A Mimic Routing Decision Method for Multiple Instance Routing Units
A decision-making method and multi-instance technology, applied in electrical components, digital transmission systems, transmission systems, etc., can solve problems such as severe cyberspace security requirements
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0034] Below in conjunction with accompanying drawing and specific implementation mode, the mimic routing decision-making method of multi-instance routing unit of the present invention is further explained: described method is the routing decision-making method of mimic routing switching system control plane, and its implementation is as follows:
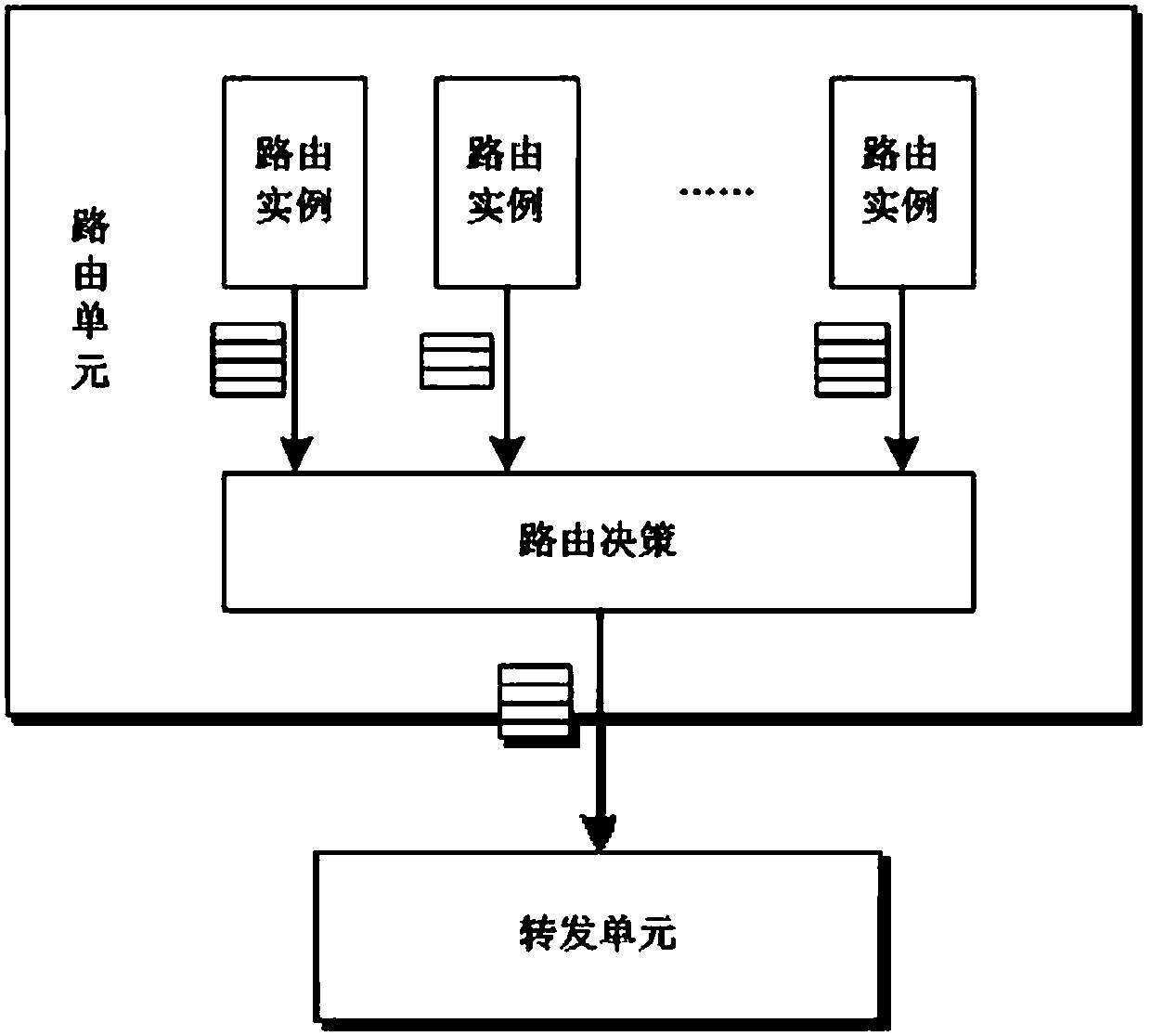
[0035] In step (1), the routing decision-making module maintains the routing table item issued by it for each routing instance; the format of the routing table item is as attached figure 2 shown.
[0036] Step (2), for each routing table item, compare it with all other routing table items maintained by the routing decision-making module, and obtain the number of routing table items that are exactly the same as the content of the routing table item, according to the same number of routing table items and the credibility of the routing instance to which it belongs to calculate the credibility of each routing entry;
[0037] Step (3)...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com