Mobile terminal information confidential method and mobile terminal
A mobile terminal and information security technology, applied in the electronic field, can solve the problem of easy leakage of user information, and achieve the effect of avoiding difficult recovery and improving reliability.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
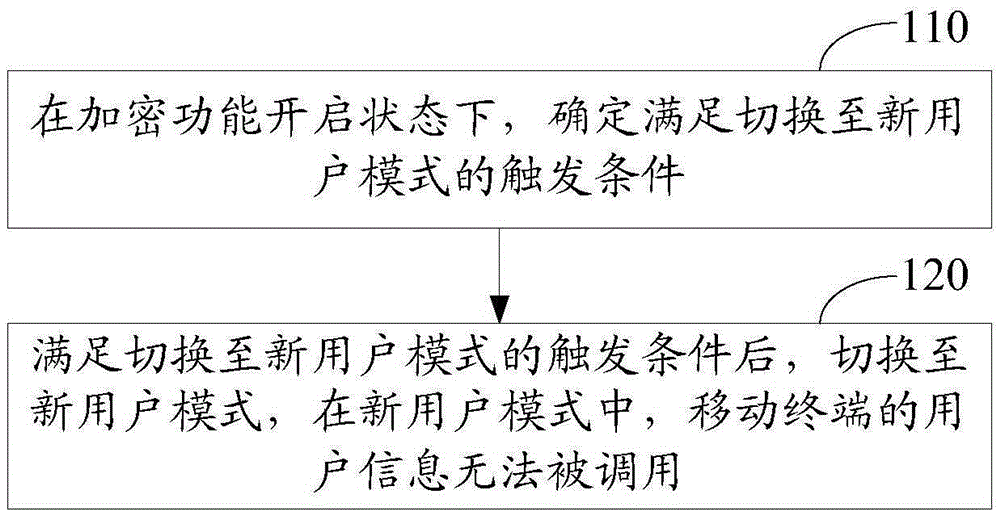
[0017] The following provides a more detailed description of an information security method for a mobile terminal and a mobile terminal provided by the present invention with reference to the accompanying drawings and embodiments.
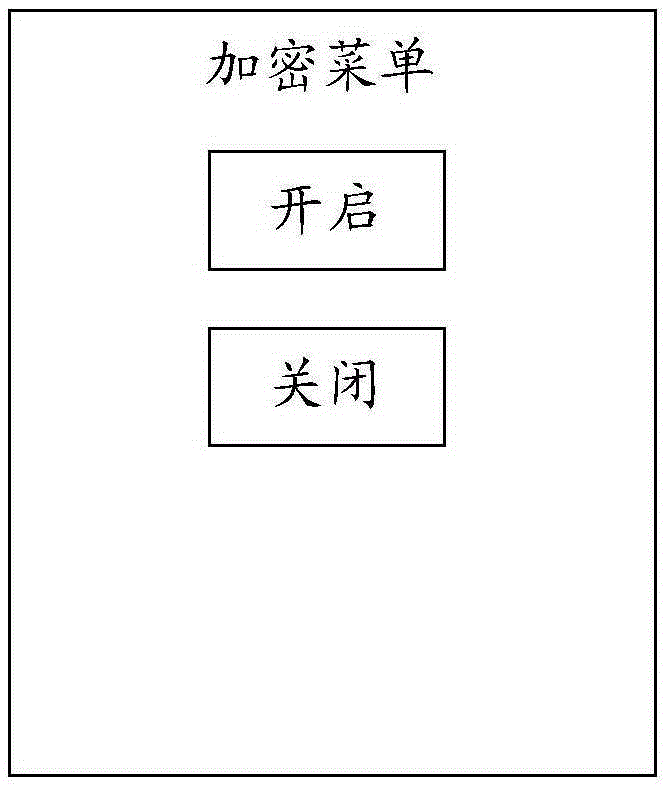
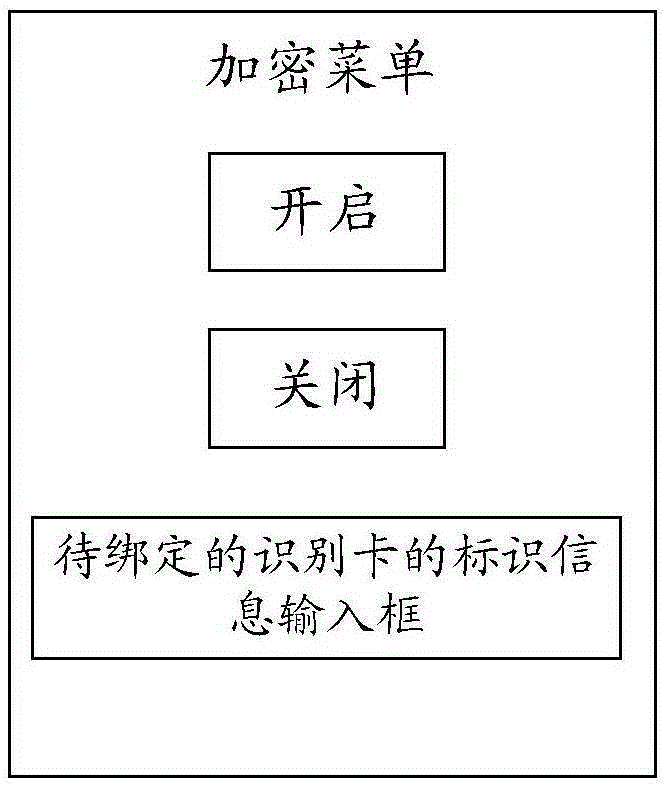
[0018] In order to keep the user information of the mobile terminal confidential, the mobile terminal adopting the technical solution provided by the embodiment of the present invention has an encryption function. Specifically, after determining that the trigger condition for switching to the new user mode is satisfied, the mobile terminal will be switched to the new user mode . Among them, in the new user mode, the user information of the mobile terminal cannot be called, thereby achieving the purpose of keeping the user information confidential. During the use process of the owner user, once the triggering condition for switching to the new user mode is met, it will also switch to the new user mode, and the owner user does not need to keep user info...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com