A detection method of wlan spoofing attack based on rss
A spoofing attack and detection method technology, applied in network topology, electrical components, security devices, etc., can solve the problems of spoofing attack detection effect, multiple RSS noise values, and inability to locate the physical location of the attacker, so as to improve the attack detection rate, The effect of eliminating security threats
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
no. 2 example
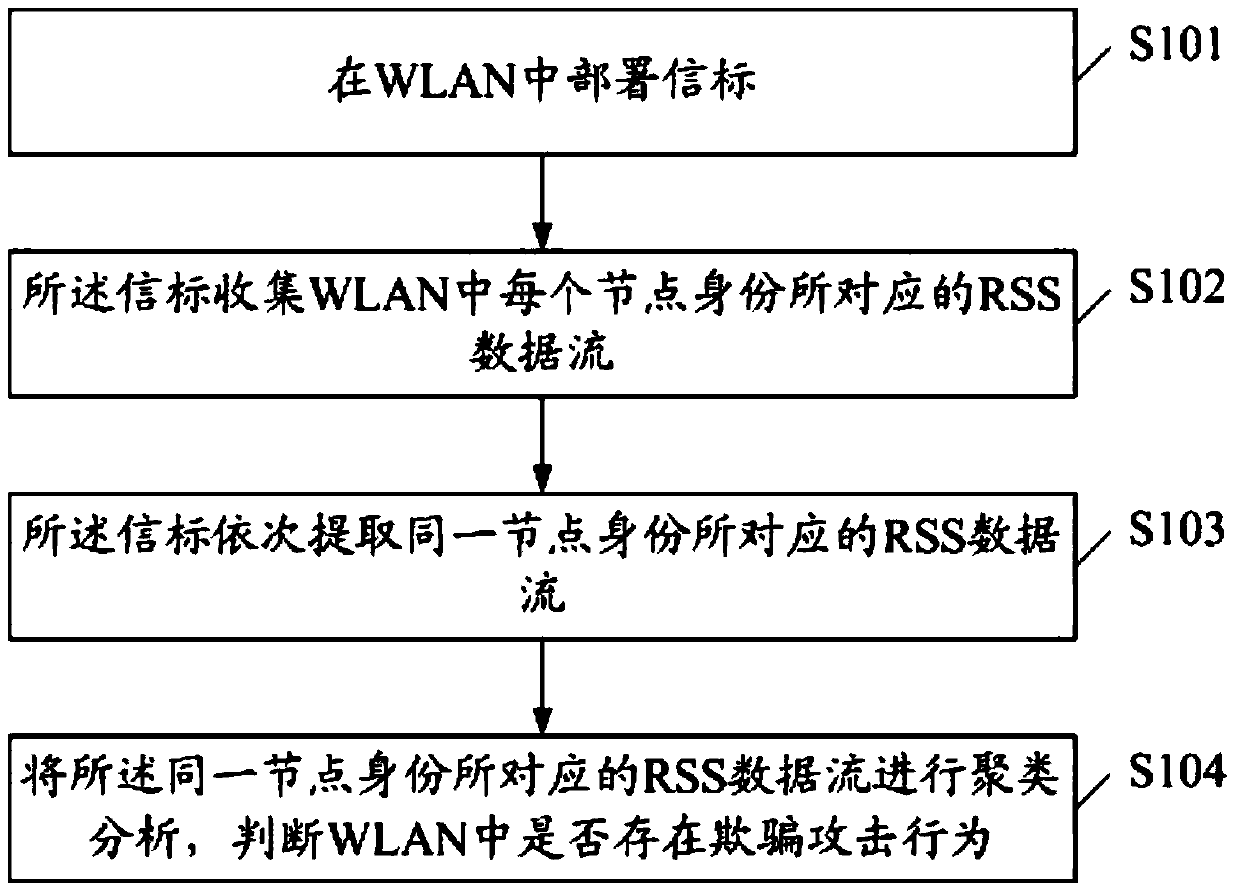
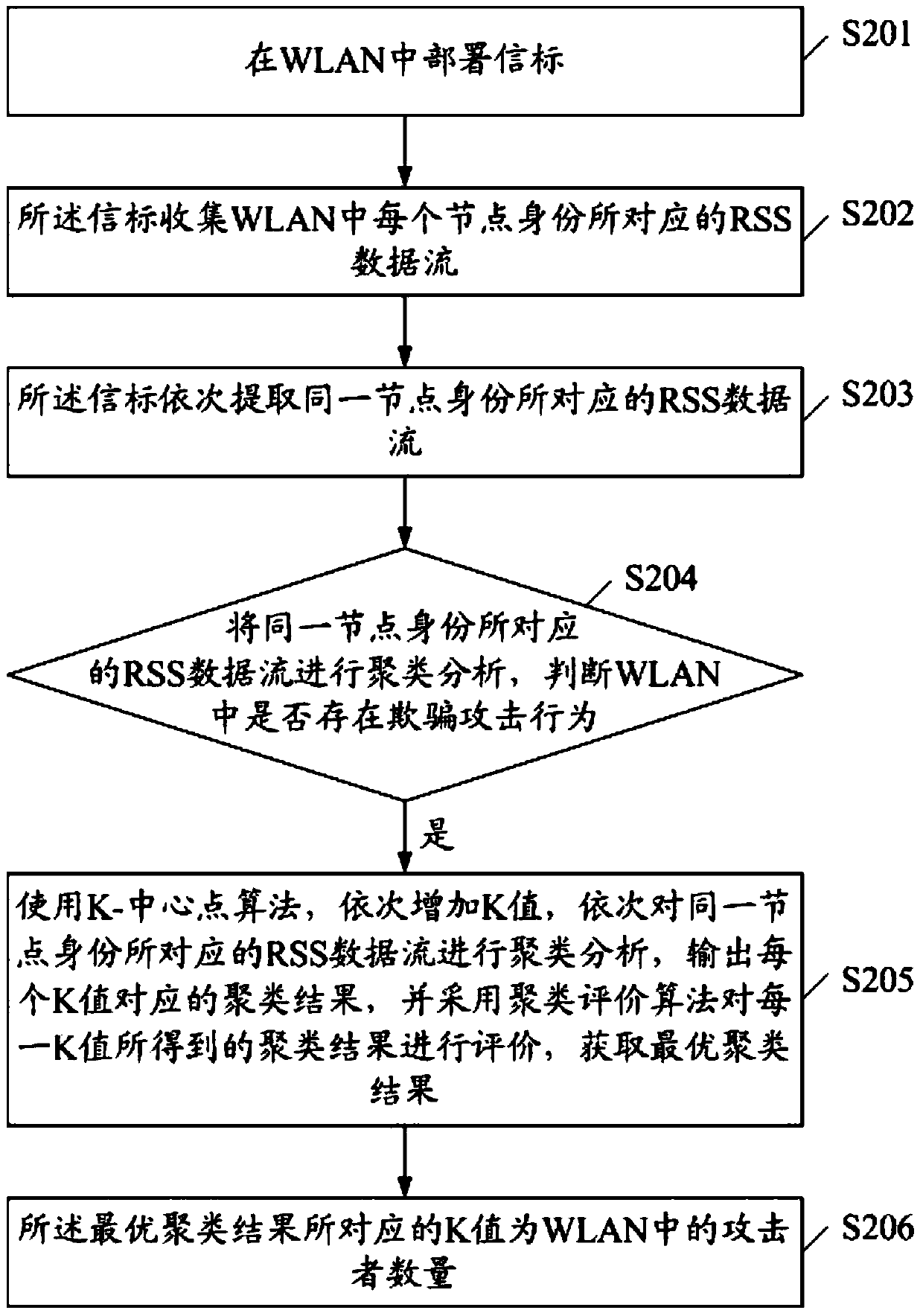
[0075] figure 2 It is a flow chart of the second embodiment of the RSS-based WLAN spoofing attack detection method of the present invention, including:
[0076] S201. Deploy a beacon in the WLAN.
[0077] S202. The beacon collects the RSS data stream corresponding to each node identity in the WLAN.
[0078] S203. The beacon sequentially extracts RSS data streams corresponding to the same node identity.
[0079] S204. Perform cluster analysis on the RSS data streams corresponding to the same node identity to determine whether there is a spoofing attack in the WLAN.
[0080] S205, when it is detected that there is a spoofing attack in the WLAN, use the K-center point algorithm to sequentially increase the K value (let K=2, 3, ...), and sequentially cluster the RSS data streams corresponding to the same node identity Analyze and output the clustering results corresponding to each K value, and use the clustering evaluation algorithm to evaluate the clustering results obtained ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com