Patents
Literature
52 results about "Decentralized computing" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Decentralized computing is the allocation of resources, both hardware and software, to each individual workstation, or office location. In contrast, centralized computing exists when the majority of functions are carried out, or obtained from a remote centralized location. Decentralized computing is a trend in modern-day business environments. This is the opposite of centralized computing, which was prevalent during the early days of computers. A decentralized computer system has many benefits over a conventional centralized network. Desktop computers have advanced so rapidly, that their potential performance far exceeds the requirements of most business applications. This results in most desktop computers remaining idle (in relation to their full potential). A decentralized system can use the potential of these systems to maximize efficiency. However, it is debatable whether these networks increase overall effectiveness.
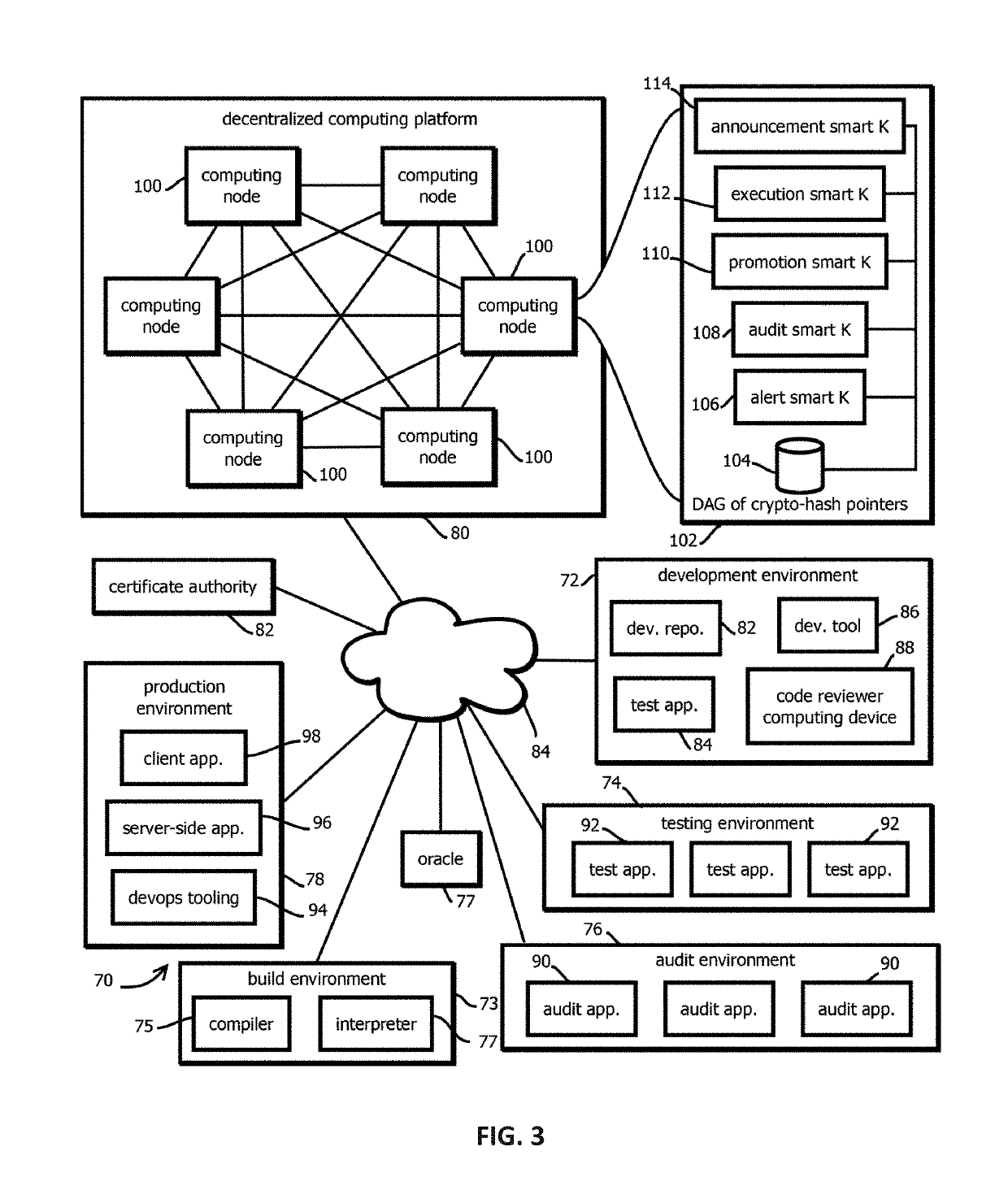
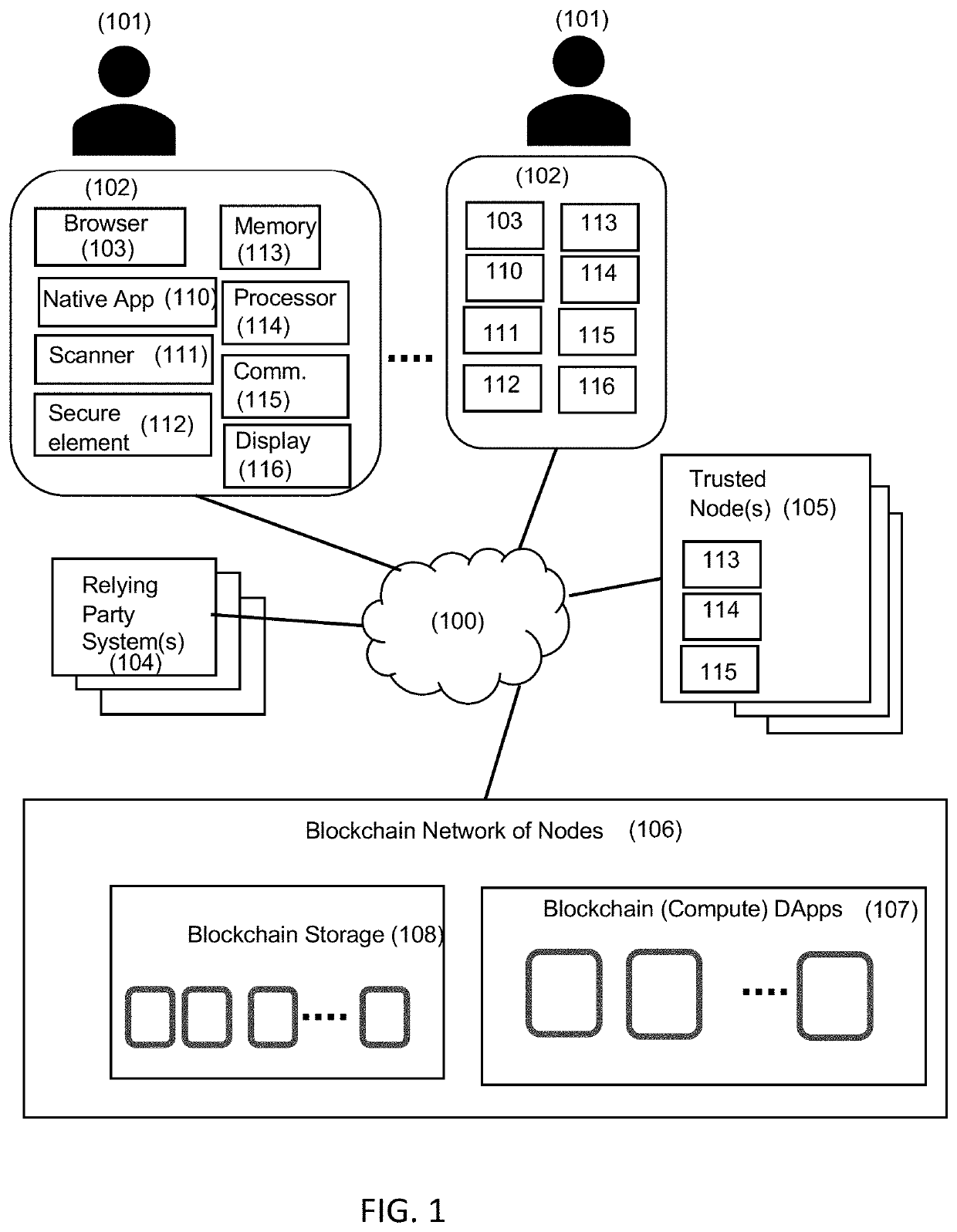
Federated identity management with decentralized computing platforms
ActiveUS20200067907A1Key distribution for secure communicationDigital data protectionInternet privacyEngineering
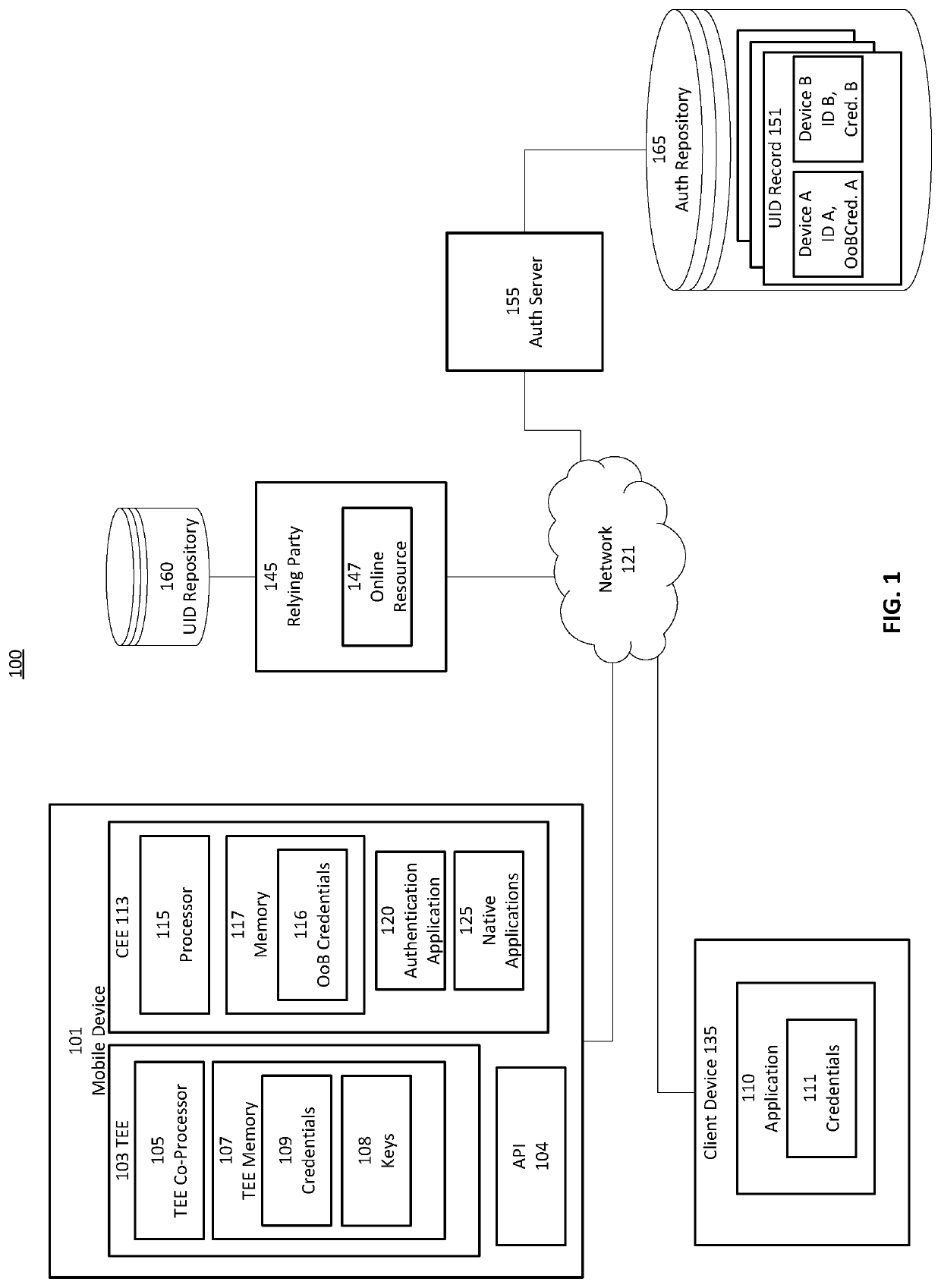
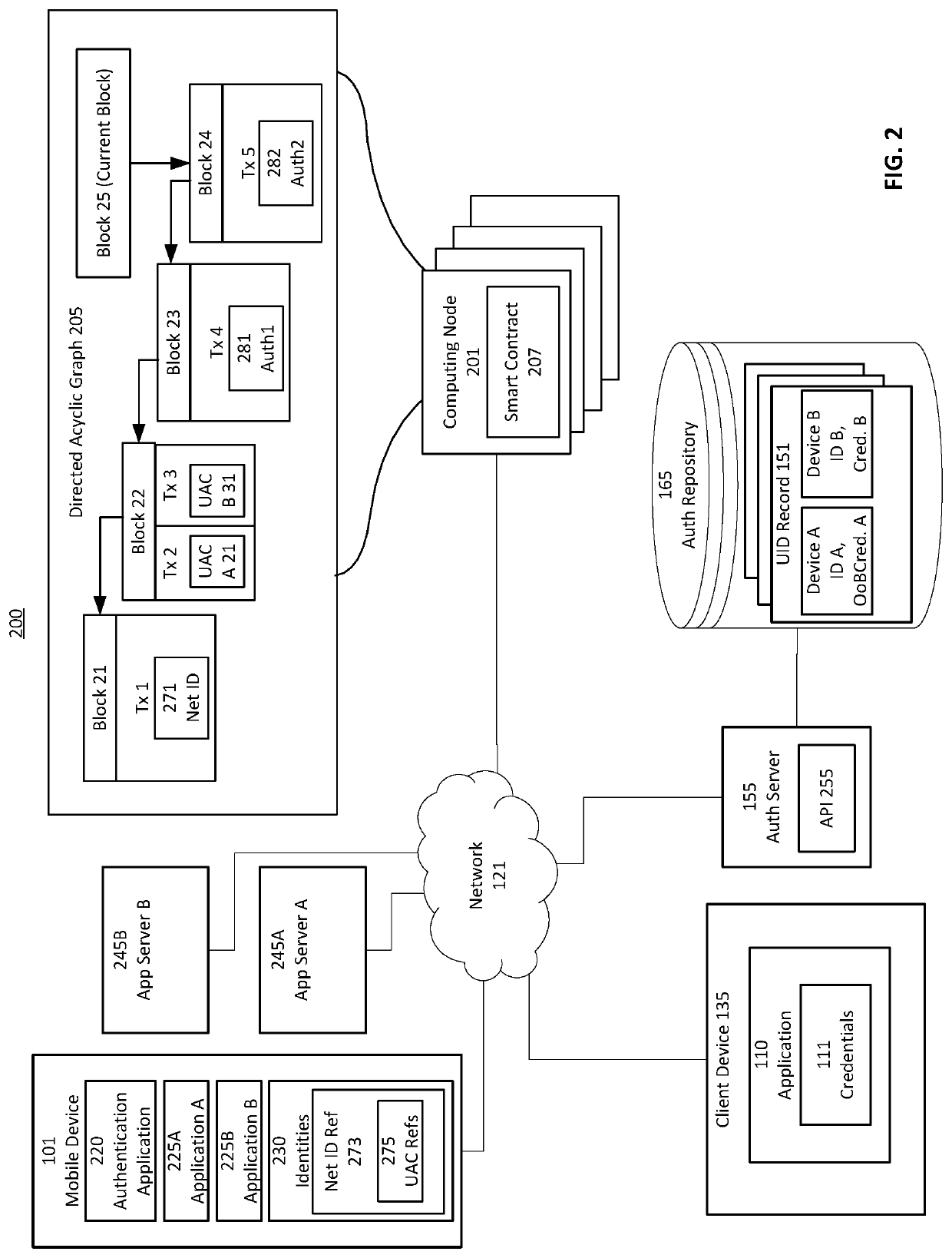
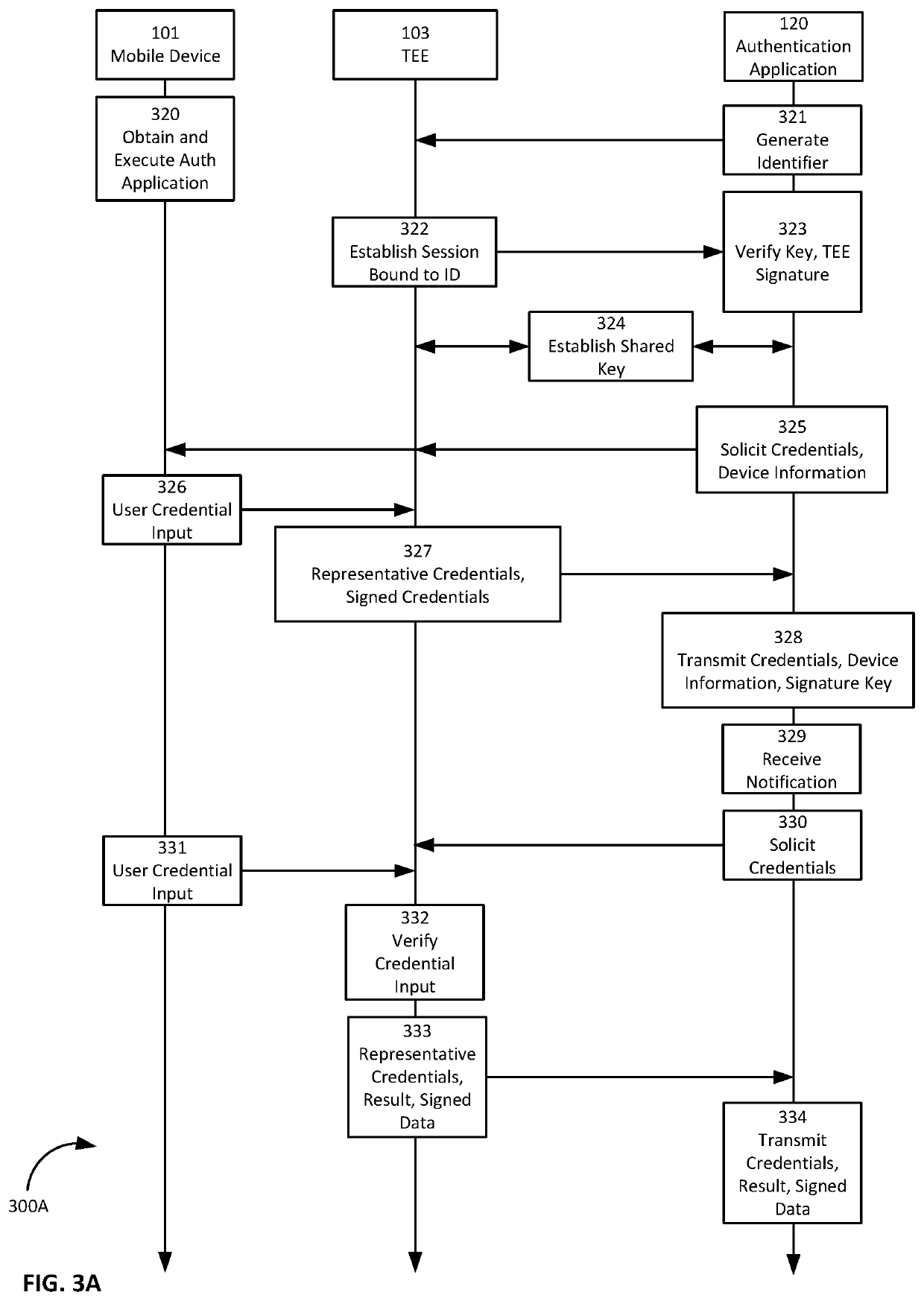
Provided is a process that establishes user identities within a decentralized data store, like a blockchain. A user's mobile device may establish credential values within a trusted execution environment of the mobile device. Representations of those credentials may be generated on the mobile device and transmitted for storage in association with an identity of the user established on the blockchain. Similarly, one or more key-pairs may be generated or otherwise used by the mobile device for signatures and signature verification. Private keys may remain resident on the device (or known and input by the user) while corresponding public keys may be stored in associated with the user identity on the blockchain. A private key is used to sign representations of credentials and other values as a proof of knowledge of the private key and credential values for authentication of the user to the user identity on the blockchain.
Owner:HYPR CORP
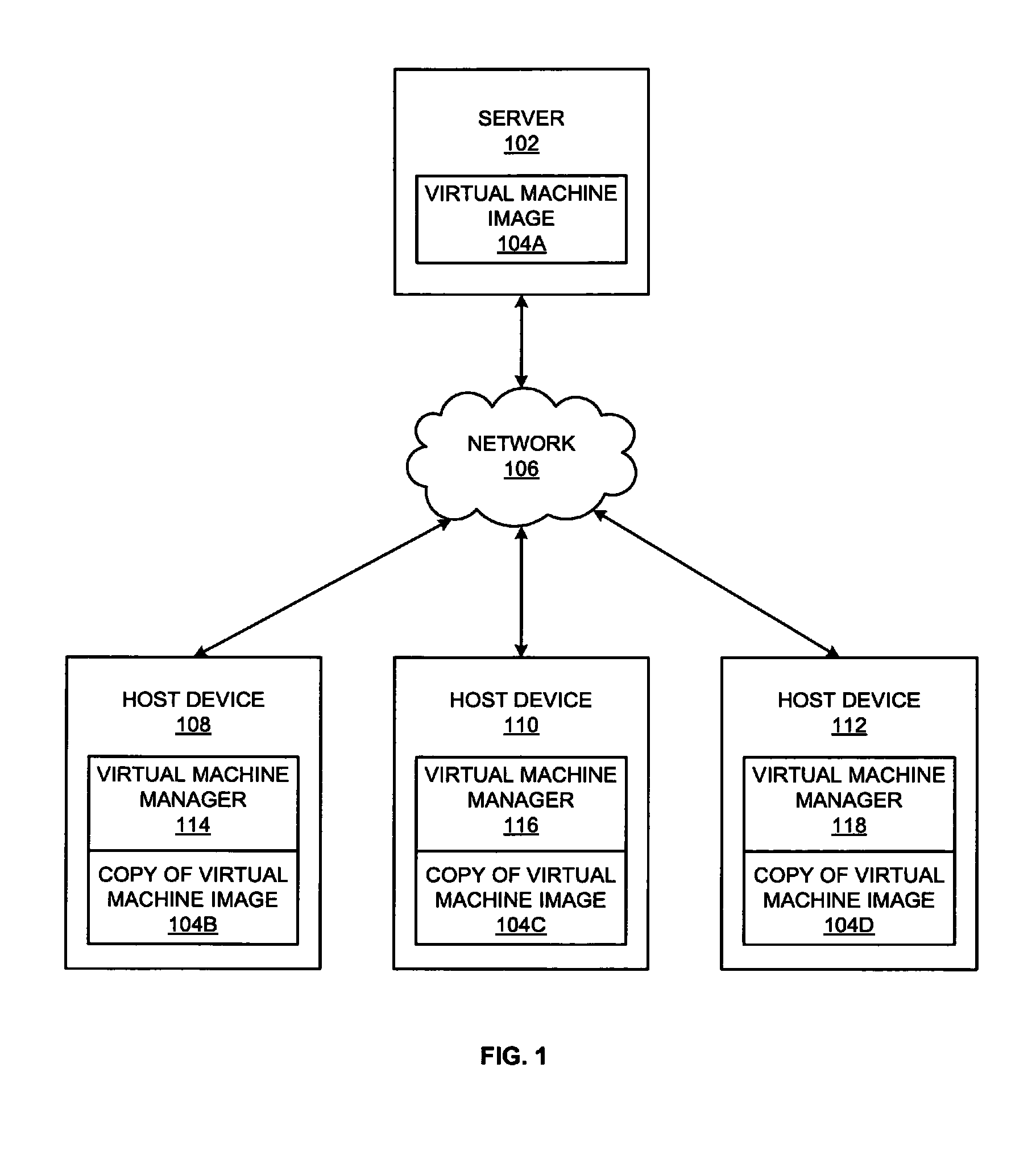
Systems and methods for decentralized computing
ActiveUS8301686B1Multiple digital computer combinationsSoftware simulation/interpretation/emulationDecentralized computingDigital device
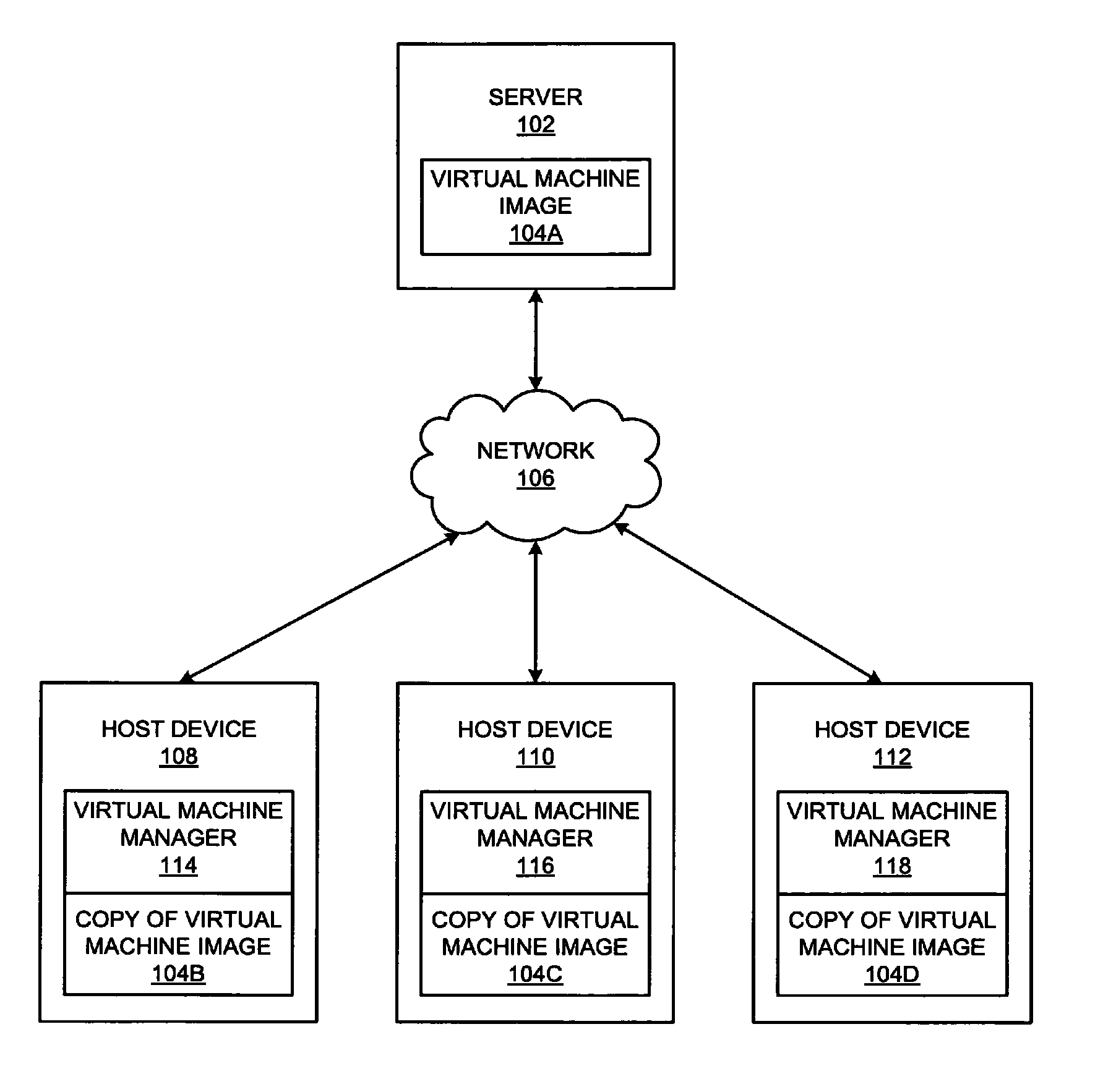
Methods and systems for providing decentralized computing are provided. An exemplary method includes generating one or more virtual machine images including at least one application and a virtual machine, associating the one or more virtual machine images with user information, receiving user information from a digital device, selecting one or more associated virtual machine images based on the user information, and providing the one or more virtual machine images to the digital device.
