A security communication method and device
A security communication and security chip technology, applied in the field of communication, can solve the problems of monitoring, endangering the security of communication interaction, poor user experience, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0079] The following will clearly and completely describe the technical solutions in the embodiments of the present invention with reference to the drawings in the embodiments of the present invention.
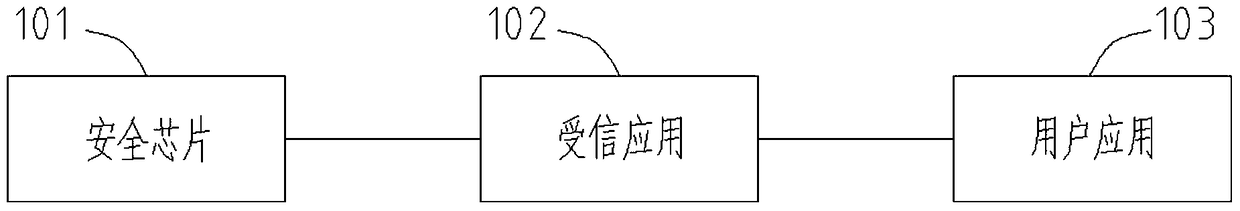
[0080] This application proposes a secure communication device, such as figure 1 As shown, it includes a security chip 101, a trusted application 102 and a user application 103. The following describes each component, wherein:
[0081] 1. The security chip 101 is used to establish a connection with the trusted application 102 and communicate with the user application 103 through the trusted application 102;
[0082] Specifically: the security chip 101 sends an application confirmation instruction to the trusted security application 102, receives the TA identity information sent by the trusted security application 102, verifies the TA identity information of the trusted security application 102; 102 sends the SE identity information; receives the external authentication instru...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com