Network attack handling method and network attack handling device
A network attack and processing method technology, which is applied in the field of network attack processing methods and devices, can solve problems such as easy misjudgment of network attacks, and achieve the effects of ensuring normal progress, improving user experience, and enhancing the ability to identify misjudgments
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0051] It should be understood that the specific embodiments described here are only used to explain the present invention, not to limit the present invention.
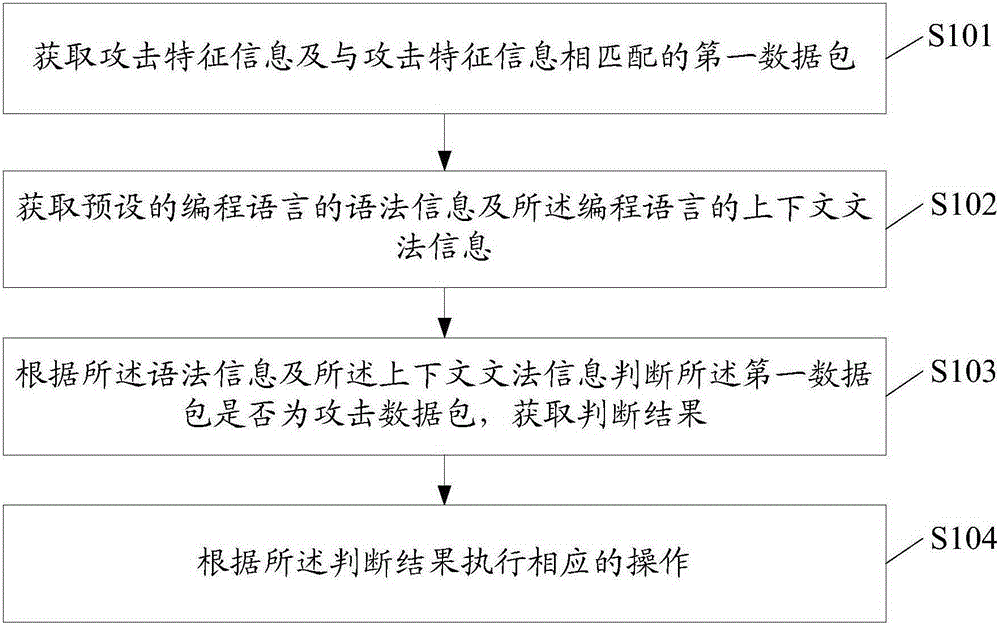
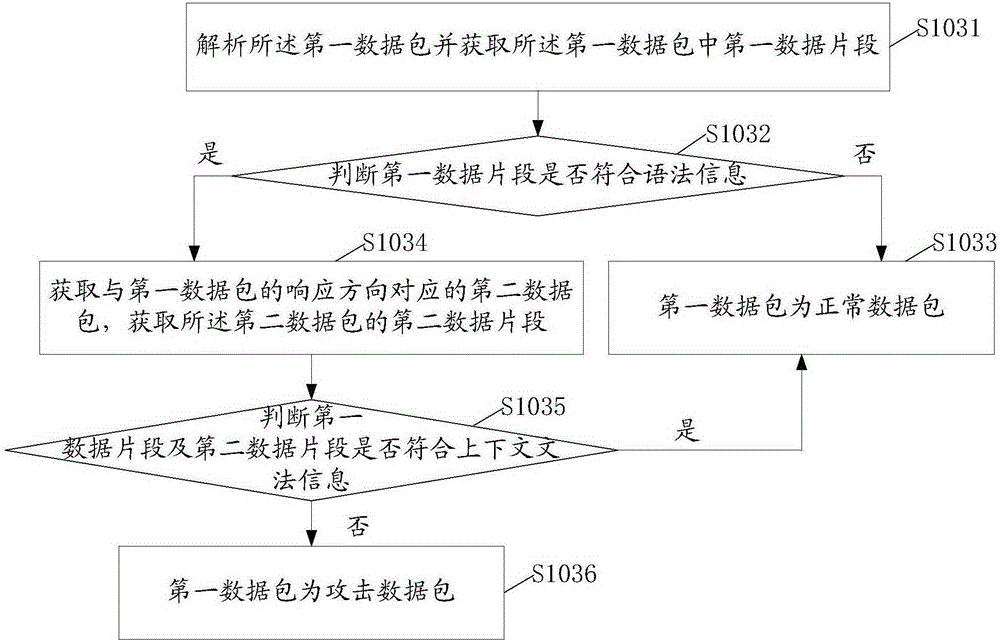
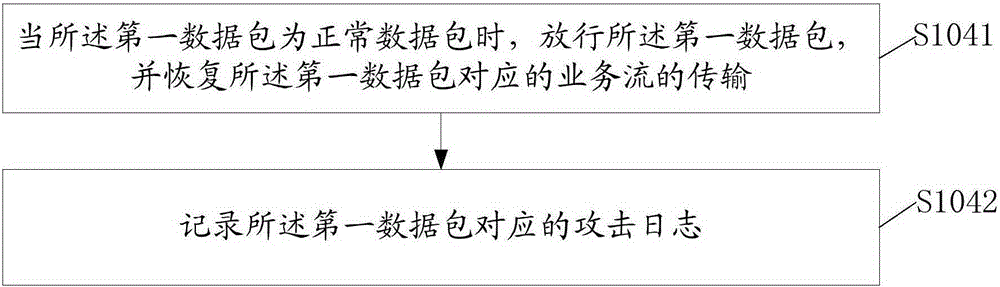
[0052] The present invention provides a kind of processing method of network attack, refer to figure 1 , in one embodiment, the processing method of the network attack includes:
[0053] Step S101, acquiring attack feature information and a first data packet matching the attack feature information;
[0054] SQL (StructuredQueryLanguage, Structured Query Language) injection is an attack that inserts or adds SQL code into the input parameters of the application, and then passes these parameters to the SQL server in the background for parsing and execution. In this embodiment, it mainly targets SQL injection This type of cyber attack, of course, can also be other cyber attacks.
[0055] In this embodiment, when performing attack detection on network data, the attack feature information stored in the cloud server is obt...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com