Owner:CITRIX SYST INC
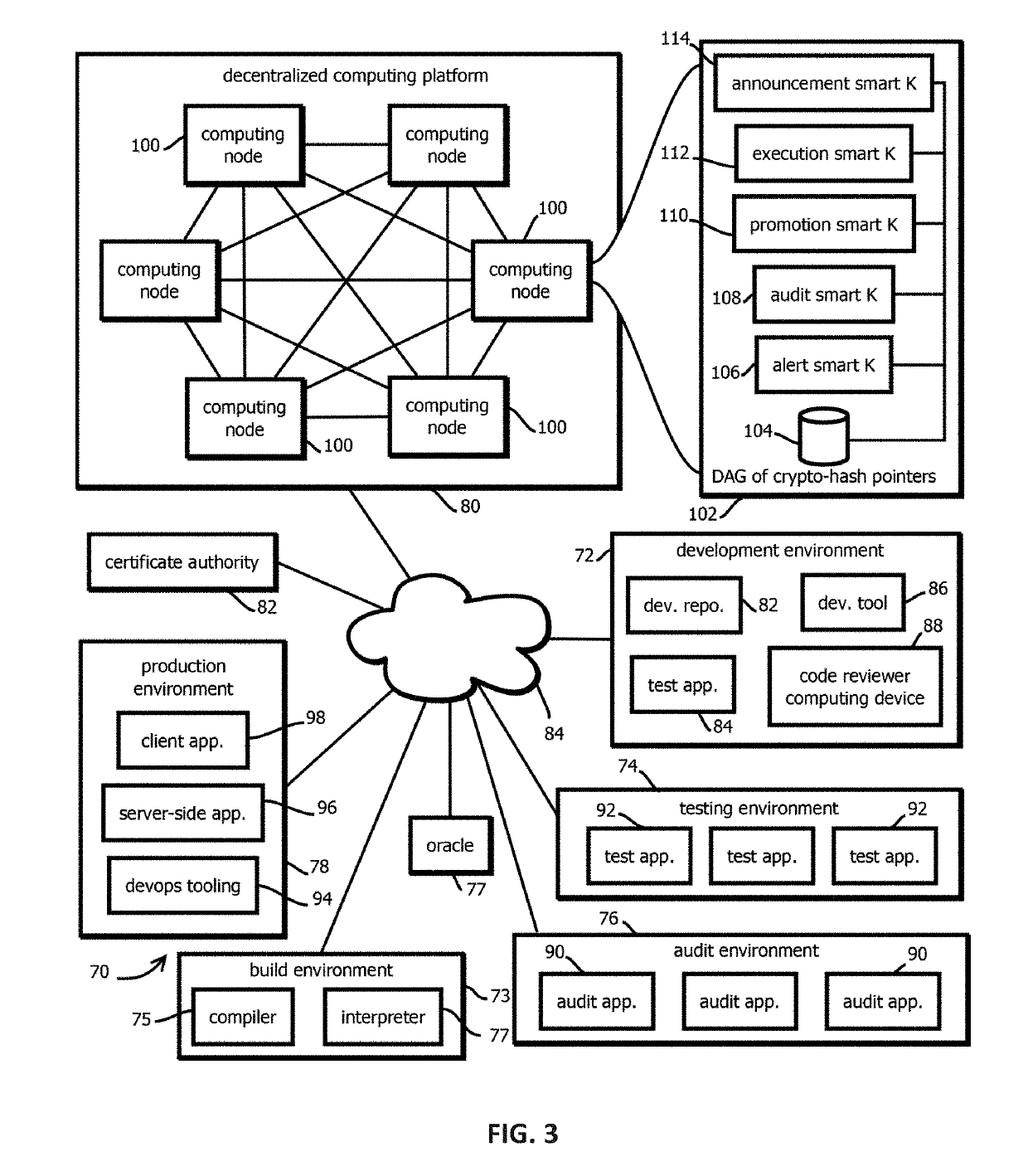
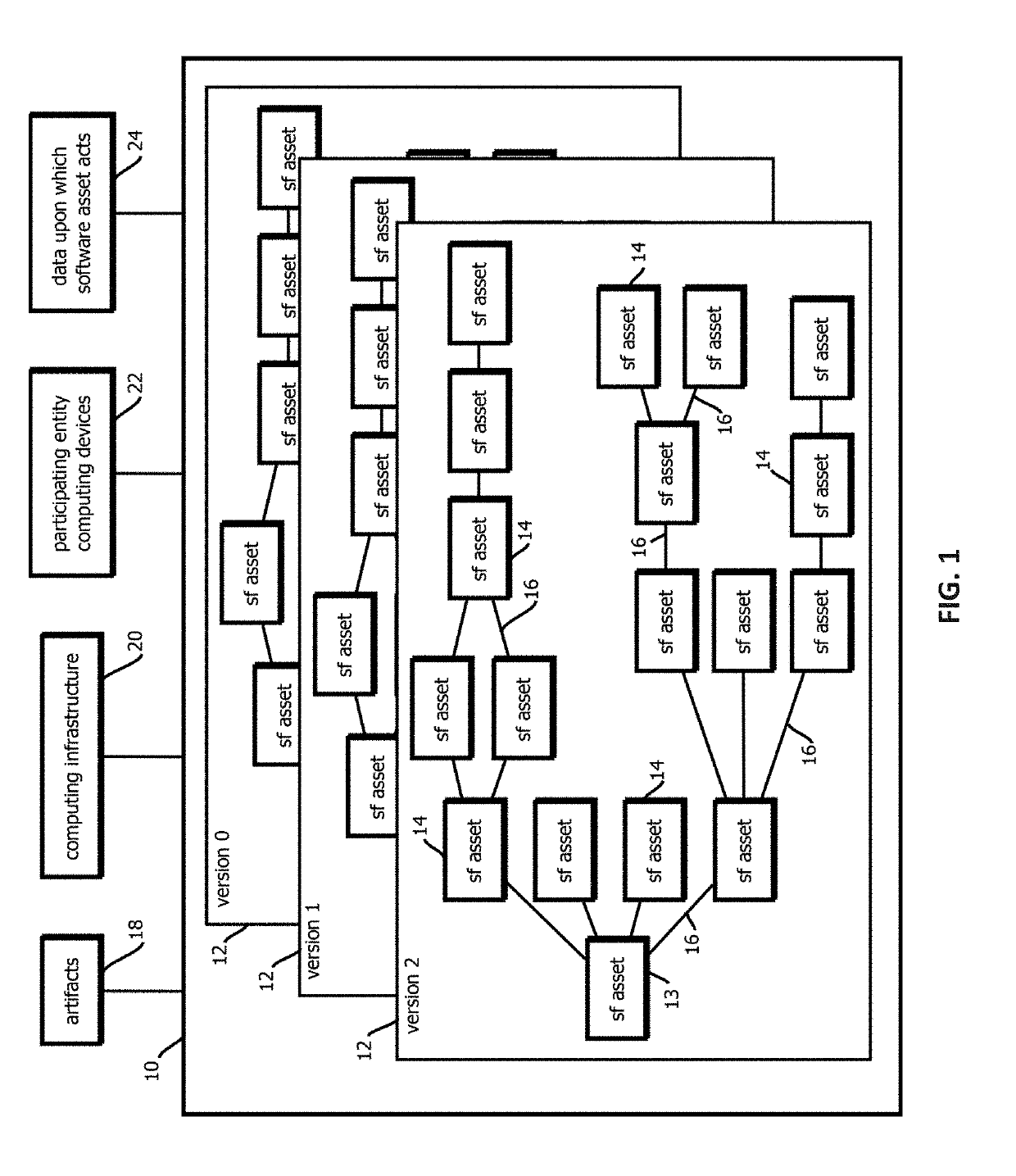
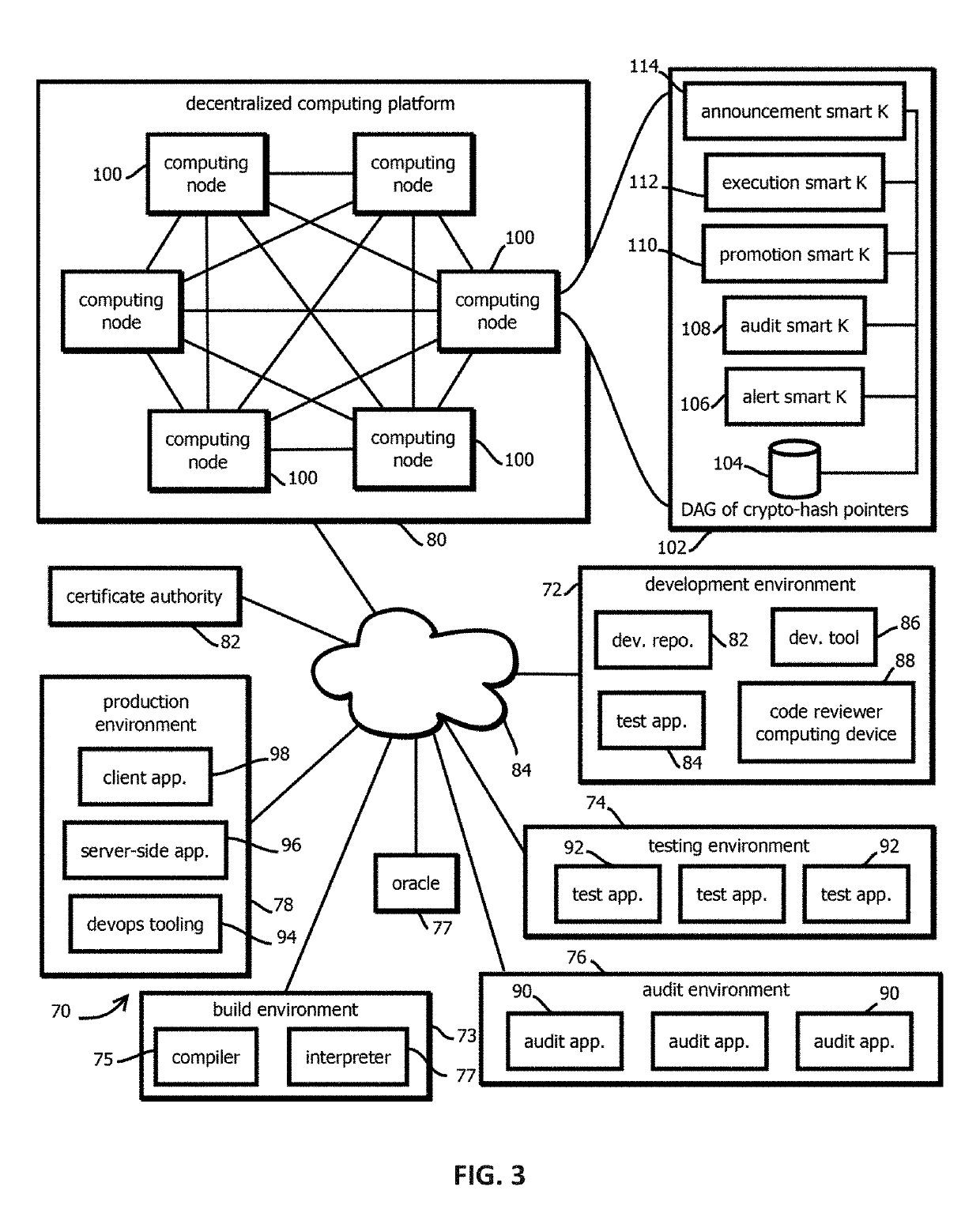
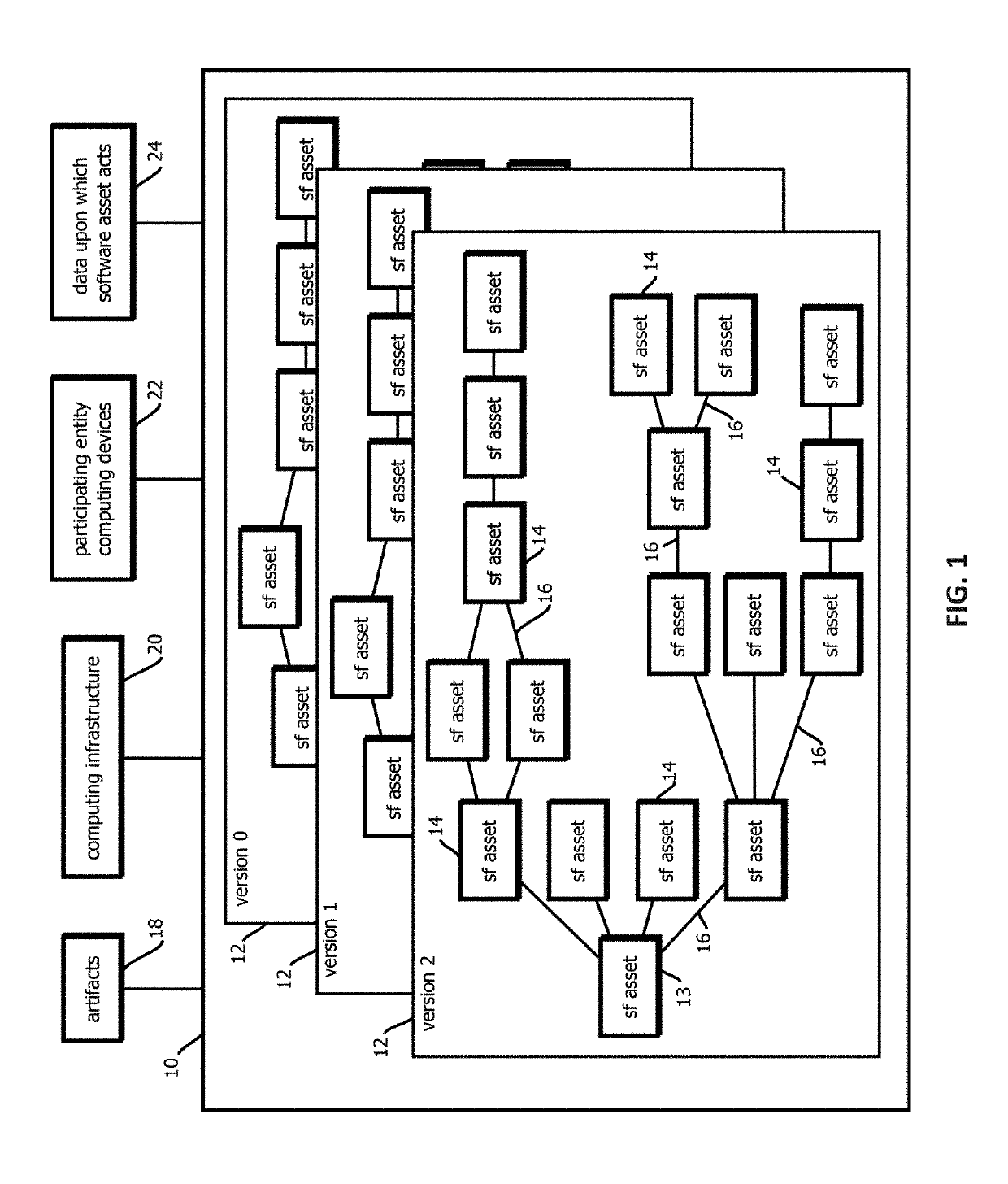
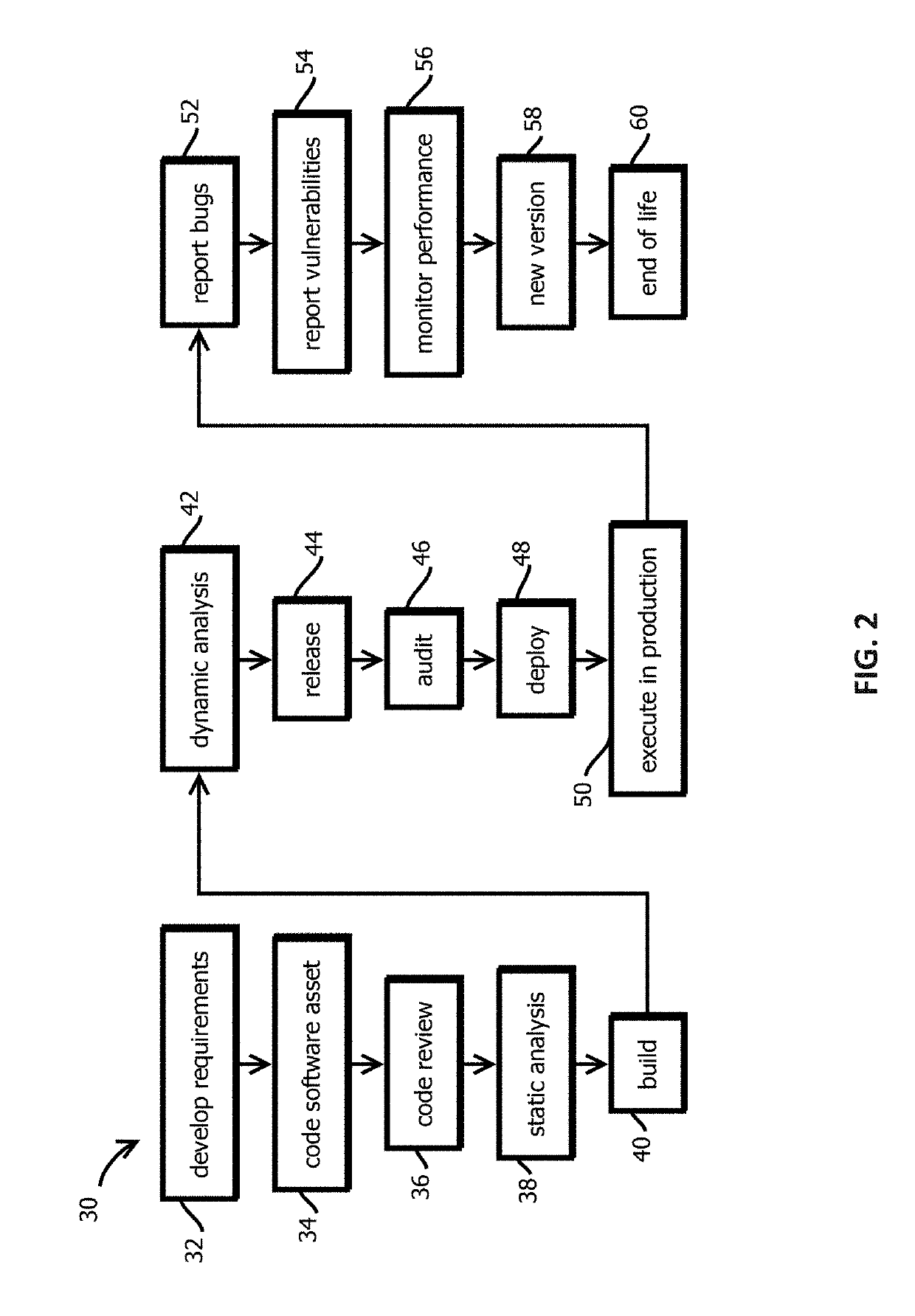
Promotion smart contracts for software development processes
InactiveUS20190303623A1Version controlUser identity/authority verificationSoftware development processSoftware engineering
Provided is a smart contract that specifies a routine to be executed by a plurality of the computing nodes of a blockchain-based, decentralized computing platform, wherein the promotion smart contract is configured to determine whether a pre-release software asset satisfies software quality criteria required to advance the pre-release software asset to a next stage, and the promotion smart contract is configured to cause an assertion indicating whether software quality criteria are satisfied to be published to a blockchain storing trust records in response to determining whether the software quality criteria are satisfied.
Owner:CA TECH INC
Implementation and management of internet accessible services using dynamically provisioned resources
InactiveUS20110161496A1Lower latencySimple configurationDigital computer detailsBuying/selling/leasing transactionsThird partyThe Internet
Systems and methods for providing a decentralized computing resource marketplace captures various attributes of a consumer's needs for remote computing services, such as cost, location, performance, network connectivity, reliability, hardware composition and service levels and identifies, provisions and manages remote resources offered by third parties on behalf of the consumers. Lease agreements may be brokered and enforced among consumers of remote computing services (e.g., storage) and the providers of such resources.
Owner:NICKLIN JONATHAN C
Alert smart contracts configured to manage and respond to alerts related to code
InactiveUS20190306173A1Encryption apparatus with shift registers/memoriesError detection/correctionSmart contractDecentralized computing
Provided is a process that includes: calling an alert program configured to execute on a decentralized computing platform and access records on a blockchain, wherein: the decentralized computing platform is configured to execute multiple instances of the program to produce multiple instances of candidate results, the decentralized computing platform is configured to determine an output of the alert program in response to the call with a first consensus algorithm, the alert program is configured to verify a cryptographic signature of the call and determine whether an alerting entity is authorized to issue the alert, and the alert program is configured to publish the information about the software asset to alert recipients or to the blockchain upon verifying the cryptographic signature and determining that the alerting entity is authorized to issue the alert.
Owner:CA TECH INC
Announcement smart contracts to announce software release
InactiveUS20190305959A1User identity/authority verificationVersion controlDocumentation procedureCryptographic nonce
Provided is a process that includes: calling a program executed on a decentralized computing platform configured to persist state to a blockchain, the call requesting the program to release the software asset to the production environment, wherein: respective instances of the program are configured to publish release documentation by which provenance of the software asset is verifiable to the blockchain, respective instances of the program are configured to verify a cryptographic signature associated with the software asset, the cryptographic signature establishes that the software asset being released has not been tampered with subsequent to signing, the cryptographic signature establishes that the releasing entity or a proxy of the releasing entity has access to a cryptographic key by which the cryptographic signature was formed, and the decentralized computing platform is configured to reach a consensus verification determination among verification results from the replicated instances of the program.
