Intelligent gate inhibition realization method, terminal, gate inhibition identification apparatus and user authorization service center
A user authorization and service center technology, applied in the field of terminals, access control identification devices, user authorization service centers, and intelligent access control implementation methods, can solve problems such as non-existence, flexibility limitations, and increased workload of property staff
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
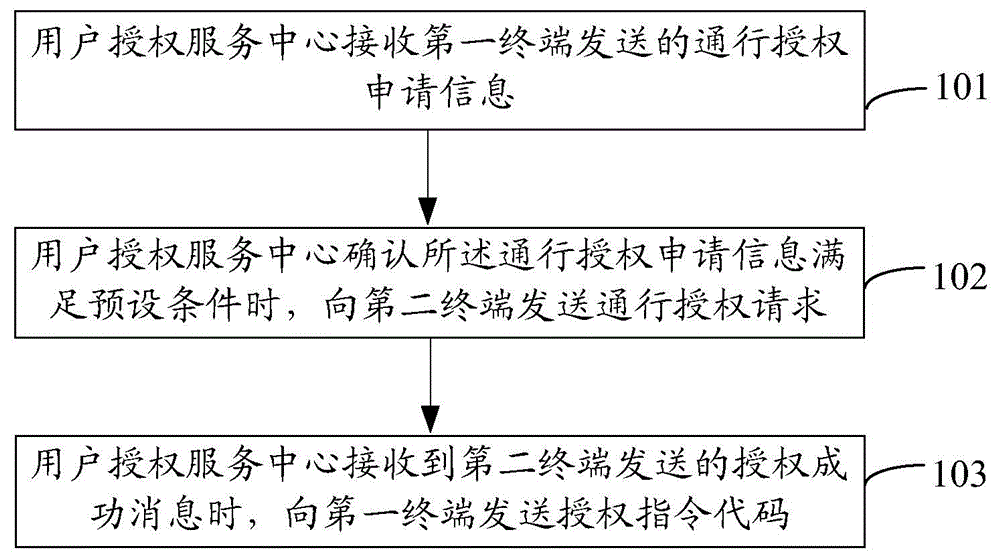
[0086] Embodiment 1 of the present invention provides a method for implementing intelligent access control, such as figure 1 As shown, the method includes the following steps:
[0087] Step 101: the user authorization service center receives the passage authorization application information sent by the first terminal;
[0088] Specifically, the user authorization service center here can be implemented by a server, a personal computer (PC, PersonalComputer) or other methods;
[0089] The first terminal is a visitor terminal. Before step 101, a communication connection has been established between the first terminal and the user authorization service center. Specifically, a communication connection can be established through Near Field Communication (NFC, Near Field Communication), Bluetooth, Wireless Fidelity (WIFI) , WIreless-Fidelity), instant messaging tools or 2G, 3G, 4G and other data mobile communication methods to establish communication connections.
[0090] The pass ...
Embodiment 2
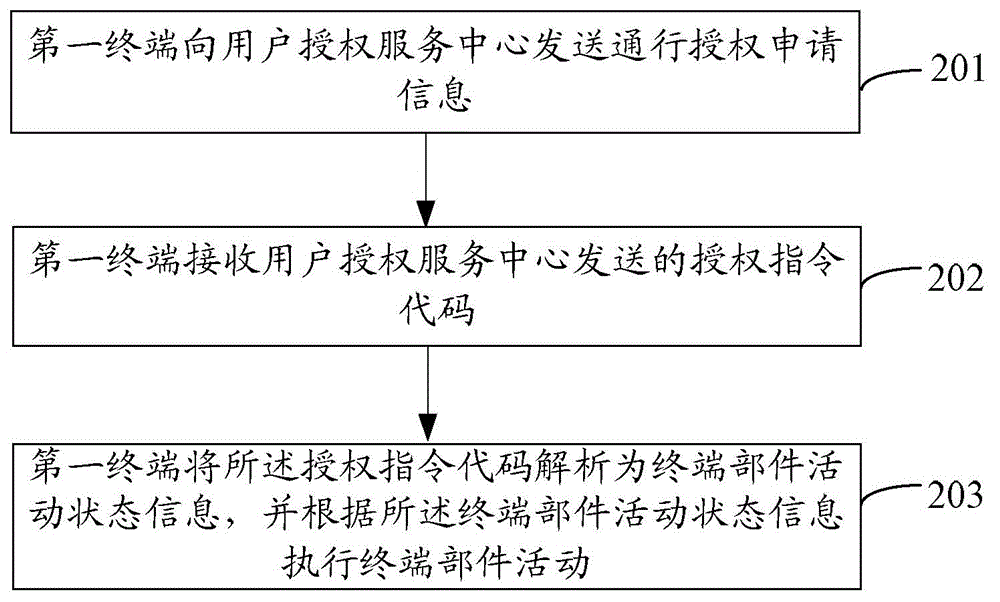
[0115] Embodiment 2 of the present invention provides a method for implementing intelligent access control, such as figure 2 As shown, the method includes the following steps:
[0116] Step 201: the first terminal sends the application information of the authorization to the user to the user authorization service center;
[0117] Specifically, before step 201, the first terminal needs to establish a communication connection with the user authorization service center, specifically, through NFC, Bluetooth, wireless fidelity (WIFI, WIreless-Fidelity), instant messaging tools or 2G, 3G, 4G and other data mobile communication methods to establish communication connections.
