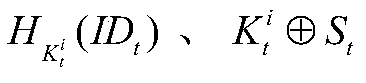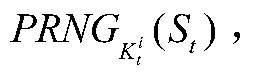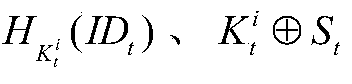Mobile RFID mutual authentication method based on dynamic shared secret key
A technology of shared key and authentication method, which is applied in the field of radio frequency identification, can solve the problems of security attacks, dynamic shared key cannot be safely updated, and cannot completely prevent desynchronization attacks, etc., achieves good label efficiency and performance, and realizes random dynamic Effect of Security Updates
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0024] Symbol Description
[0025] Table 1 Symbol description
[0026]
[0027] The present invention will be described in further detail below in conjunction with the accompanying drawings.
[0028]Initialization stage: When the system is initialized, four data tables are set up in the background database to store the shared key and identification information of the tag and the reader and the background database. The tag's current information table Tag_c_au stores the tag ID, the current shared key, and the hash code of the tag ID with the current key as a parameter; the tag's history information table Tag_h_au stores the tag ID, the tag history shared key, and the tag ID with the history The shared key is the Hash code of the parameter; the reader identity and the current key are stored in the reader current information table Reader_c_au; the reader identity and the historical key are stored in the reader history information table Reader_h_au. Each tag stores the shared...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com