Smart contract security detection method and system, equipment, terminal and application
A technology of smart contracts and security detection, applied in neural learning methods, computer security devices, special data processing applications, etc., can solve the problems of increasing difficulty, difficulty in obtaining, and increasing the difficulty of model training, so as to reduce cumbersomeness and improve efficiency. Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
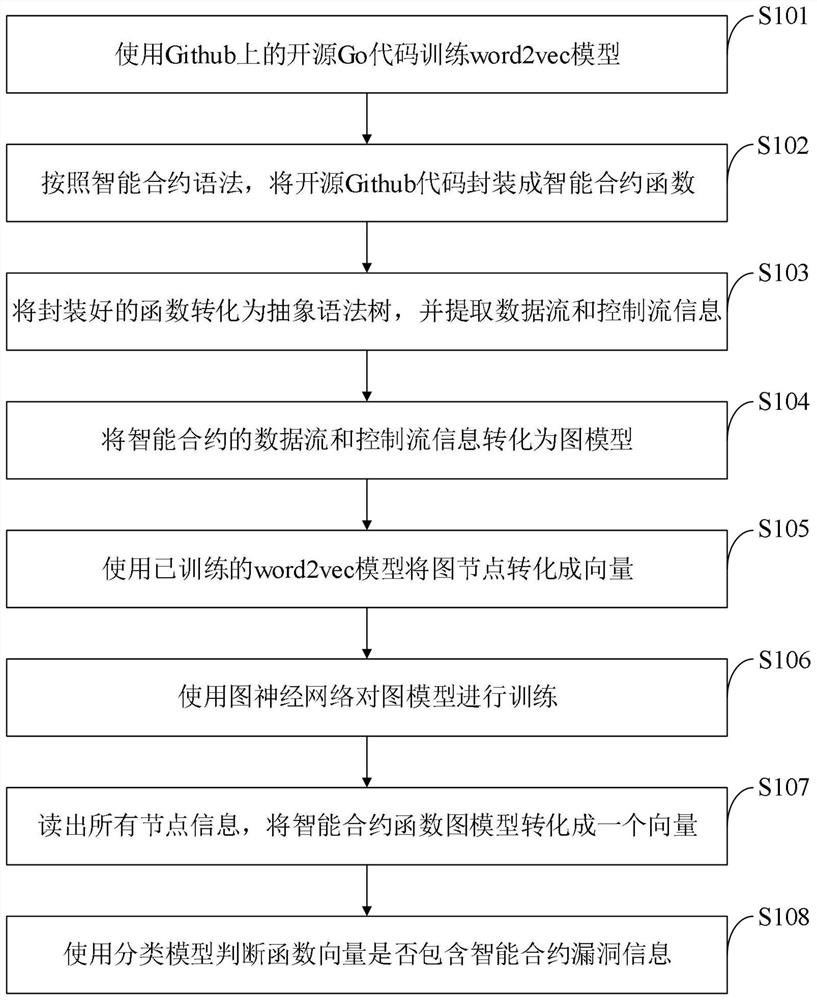
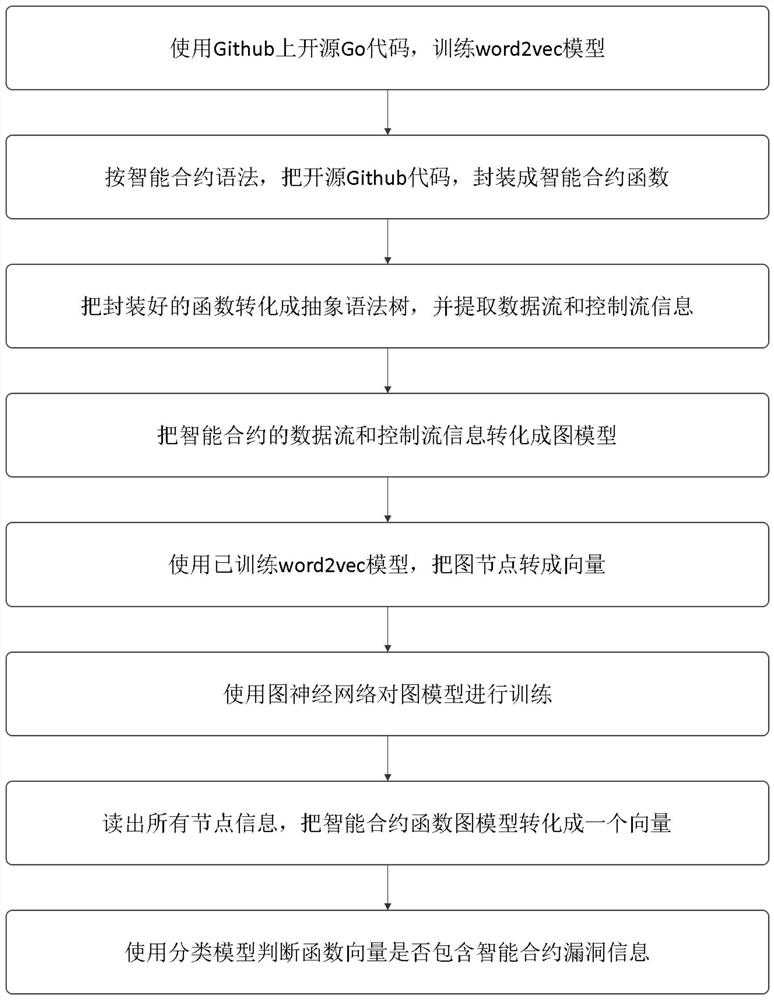