Owner:CA TECH INC
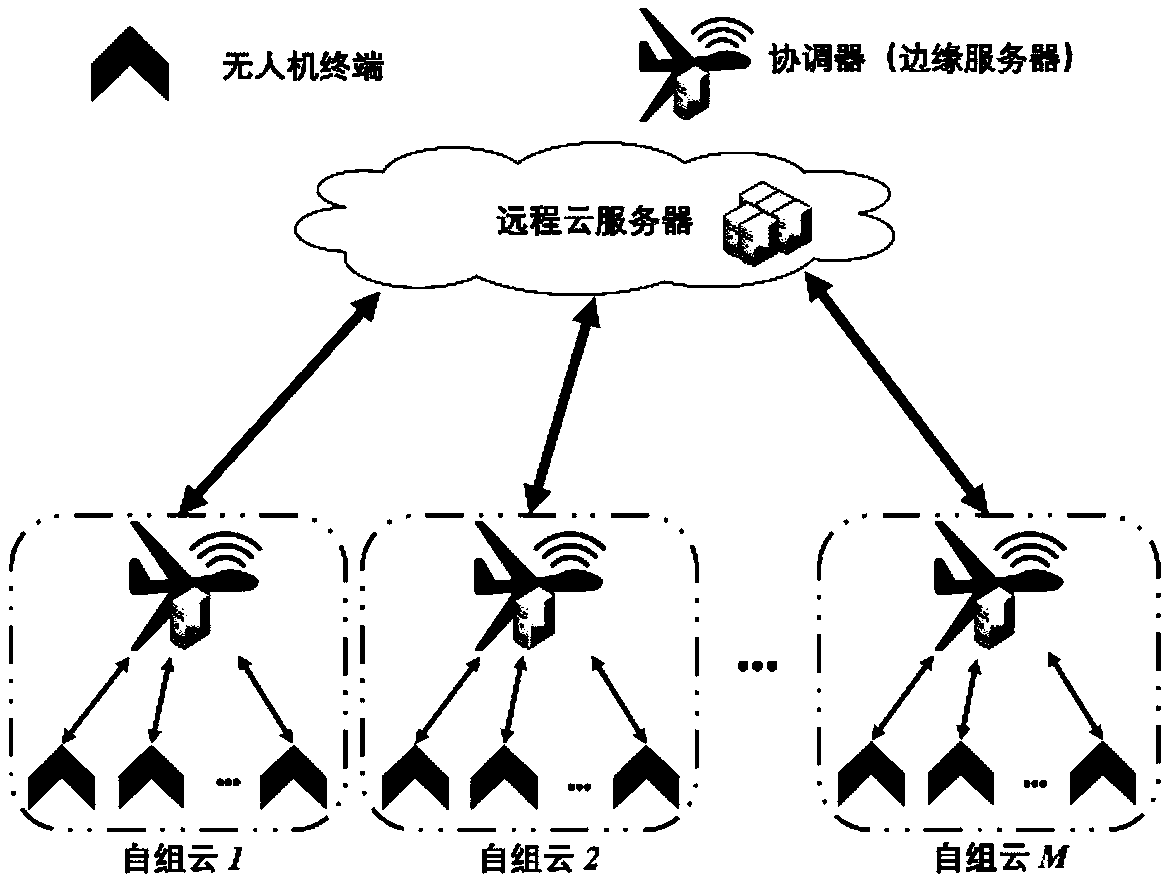
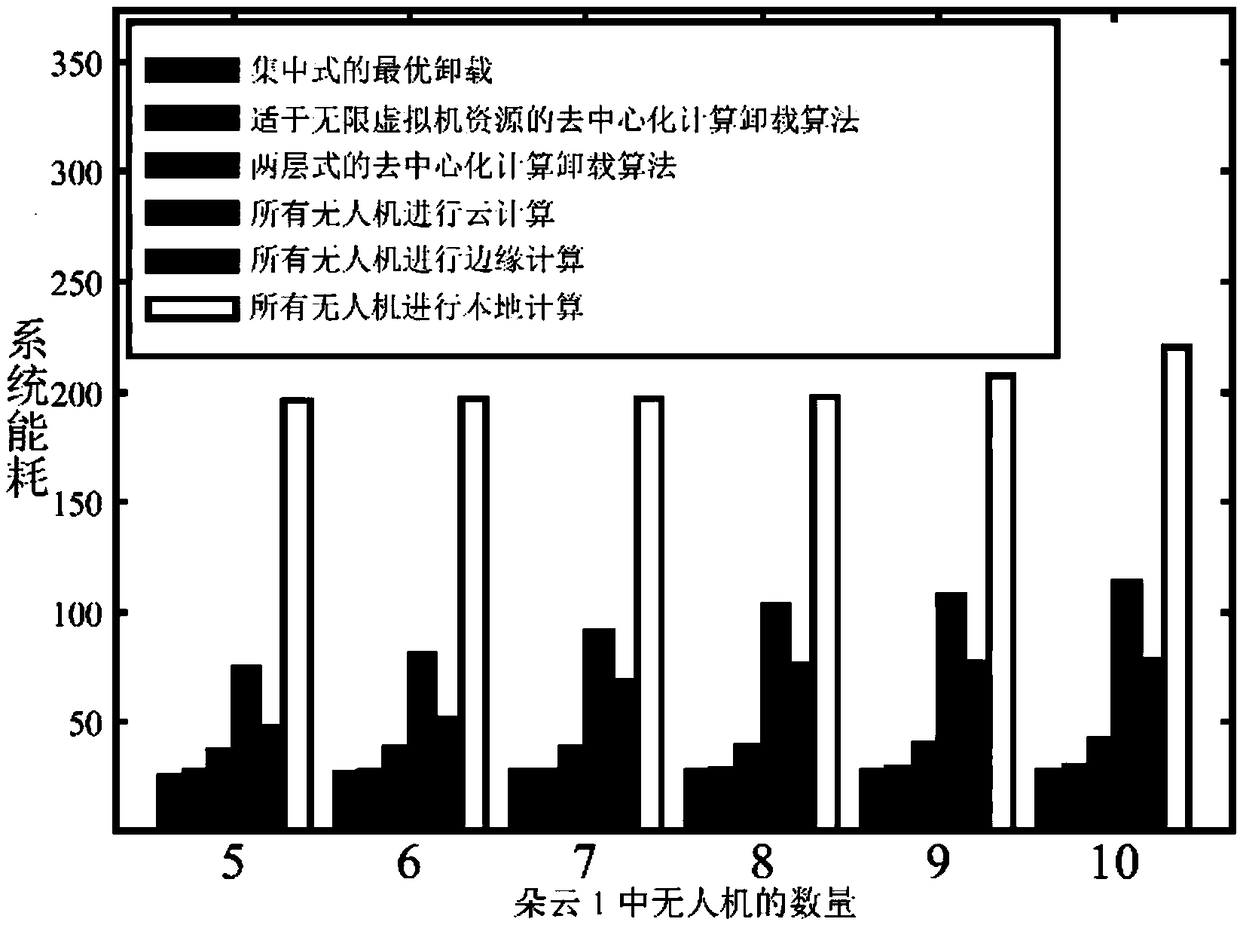
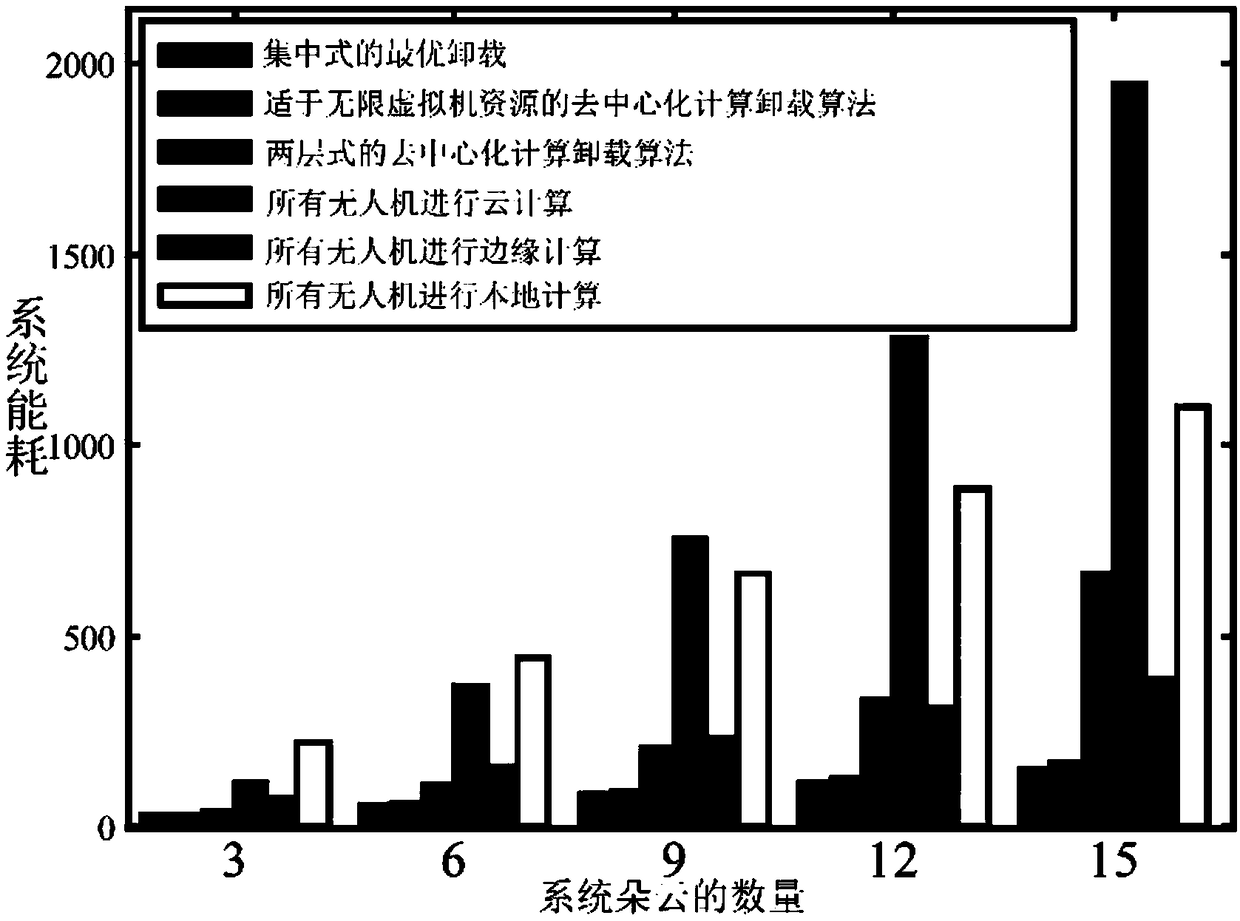
Self-organizing cloud architecture and optimization method and system for edge computing
ActiveCN109302463AReduce overheadReduce energy consumptionEnergy efficient computingData switching networksEdge computingComputer terminal
The invention provides a self-organizing cloud architecture and optimization method and system for edge computing. The method comprises: a model construction step: performing model construction on a hierarchical unmanned aerial vehicle system; a decentralized computing unloading algorithm step suitable for an infinite virtual machine resource situation: respectively performing game decision according to conditions met by an unmanned aerial vehicle terminal bandwidth of the unmanned aerial vehicle system so as to achieve Nash equilibrium; and a decentralized computing unloading algorithm step suitable for a finite virtual machine resource situation: designing a decentralized computing unloading algorithm to perform algorithm computing. The invention provides a layered decentralized unloading method to reduce the communication overhead while maintaining the energy efficiency; and according to the self-organizing cloud architecture and optimization method and system provided by the invention, the energy-saving computing unloading decision problem in the hierarchical unmanned aerial vehicle system is modeled as a non-cooperative game for research, the decentralized computing unloadingalgorithm is designed for the situations of infinite virtual machine resources and finite virtual machine resources, and it is proved that the algorithm can achieve the Nash equilibrium.
Owner:SHANGHAI JIAO TONG UNIV
Multi-address population based on single address
ActiveUS10554401B1StampsKey distribution for secure communicationSoftware engineeringFinancial transaction
A physical card (in some cases without any on-board source of power or computing capabilities) is configured to maintain access information for digital bearer assets. The physical card may include disposed thereon a single address operable to receive digital bearer assets in one or more transactions on a decentralized computing platform, like a blockchain-based decentralized computing platform. Other decentralized computing platforms utilize different address generation protocols, thus preventing use of a single address on those other platforms. A set of addresses is generated, each address corresponding to a given decentralized computing platform. Each address is based on a same underlying key-pair, and a primary address is selected from the set for a given card. The remaining addresses in the set are stored, without storage of the public key or private key, and returned in a response to a request for additional addresses of the currency card.
Owner:BALLET GLOBAL INC
Methods for decentralized genome storage, distribution, marketing and analysis
PendingUS20200073560A1Easy to optimizeEasy to understandInput/output to record carriersData stream serial/continuous modificationData packBio molecules
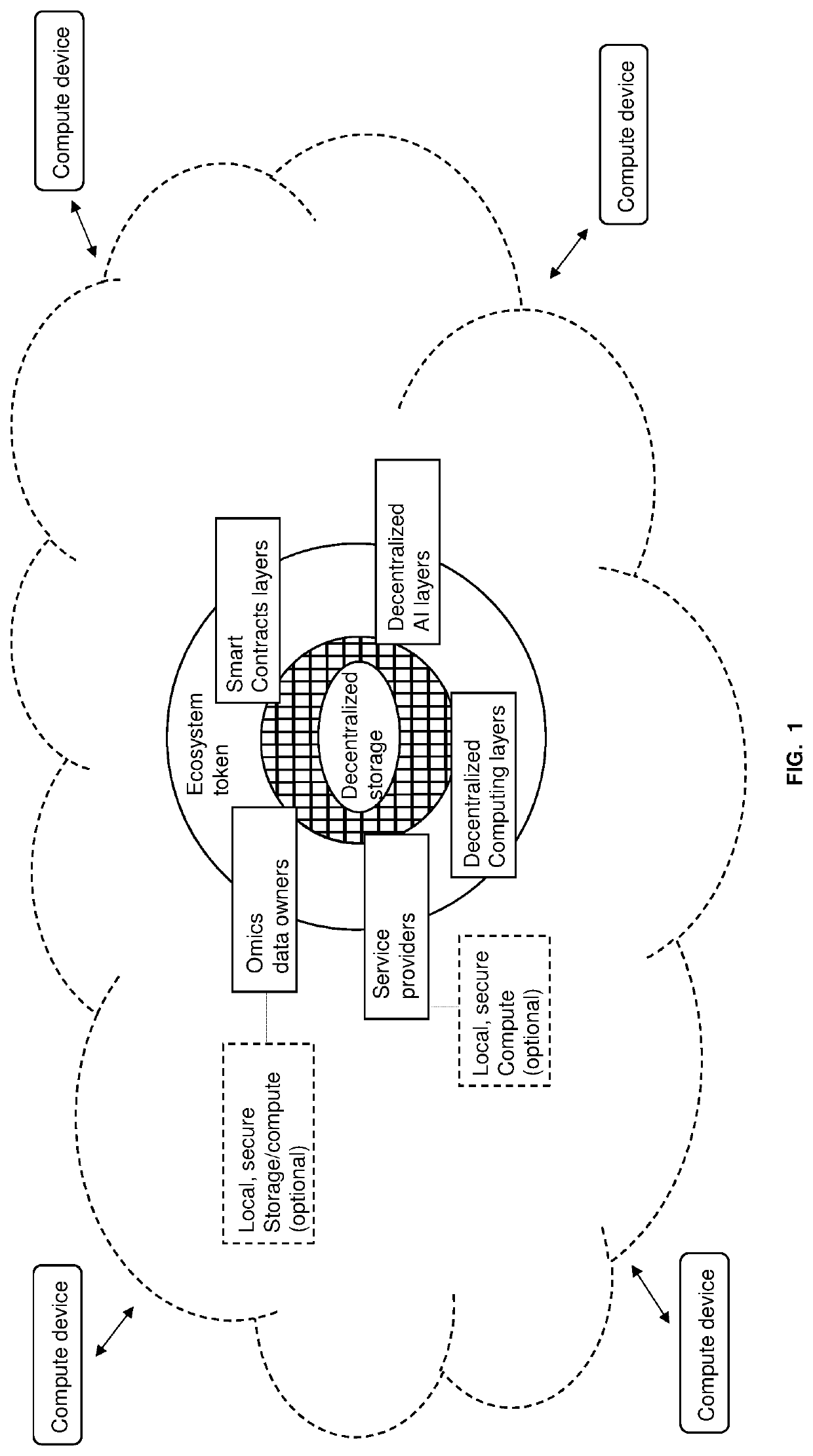
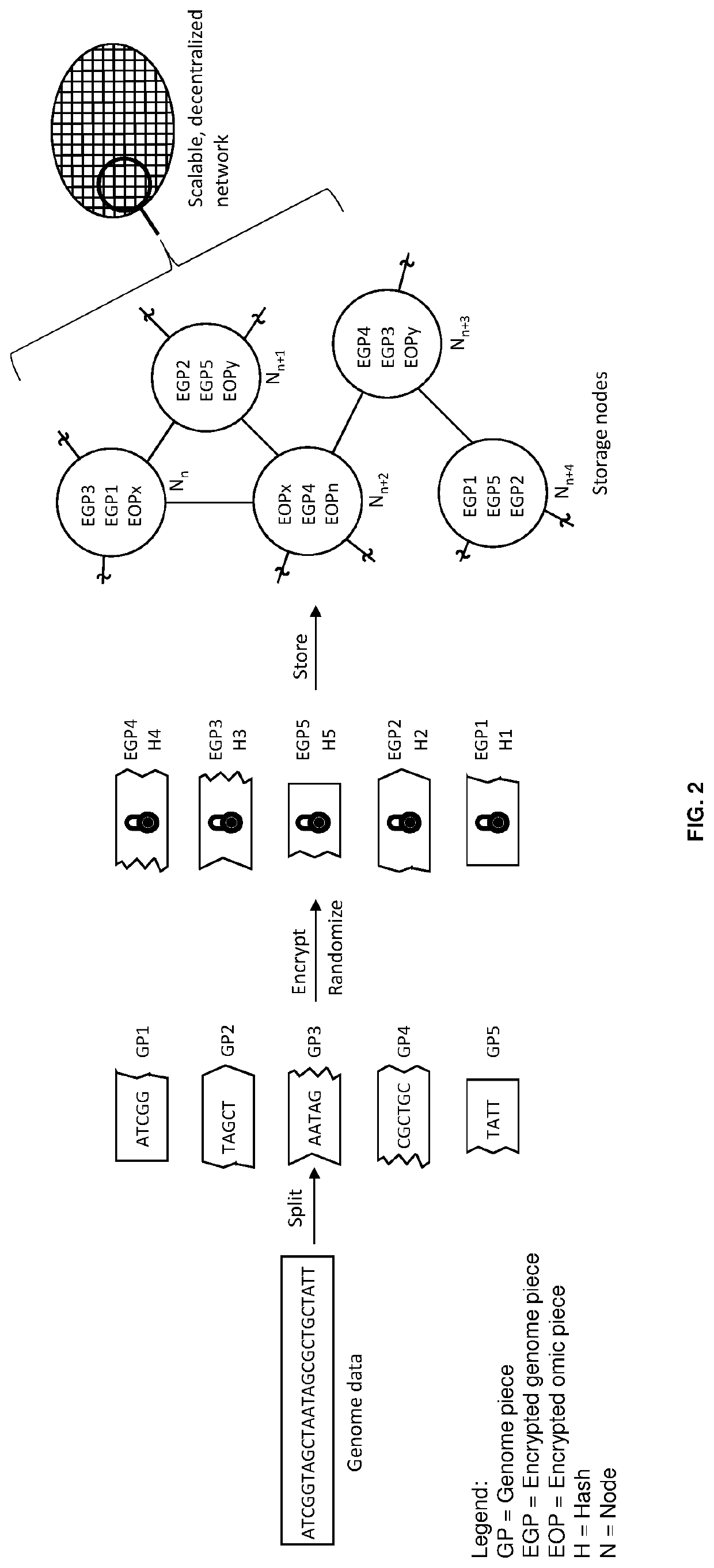
Techniques for storing omics data that indicates long sequences of elements associated with a particular biological molecule include receiving digital omics data comprising over two kilobytes. The digital omics data is split into multiple partitions. The maximum partition size is much less than then a number of elements in a typical instance of the particular biological molecule. Each partition is encrypted. Each encrypted partition is inserted into a corresponding data packet that includes an owner field that uniquely indicates an owner of the omics data. Each data packet is uploaded into a non-centralized, peer-to-peer distributed storage network. Thus, genome data is encrypted and stored in a distributed, scalable, fully decentralized, fast, and highly secure network. The network further provides for decentralized computing, trustless validation of the genomes by way of oracles and trustless genome analysis by third party providers through smart contracts.
