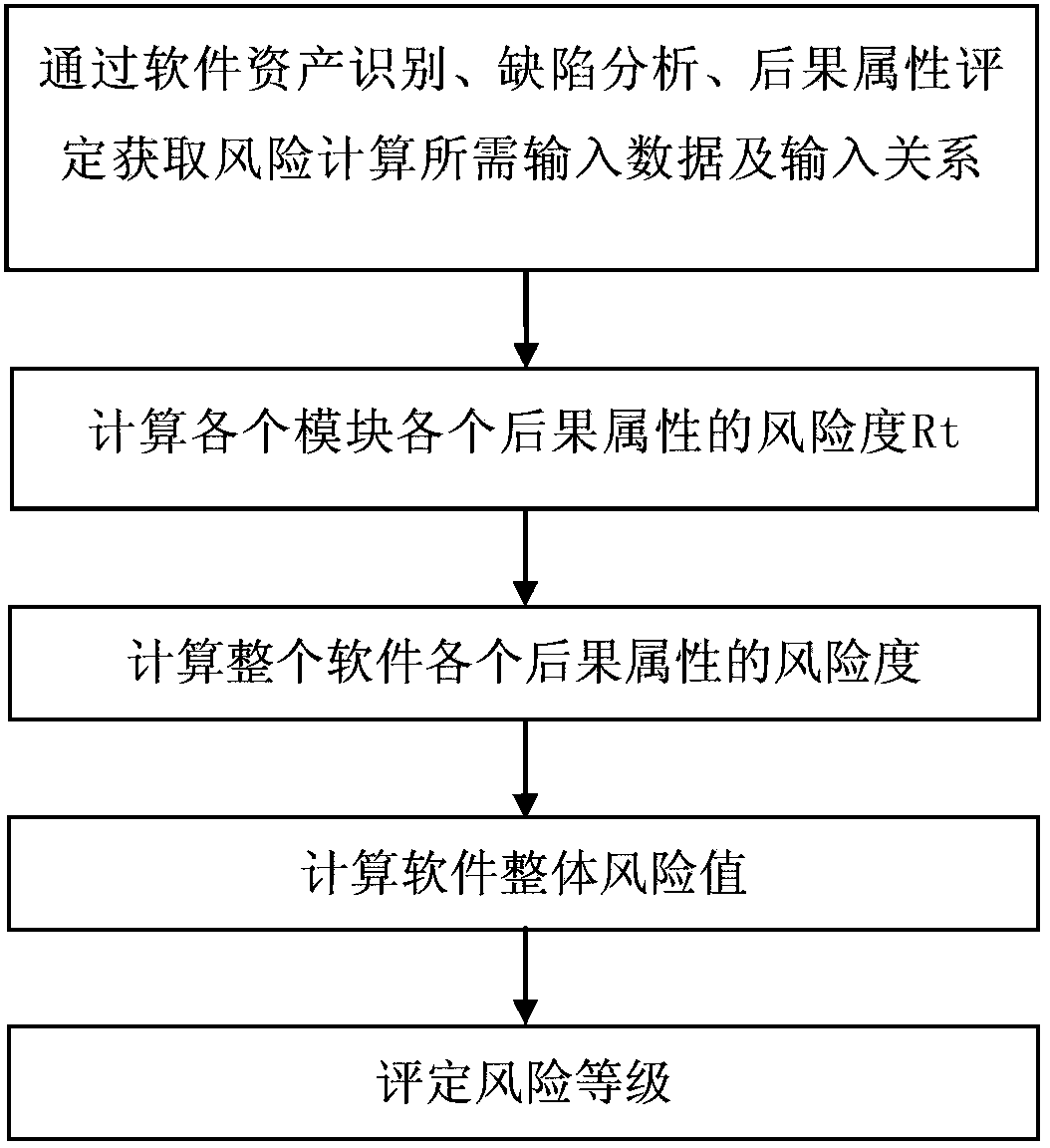
Software risk assessment method based on defect analysis
ActiveCN103366123AOvercoming Risk Double Counting ProblemsRisk Double Counting Problem AvoidancePlatform integrity maintainanceRisk levelRisk rating
The invention discloses a software risk assessment method based on defect analysis. The risk assessment method comprises the following steps of obtaining input data and an input relationship required by risk calculation through software asset identification, the defect analysis and consequence attribute evaluation, calculating consequence attribute factors of consequence attributes in functional modules, calculating risk degrees sumRtk of consequences of whole software, calculating weighted means of the risk degrees of the consequence attributes according to weights (pwti) of the functional modules of the software, obtaining the risk degrees sumRtk of the consequence attributes of the whole software, calculating a whole risk value of the software, calculating weighted means of the risk degrees of the consequence attributes of the whole software according to weights (rwtk) of the consequence attributes, obtaining a final risk value Risk of the software, evaluating a risk level, and obtaining the risk level of the software as an assessment result according to the risk value Risk of the software. The method solves the problems that risk element assignments in most risk assessment models relate to more expert opinions at present, and some assignments are unquantifiable. The method avoids repeated risk calculation to the greatest extent.
