Feature screening system and method for network traffic attack detection based on learning automaton
A technology for network traffic and attack detection, applied in transmission systems, electrical components, etc., can solve problems such as high dimensionality and large amount of network traffic data, and achieve the effects of ensuring redundancy, reducing complexity, and improving effects
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
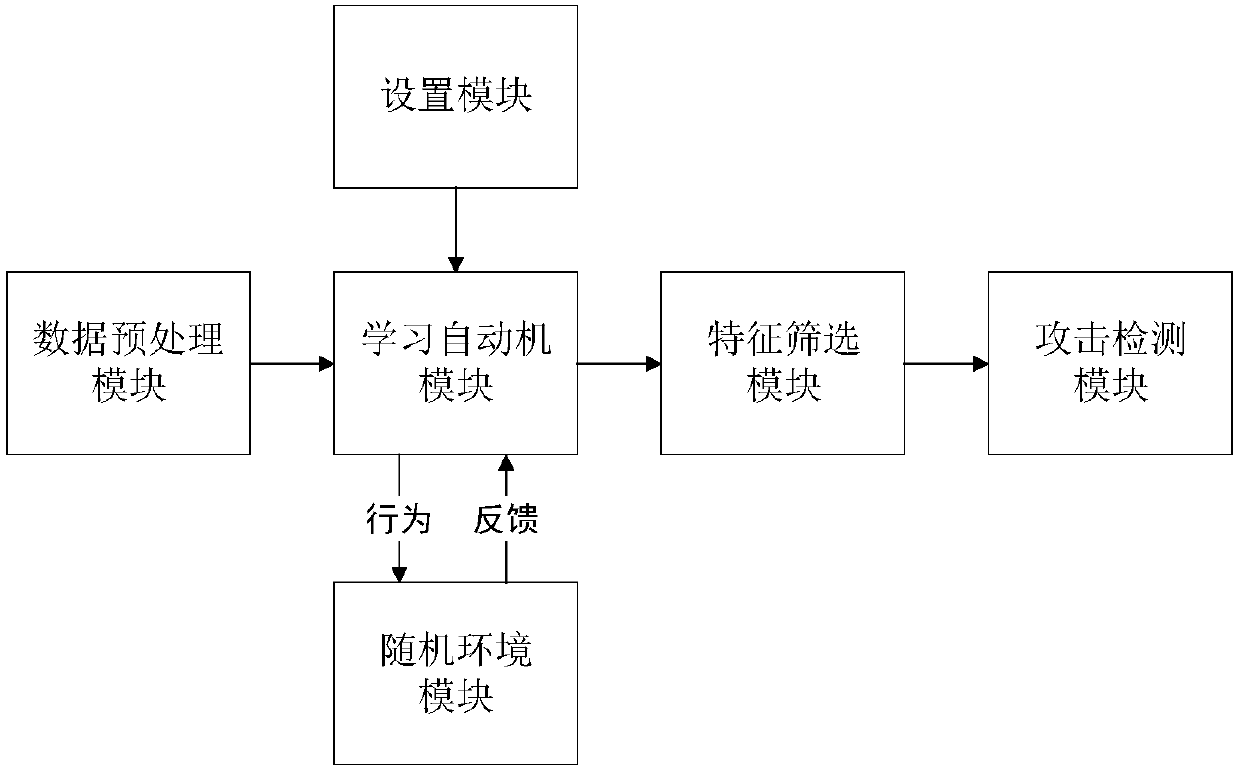
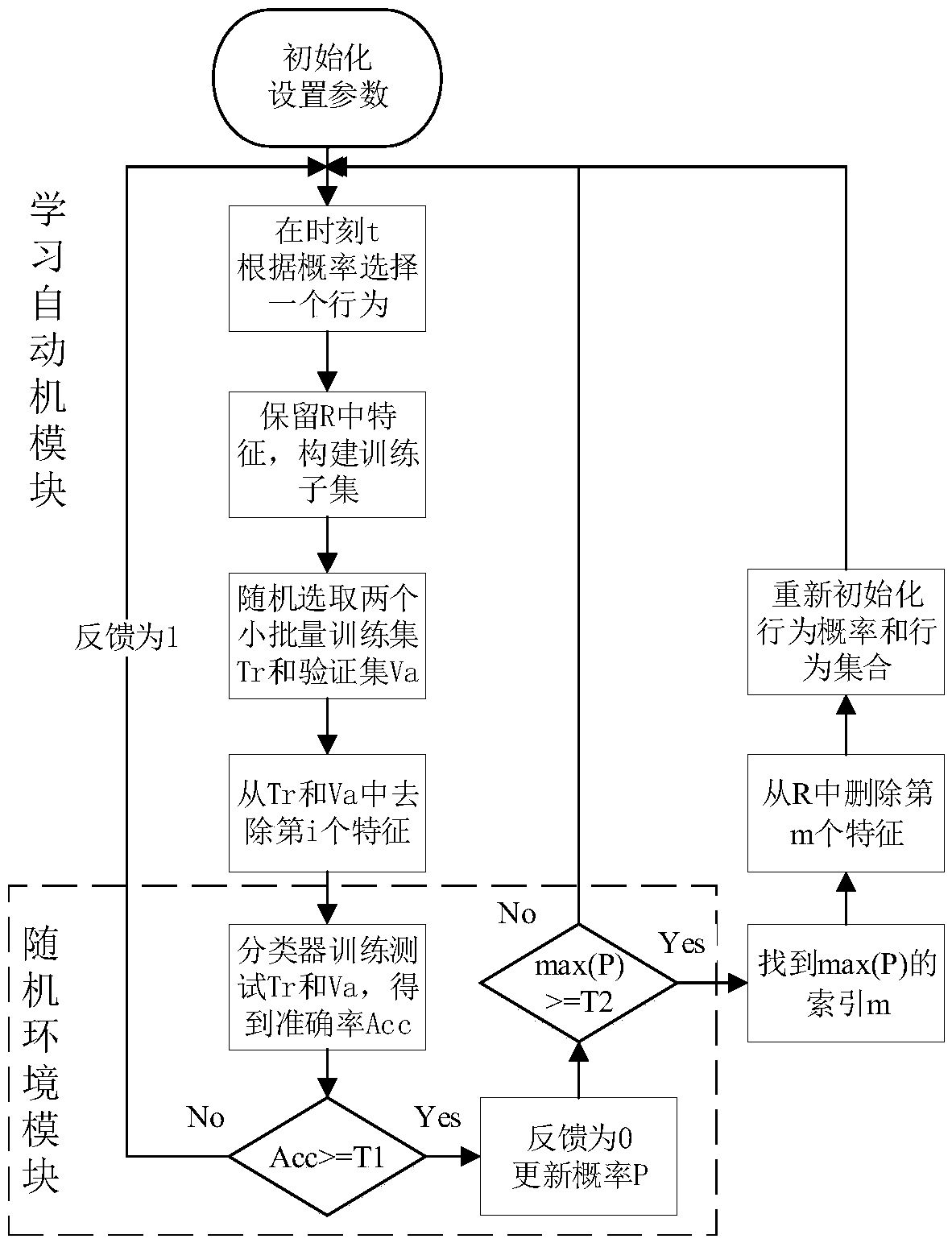
[0019] The feature screening problem can be mapped to the learning problem of automata, and the learning process of learning automata includes four main entities: learning automaton, behavior, stochastic environment and feedback. In this embodiment, all network traffic features are modeled as a whole learning automaton, feature set F={f 1 ,f 2 ,...,f n} represents the set of optional behaviors of the learning automata, and each feature is an optional behavior. A Classic Learning Automata Algorithm DL RI It is applied to the problem of selecting the optimal feature subset from the entire feature set. The random environment allows feedback to be binary, including a P-type environment with rewards and penalties. The behavior probability update strategy is the RI (Reward-Inaction) strategy. Only when the selected features reduce the overall accuracy rate will the behavior be rewarded and the selection probability of the behavior will be increased. Otherwise, no change is made ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com