Owner:GENETIC INTELLIGENCE INC
System and Method for Toll Transactions Utilizing a Distributed Ledger
ActiveUS20190180519A1Ticket-issuing apparatusEncryption apparatus with shift registers/memoriesDecentralized computingManagement system
The present disclosure relates to implementing an electronic toll data collection management system in a decentralized computing network that employs a distributed ledger. An electronic toll data collection management system may comprise a plurality of nodes, wherein the plurality of nodes are connected to each other over a communication network. Each node may have access to a copy of a distributed ledger, wherein the plurality of nodes is configured to utilize blockchain protocols to verify and record a transaction occurring within the distributed ledger. Data may be recorded as a block, wherein a blockchain is formed by the addition of blocks. Each block may be encrypted and linked to a previous block, wherein a consensus must be reached to update the distributed ledger with the addition of a new block
Owner:HAUSMAN PROPERTIES LLC
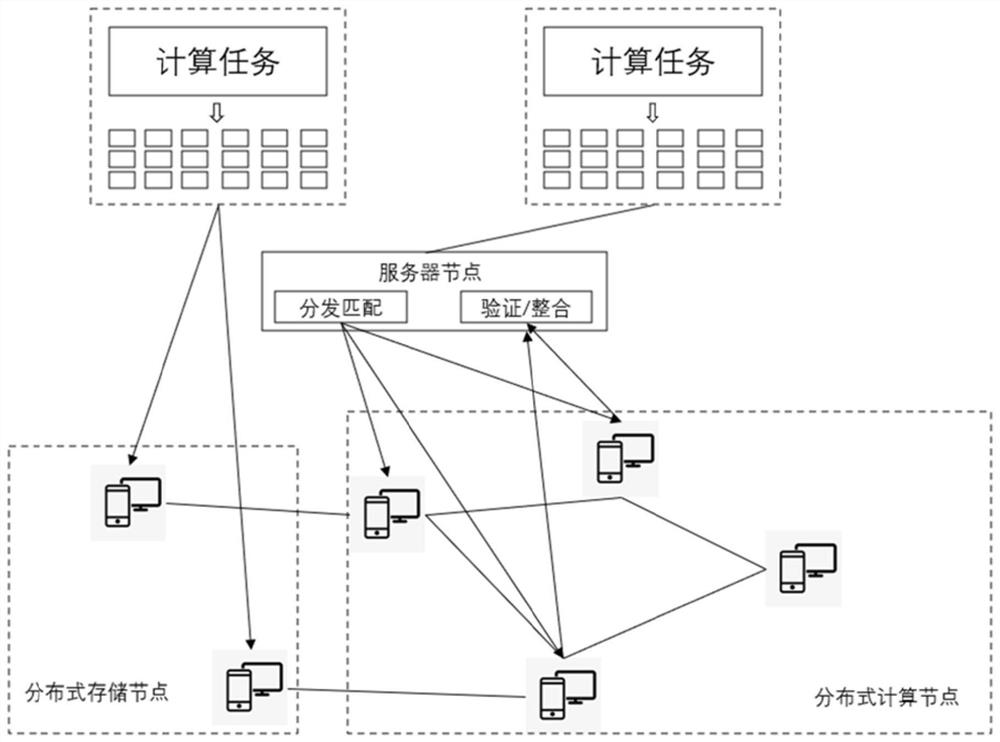
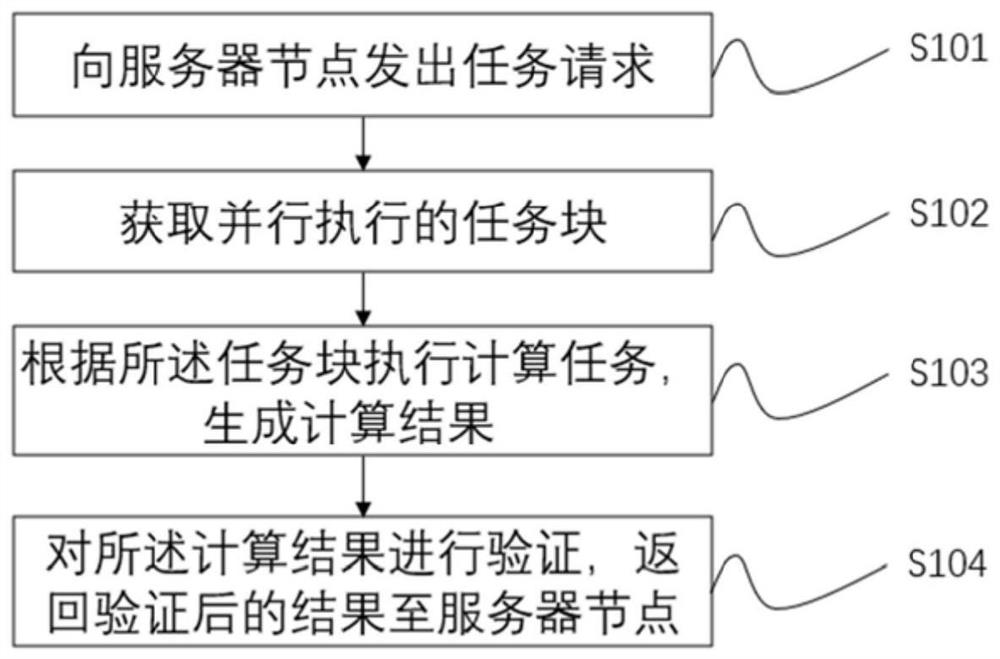
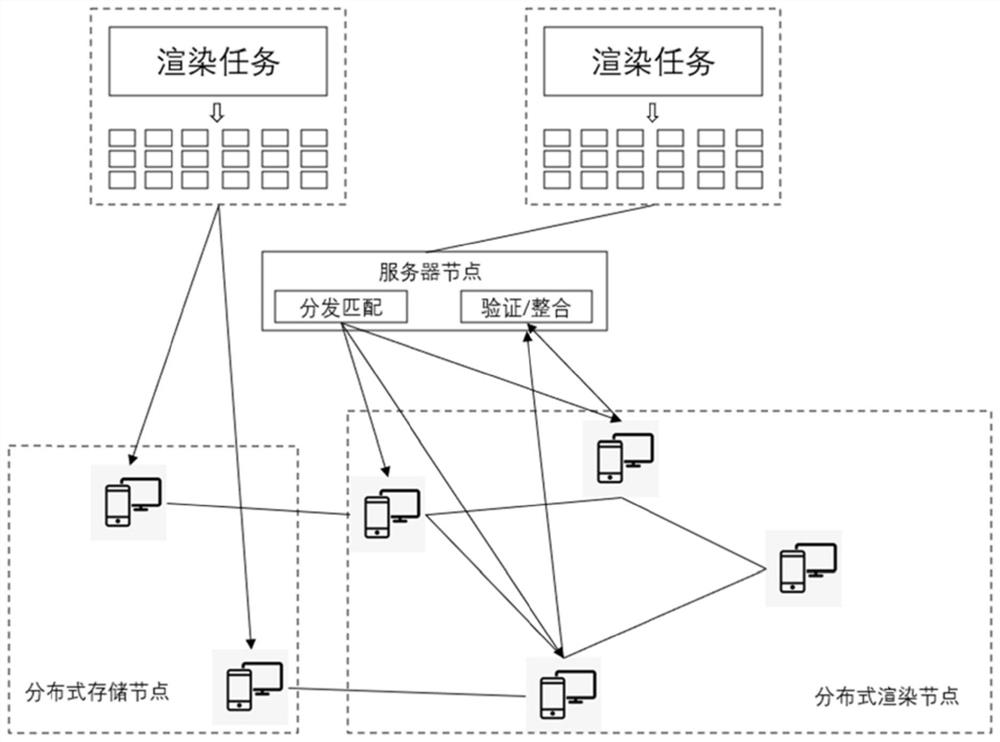
Method and system for sharing computing power resources and storage medium
PendingCN111949394AAchieve autonomyAchieve Indiscriminate AutonomyResource allocationParallel computingEngineering
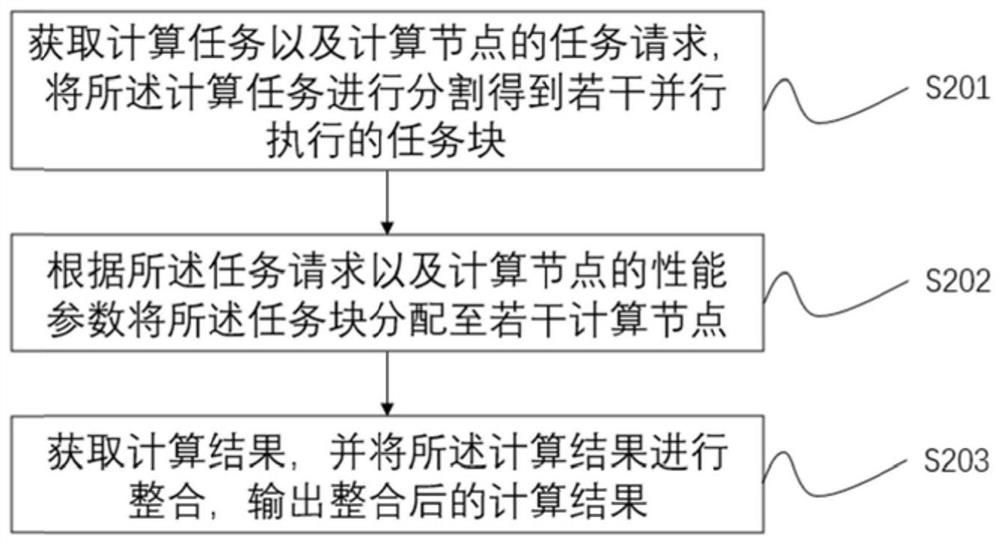
The invention provides a method and system for sharing computing power resources and a storage medium. The method comprises the following steps: sending a task request to a server node; obtaining taskblocks which are executed in parallel; executing a calculation task according to a task block to generate a calculation result; verifying the calculation result, and returning a verified result to the server node; The task request is actively put forward according to computing nodes, a large number of task blocks generated after task processing and splitting are reasonably distributed to all available computing nodes in a network, optimal distribution is guaranteed, powerful decentralized computing resources are provided for high-strength computing type tasks by utilizing the idle states of the computing nodes, and the data processing efficiency is higher; and through an active request and distribution matching mechanism, the distribution of the computing tasks is more reasonable, and thenon-difference computing node autonomy is further realized, so that the method can be widely applied to the technical field of distributed computing networks.
Owner:GUANGZHOU JIUDI DIGITAL TECH CO LTD
Cross-partition calls in partitioned, tamper-evident data stores
ActiveUS20210165890A1Input/output to record carriersEncryption apparatus with shift registers/memoriesTamper resistanceComputer network
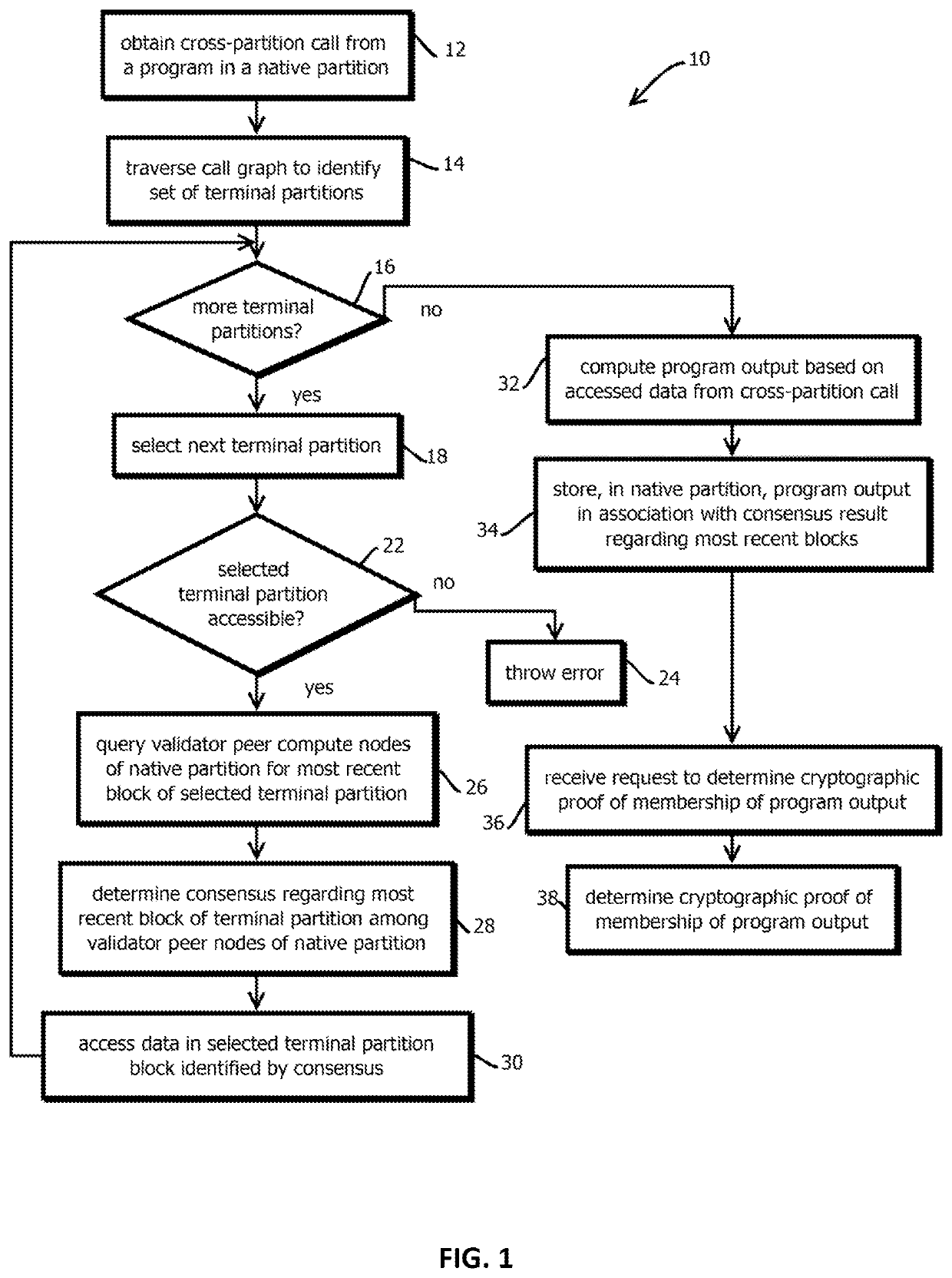
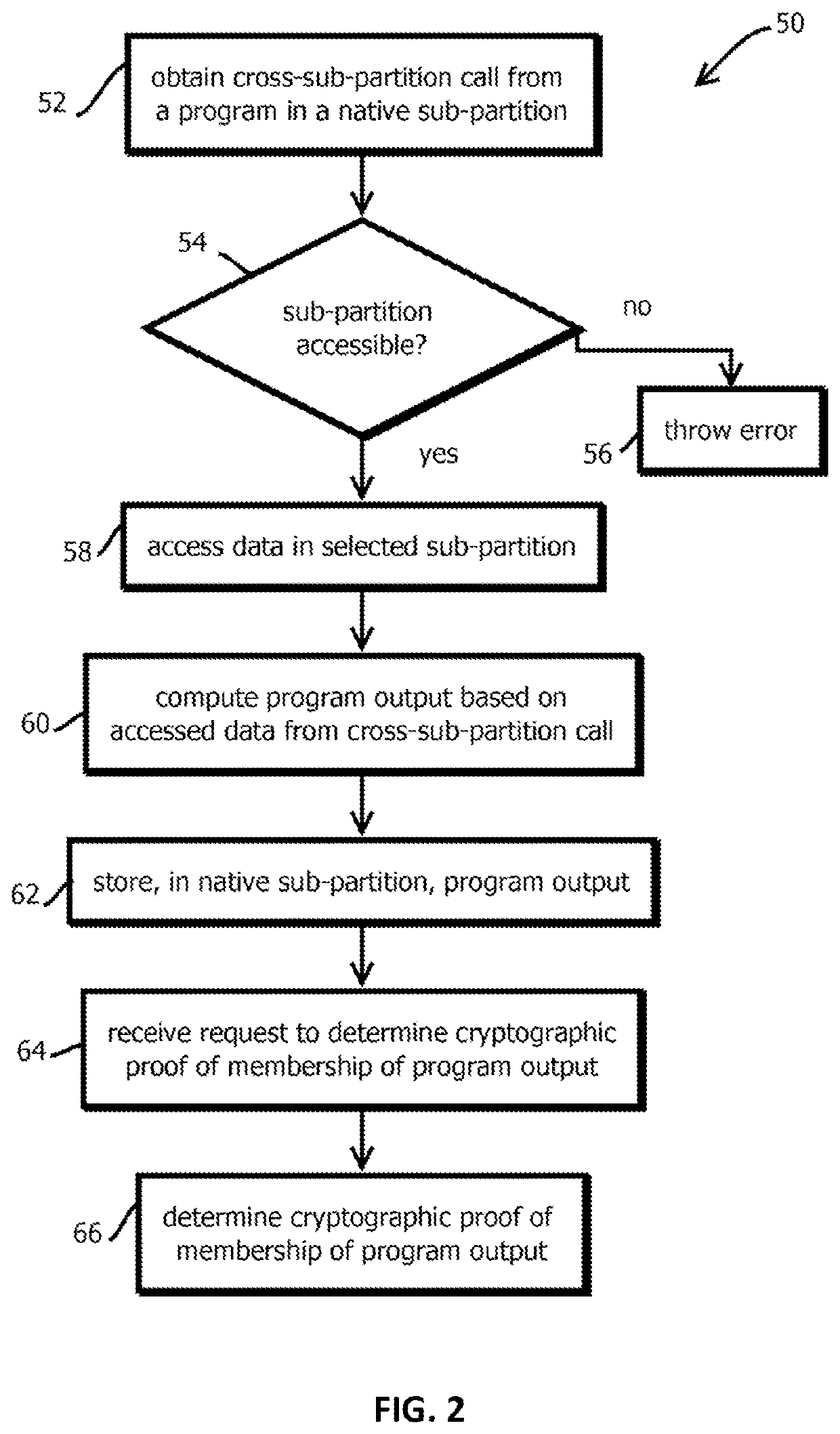
Provided is a process that includes: obtaining a first request by a first program associated with a first sub-partition of a first partition of a tamper-evident data store of a decentralized computing platform to read data stored in either (i) a second sub-partition of the first partition of the tamper-evident data store of the decentralized computing platform, or (ii) a second partition of the tamper-evident data store of the decentralized computing platform; determining with a subset of peer computing nodes of a set of peer computing nodes that the first program is authorized to read from the second sub-partition or the second partition; and in response to the determination, causing the requested data to be read from the second sub-partition or the second partition.
Owner:SCHVEY INC D B A AXONI
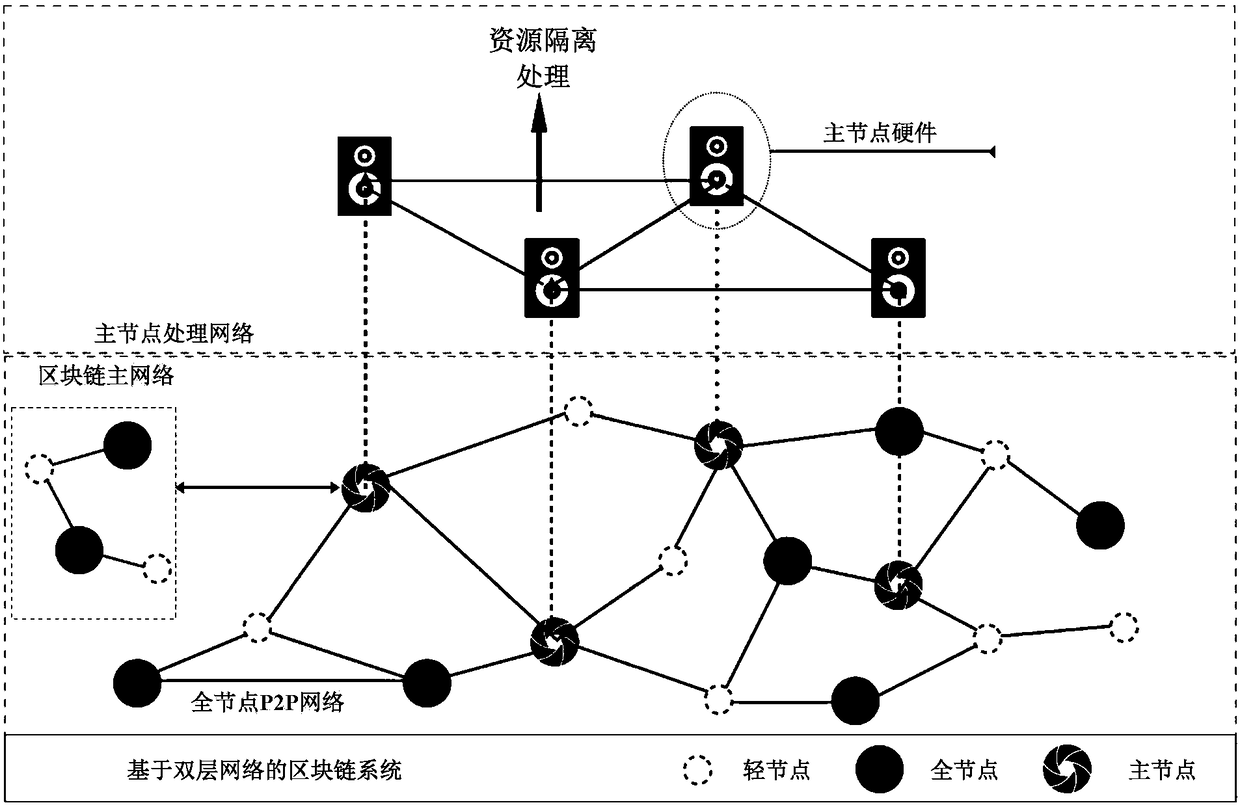
Decentration computation system based on double-layer network
ActiveCN108347483AReduce processing constraintsSmall amount of calculationPayment circuitsTransmissionResource isolationChain network
The invention discloses a decentration computation system based on a double-layer network. The system is constituted by a plurality of light nodes, a plurality of full nodes, and a plurality of mainnodes. A plurality of light nodes, a plurality of full nodes, and a plurality of main nodes are used to form a block chain main network, and a plurality of main nodes are used to form a main node processing network. A plurality of light nodes are used to store user specific data in the block chain network. A plurality of full nodes and a plurality of main nodes are used for a consensus mechanism to store a complete block chain. In the main node processing network, a plurality of main nodes comprise computation nodes having computation functions, which are used to carry out off-chain data computation tasks to acquire computation results. According to the technical scheme provided by the invention, a plurality of main nodes are used for resource isolation, and high expandability is provided,data processing constraints are reduced, and the data throughout of the system is effectively improved.
Owner:BEIJING QIHOO TECH CO LTD
Federated identity management with decentralized computing platforms
ActiveUS11057366B2Key distribution for secure communicationDigital data protectionInternet privacyEngineering
Provided is a process that establishes user identities within a decentralized data store, like a blockchain. A user's mobile device may establish credential values within a trusted execution environment of the mobile device. Representations of those credentials may be generated on the mobile device and transmitted for storage in association with an identity of the user established on the blockchain. Similarly, one or more key-pairs may be generated or otherwise used by the mobile device for signatures and signature verification. Private keys may remain resident on the device (or known and input by the user) while corresponding public keys may be stored in association with the user identity on the blockchain. A private key is used to sign representations of credentials and other values as a proof of knowledge of the private key and credential values for authentication of the user to the user identity on the blockchain.
Owner:HYPR CORP
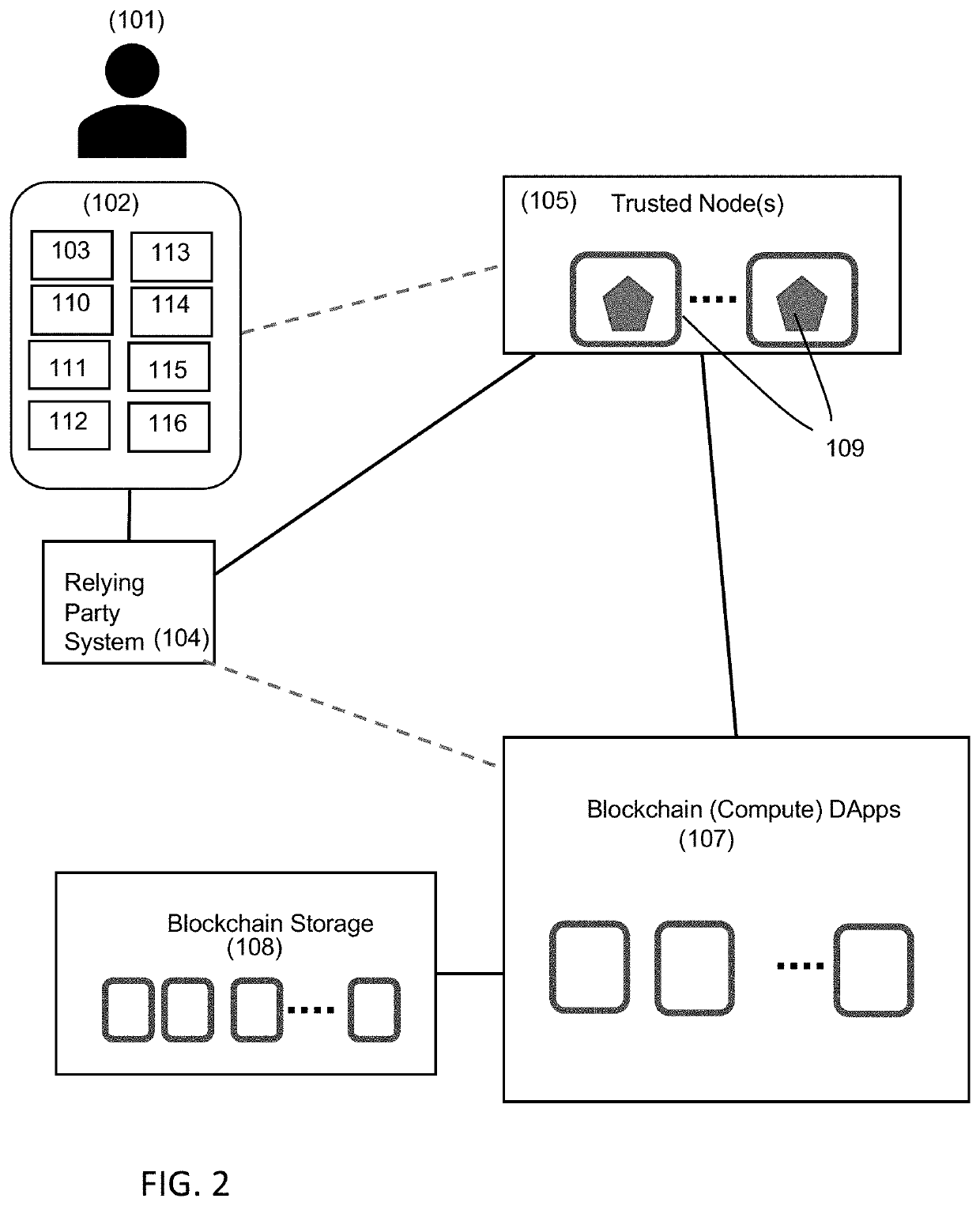
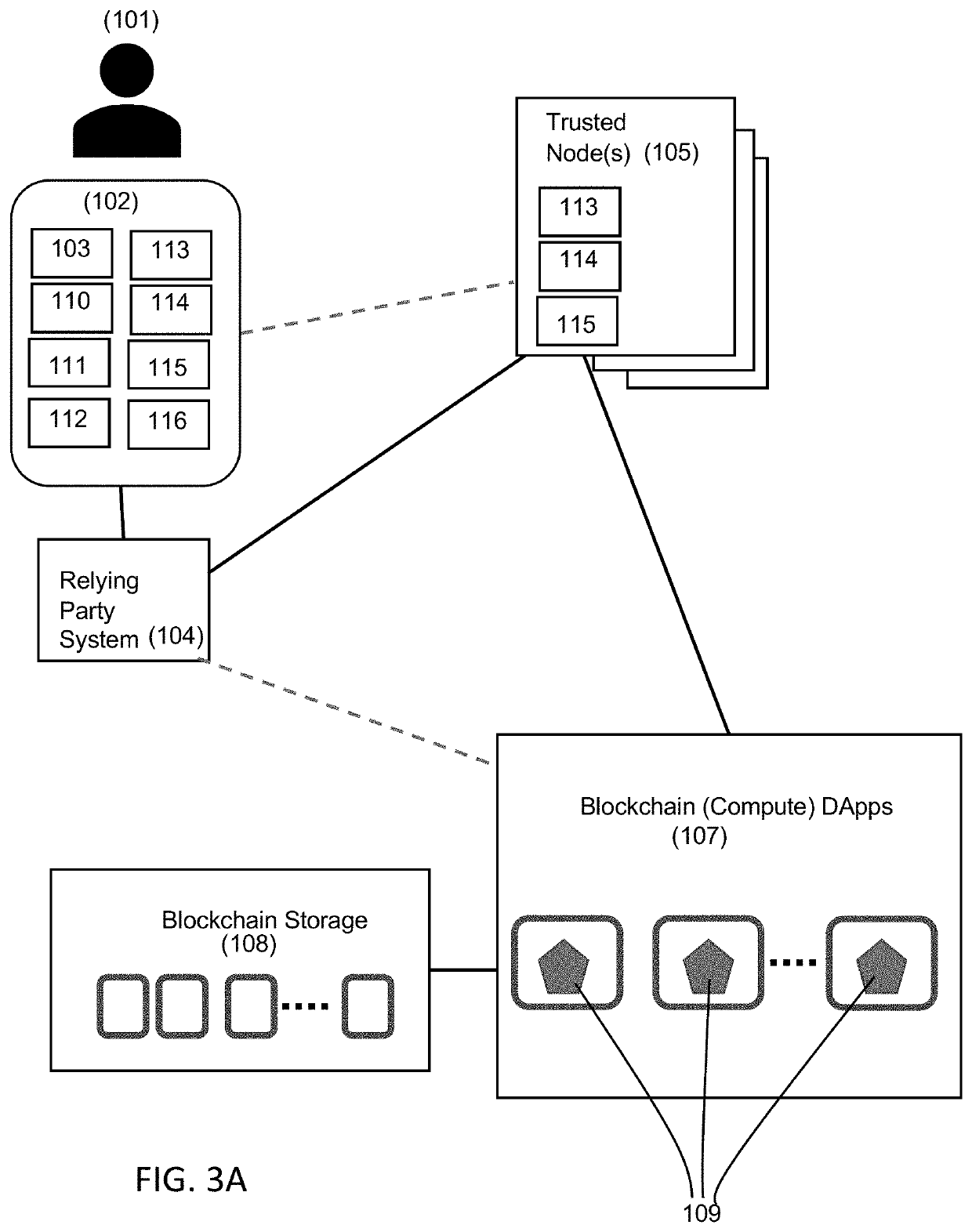
Decentralized computing systems and methods for performing actions using stored private data
PendingUS20210392003A1Key distribution for secure communicationEncryption apparatus with shift registers/memoriesThird partyInformation type
It is typically difficult for a user to have any awareness of which private data is being used by a third party and to control the flow of the private data to the third party. A computing system is provided with a trusted node that stores encrypted private data. When the third party wishes to obtain information types from the user, the trusted node generates a scope document that specifies the requested information types. This scope document is sent to the user device as a challenge. The user device uses the scope document to display the requested information types, and the user provides input to permit providing the information types to the third party. The user device returns a signed challenge response, which includes the scope document. The trusted node then decrypts the encrypted private data, which corresponds to the requested information types, for the third party.
