Mobile terminal safety control method and apparatus
A security control and mobile terminal technology, applied in computer security devices, instruments, electrical digital data processing, etc., can solve the problems of low security, mobile terminal information is easy to be stolen by others, etc., and achieve the effect of improving security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
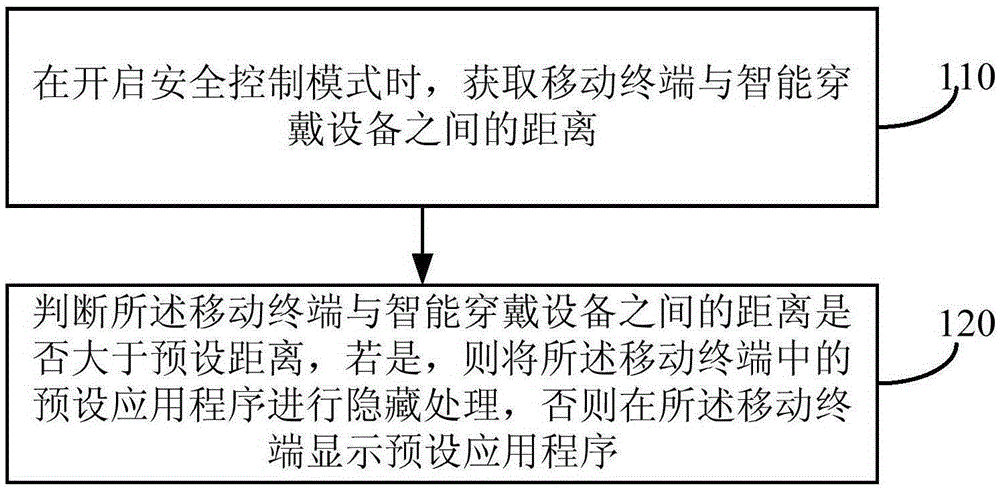
[0020] figure 1 It is a flow chart of a mobile terminal security control method provided by Embodiment 1 of the present invention. This embodiment is applicable to the situation where sensitive information is avoided when the mobile terminal is not with the owner user. This method can be implemented by the mobile terminal security control device To execute, the device can be implemented by means of software and / or hardware, specifically including the following steps:
[0021] Step 110, when the security control mode is turned on, obtain the distance between the mobile terminal and the smart wearable device;
[0022] Wherein, the user wears a smart wearable device, such as a smart bracelet or a smart watch. The mobile terminal includes a smart phone or a tablet computer and the like. Specifically, the distance between the mobile terminal and the smart wearable device can be obtained through GPS positioning, etc., and the distance between the mobile terminal and the smart wear...
Embodiment 2
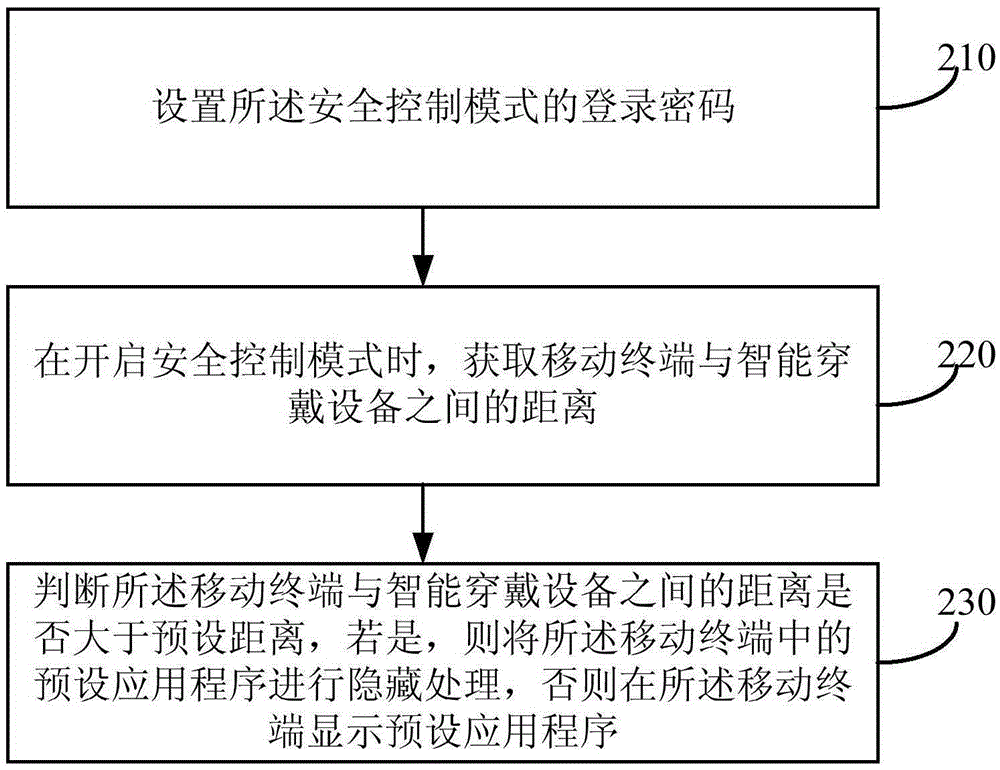
[0030] figure 2 It is a flow chart of a mobile terminal security control method provided by Embodiment 2 of the present invention. This embodiment is a further optimization of the above embodiment. The difference from the above embodiment is that before the security control mode is turned on, the setting described The login password of the security control mode, the benefit of setting this way is to prevent other people except the user from closing the security control mode of the mobile terminal, so that the relevant information of the user is leaked through the mobile terminal. see figure 2 , the method specifically includes the following:
[0031] Step 210, setting the login password of the security control mode.
