Portal authentication method, portal server and terminal
An authentication method and server technology, applied in the Internet field, can solve the problem of low security of user information and achieve the effect of improving security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
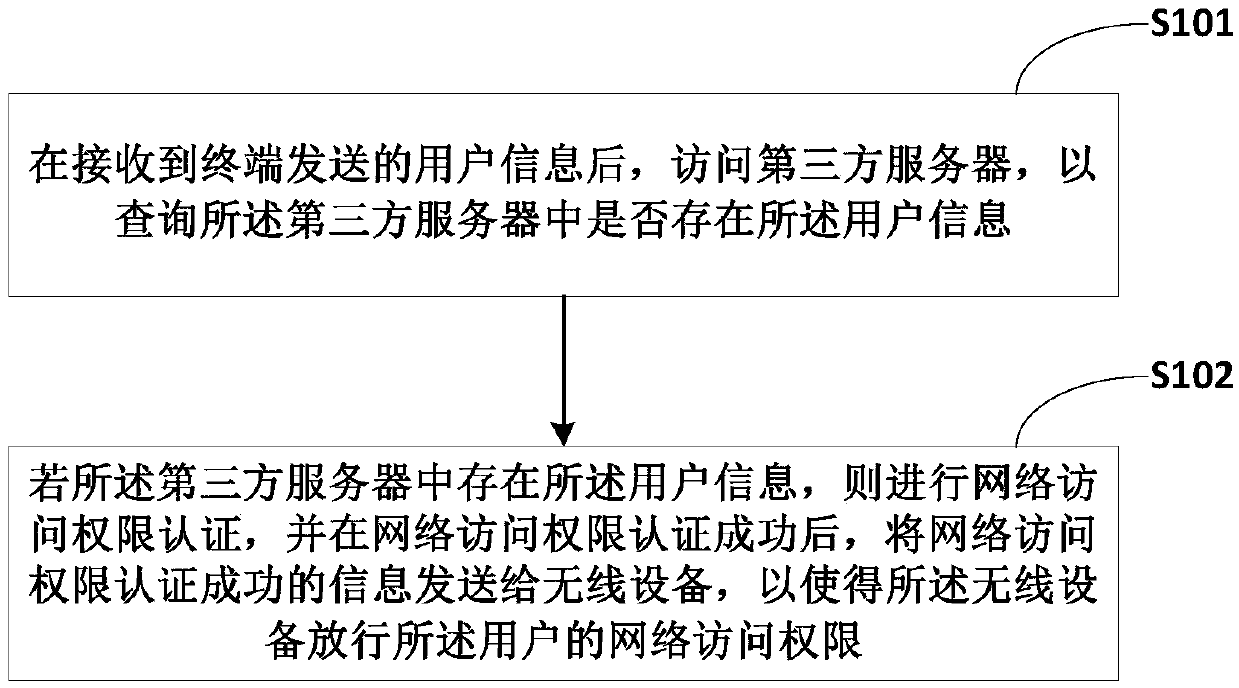
[0034] figure 1 The implementation flow of the portal authentication method provided by Embodiment 1 of the present invention is shown, and the implementation flow is described in detail as follows:
[0035] In step S101, after receiving the user information sent by the terminal, access a third-party server to query whether the user information exists in the third-party server;
[0036] In the embodiment of the present invention, after the portal server receives the user information sent by the terminal, it queries the user information of the third-party server, such as the member information of Taobao. Verify user information in the portal server, improving the security of user information.
[0037] In the embodiment of the present invention, the user information includes a user name and an encrypted password. After receiving the user name and encrypted password sent by the terminal, the portal server accesses the third-party server to inquire whether there is a password in ...