Owner:LOGIN ID INC
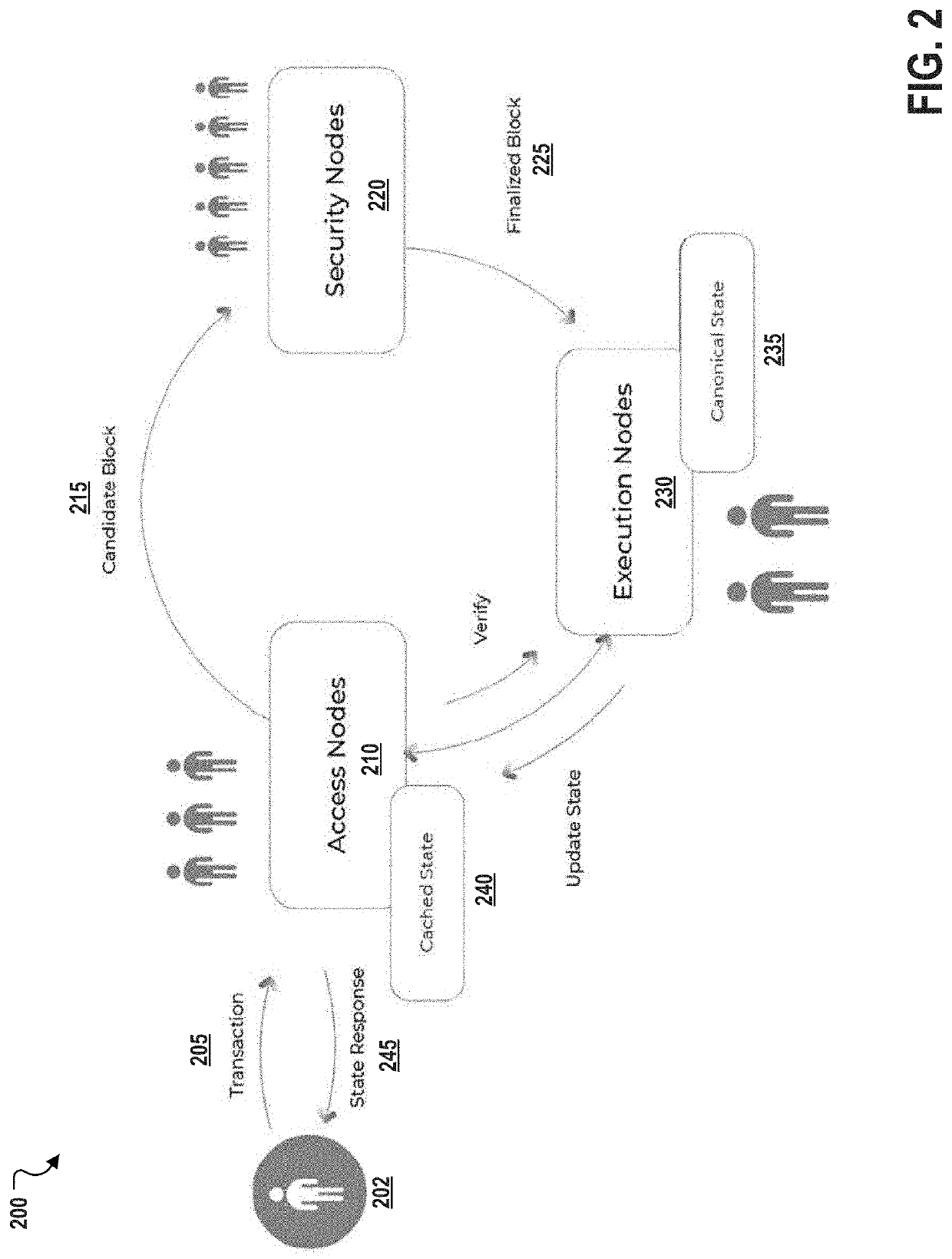
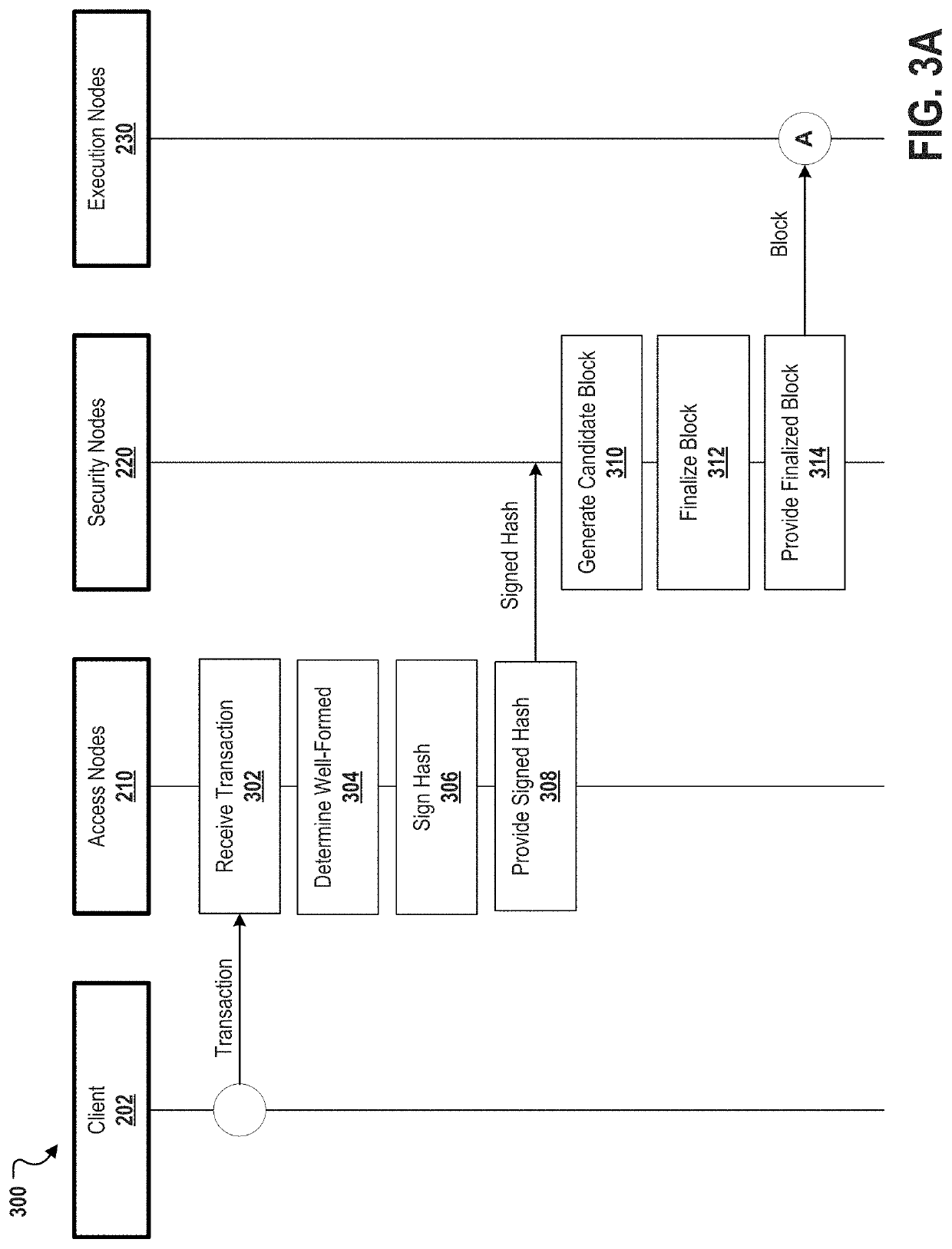
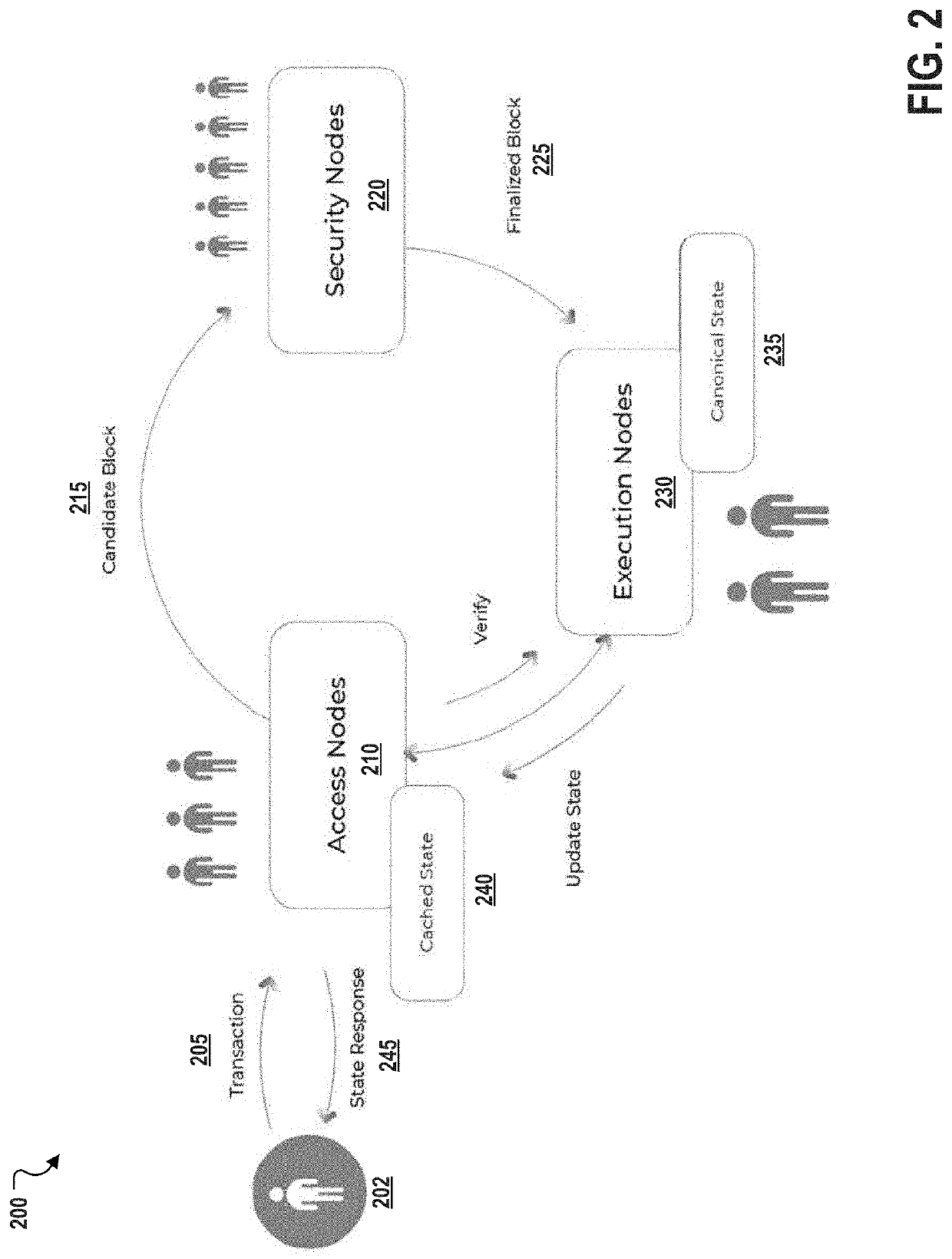
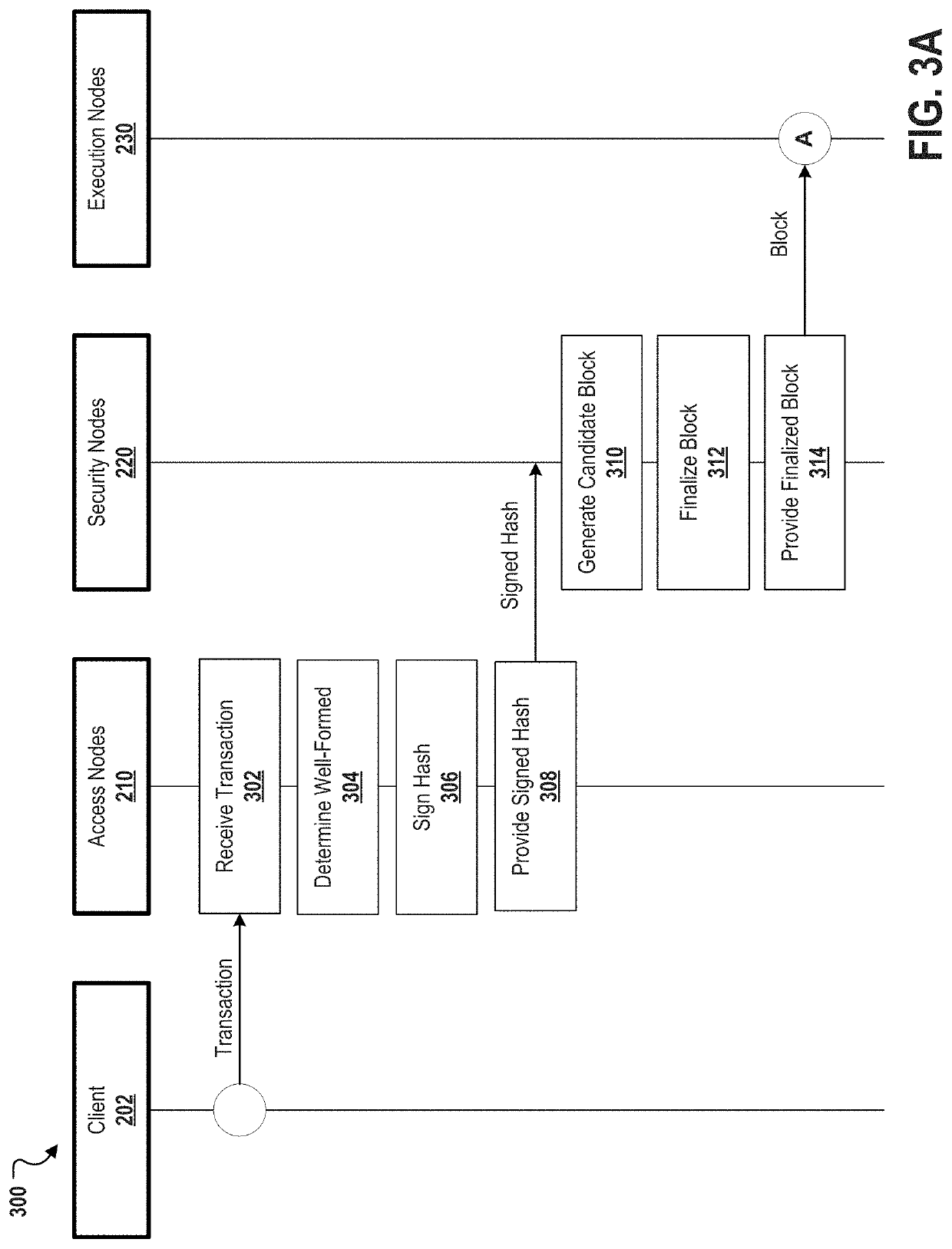
Decentralized computation system architecture based on node specialization
ActiveUS20210273993A1Improve scalabilityIncrease the number ofCryptography processingUser identity/authority verificationComputer networkEngineering
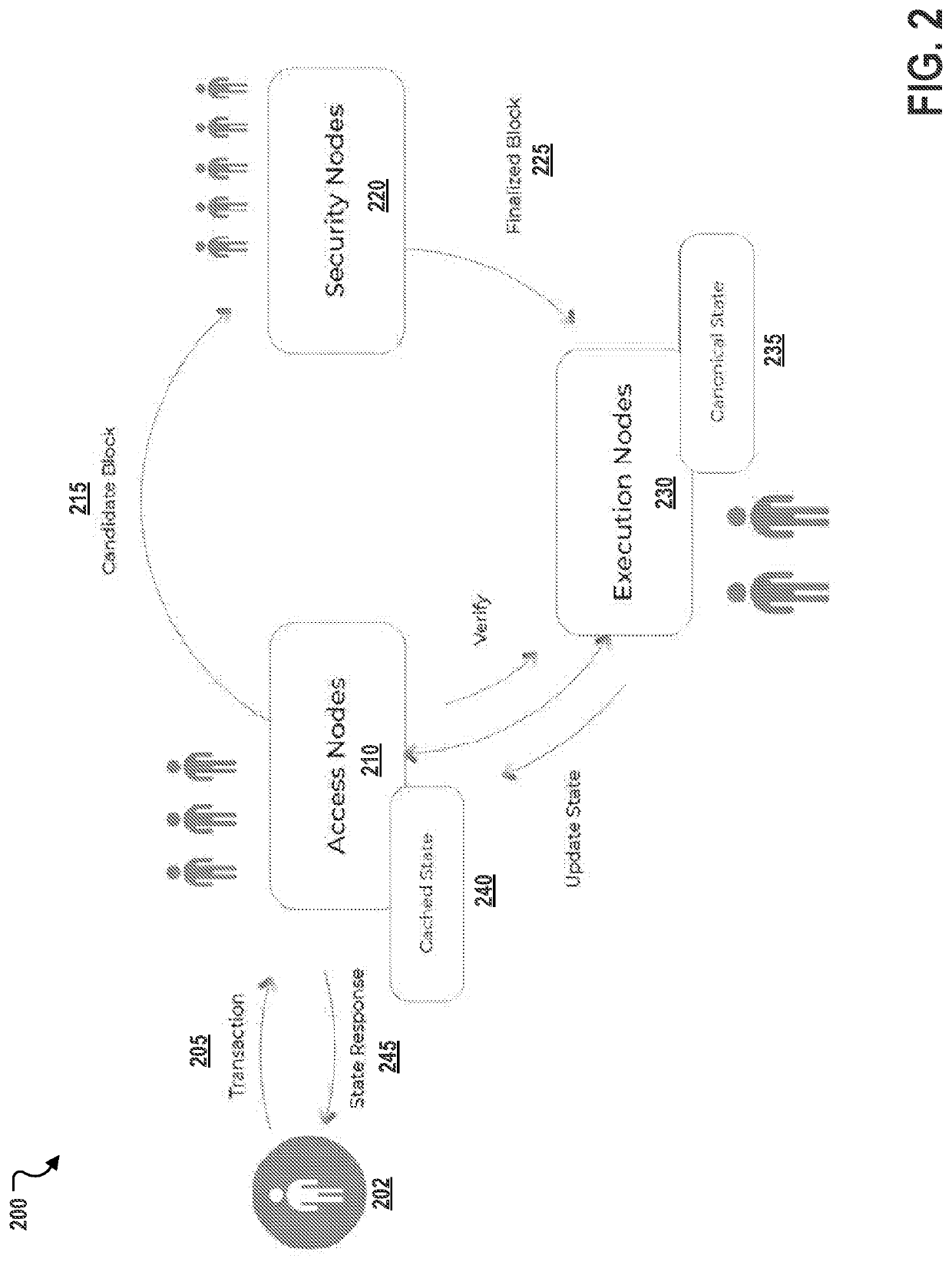
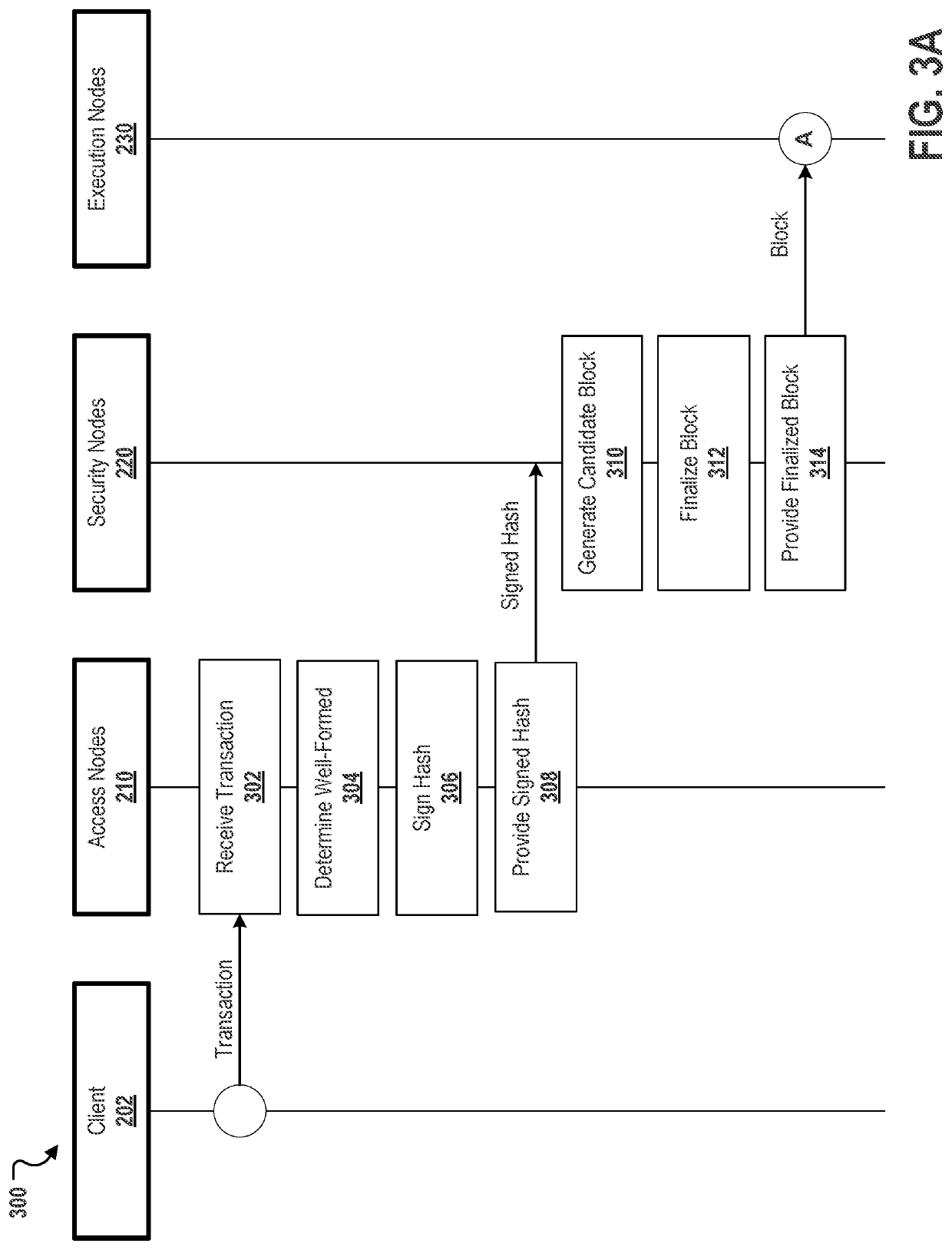
Described are systems, methods, and media for providing secure and scalable decentralized computation for one or more decentralized applications. Features include a blockchain, and a plurality of nodes that are separated into at least a first specialized node type and a second specialized node type. Nodes of the first specialized node type can be assigned non-deterministic tasks to perform, and each of the nodes of the second specialized node type can be assigned deterministic tasks to perform. Thus, the disclosed systems and methods can achieve improvements in speed and cost that scale with hardware capacity without compromising decentralization.
