Obfuscated script processing method and device
A processing method and script technology, applied in the computer field, can solve the problems of inability to accurately detect obfuscated scripts, low attack detection rate, etc., and achieve the effect of improving the attack detection rate
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
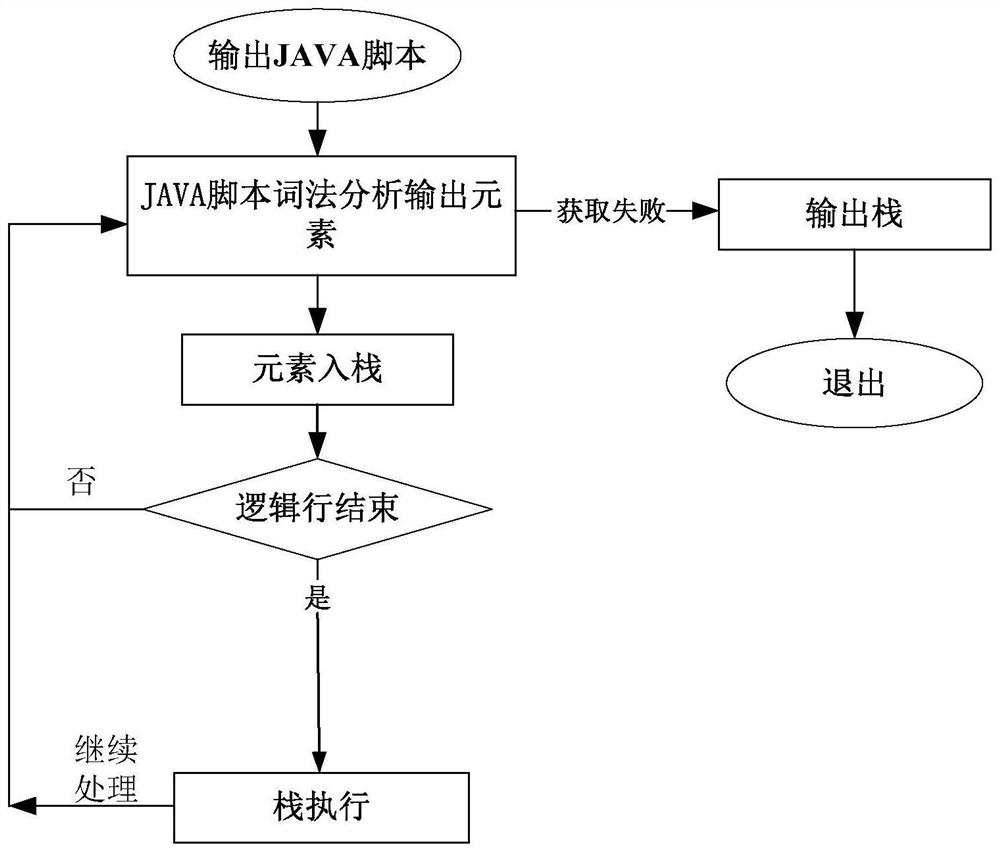
[0026] According to an embodiment of the present invention, an embodiment of a method for processing obfuscated scripts is provided. It should be noted that the steps shown in the flowcharts of the accompanying drawings can be executed in a computer system such as a set of computer-executable instructions, and , although a logical order is shown in the flowcharts, in some cases the steps shown or described may be performed in an order different from that shown or described herein.
