Method and device for detecting abnormal flow, and method and device for defending against Web attack
A technology of abnormal traffic and detection method, which is applied in the field of network security, can solve the problems of inability to protect the network, 0day loophole defense lag, etc., and achieve the effect of overcoming the lag of defense
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
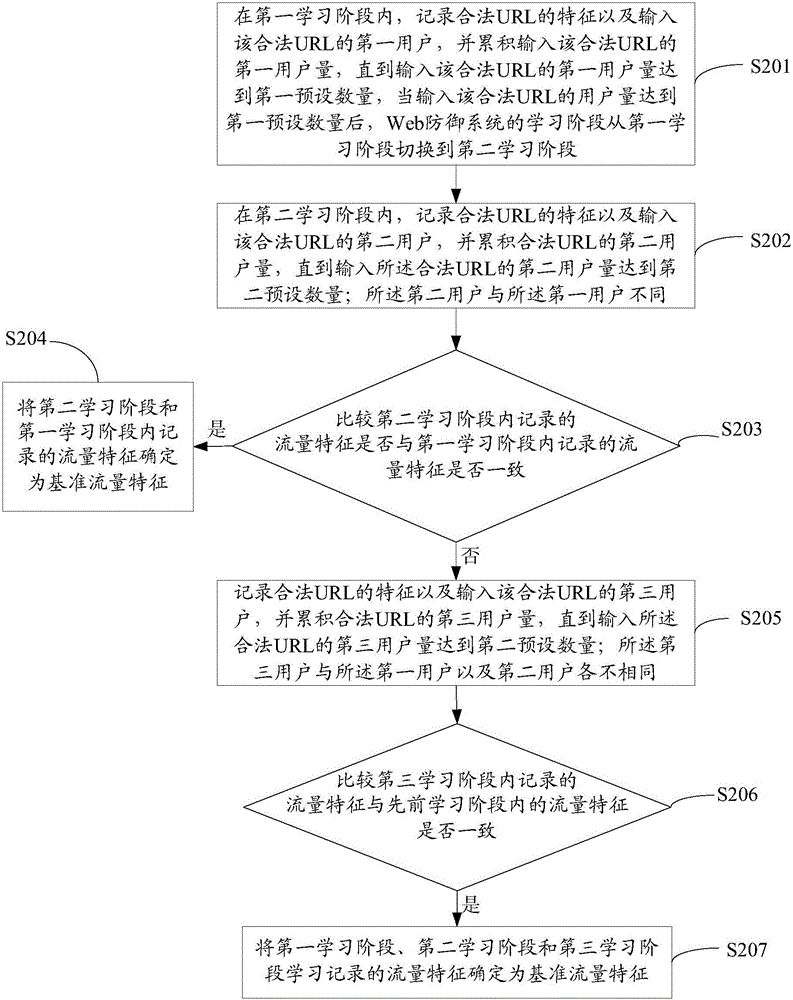
[0059] figure 1 It is a schematic flowchart of the method for detecting abnormal traffic provided in Embodiment 1 of the present invention. like figure 1 As shown, the method includes the following steps:
[0060] S101. Obtain the benchmark traffic characteristics of the website:
[0061] It should be noted that the reference traffic characteristics described in the embodiment of the present invention are URL characteristics constructed according to legal URLs of websites. How to determine whether a URL is legitimate? In this embodiment of the present invention, whether the URL is legal can be determined by checking the response of the URL. For example, when the response of the URL is "HTTP 200 OK", it indicates that the URL is legal and correct; when the response of the URL is "HTTP 404 Not Found", it indicates that the URL does not exist or is a broken URL. Links or citations are not legal.
[0062] In the embodiment of the present invention, any one of the following t...
Embodiment 2
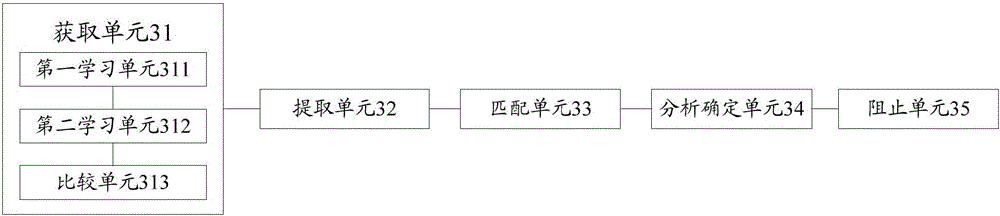
[0137] Figure 4 is a schematic flowchart of the method for defending against Web attacks provided by Embodiment 2 of the present invention. like Figure 4 As shown, the method includes the following steps:
[0138] S401. Detect whether the received traffic is abnormal traffic;
[0139] According to step S101 to step S104 in the method for detecting abnormal traffic according to the first embodiment, it is detected whether the received traffic is abnormal traffic.
[0140] S402. When the received traffic is abnormal traffic, track the user who generated the abnormal traffic;
[0141] When the received traffic is abnormal, track the user who generated the abnormal traffic.
[0142] S403. Determine the trust degree of the user within the preset time period according to the degree of abnormal traffic generated by the user within the current preset time period:
[0143] It should be noted that the time corresponding to the current flow input by the user is pushed forward by a...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com