Embodiment 2
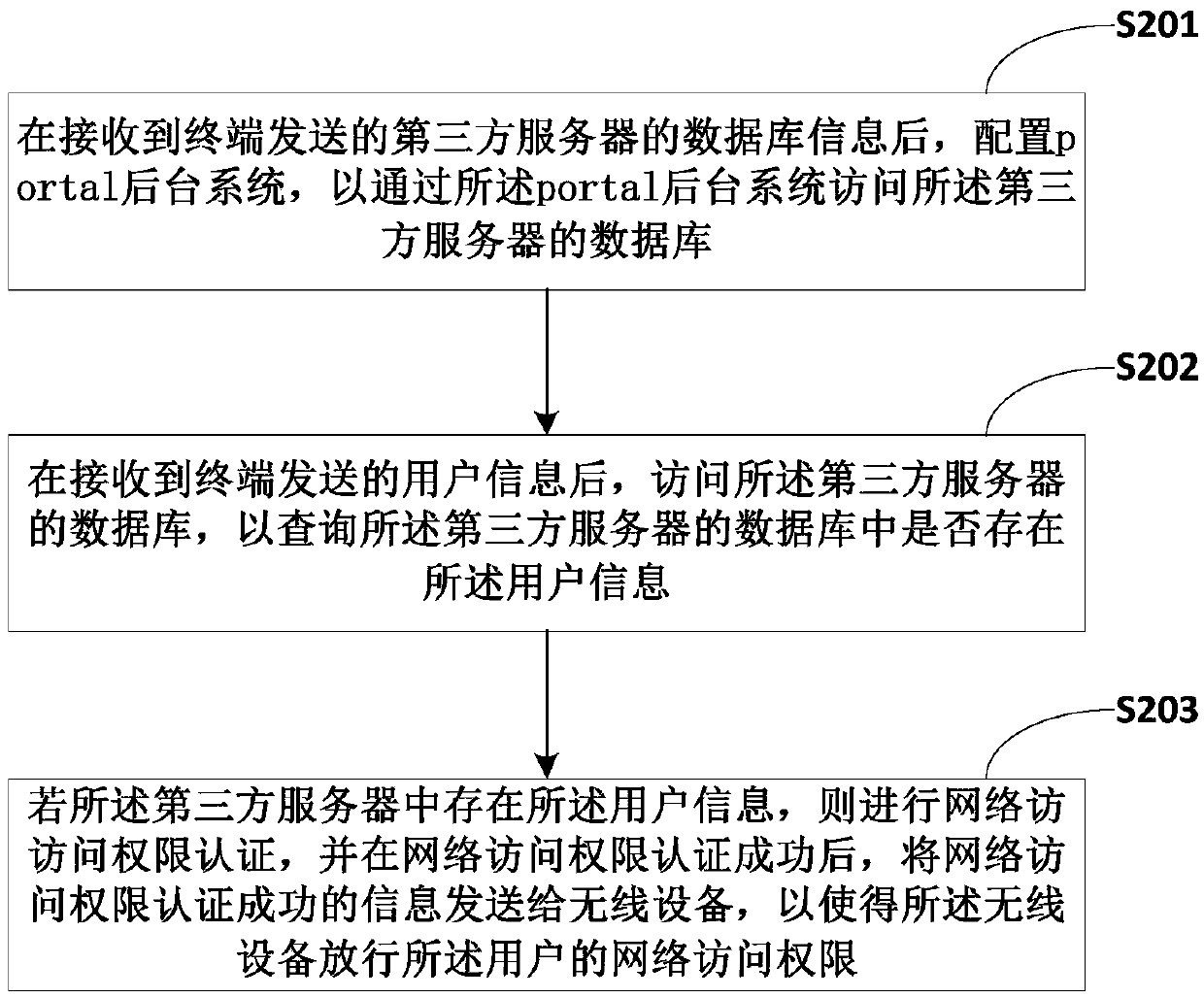
[0046] figure 2 The implementation flow of the portal authentication method provided by Embodiment 2 of the present invention is shown, and the implementation flow is described in detail as follows:
[0047] In step S201, after receiving the database information of the third-party server sent by the terminal, configure the portal background system to access the database of the third-party server through the portal background system;
[0048] In the embodiment of the present invention, after receiving the database information of the third-party server sent by the terminal, the portal server configures the portal background system according to the database information of the third-party server, so as to access the third-party server through the portal background system database, query the basic user information in the database of the third-party server, the basic user information does not include encrypted passwords, including but not limited to user names, phone numbers, and h...
