Method of using cryptographic equipment by JAVASCRIPT
A cryptographic device and parameter technology, applied in digital transmission systems, electrical components, transmission systems, etc., can solve problems such as process crashes, hidden safety hazards, and complicated use, and achieve the effects of enhancing stability, ensuring security, and reducing complexity
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
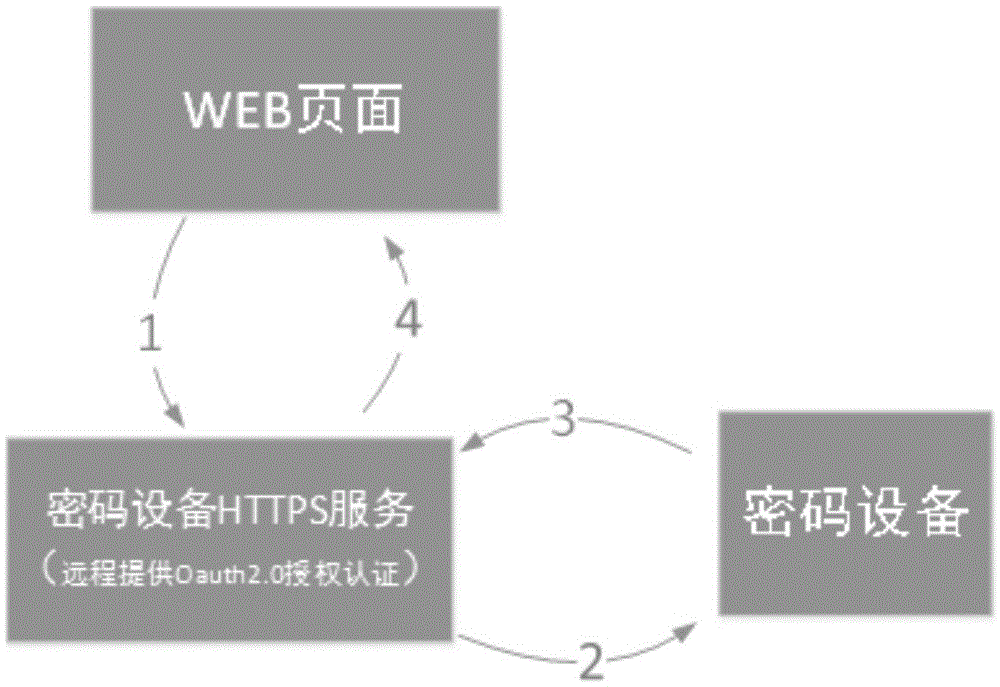
[0045]1、部署一台密码设备HTTPS服务器,用来处理密码设备请求。该服务器与密码设备对接,通过密码设备的应用接口访问密码设备。
[0046]2、WEB应用后台配置密码设备HTTPS服务的地址和端口。WEB应用页面通过密码设备HTTPS服务的地址和端口访问部署在远程的密码设备。
[0047]3、WEB应用页面在需要进行密码设备操作的时候调用密码设备HTTPS服务的授权认证,终端用户在密码设备HTTPS服务的授权认证页面上输入用户名和密码。认证通过后WEB应用获得一个授权的令牌。
[0048]4、WEB应用页面脚本通过的SRC属性调用调用密码设备HTTPS服务,并传入授权的令牌。先传入缓存数据,例如加密操作,先将加密原文分成1500字节长度多个数据段,将数据段BASE64防止特殊字符。然后循环发送,每次发送的示例代码如下:
[0049]varhead=document.getElementsByTagName('head')[0];
[0050]varscript=document.createElement('script');
[0051]script.type='text / javascript';
[0052]script.onload=script.onreadystatechange=function(){
[0053]if(!this.readyState||this.readyState==="loaded"||this.readyState==="complete"){
[0054]script.onload=script.onreadystatechange=null;
[0055]}};
[0056]script.src='https: / / 密码设备HTTPS服务地址:端口 / CryptService?callback=onCallBack&method=cache&guid=340282366920938463463374607431768211456&total=120&sn=1&len=1500&expired=10m&data=……&token=64a0623103634c71a94cd8ef1e3581f5';
[0057]head.appendChild(script);
[0058]}
[0059]其中method为cache标识本次调用为数据缓存。gui...
Embodiment 2
[0089]1、在终端用户的计算机上部署密码设备HTTPS服务,服务地址为127.0.0.1,端口为空闲端口:9818。这个密码设备HTTPS服务访问接入到终端计算机上密码设备,如智能卡钥匙等。
[0090]2、WEB应用后台配置密码设备HTTPS服务的地址和端口。WEB应用页面通过密码设备HTTPS服务的地址和端口访问接入终端计算机的密码设备。
[0091]3、WEB应用页面脚本通过的SRC属性调用调用密码设备HTTPS服务,并传入授权的令牌。先传入缓存数据,例如加密操作,先将加密原文分成1500字节长度多个数据段,将数据段BASE64防止特殊字符。然后循环发送,每次发送的示例代码如下:
[0092]varhead=document.getElementsByTagName('head')[0];
[0093]varscript=document.createElement('script');
[0094]script.type='text / javascript';
[0095]script.onload=script.onreadystatechange=function(){
[0096]if(!this.readyState||this.readyState==="loaded"||this.readyState==="complete"){
[0097]script.onload=script.onreadystatechange=null;
[0098]}};
[0099]script.src='https: / / 密码设备HTTPS服务地址:端口 / CryptService?callback=onCallBack&method=cache&guid=340282366920938463463374607431768211456&total=120&sn=1&len=1500&expired=10m&data=……&token=64a0623103634c71a94cd8ef1e3581f5';
[0100]head.appendChild(script);
[0101]}
[0102]其中method为cache标识本次调用为数据缓存。guid为缓存数据标识,total为数据段数目,sn为数据段序号,len为数据体长度,expired为时效时间(10m表示十分钟,即收到第一段...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com