Computer network access control system and method
A technology of control system and control method, which is applied to computer components, computing, transmission systems, etc., can solve problems such as system loopholes, being impersonated or replaced, and unsatisfactory effects, and achieve high security effects
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
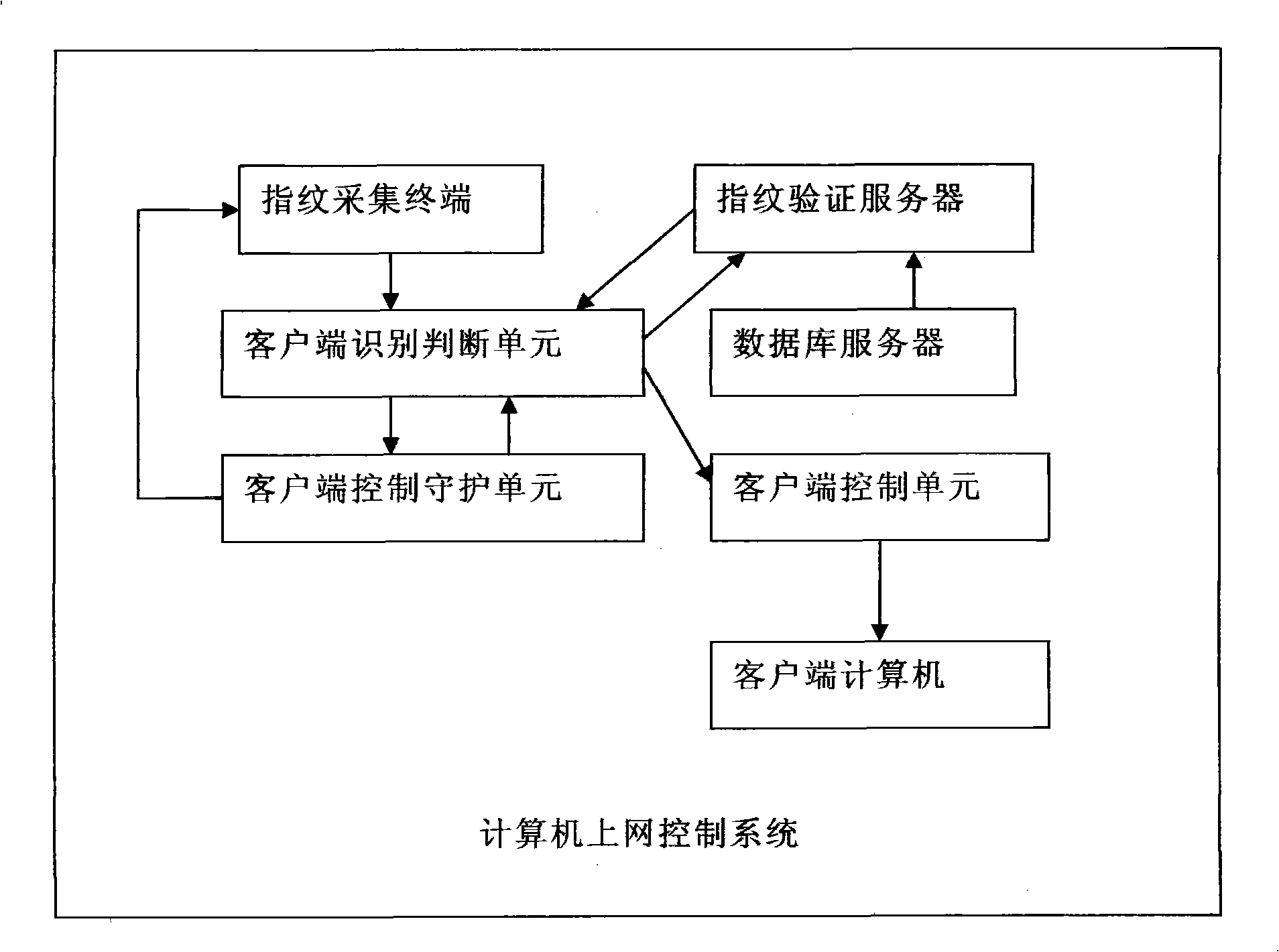
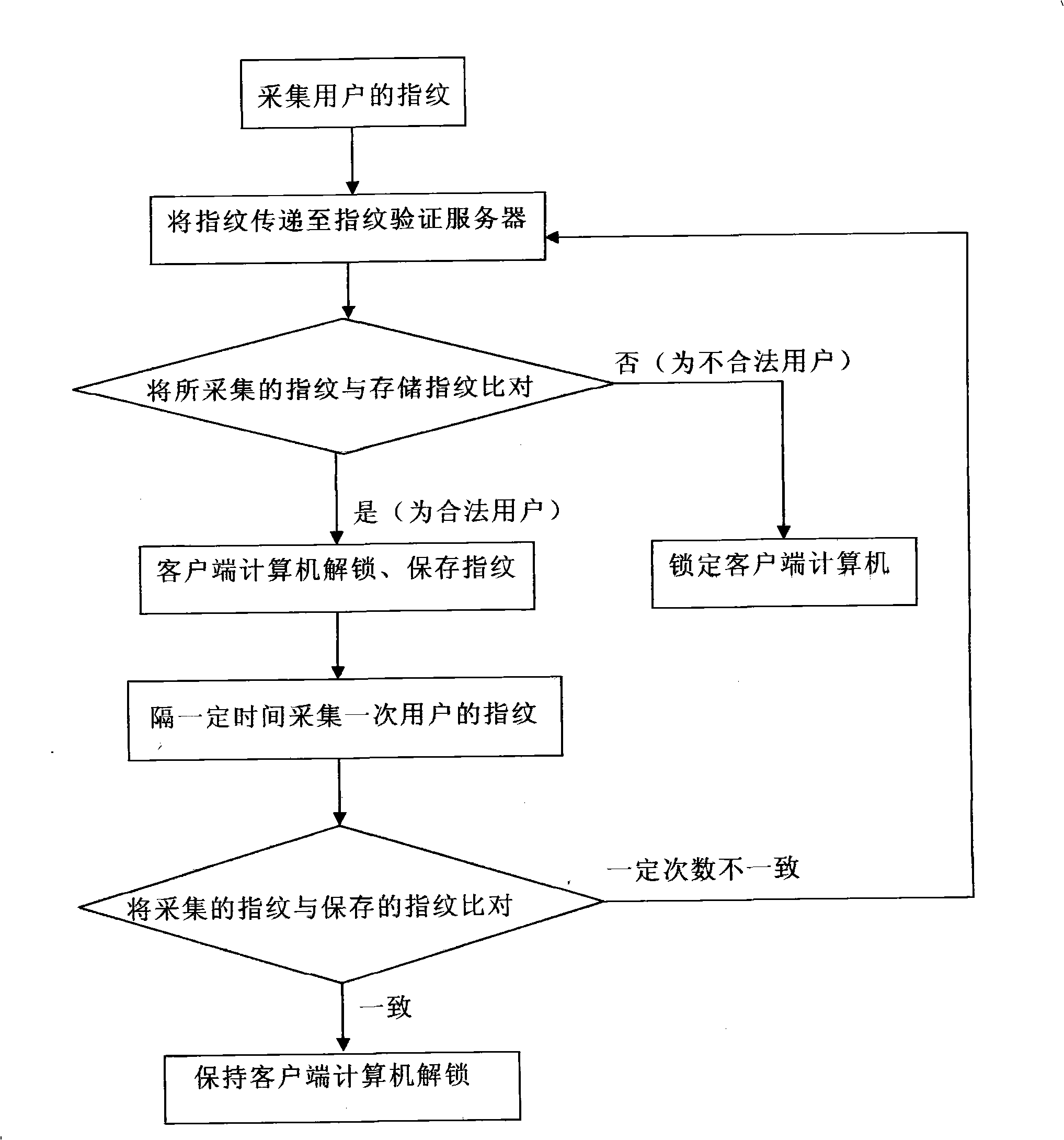
[0036] The present invention starts with the mouse and keyboard that must be used by surfers, adopts the fingerprint mouse and the fingerprint keyboard, uses the current high-tech fingerprint identification technology, and identifies whether the system user or the surfer is an illegal user through the identification of the pre-established fingerprint database. And monitor and identify in real time during the user's use to prevent other people from replacing the operation, and perform real-time monitoring and management on the operation of each client on the server side to ensure that each client device can operate normally and prevent malicious blocking and Uninstall to ensure the normal operation of the entire system.
[0037] Such as figure 1 As shown in , the present invention discloses a computer access control system, which includes a fingerprint collection terminal for collecting the user's fingerprint. This fingerprint collection terminal can be any known and public fin...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com