[0118] The pass authorization application information sent by the first terminal includes interviewee information, and the interviewee information includes at least one of the following information: interviewee name, interviewee phone number, interviewee house number. Further described communication authoriz...
Embodiment 3
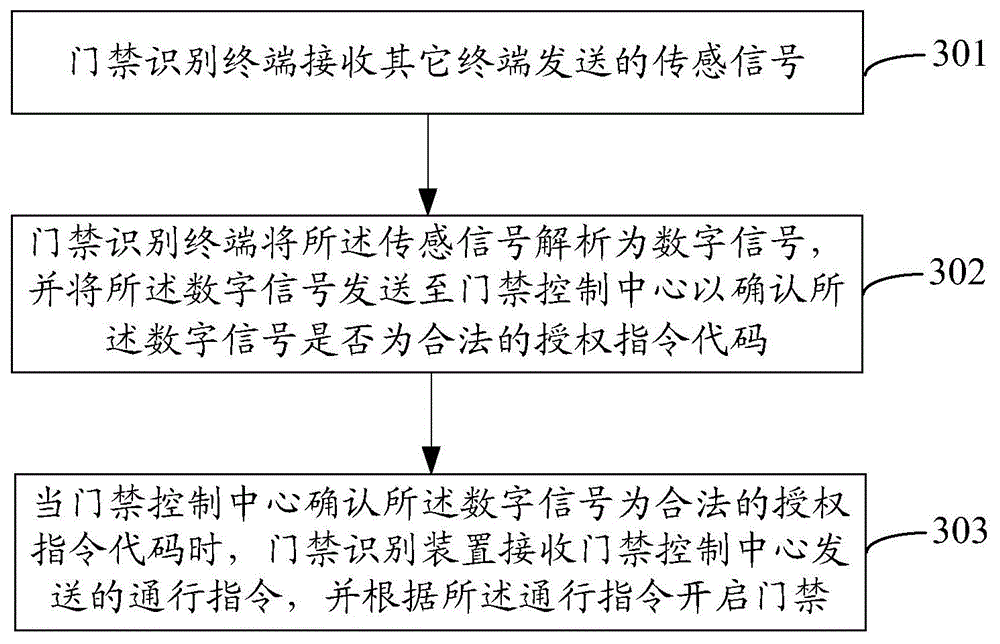
[0132] Embodiment 3 of the present invention provides a method for implementing intelligent access control, such as image 3 As shown, the method includes the following steps:
[0133] Step 301: the access control identification device receives sensing signals sent by other terminals;
[0134] Specifically, the sensing signal includes at least one of the following signals: a vibration signal, an audio signal, and a flash signal;
[0135] Step 302: the access control identification device parses the sensing signal into a digital signal, and sends the digital signal to the access control center to confirm whether the digital signal is a legal authorization instruction code;
[0136] The access control identification device resolves the sensing signal into a digital signal, including:
[0137] When the sensing signal is a vibration signal, the access control identification device resolves the vibration signal into a vibration frequency, and resolves the vibration frequency into...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com