Smart card password authentication and password modification method
An authentication method and password modification technology, applied in electrical components, transmission systems, etc., can solve the problems of battery exhaustion of security tokens, slow encryption speed of block ciphers, difficulty in resisting dictionary attacks, etc., to prevent replay attacks and information Effects of intercepting attacks, reducing stress, mitigating risks
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0047] In order to make the object, technical solution and advantages of the present invention clearer, the present invention will be further described in detail below in conjunction with the accompanying drawings and embodiments. It should be understood that the specific embodiments described here are only used to explain the present invention, not to limit the present invention.
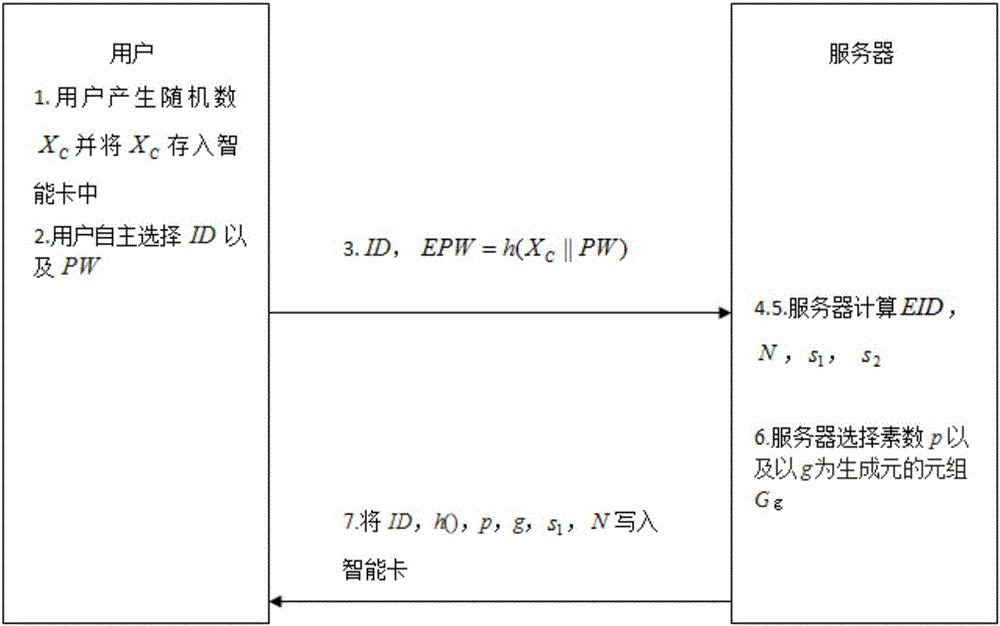
[0048] Step one, the registration stage. At this stage, the registered user needs to apply for a smart card first, which stores various information of the user, such as date of birth, home address, mobile phone number and personal signature.
[0049] (1) In the initial stage of user registration, the user first randomly generates a random number X C and put X C Confidentially stored in the smart card. In order to ensure the security of the system, X C It should be greater than 1024bit.
[0050] (2) The user freely chooses his user name (ID) and password (PW).
[0051] (3) In order to protect ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com