Owner:DAPPER LABS INC
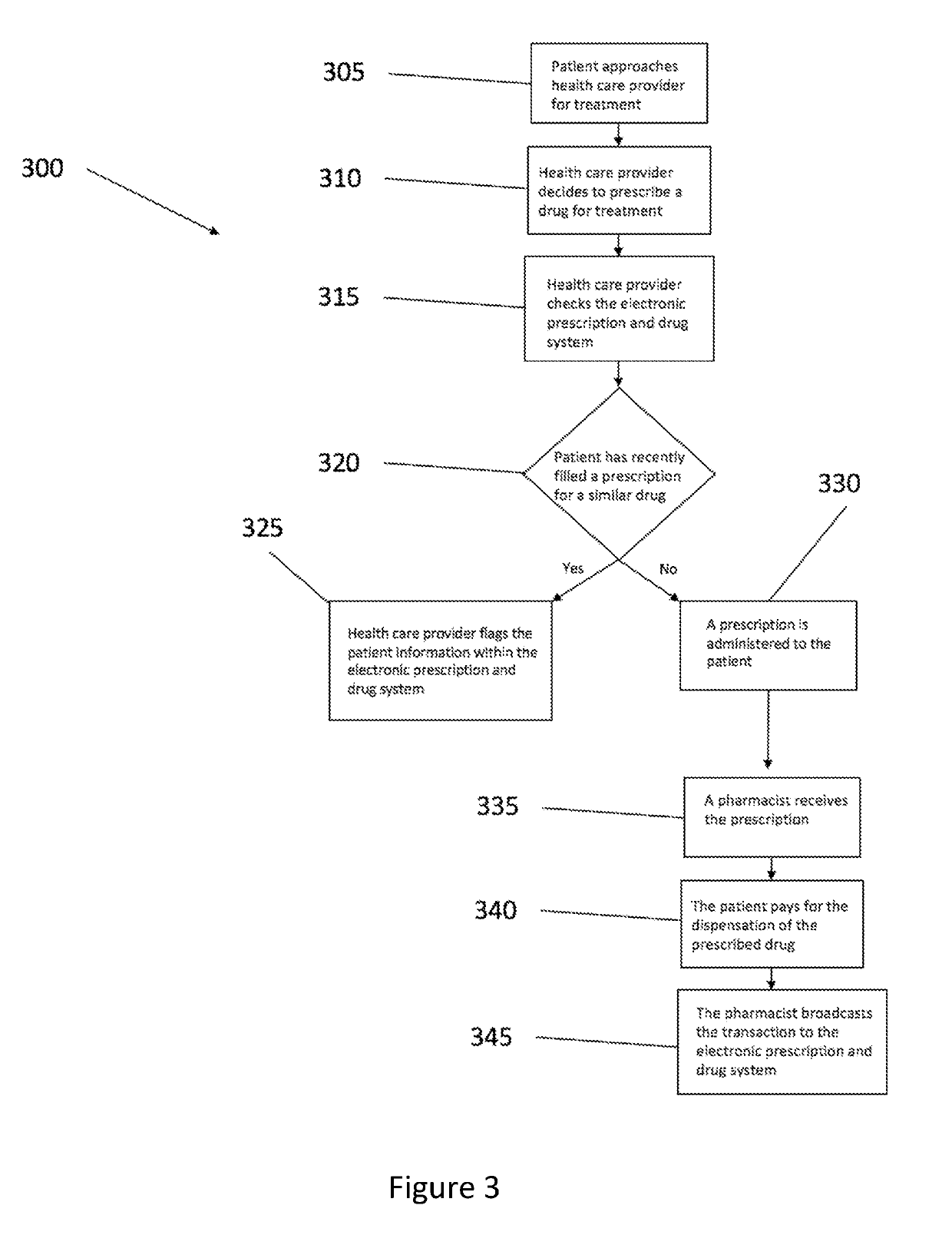
System and method for prescription monitoring and drug dispensation utilizing a distributed ledger
InactiveUS20190206536A1Medical communicationData processing applicationsMedicinePrescription monitoring
The present disclosure relates to implementing an electronic prescription and drug system in a decentralized computing network that employs a distributed ledger. A method for prescribing and dispensing drugs may comprise of examining a patient; checking an electronic prescription and drug system, wherein the electronic prescription and drug system comprises a plurality of nodes, wherein the plurality of nodes comprise a processor, a memory unit, and a bus, wherein the plurality of nodes are connected to each other over a communication network, wherein each of the plurality of nodes has access to a copy of a distributed ledger, wherein the plurality of nodes verify and record transactions occurring within the distributed ledger; administering a prescription; dispensing a drug; and broadcasting transactions to the distributed ledger.
Owner:HAUSMAN PROPERTIES LLC
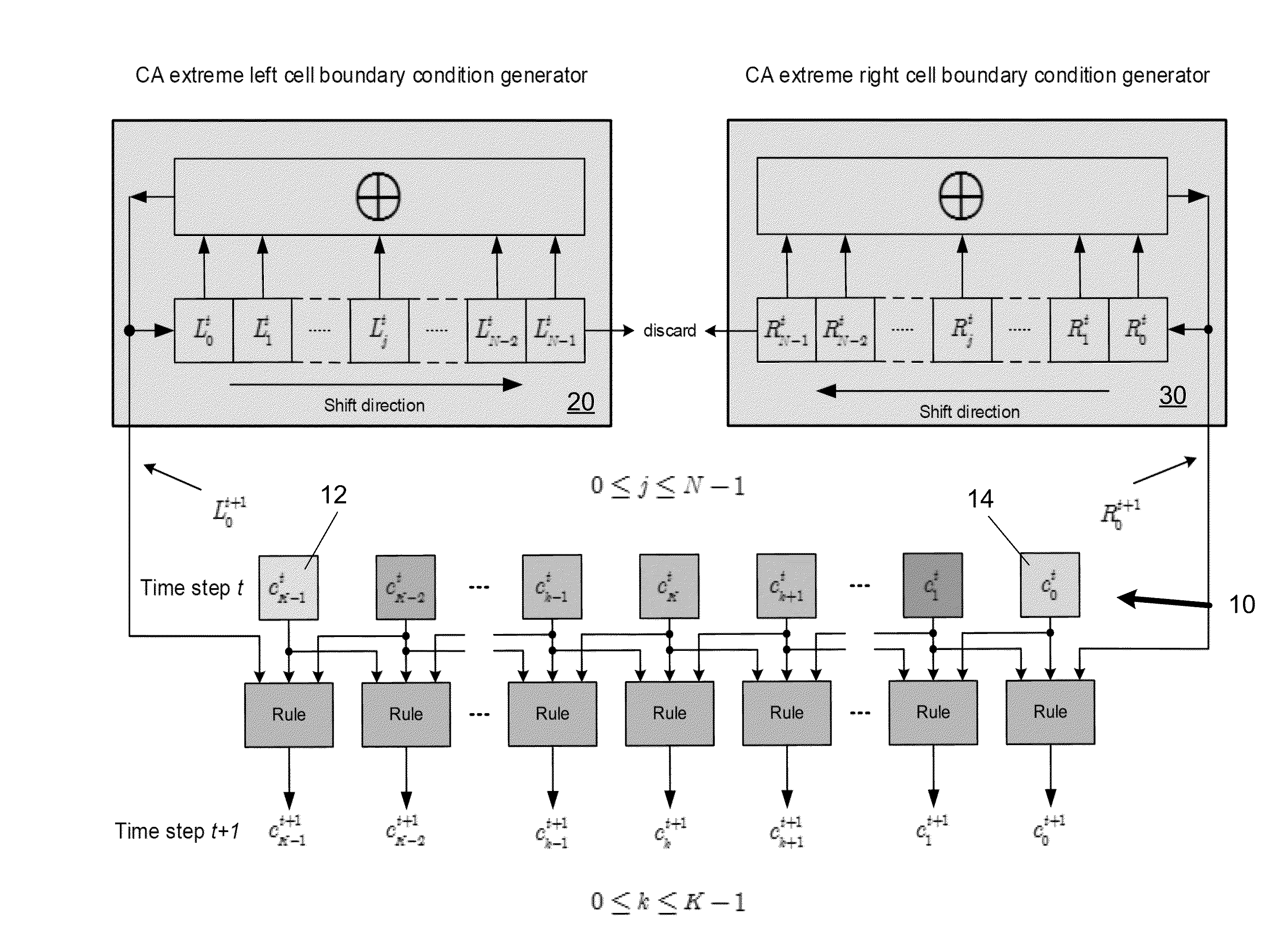
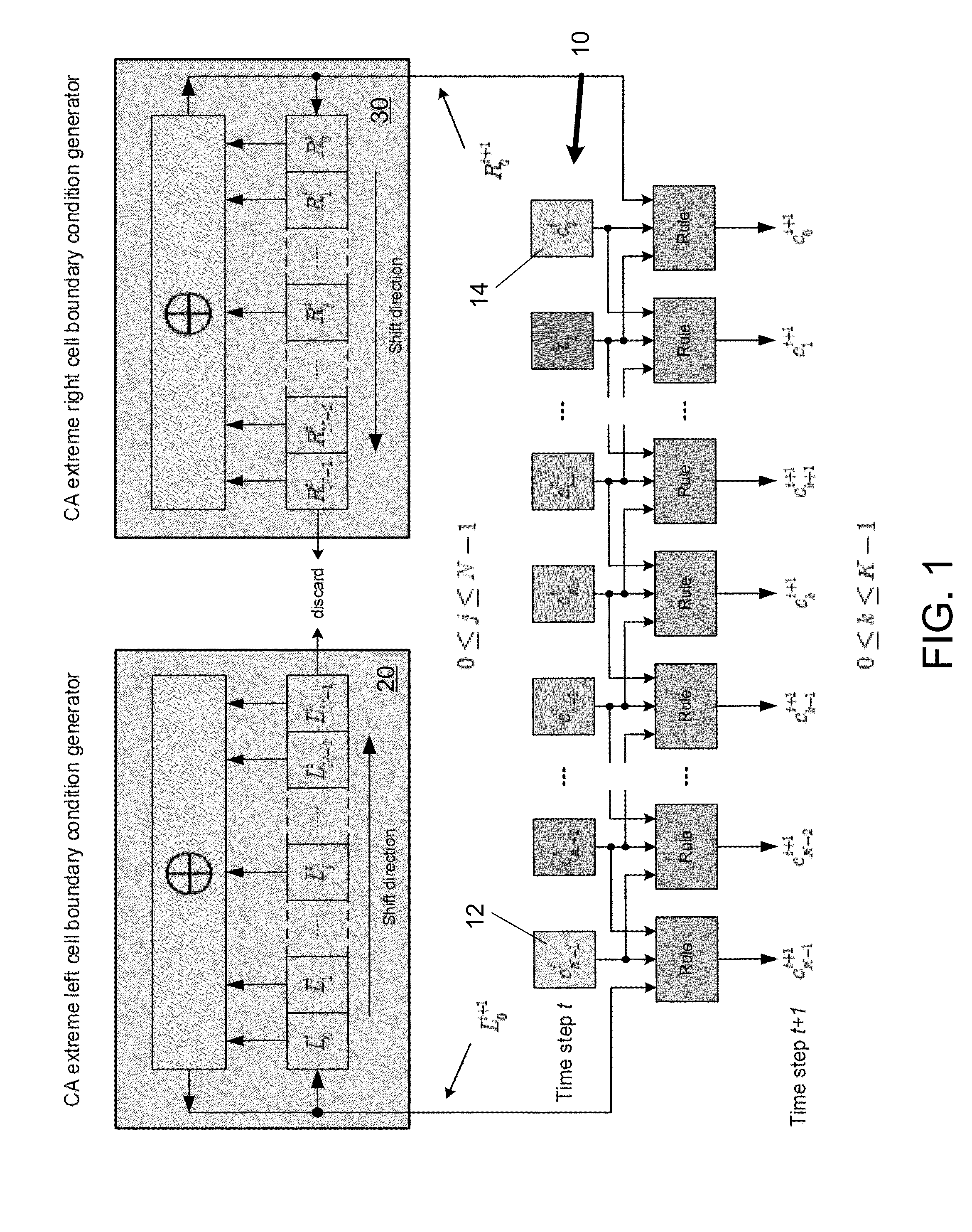
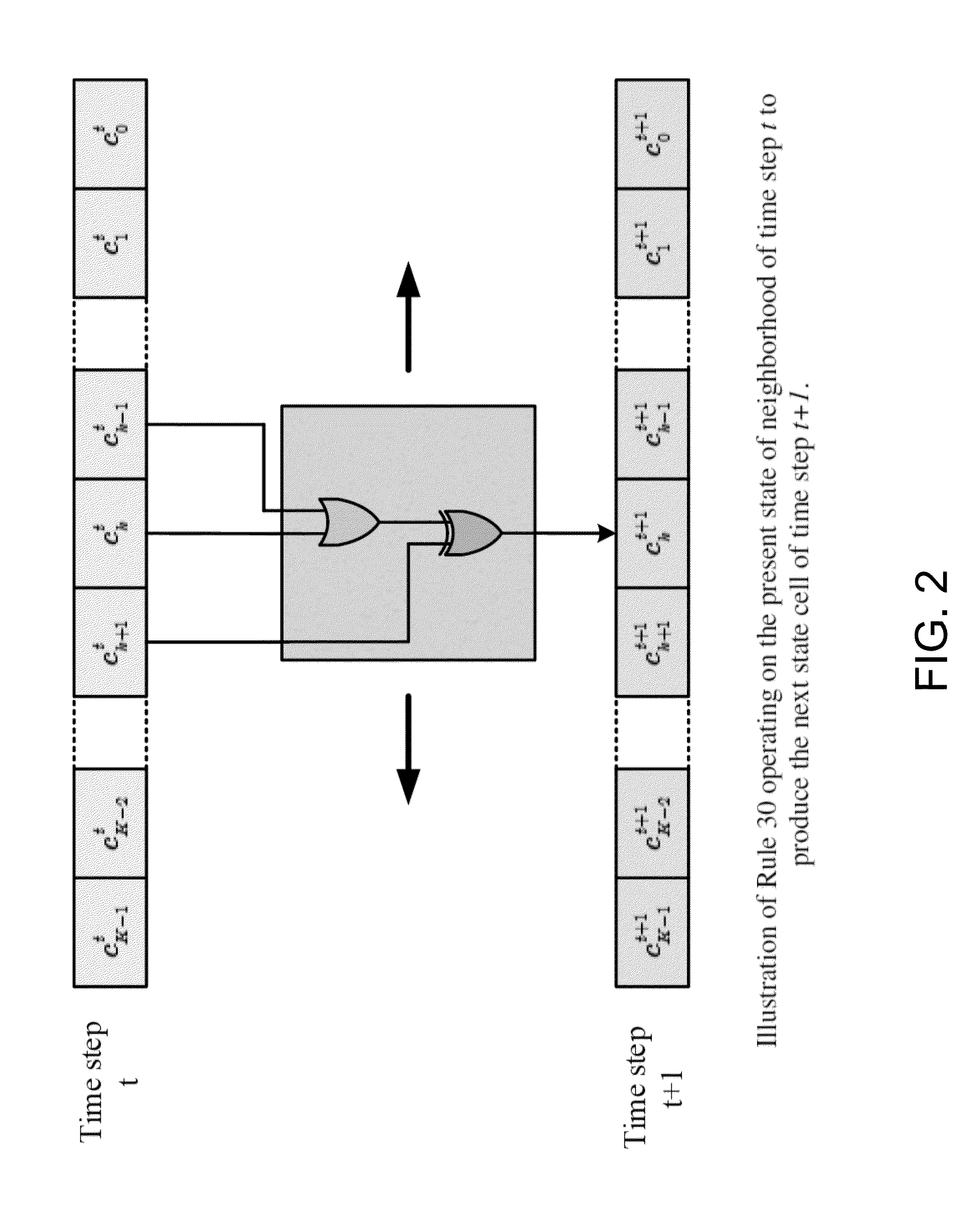
Generating pseudo-random numbers using cellular automata
InactiveUS20150331671A1Improve performanceRandom number generatorsEncryption apparatus with shift registers/memoriesShift registerCellular automation
A method for using cellular automata to generate quality pseudo-random numbers, which may be used in cryptographic and other applications. A cellular automaton is a decentralized computing model that enables the performance of complex computations with the help of only local information. In general, cellular automata comprise a plurality of identical basic memory building blocks that are discrete in time and space, where the structure evolves over time according to a local transition rule. Cellular automata can be used in information security as an alternative for classic Feedback Shift Registers (FSRs) for pseudo-random sequence generation. The outputs of a pair of linear FSRs (LFSRs) act as continuous inputs to the two boundaries of a one-dimensional or two-dimensional elementary cellular automata.
Owner:SALMAN KARIM
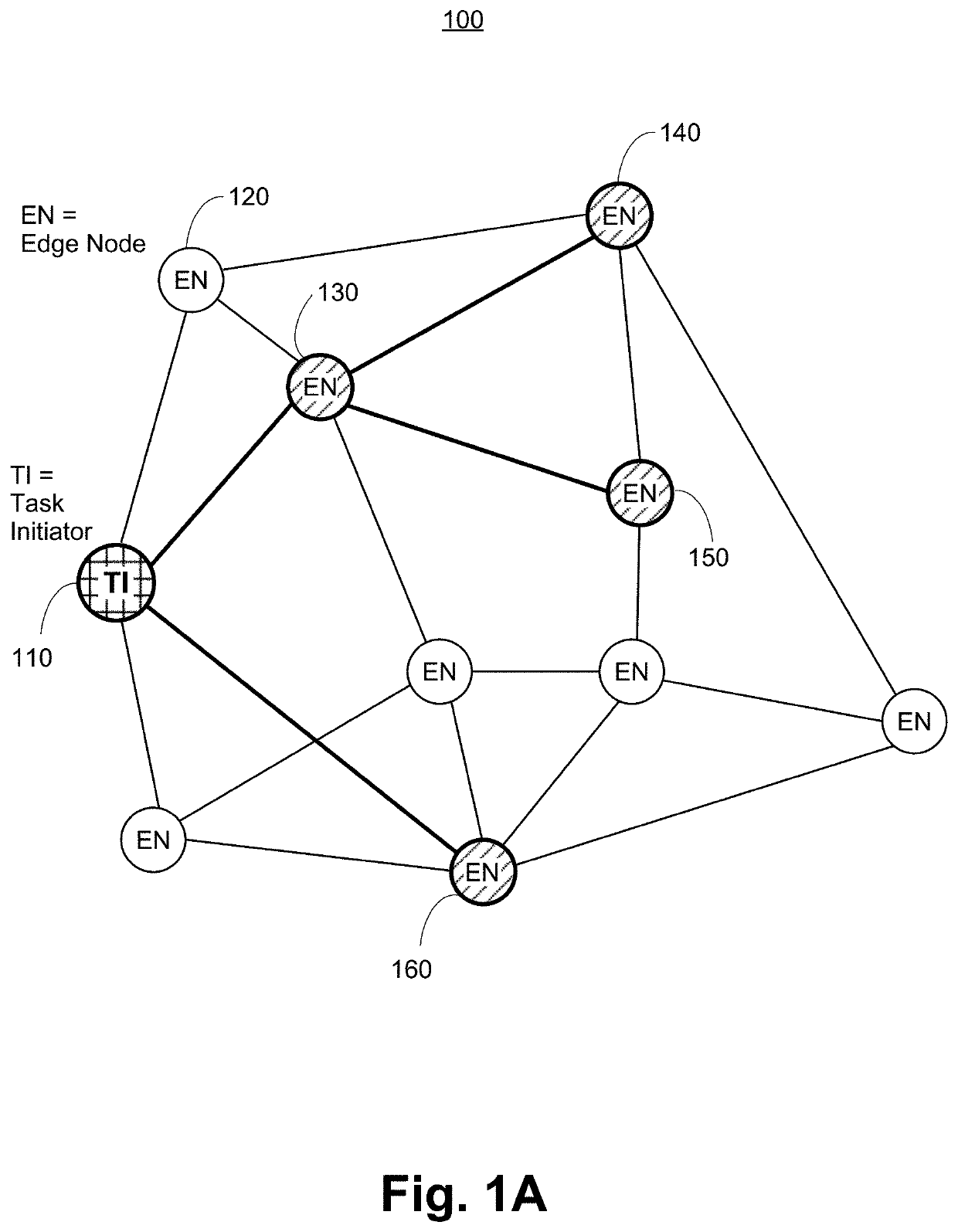
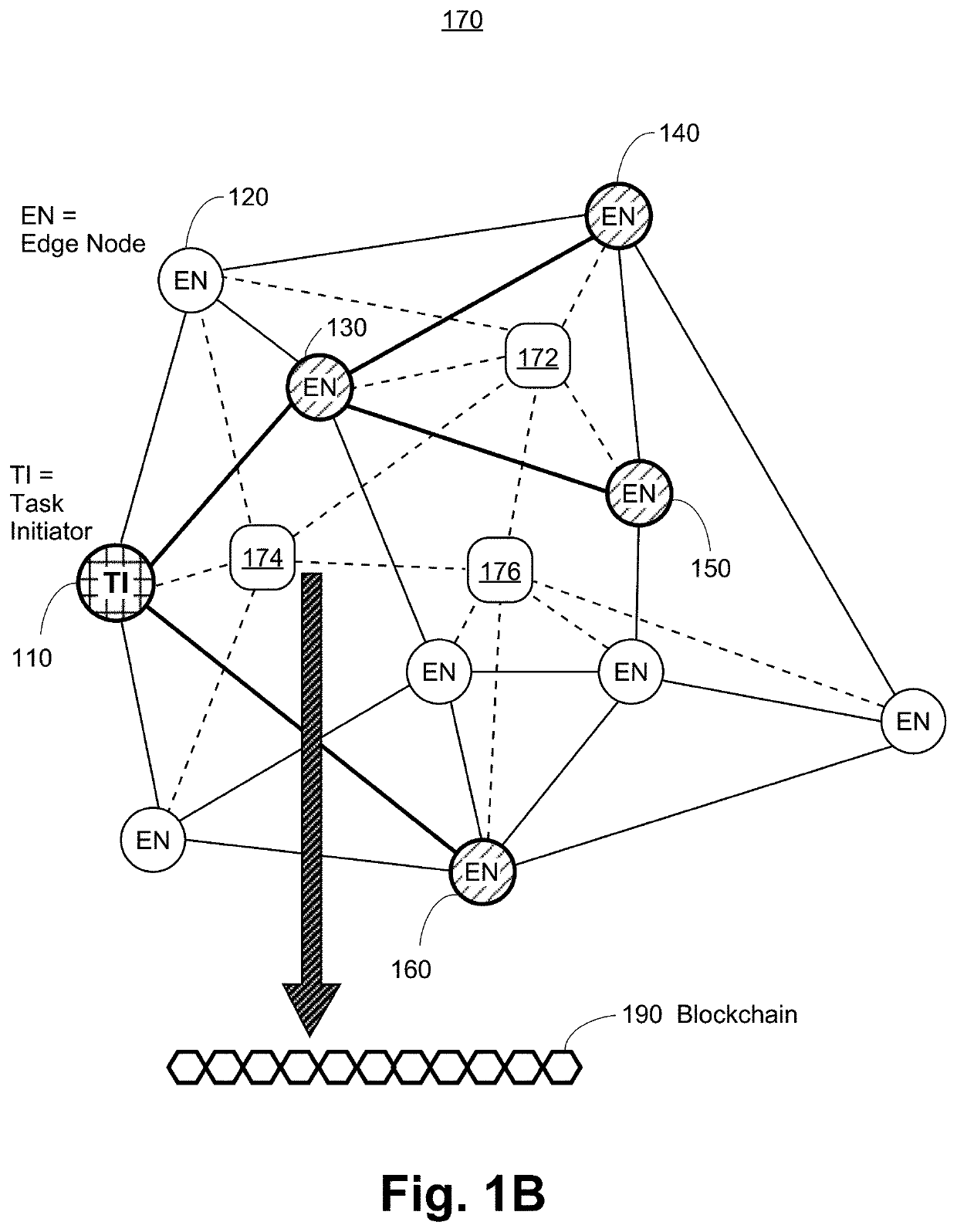
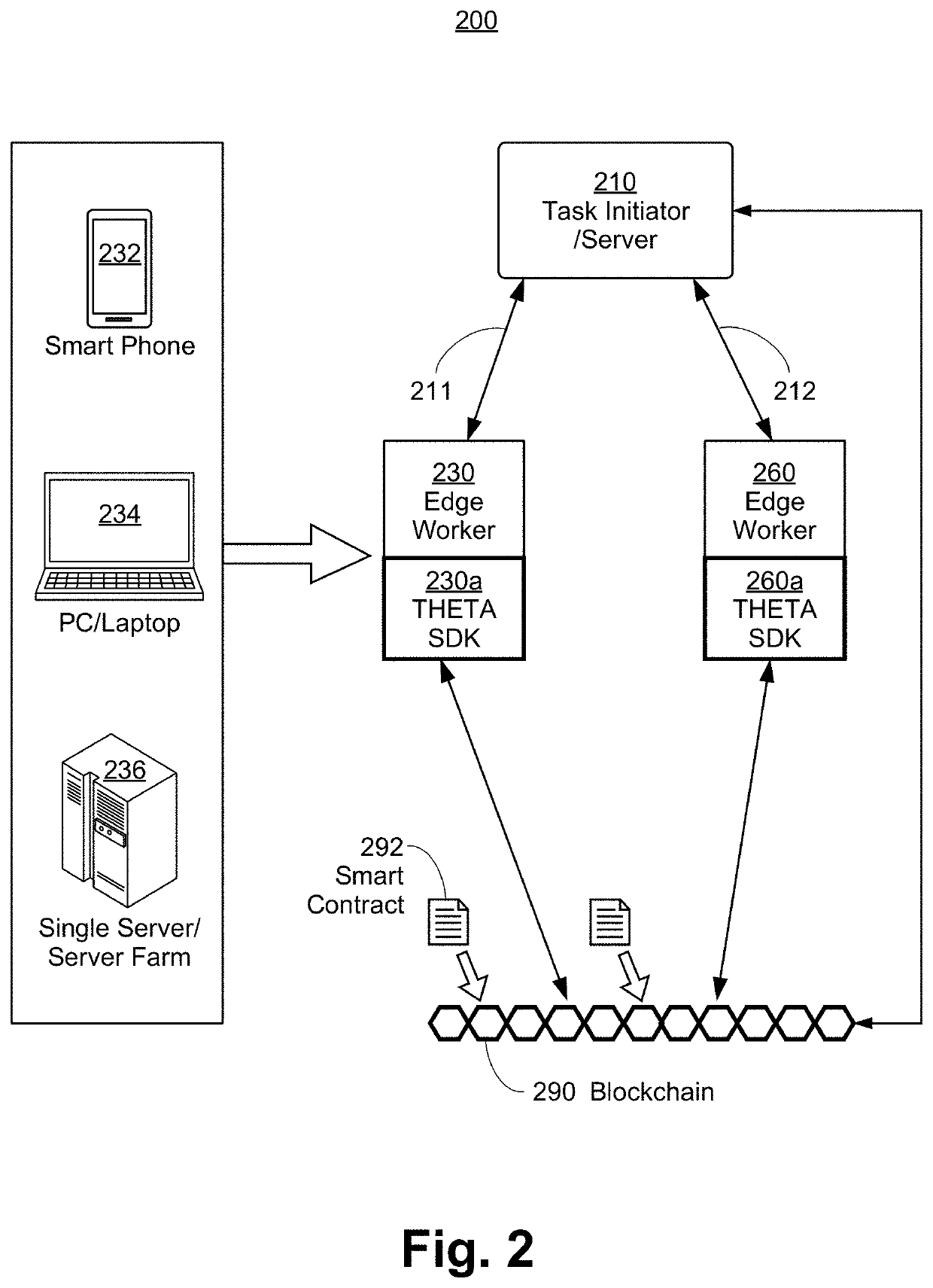
Edge Computing Platform Supported by Smart Contract Enabled Blockchain Network
Methods and systems for blockchain and smart contract-supported decentralized computation are provided. A computation task from a task initiator node is registered on a blockchain, and assigned to an edge computing node within a decentralized computing network, with task details sent by the task initiator to the edge computing node through a secure peer-to-peer connection. The edge computing node determines a solution to the computation task. The solution may be verified on-chain by a smart contract, and a token reward from the task initiator may be given to the edge computing node by the smart contract correspondingly. The solution may alternatively be verified off-chain by the task initiator node, and a token reward may be given to the edge computing node by the smart contract upon solution verification.
