Ultrahigh frequency RFID key alarm system
An alarm system and RFID tag technology, applied in the field of key alarm systems, can solve the problems that the key chain is easy to drop in places that are not easy to see, it is difficult to find the key, and the key is easy to be lost or stolen, so as to avoid the inconvenience of life , easy to expand, and low power consumption
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
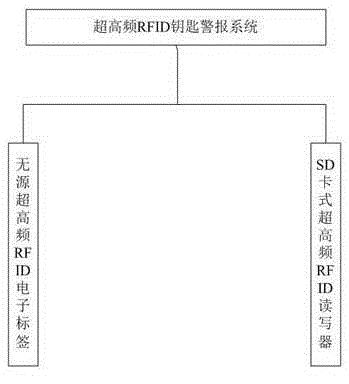
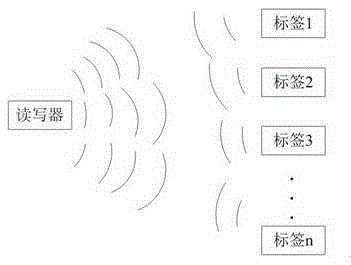
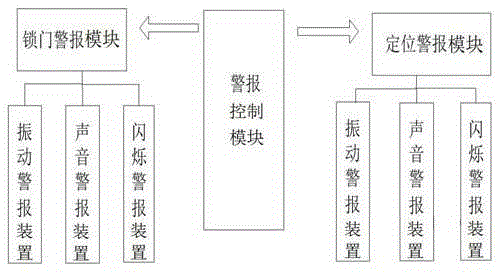
[0012] Example 1. like figure 1 As shown, it consists of two parts: UHF RFID tag and RFID reader. The UHF RFID tag uses a passive UHF RFID tag. The passive UHF RFID tag is pasted on the key handle. The RFID reader uses SD card type RFID reader, the RFID reader is placed in the SD card slot of the mobile phone. like image 3 As shown, a door lock alarm module, a location alarm module and an alarm control module are installed in the mobile phone, the door lock alarm module and the location alarm module are connected to the alarm control module, and the alarm control module is connected to the RFID reader; The alarm module is respectively provided with a vibration alarm device, a sound alarm device and a flashing alarm device.
[0013] Working principle: The present invention can realize two functions: one is door lock alarm; The realization of its function is based on the judgment of the signal strength between the RFID reader and the UHF RFID electronic tag. When the ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com