Active attack detection method for improving detection rate
A technology of active attack and detection method, applied in the direction of electrical test/monitoring, test/monitoring control system, instrument, etc., to achieve the effect of improving malicious attack detection rate and attack detection rate
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0082] The specific implementation manners of the present invention will be further described in detail below in conjunction with the accompanying drawings and embodiments.
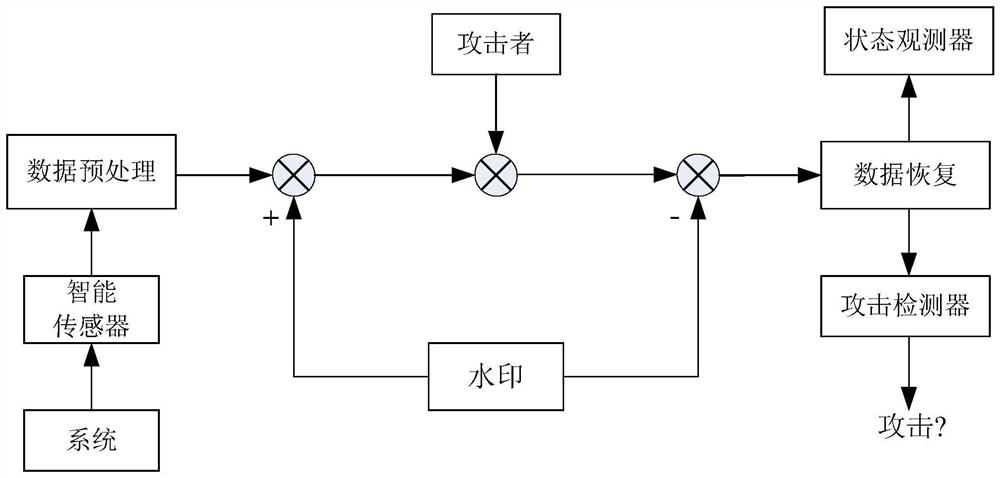
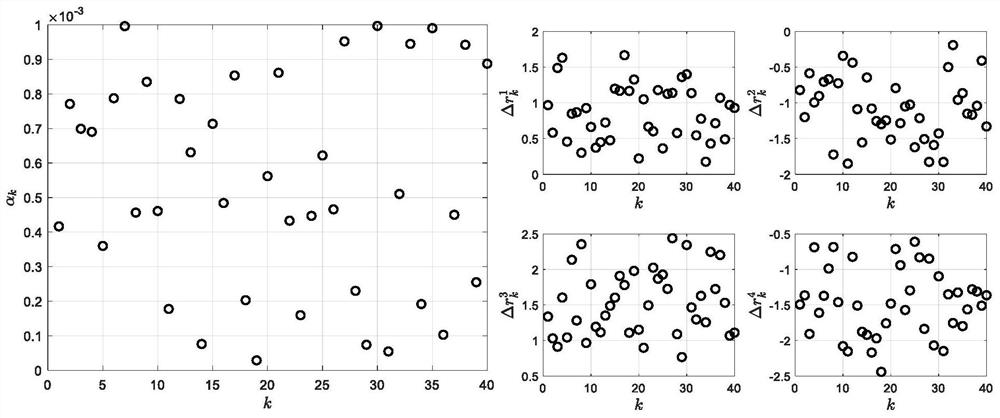
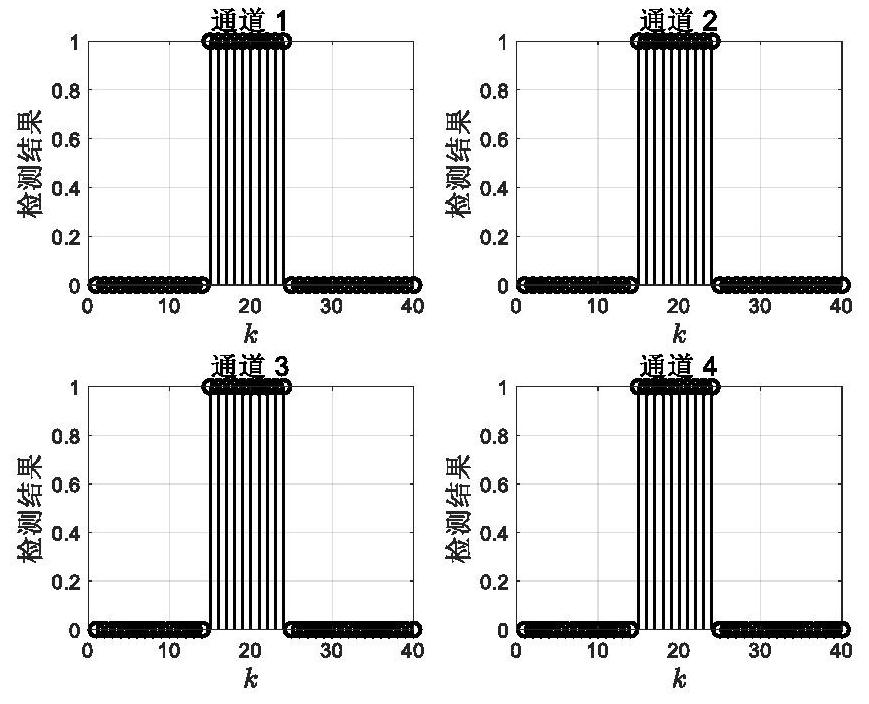
[0083] Such as figure 1 As shown, the method of the present embodiment is as follows;
[0084] Step 1: Obtain observation residual data and perform data processing;
[0085] Step 1.1: Obtain observation residual data;
[0086] Step 1.1.1: Build a linear system model with unknown but bounded noise:
[0087] A linear system model with unknown but bounded noise is as follows:
[0088] x k+1 =Ax k +ω k (1)
[0089] the y k =Cx k +v k (2)
[0090] in, is the system state, n x is the system state dimension, is the system output, n y Output dimension for the system, A and C are system matrices of dimension, and is unknown but bounded noise; the initial state of the system satisfies 0 , H 0 > means the center is p 0 , the generating matrix is H 0 The fully symmetrical polytope of a...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com