Control flow obfuscation method and system based on a callback function
A callback function and control flow technology, applied in the field of network security, can solve the problems of high running overhead and low obfuscation intensity, achieve good applicability and enhance the anti-analysis ability.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0026] In order to make the purpose, technical solution and advantages of the present invention more clear and understandable, the present invention will be further described in detail below in conjunction with the accompanying drawings and technical solutions.
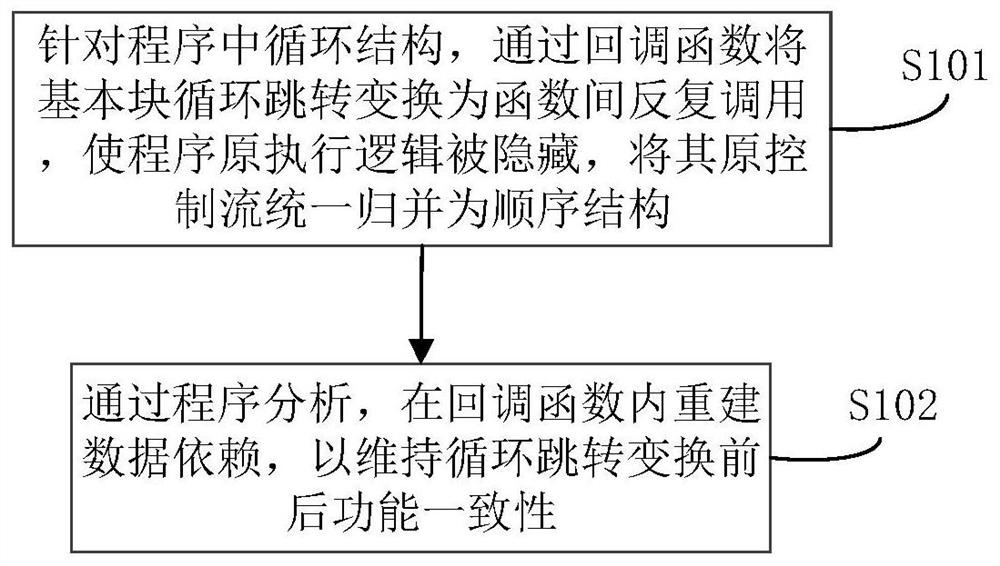
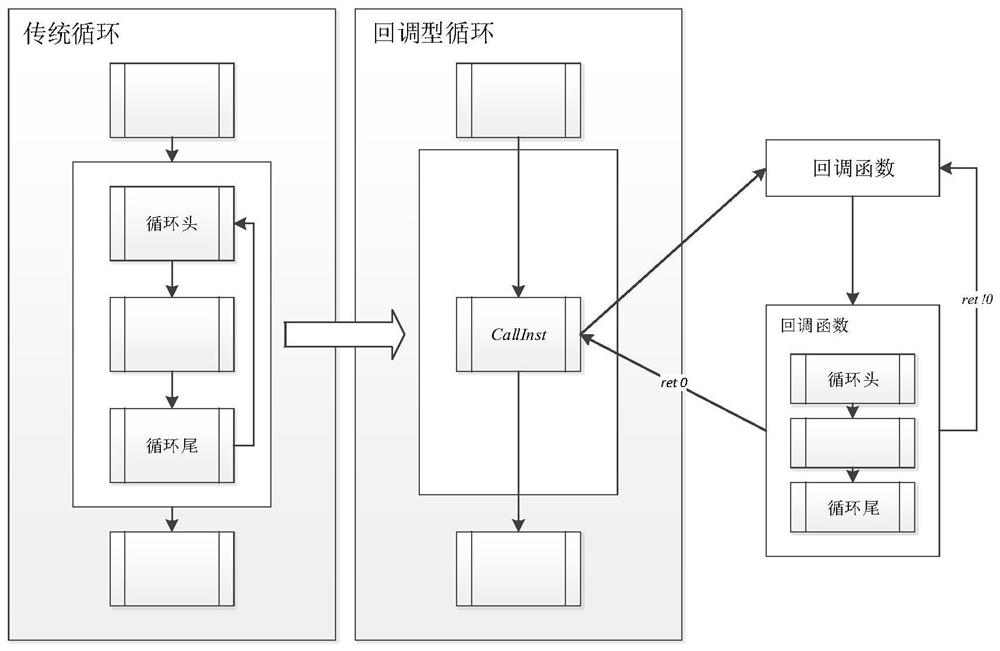
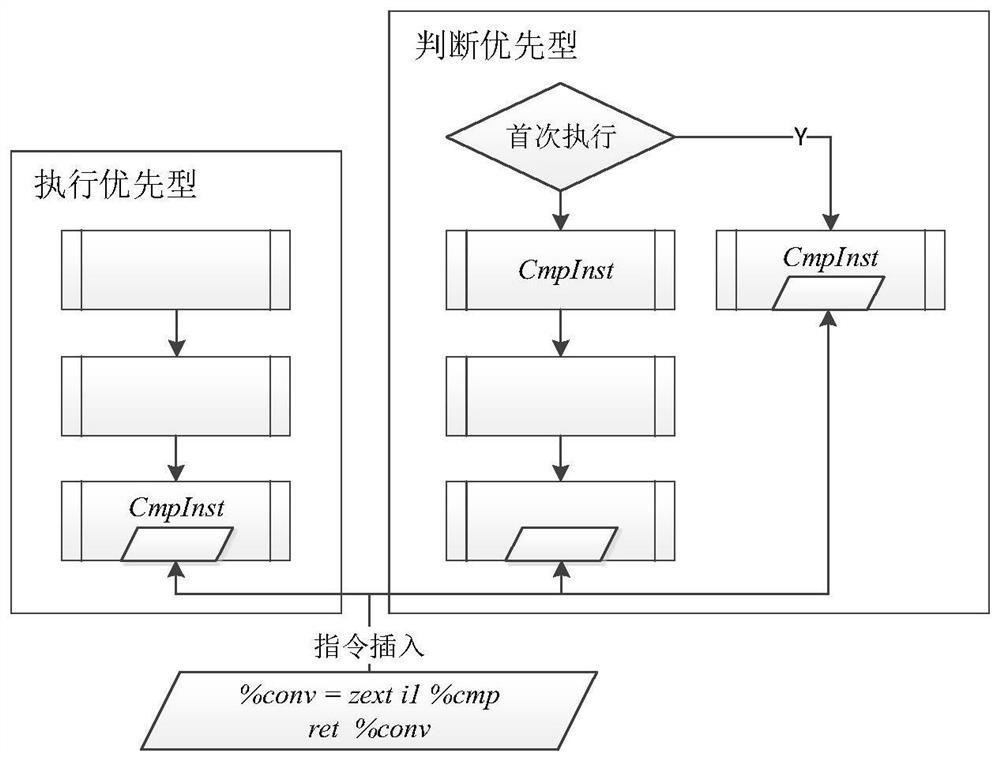
[0027] Traditional obfuscation methods mainly increase program complexity by adding code redundancy and resist reverse analysis. The confusion intensity of this method depends on the degree of code redundancy, and it is difficult to cope with the increasingly efficient automatic analysis technology. Moreover, the introduction of code redundancy in the program will lead to increased code size and reduced operating efficiency, which does not meet the needs of the development of the software industry. . For this reason, embodiment of the present invention, see figure 1 As shown, a control flow obfuscation method based on a callback function is provided, including the following content:
[0028] S101. For the loop struc...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com