Owner:TIANJIN UNIV
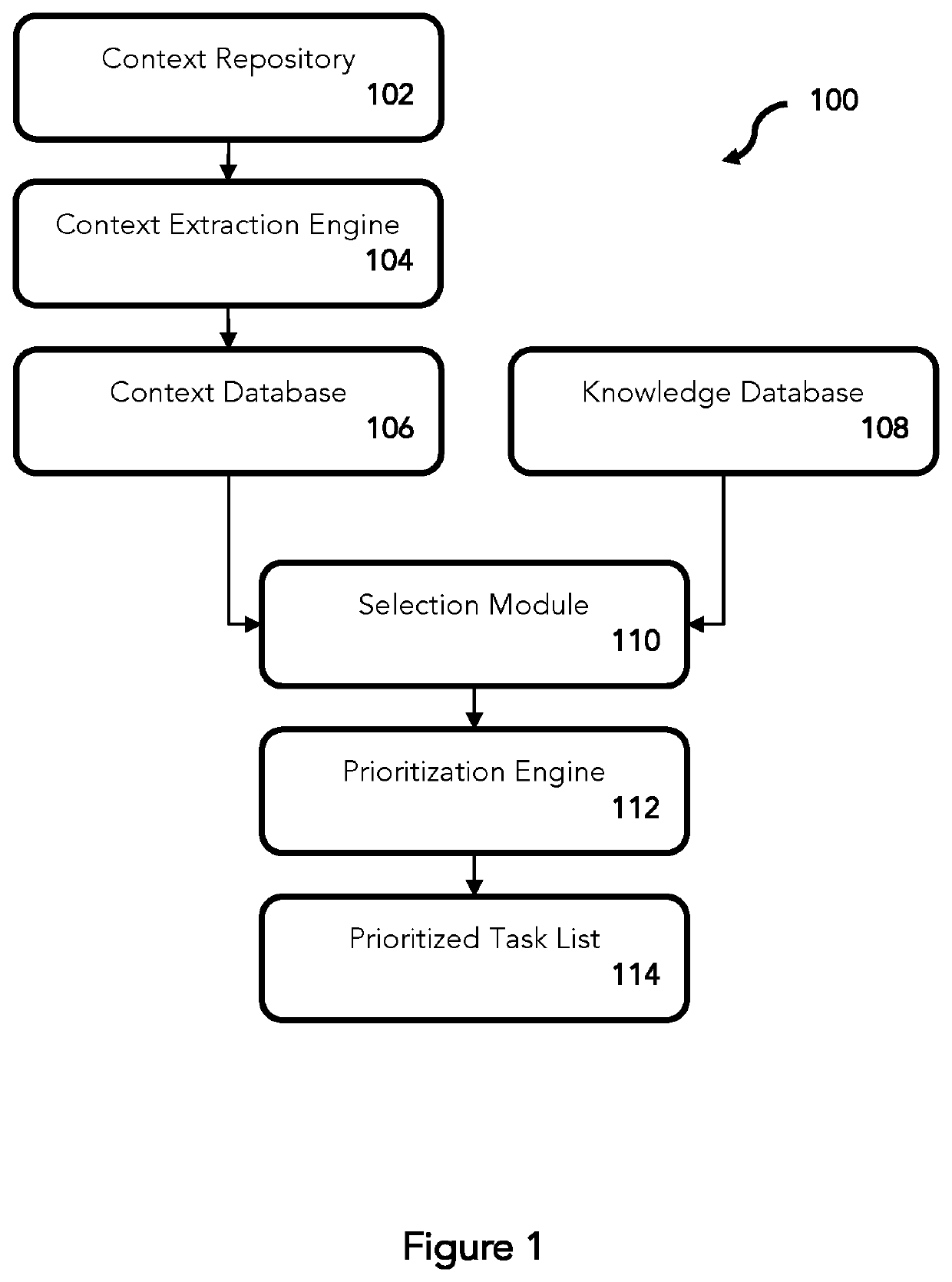
Automation of task identification in a software lifecycle
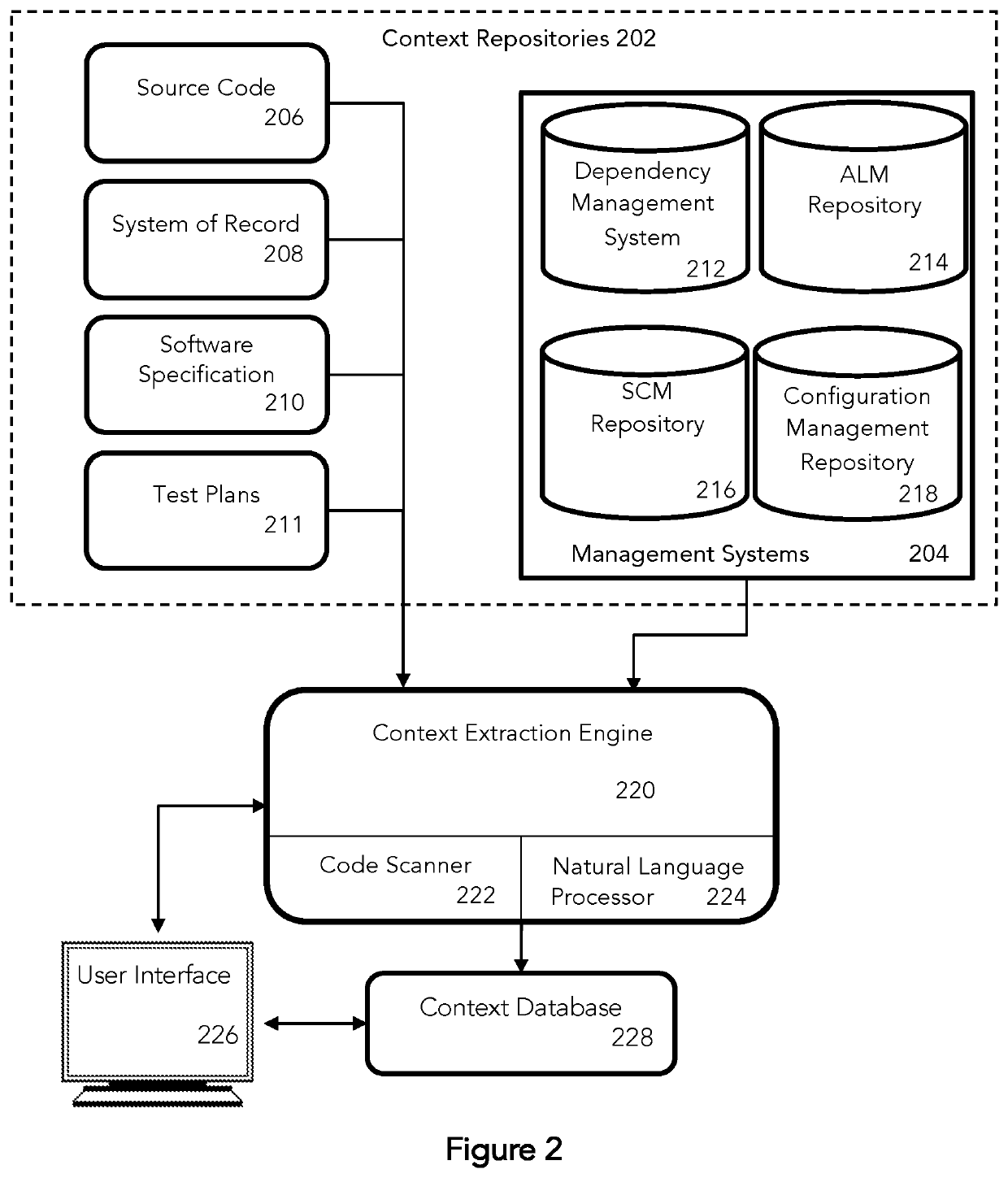
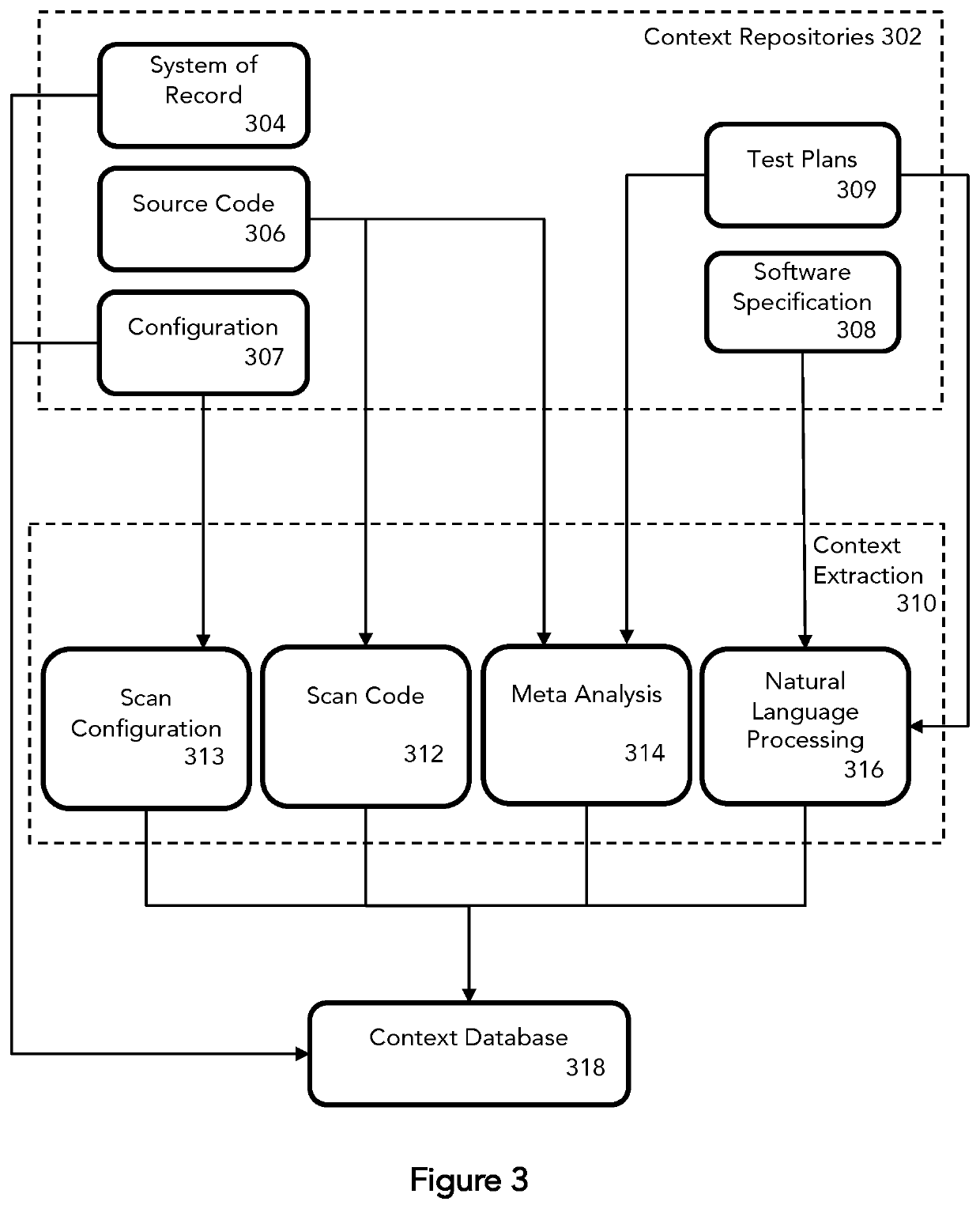
A system and method for automation of task identification and control in a software lifecycle. Software context for a software asset is extracted from context repositories of the software asset during software development and operation, the extracted context data is matched to relevant tasks in a knowledge database to select tasks for the software asset, and task prioritization and orchestration are presented in a prioritized task list during a software lifecycle.