Owner:THETA LABS INC
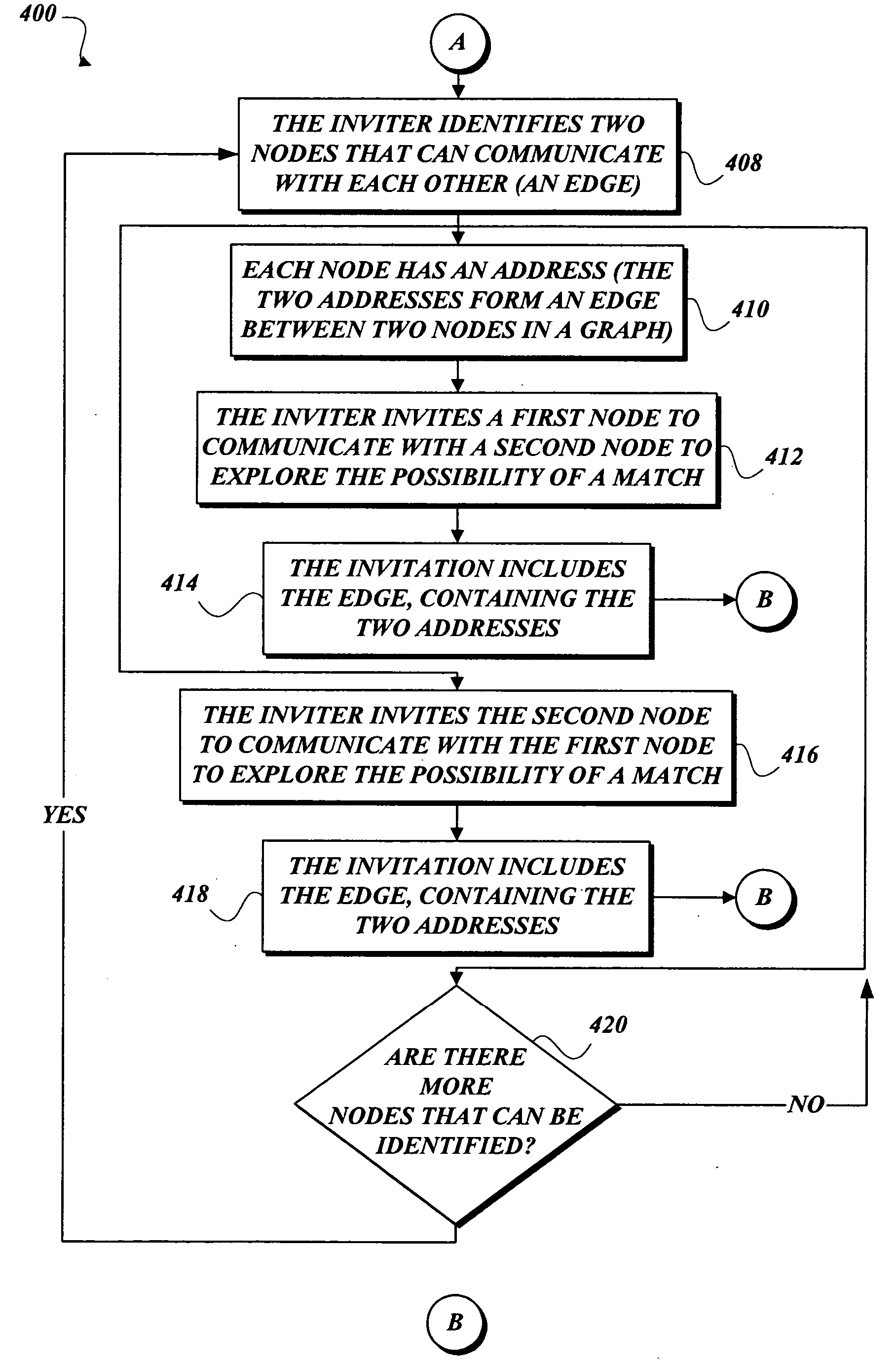
Node matching in a dynamic, decentralized environment
InactiveUS20050204023A1Data processing applicationsProgram synchronisationDecentralized computingTheoretical computer science
Computing entities in a dynamic, decentralized computing environment are treated as if these computing entities were nodes in a graph linked by edges so as to match these nodes until no further matches are possible. New nodes may dynamically be introduced into the decentralized computing environment and yet various embodiments of the present invention continue to match nodes while inhibiting deadlocks in the decentralized computing environment.
Owner:MICROSOFT TECH LICENSING LLC
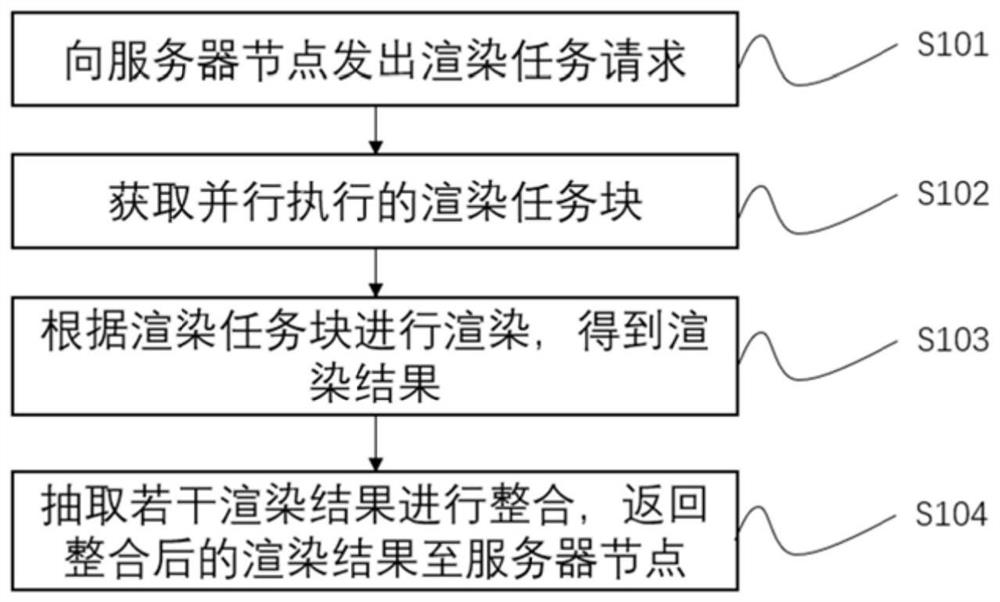
Rendering method and system based on cloud computing chain and storage medium
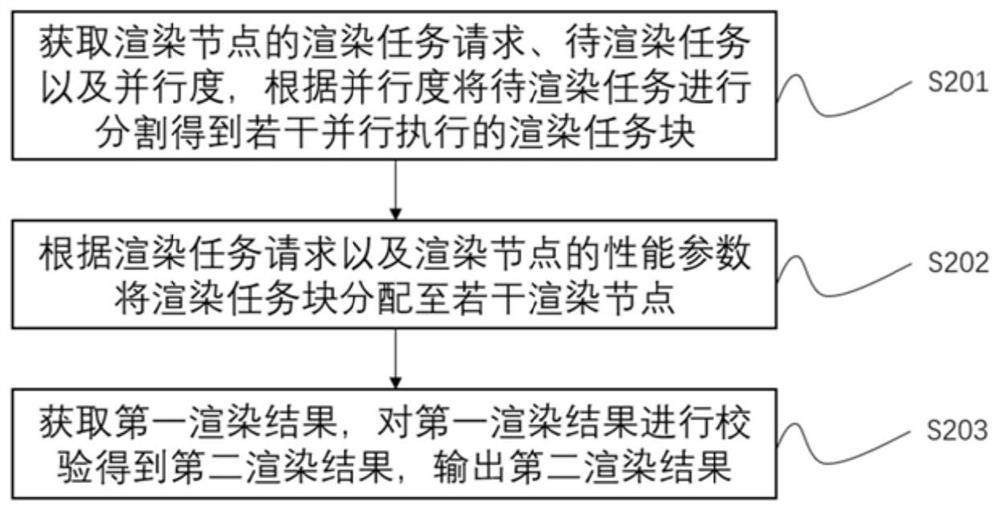
PendingCN111951363AAchieve autonomyAchieve Indiscriminate AutonomyResource allocation3D-image renderingEngineeringDecentralized computing
The invention provides a rendering method and system based on a cloud computing chain and a storage medium. The method comprises the following steps: sending a rendering task request to a server node;obtaining rendering task blocks which are executed in parallel; rendering according to rendering task blocks to obtain rendering results; extracting and integrating the rendering results and returning the integrated results to server nodes; actively putting forwarding task requests according to the rendering nodes, reasonably distributing the task blocks generated after task processing and splitting to all the available rendering nodes in a network, providing powerful decentralized computing resources for high-strength computing type tasks through the idle states of the rendering nodes so that data processing efficiency is higher. By the active requests and a distribution matching mechanism, the distribution of the computing tasks is more reasonable, the autonomous rendering nodes withoutdifference is further realized, and the invention can be widely applied to the technical field of distributed computing networks.
Owner:GUANGZHOU JIUDI DIGITAL TECH CO LTD
Method and apparatus for creating and managing user configurable objects and functions on distributed ledger networks
PendingUS20220188810A1Effective interactionReduce the amount requiredCryptography processingProtocol authorisationEvent triggerNetwork on
To achieve no code or low code parity in decentralized computing systems, disclosed implementations provide a data structure and trusted control plane that enables the creation and operation of composable objects, that is objects whose functions and properties are derived from configurable and upgradable templates. The templates are data structures that define the behavior of a collection of objects, the behaviors being the interfaces, functions, properties, events, triggers, error messages, and dependencies that define and object and its interaction with other objects and entities. Templates are configured by mapping the desired object behaviors to registered smart contract logic that affects the behaviors. Thus, complex objects can be composed without the need for new computer code. Additional logic to enable new behaviors can be added by authorized smart contract developers and, once certified, added to one or more templates to provide the objects access to the new capabilities.
Owner:SECURRENCY INC
Programmable real-time computing and network load awareness method for decentralized computing network
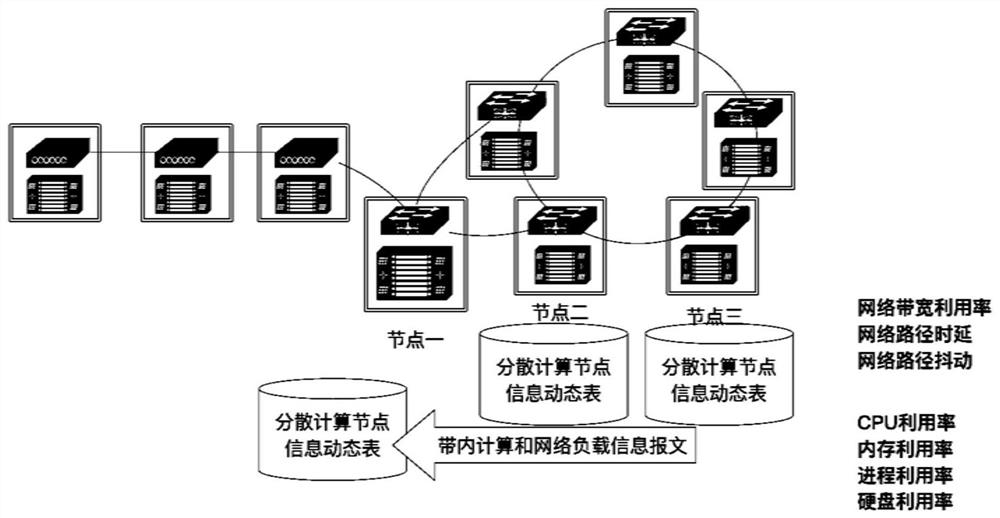
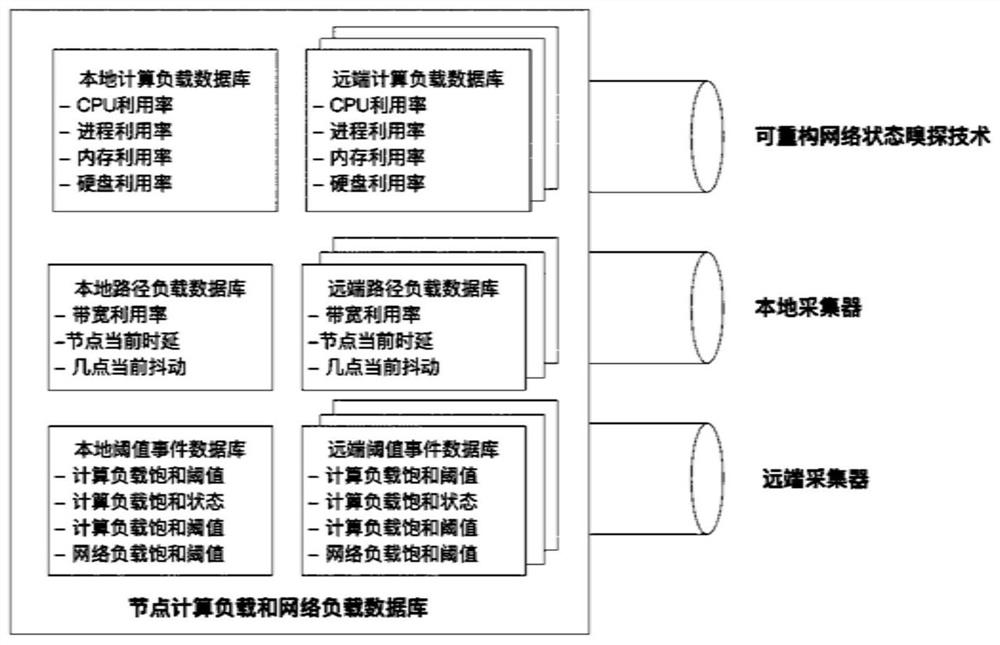
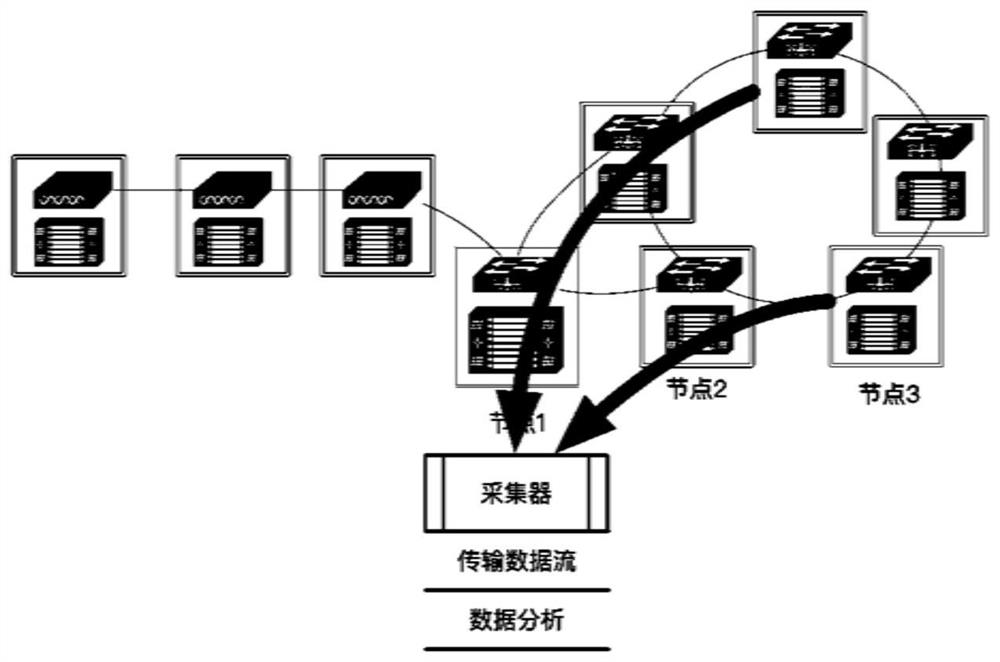
ActiveCN111726410ASatisfy fine-grained flow function requirementsSatisfy traffic functional requirementsTransmissionPathPingInternet traffic
The invention discloses a programmable real-time computing and network load sensing method for a distributed computing network, which comprises the following steps of: (1) realizing the computing of anode, the network load and the state collection in a switch chip through a single-node load and state sniffing technology; synchronizing the information to other decentralized computing nodes throughthe reconstructed protocol message; (2) realizing load and state information collection of each node in a network flow transmission process in the switch chip through an end-to-end load and state sniffing technology, carrying the information in the network flow in a stack manner, and collecting the path information at a tail node; and (3) setting a flow acquisition point through calculation, network state acquisition and threshold calculation, thereby realizing analysis of all flows in the monitored network. According to the invention, the real-time load, time delay and jitter perception of the network is realized, and the capability requirements of a decentralized computing network on programmable perception and programmable scheduling are met.
Owner:中科边缘智慧信息科技(苏州)有限公司
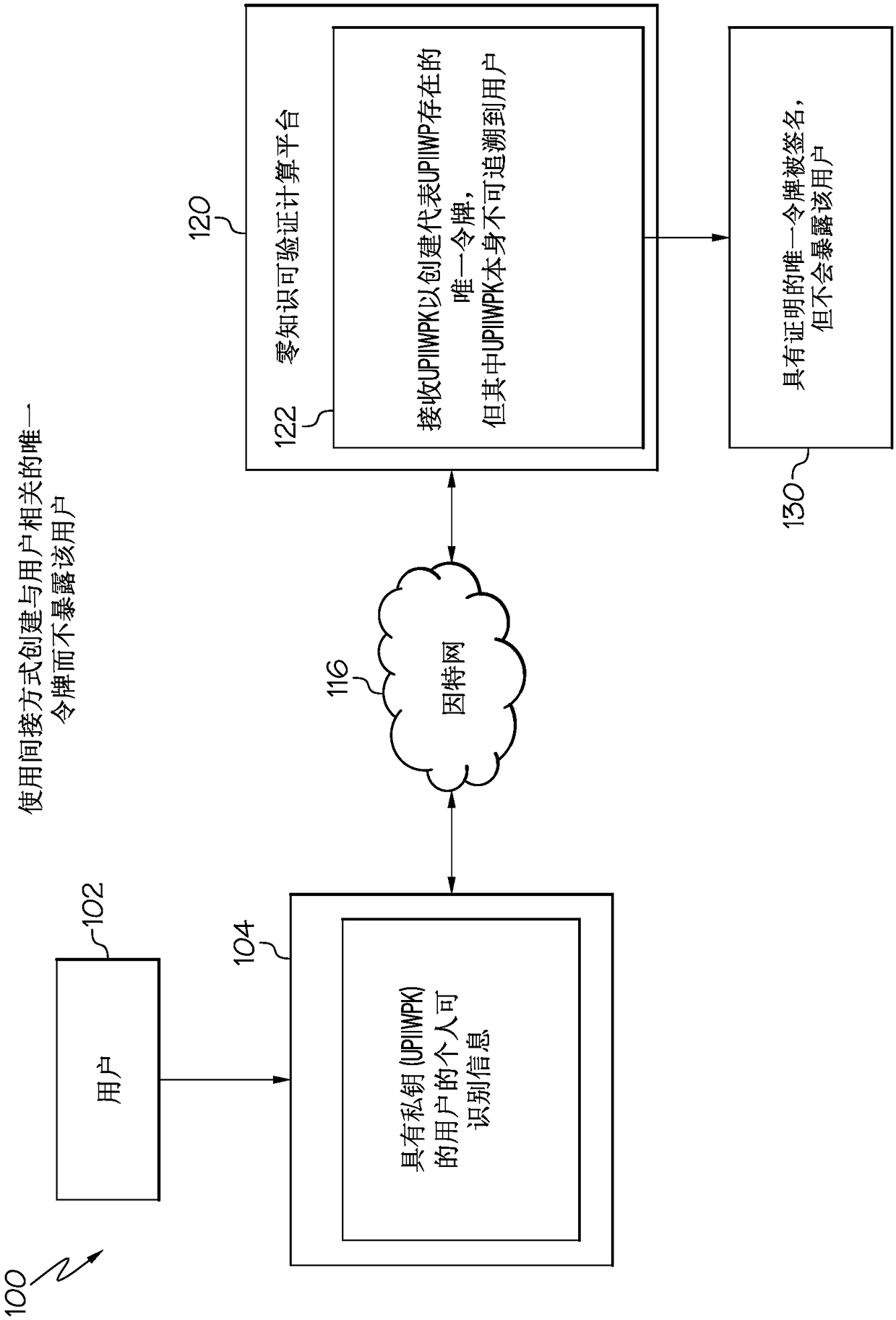
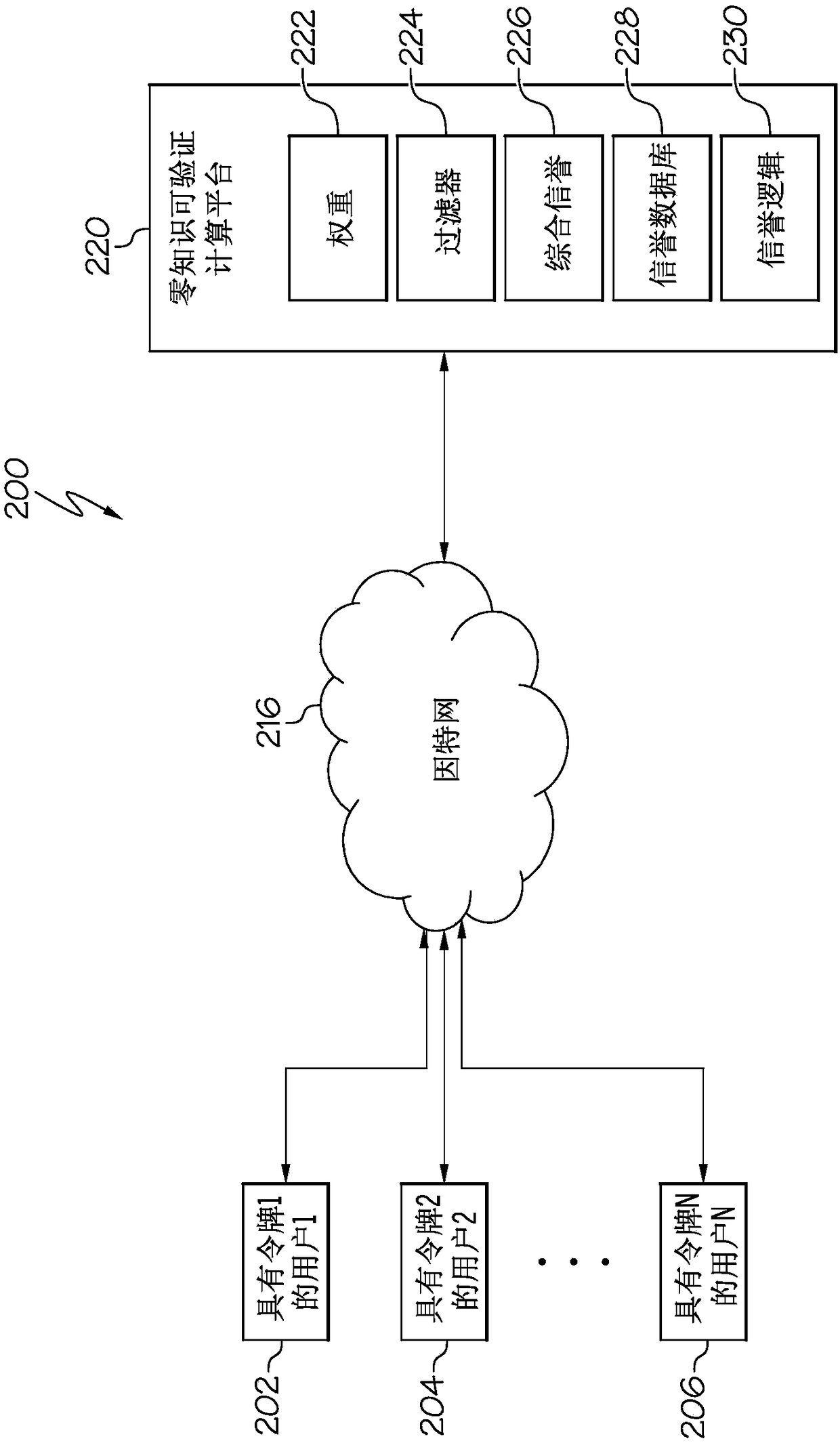
Zero knowledge third party guarantee of service on decentralized computing platform
The disclosure relates to zero knowledge third party guarantee of service on a decentralized computing platform. A service running on a server, for example as a cloud server, provides services with aguarantee from a guarantor. The service includes receiving, from a user using a zero-knowledge protocol to ensure privacy of the user, a request for a service with an associated quality level for a fee. Next, the request for service received requires a guarantee of the service requiring additional assurances based on a rating quantity available by a guarantor of the service is identified. At leasta portion of the rating quantity available by the guarantor of the service is received. A notification from the user that the service is unacceptable is received. In response to the notification anda verification that the associated quality level was not met, at least a portion of the fee is refunded to the user from the guarantor of the service.
