Link security detection method and client
A security detection and client-side technology, applied in electrical components, transmission systems, platform integrity maintenance, etc., can solve problems such as reducing the role of security detection on network security protection, inefficiency, and inability to remove in time, to ensure network security, Improve user experience and improve real-time effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0045] In order to clarify the link security detection method provided by the above preferred embodiments more clearly, a preferred embodiment is now used to introduce the link security detection method provided by the embodiment of the present invention. Figure 5 A processing flowchart of a link security detection method according to a preferred embodiment of the present invention is shown. see Figure 5 , the process includes at least step S502 to step S516.
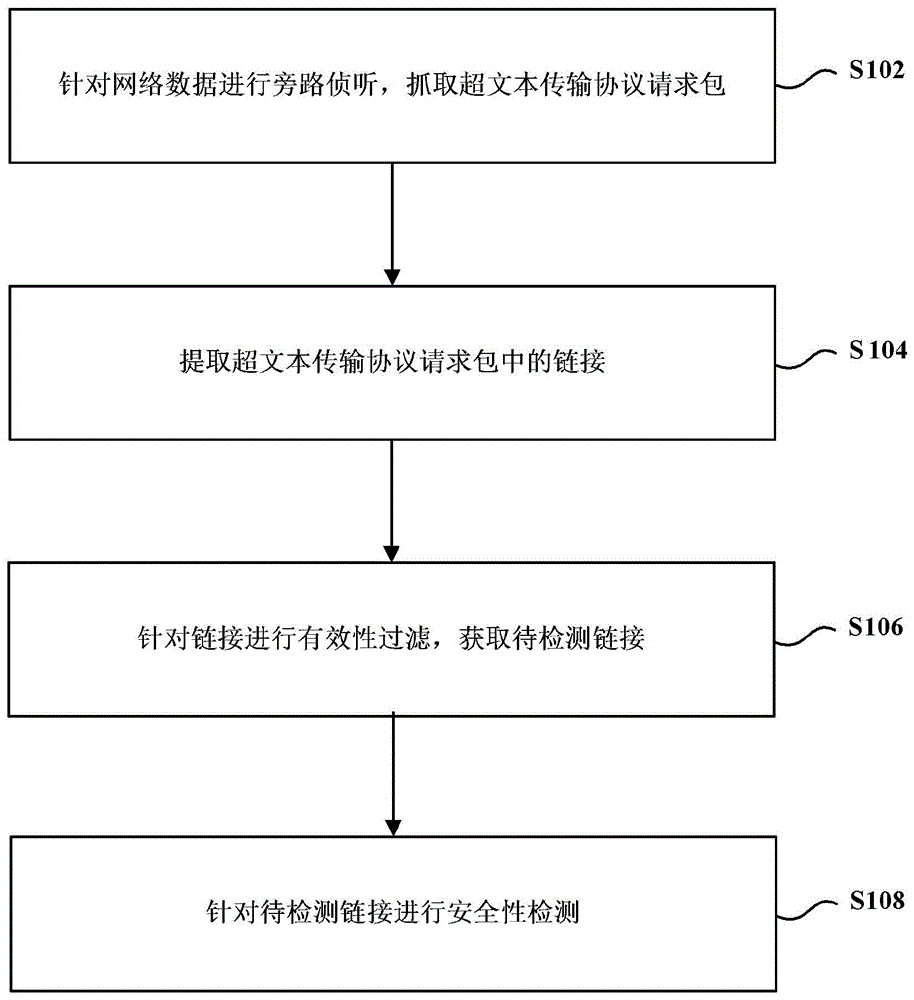
[0046] Step S502, perform bypass interception for network data, and capture the HTTP request packet.
[0047] Step S504, making statistics on the initiator IP addresses of the request packets captured in step S502.
[0048] Specifically, after capturing the request packet, count the number of requests initiated by the initiator of the request packet within a predetermined time.
[0049] Step S506, judging whether the number of requests initiated by the initiator within a predetermined time exceeds a predetermined t...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com