[0032] Before the security control mode is opened, the login password of the security control mode is set. This operation can be to increase the switch of the security control mode in the application setting interface of the mobile terminal, which is used to ...
Embodiment 3
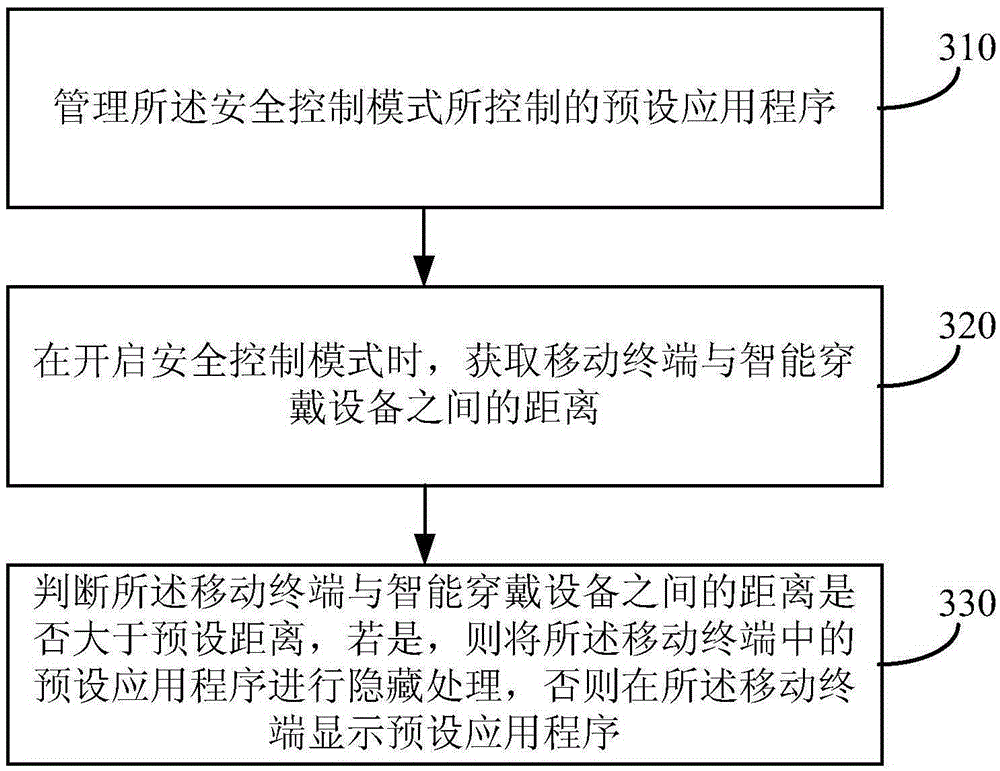
[0038] image 3 It is a flow chart of a mobile terminal security control method provided in Embodiment 3 of the present invention. Compared with the mobile terminal security control method provided in Embodiment 1, this method adds the preset application controlled by the management of the security control mode The advantage of this setting is that it is convenient for users to set preset applications. see image 3 , the method specifically includes the following:
[0039] Step 310, manage the preset application programs controlled by the security control mode.
[0040] This step can be set when the user turns on the security control mode of the mobile terminal. When the user turns on the security control mode, the system will pop up a window for setting the security control application for the user to select the corresponding application program, or put the existing one under security control The application of the mode is deleted. An independent operation button can also...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com