[0027] figure 1 It is a flow chart of a method for processing obfuscated scripts according to an embodiment of the present invention, such as figure 1 As shown, the method includes the following steps:
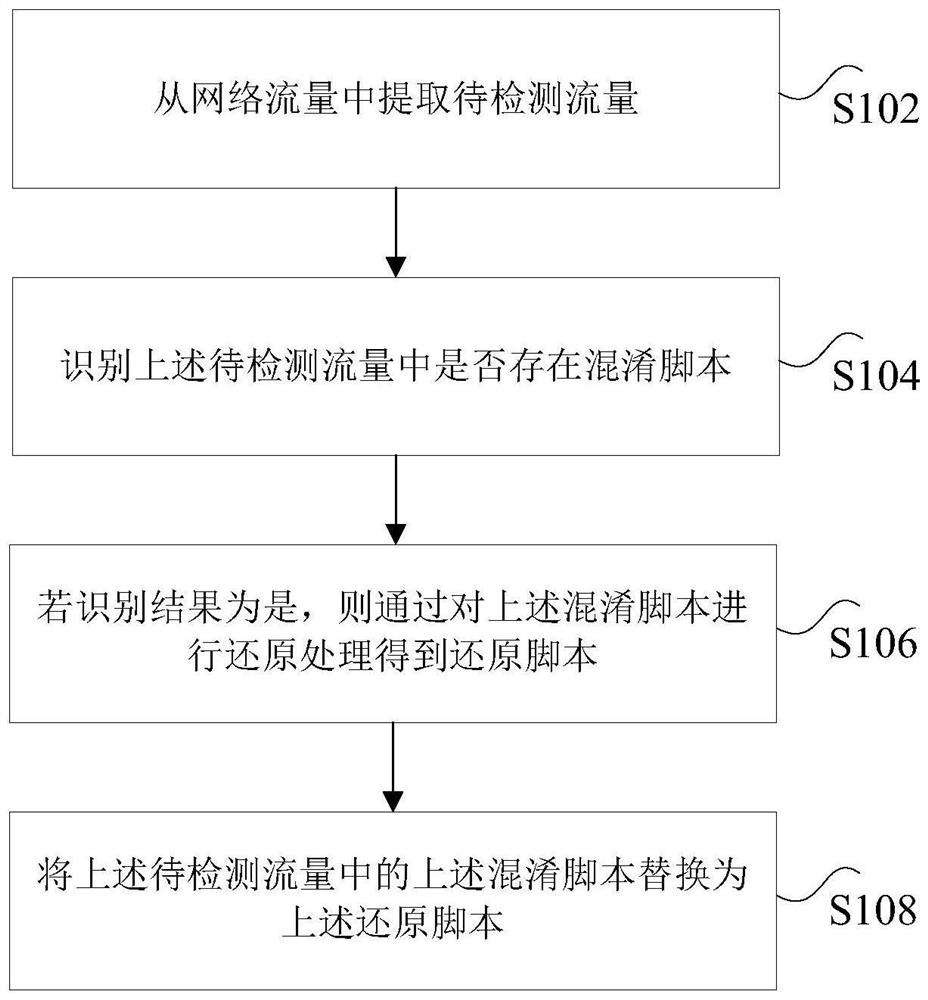
[0028] Step S102, extracting the traffic to be detected from the network traffic;
[0029] Step S104, identifying whether there is an obfuscation script in the traffic to be detected;
[0030] Step S106, if the recognition result is yes, then obtain the restored script by performing restoration ...
Embodiment 2
[0101]根据本发明实施例,还提供了一种用于实施上述混淆脚本的处理方法的装置实施例,图5是根据本发明实施例的一种混淆脚本的处理装置的结构示意图,如图5所示,上述混淆脚本的处理装置,包括:提取模块50、识别模块52、还原模块54和替换模块56,其中:
[0102]提取模块50,用于从网络流量中提取待检测流量;识别模块52,用于识别上述待检测流量中是否存在混淆脚本;还原模块54,用于若识别结果为是,则通过对上述混淆脚本进行还原处理得到还原脚本;替换模块56,用于将上述待检测流量中的上述混淆脚本替换为上述还原脚本。