Embodiment 3
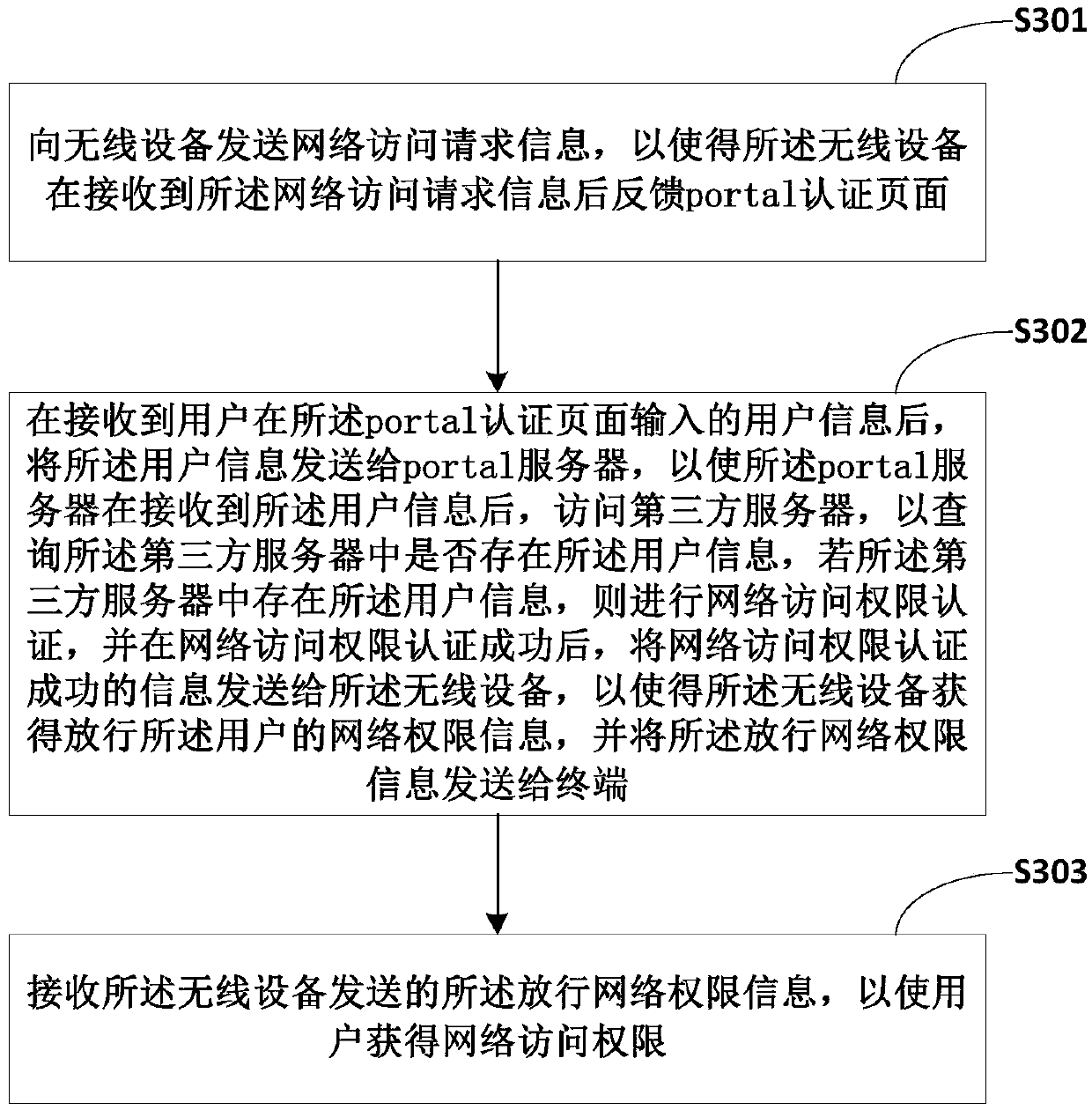
[0065] image 3 The implementation flow of the portal authentication method provided by Embodiment 3 of the present invention is shown, and the implementation flow is described in detail as follows:
[0066] In step S301, sending network access request information to the wireless device, so that the wireless device feeds back a portal authentication page after receiving the network access request information;
[0067] In the embodiment of the present invention, the terminal sends network access request information to the wireless device, so that the wireless device feeds back a portal authentication page after receiving the network access request information.
[0068] Preferably, the wireless device may be an AP and / or an AC.
[0069] In step S302, after receiving the user information input by the user on the portal authentication page, the user information is sent to the portal server, so that the portal server can access the third-party server after receiving the user infor...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com