Method and network node for obtaining a permanent identity for authenticating a wireless device
A technology for wireless devices and network nodes, applied in the field of permanent device identity, which can solve problems such as trouble
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
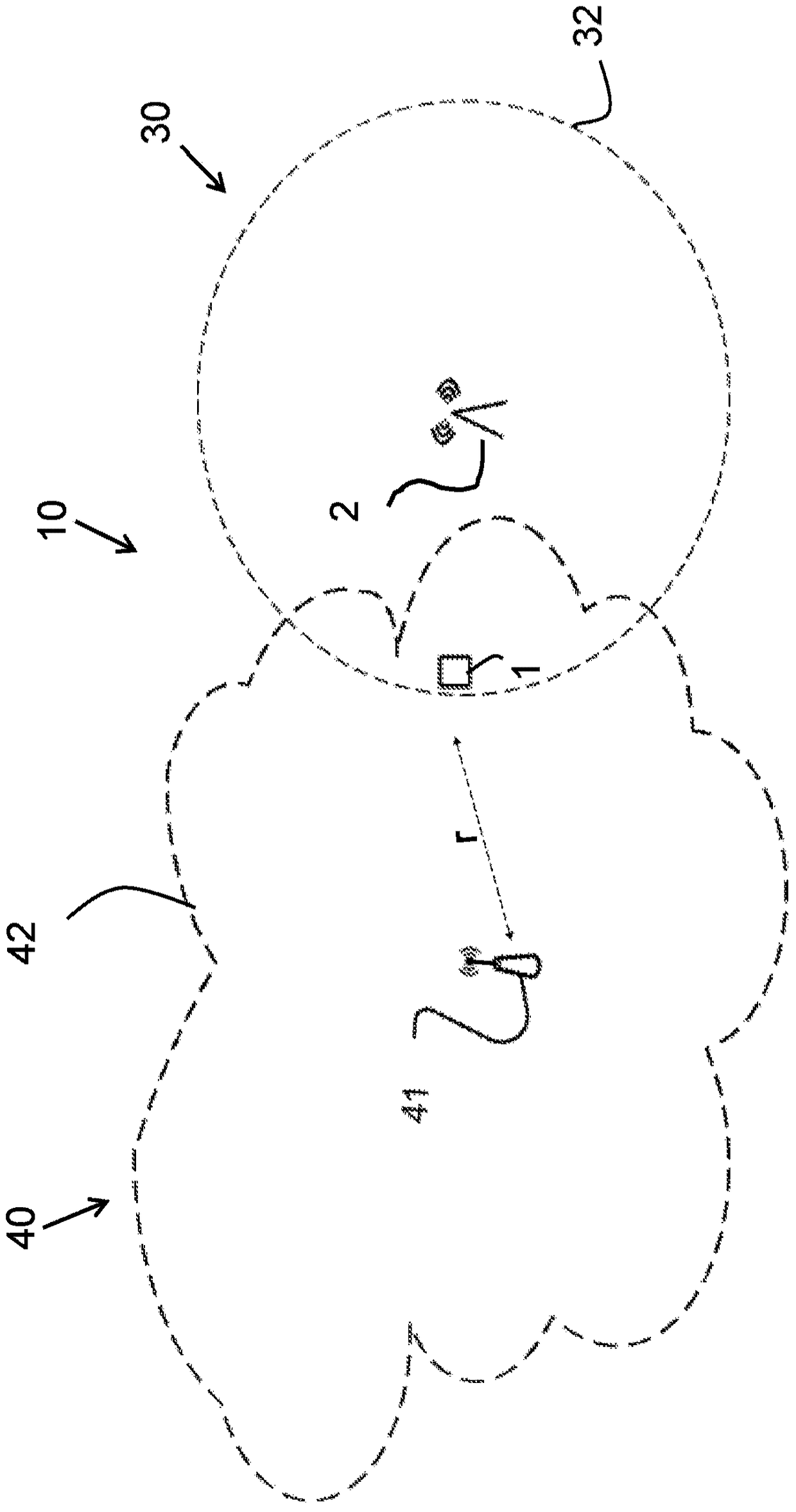
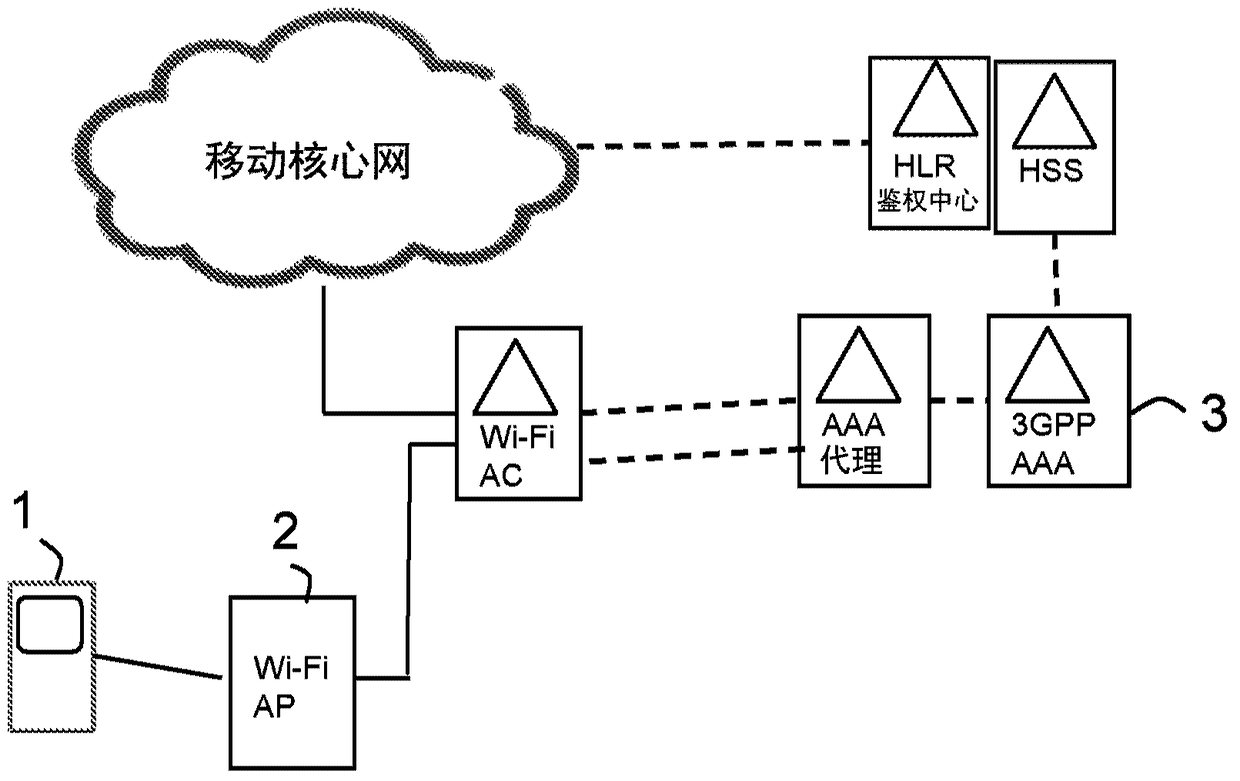
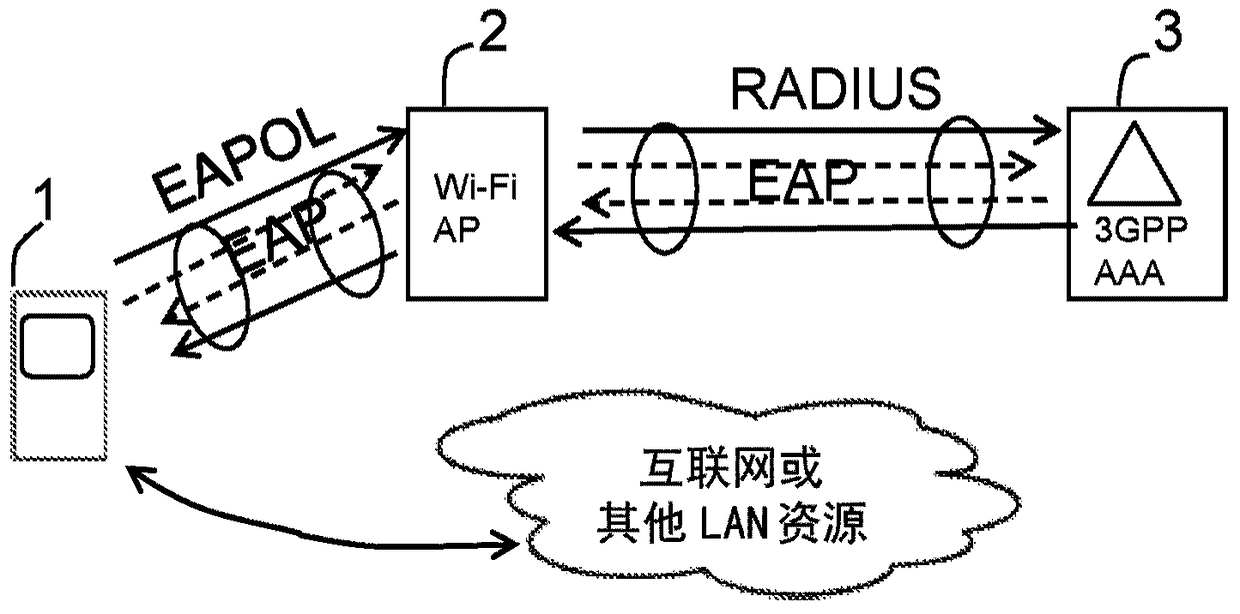
[0035] Hereinafter, embodiments of the present invention will be described in more detail with reference to the accompanying drawings. For purposes of explanation and not limitation, specific details are disclosed, such as of specific scenarios and techniques, to provide a thorough understanding.
[0036] The various steps described below in connection with the figures should be understood primarily in a logical sense, while each step may include the communication of one or more specific messages depending on the implementation and protocol used. Embodiments to which this disclosure relates generally relate to the field of EAP authentication using EAP-SIM, EAP-AKA or EAP-AKA' authentication frameworks. However, it must be understood that the same principle can be applied in other authentication frameworks with similar signaling flows. In this disclosure, the term wireless device is used generally. A wireless device or user equipment UE as the term is used in 3GPP specificati...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com