Owner:IBM CORP
Decentralized computation system architecture based on node specialization
ActiveUS11139956B2Improve throughputImprove network throughputEncryption apparatus with shift registers/memoriesCryptography processingComputer networkDecentralized computing
Described are systems, methods, and media for providing secure and scalable decentralized computation for one or more decentralized applications. Features include a blockchain; and a plurality of nodes comprising a plurality of each of three specialized node types, the specialized node types comprising access nodes, security nodes, and execution nodes.
Owner:DAPPER LABS INC
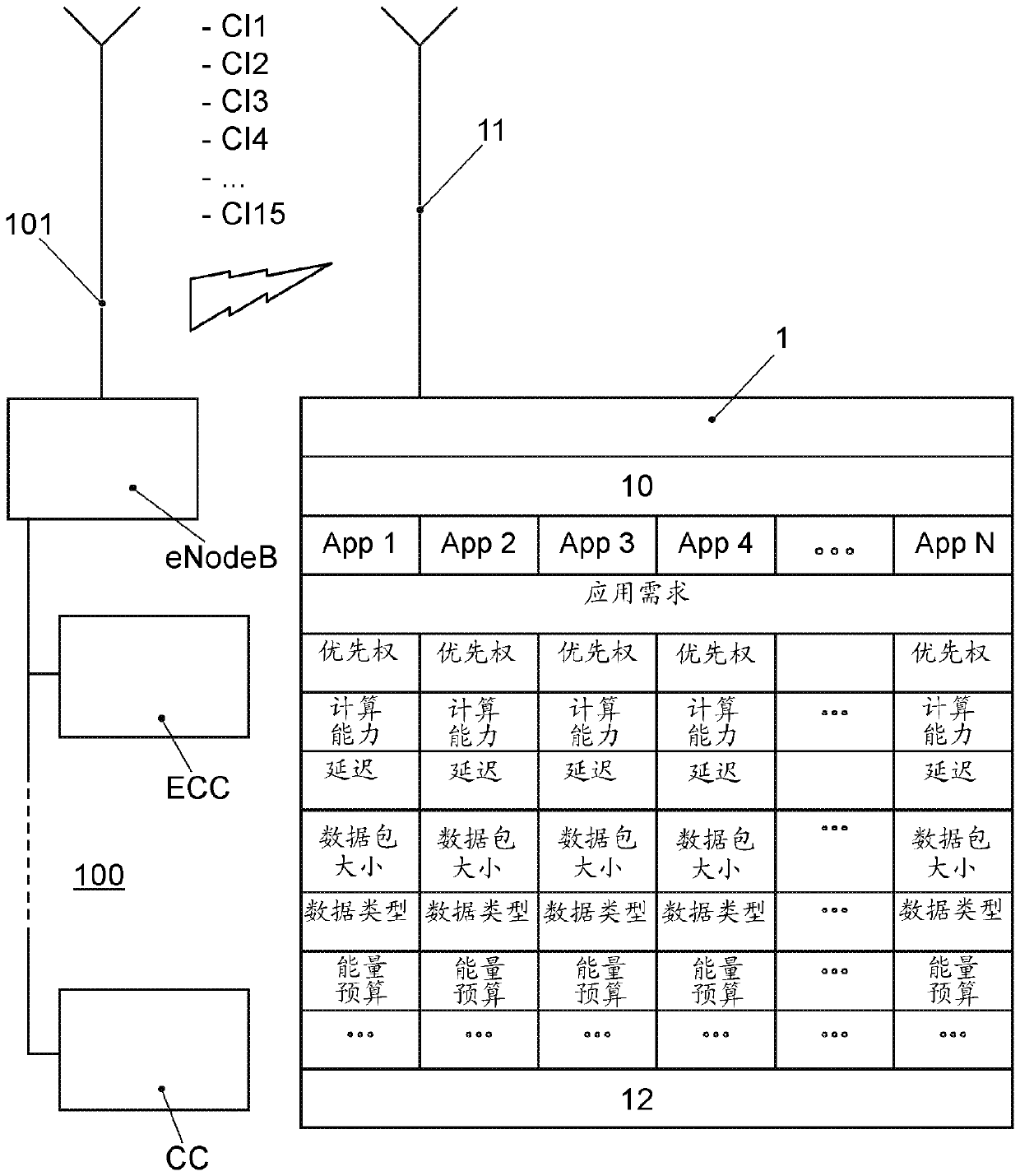
Method for operating a decentralized computing network, in particular an edge-cloud computer of the decentralized computer network
PendingCN111356107AValid choiceFast and effective selectionNetwork traffic/resource managementParticular environment based servicesResource informationTerminal equipment
The invention describes a method for operating an edge cloud computer (ECC) when providing computing power to at least one terminal device, in particular a vehicle (1), the method comprises the following steps: 1) detecting resource information (CI) at an edge cloud computer (ECC), 2) sending the resource information (CI) to at least one terminal device, and 3) providing at least one part of the computing capacity of the edge cloud computer (ECC) to the at least one terminal device according to the resource information (CI).
Owner:VOLKSWAGEN AG
System and method for toll transactions utilizing a distributed ledger
ActiveUS10699493B2Ticket-issuing apparatusEncryption apparatus with shift registers/memoriesComputer networkTransaction data
The present disclosure relates to implementing an electronic toll data collection management system in a decentralized computing network that employs a distributed ledger. An electronic toll data collection management system may comprise a plurality of nodes, wherein the plurality of nodes are connected to each other over a communication network. Each node may have access to a copy of a distributed ledger, wherein the plurality of nodes is configured to utilize blockchain protocols to verify and record a transaction occurring within the distributed ledger. Data may be recorded as a block, wherein a blockchain is formed by the addition of blocks. Each block may be encrypted and linked to a previous block, wherein a consensus must be reached to update the distributed ledger with the addition of a new block.
Owner:HAUSMAN PROPERTIES LLC
Decentralized computation system architecture based on node specialization
InactiveUS20210336769A1Improve throughputImprove network throughputEncryption apparatus with shift registers/memoriesCryptography processingComputer networkDecentralized computing
Described are systems, methods, and media for providing secure and scalable decentralized computation for one or more decentralized applications. Features include a blockchain; and a plurality of nodes comprising a plurality of each of three specialized node types, the specialized node types comprising access nodes, security nodes, and execution nodes.
Owner:DAPPER LABS INC
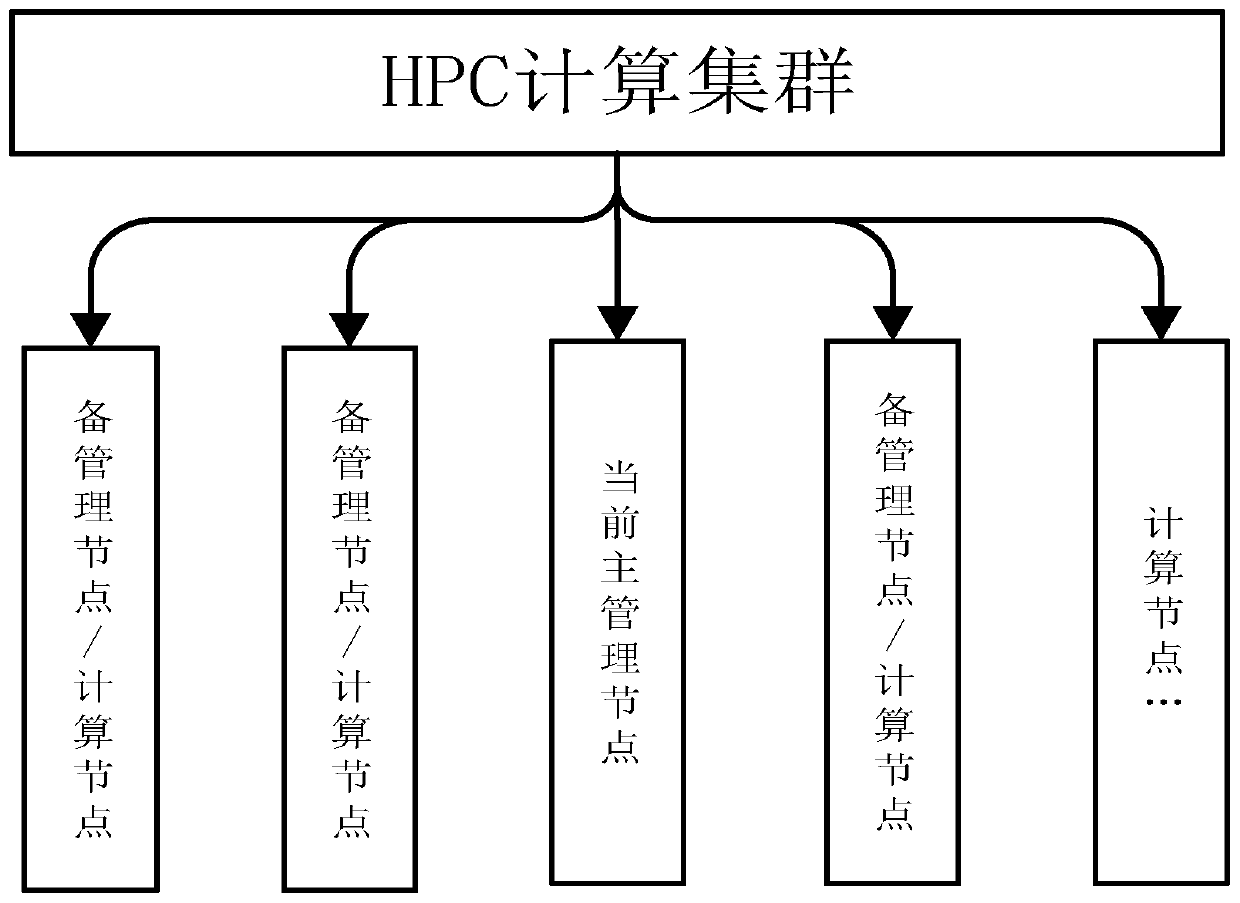
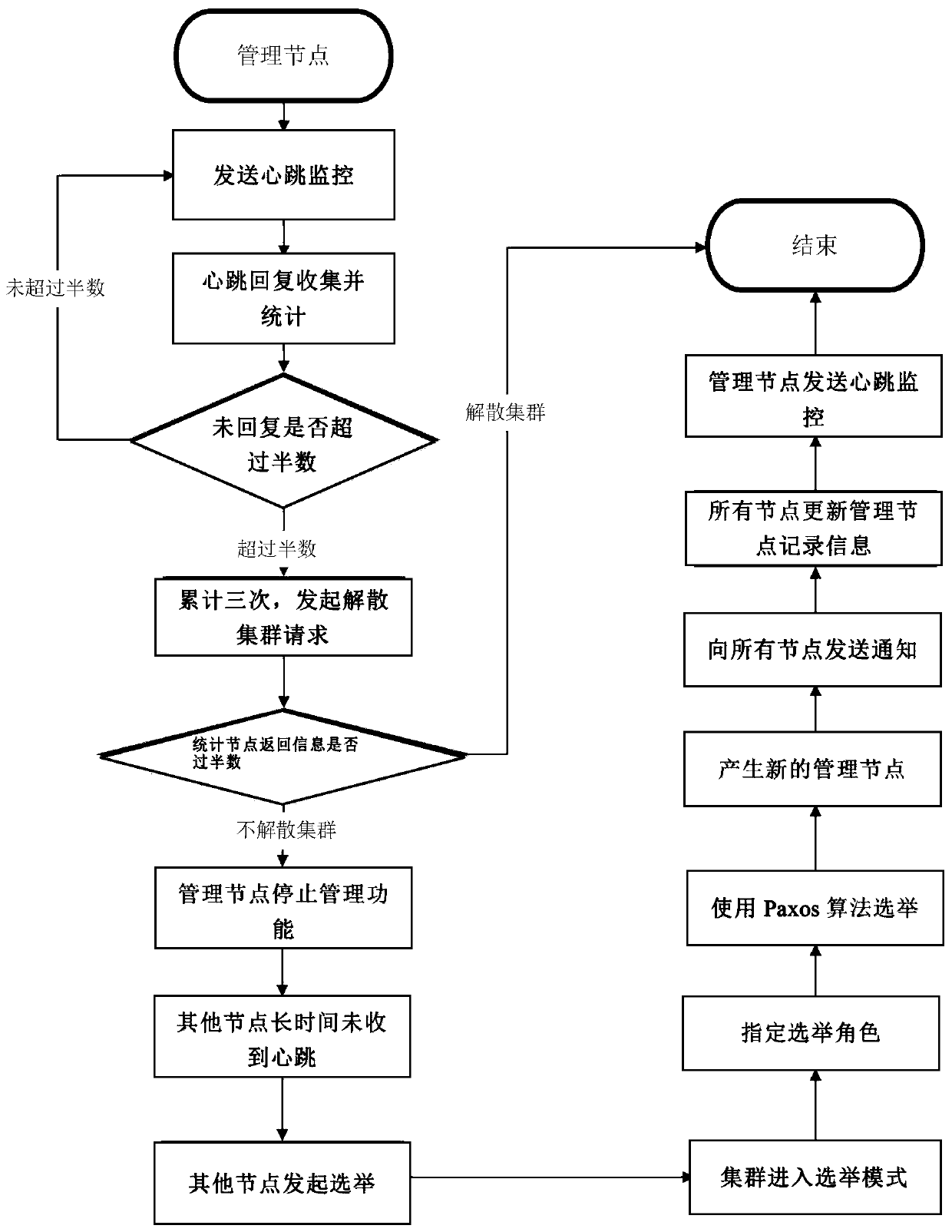
Decentralized HPC computing cluster management method and system based on paxos algorithm
ActiveCN111200518AImprove usabilityImprove fault toleranceData switching networksThird partyOperation scheduling
The invention discloses a decentralized HPC computing cluster management method and system based on a paxos algorithm. The method comprises the steps of deploying a main management node and a plurality of standby management nodes, and setting a cluster management election mechanism, wherein the cluster management election mechanism comprises the steps that a reply of heartbeat connection sent by amain management node exceeds a preset value, and a standby management node carries out election according to the paxos algorithm to generate a new main management node; and enabling the original mainmanagement node to be offline, and enabling the new main management node to perform heartbeat monitoring on the remaining standby management nodes. According to the invention, the HPC high-performance job scheduling cluster can be optimized from a single-master centralized cluster mode to a decentralized cluster mode; the change of the mode enables the availability of the cluster to be greatly improved; limit of a single-point fault of the single-master cluster centralization mode is avoided; the fault-tolerant capability of the cluster is improved by several orders of magnitudes; the faultis more suitable for an actual scene; automatic high availability is provided for the cluster; and high availability is completed without a third-party tool.
Owner:DAWNING INFORMATION IND BEIJING +1
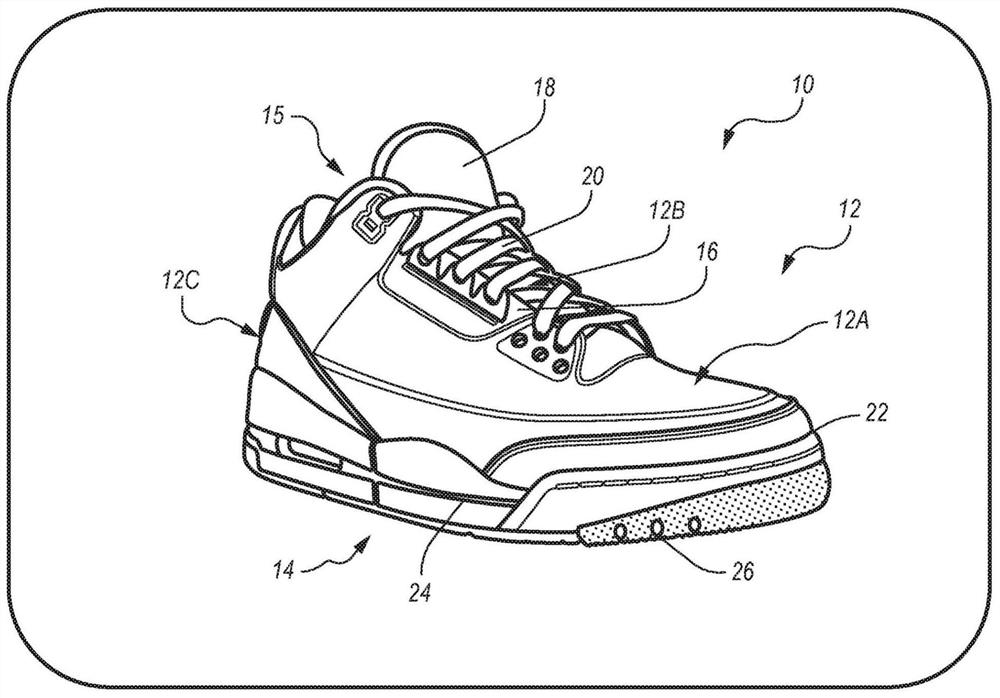
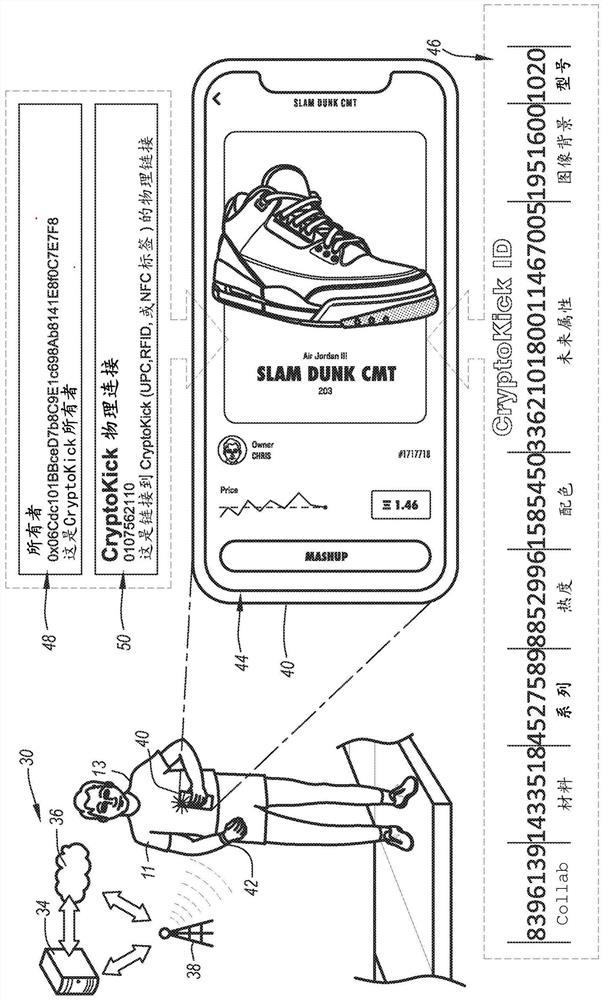
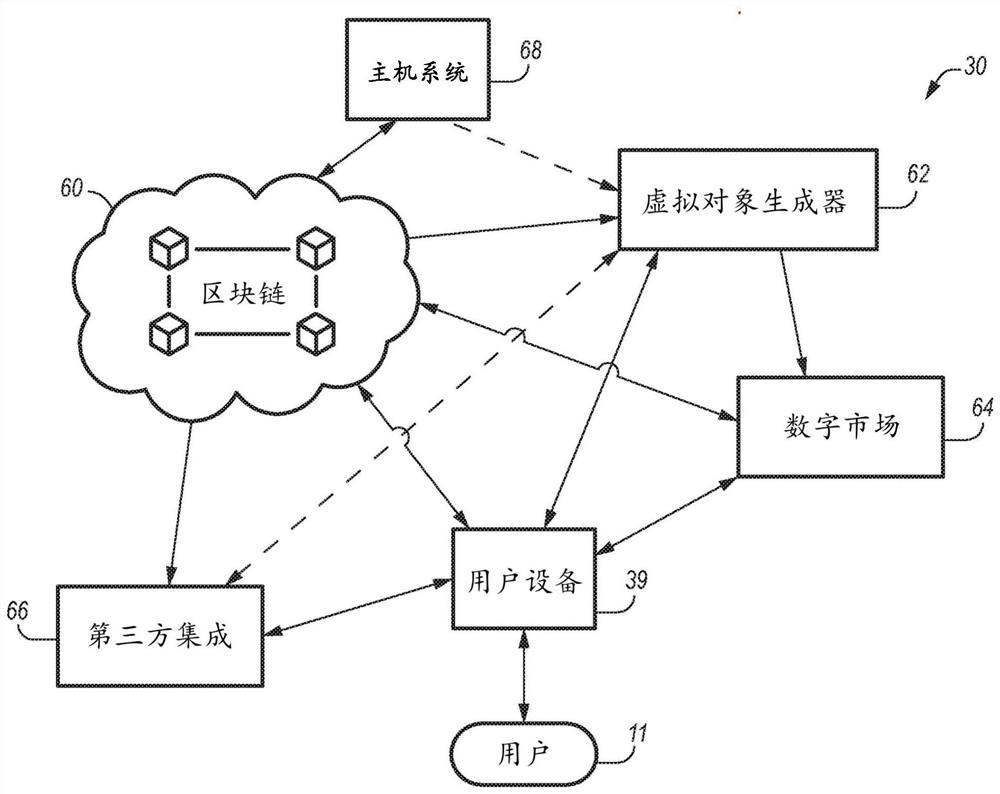
System and method for providing cryptographically secured digital assets
PendingCN113396388AKey distribution for secure communicationRandom number generatorsComputer networkEngineering
Presented are cryptographic digital assets for articles of footwear, methods for making / using such cryptographic digital assets, and decentralized computing systems with blockchain control logic for mining, intermingling, and exchanging blockchain-enabled digital shoes. A method of provisioning the digital assets includes receiving a transaction confirmation indicative of a completed transaction of an article of footwear or a digital file representative thereof from a first party to a second party, and transmitting a cryptographic block to a distributed blockchain ledger to record transfer of the cryptographic digital asset to the second party.
Owner:NIKE INNOVATE CV
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com