Owner:SECURITY COMPASS TECH LTD
Managing software asset environment using cognitive distributed cloud infrastructure
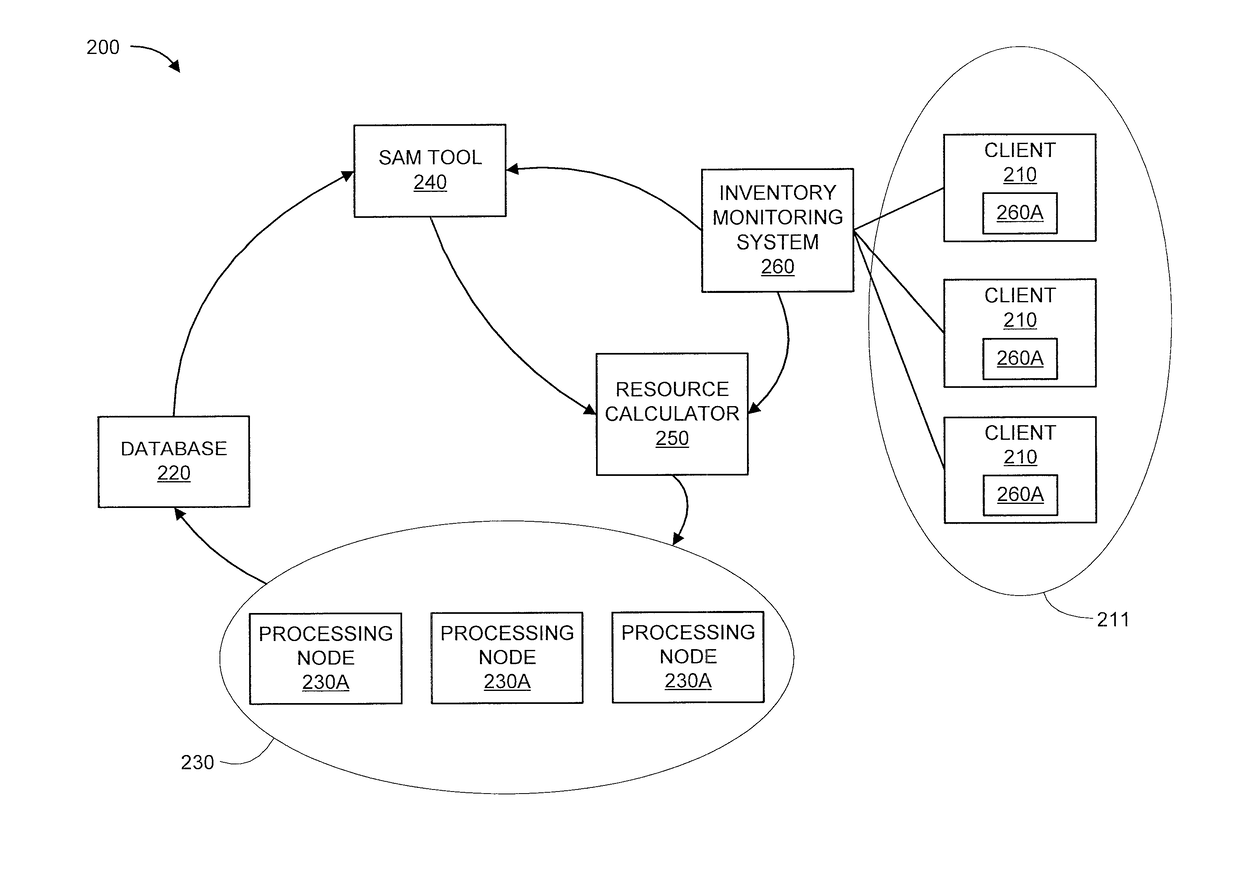
A method and system are provided for performing an extract-transform-load (ETL) process. The method includes collecting load information about a volume and a complexity of raw data to be processed during the ETL process. The method further includes receiving an expected completion time of the ETL process and execution information about (i) hardware resources and (ii) an influence of the hardware resource on an execution time of the ETL process. The method also includes calculating resources for a distributed processing software infrastructure to be used to perform the ETL process, by applying a statistical method to the load information, expected completion time, and execution information. The method additionally includes dynamically assigning cloud resources corresponding to and based on the calculated resources, in accordance with the expected completion time. The method further includes performing the ETL process on the raw data using the assigned cloud resources and storing ETL process results.