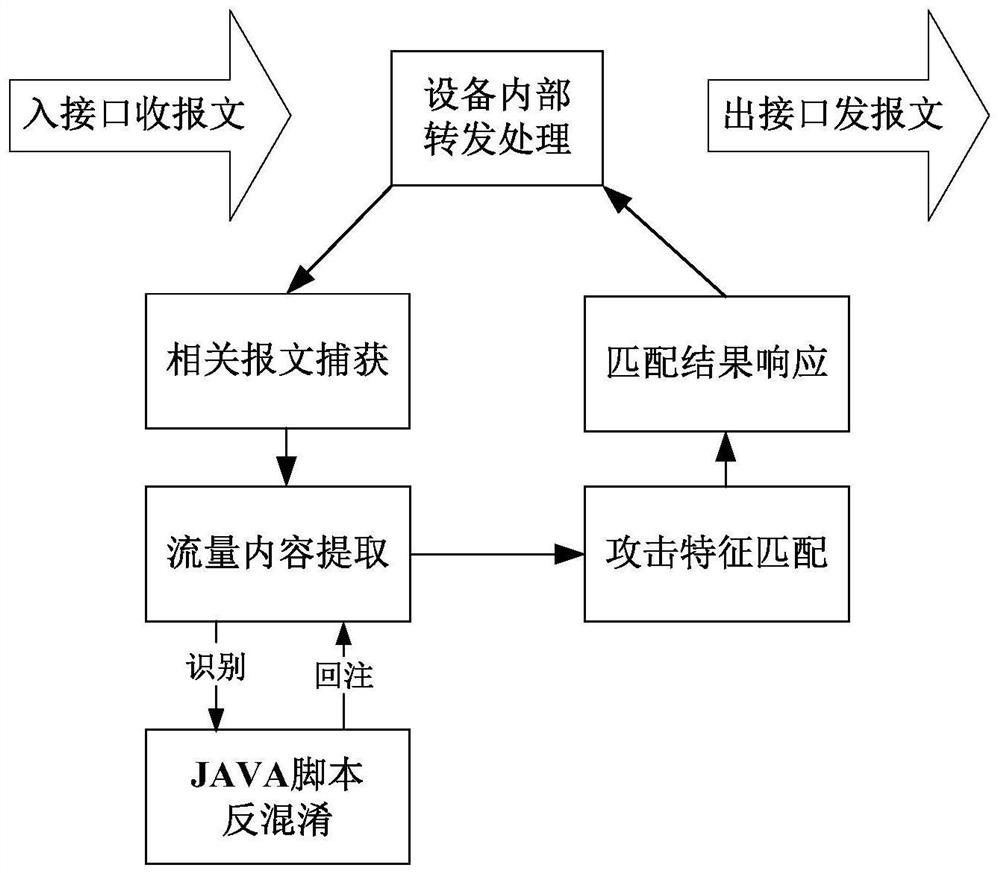
[0103]在本发明实施例中,通过从网络流量中提取待检测流量;识别上述待检测流量中是否存在混淆脚本;若识别结果为是,则通过对上述混淆脚本进行还原处理得到还原脚本;将上述待检测流量中的上述混淆脚本替换为上述还原脚本,达到了准确检测出混淆脚本的目的,从而实现了提高攻击检出率的技术效果,进而解决了现有技术中通过对混淆后的JAVA脚本提取规则的方式检测混淆脚本,无法准确检测出混淆脚本导致攻击检出率较低的技术问题。
[0104]需要说明的是,上述各个模块是可以通过软件或硬件来实现的,例如,对于后者,可以通过以下方式实现:上述各个模块可以位于同一处理器中;或者,上述各个模块以任意组合的方式位于不同的处理器中。
[0105]此处需要说明的是,上述提取模块50、识别模块52、还原模块54和替换模块56对应于实施例1中的步骤S102至步骤S108,上述模块与对应的步骤所实现的实例和应用场景相同,但不限于上述实施例1所公开的内容。需要说明的是,上述模块作为装置的一部分可以运行在计算机终端中。
[0106]需要说明的是,本实施例的可选或优选实施方式可以参见实施例1中的相关描述,此处不再赘述。
[0107]上述的混淆脚本的处理装置还可以包括处理器和存储器,上述提取模块50、识别模块52、还原模块54和替换模块56等均作为程序单元存储在存储器中,由处理器执行存储在存储器中的上述程序单元来实现相应的功能。
[0108]处理器中包含内核,由内核去存储器中调取相应的程序单元,上述内核可以设置一个或以上。存储器可能包括计算机可读介质中的非永久性存储器,随机存取存储器(RAM)和 / 或非易失性内存等形式,如只读存储器(ROM)或闪存(flash RAM),存储器包括至少一个存储芯片。
[0109]根据本申...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com