Owner:IBM CORP
Development system with improved methodology for creation and reuse of software assets
A development system with improved methodology for creation and reuse of software assets is shown and described. In one embodiment, for example, in a development system, a method is described for facilitating creation of a reusable application, the method comprises steps of: during development of the application, capturing knowledge and intent of the application's original developer alongside source code created for the application; producing an archival module storing the source code for the application together with metadata capturing the knowledge and intent of the original developer, the metadata including at least one script guiding subsequent developers in use and modification of the source code for the application; and consuming the archival module by a follow-on developer, including executing the at least one script for facilitating creation of a reusable version of the application.
Owner:EMBARCADERO TECHNOLOGIES
Software asset management system and software and hardware information automatic grabbing method
InactiveCN106295926AResponsibilities are clearAvoid wastingResourcesSpecial data processing applicationsSoftware asset managementSystems management
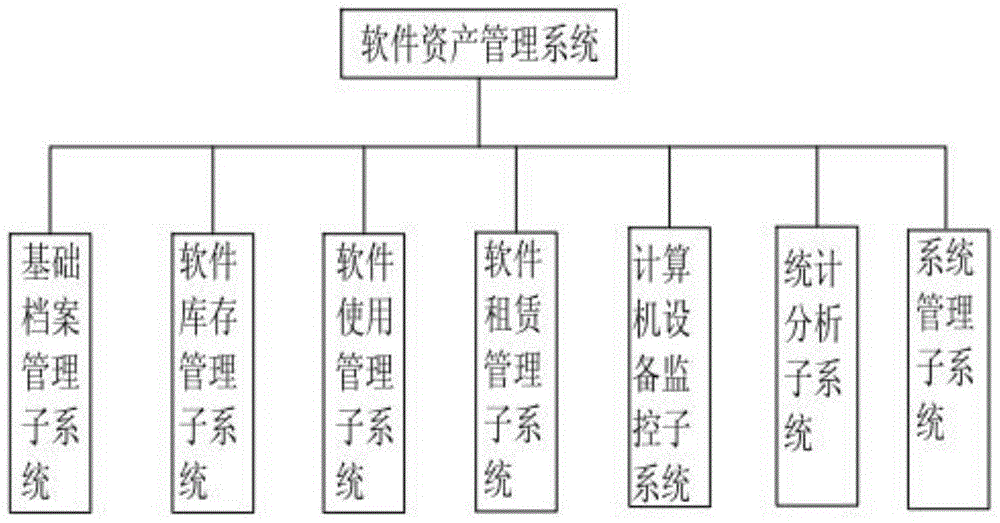
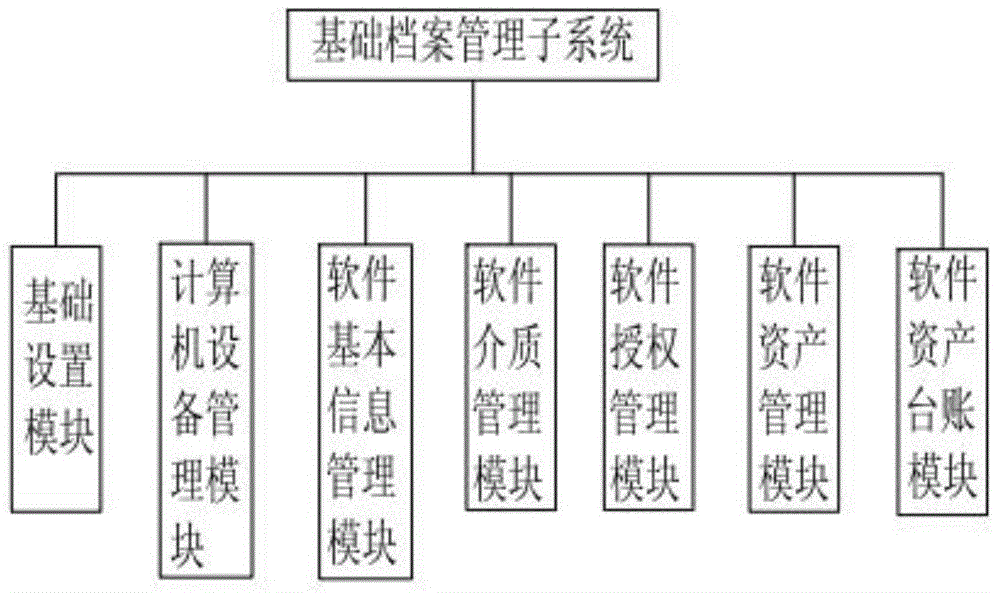
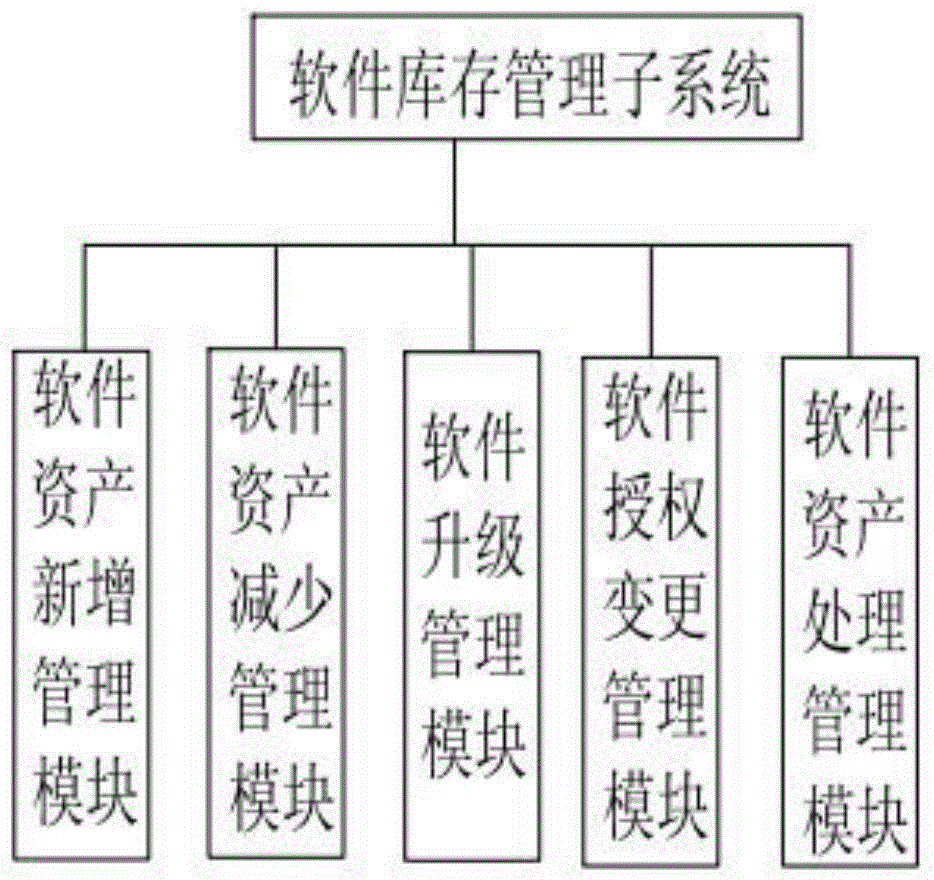
The invention discloses a software asset management system and a software and hardware information automatic grabbing method, and relates to the management device or system technology field. The asset management system comprises a fundament archive management sub-system, a software inventory management sub-system, a software utilization management sub-system, a software lease management sub-system, a computer device monitoring system, a statistical analysis sub-system, and a system management sub-system. The asset management system is used for effective management, control, and protection of software and hardware devices of users, is used to facilitate the control of the users over the purchasing costs and the utilization costs of the software, is used to improve the utilization rate and the integral benefit of the IT asset, and is used to guarantee the legality of the software utilization, and therefore the legal risks and the financial risks caused by the utilization of the software asset are prevented.
Owner:北京思图科技有限公司
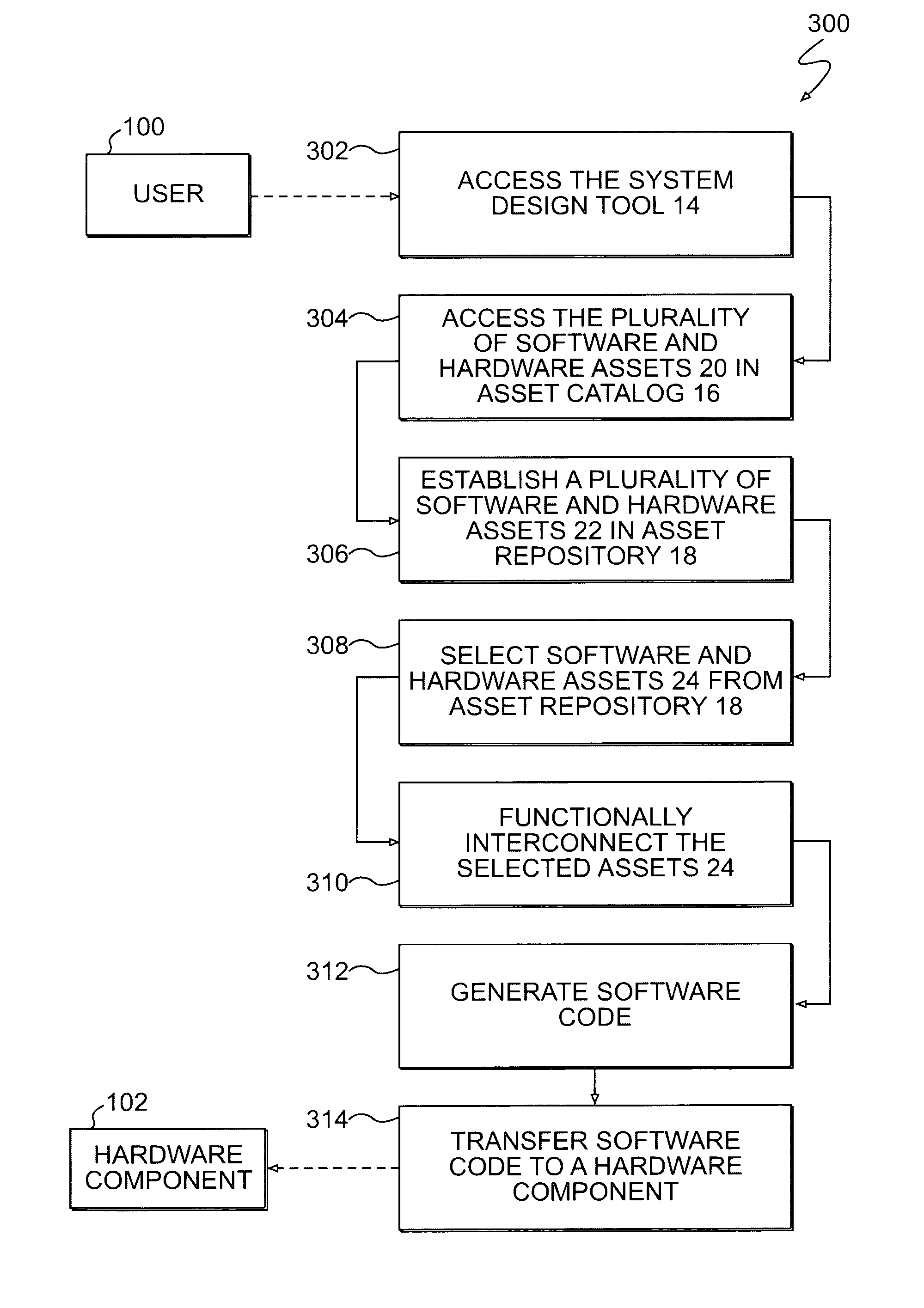
System design tool according to reusable asset specifications
An asset catalog is disclosed which includes a plurality of software assets and at least one hardware asset configured to be selectively functionally interconnected with at least one of the plurality of software assets. The plurality of software assets and the at least one hardware asset are organized in accordance with reusable asset specifications.
Owner:CATERPILLAR INC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com