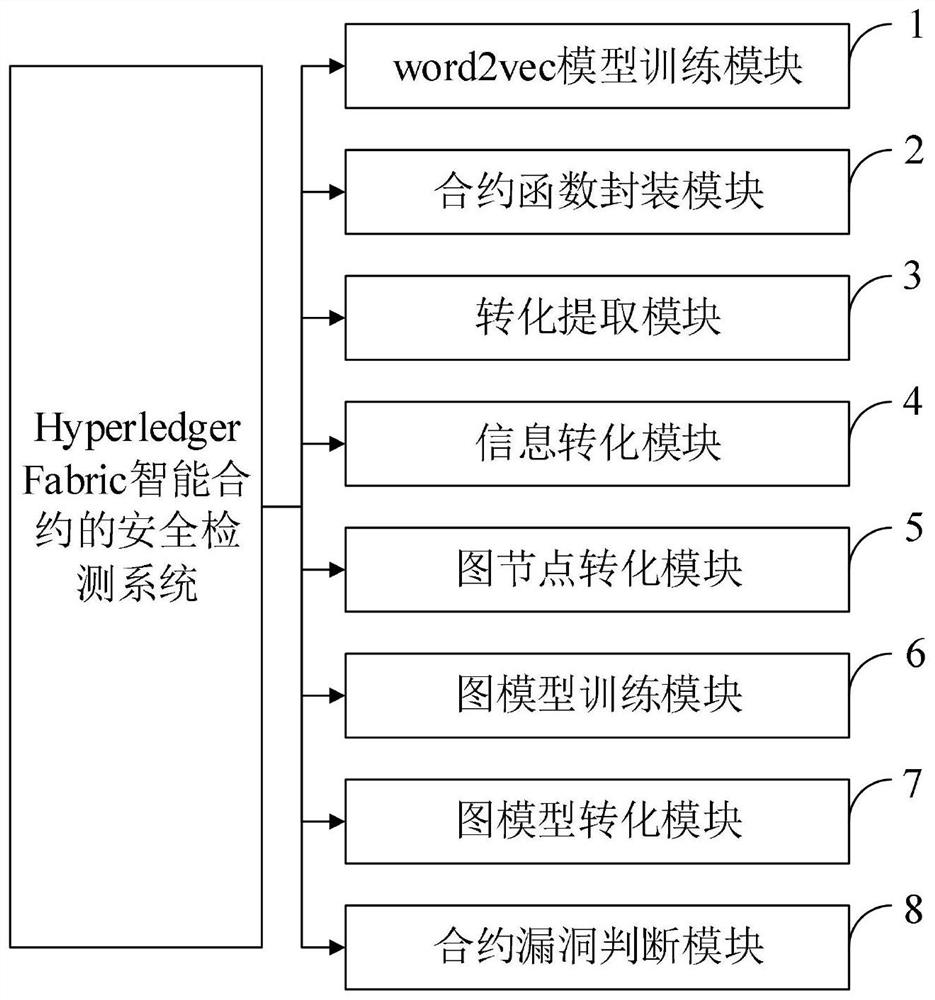
[0066] 1) The experiment uses TensorFlow-2.1.0 to implement the Fabric smart contract security detection model.
[0067] 2) Construct the AST graph of the source code with the help of the Go language ast package, and extract different edge relationships from it. That is, AST nodes of all source codes are traversed. When traversing, all nodes are sequentially numbered, and the relationship between different edges is obtained according to specific rules, and variable names are rewritten using a unified naming scheme. This step ensures that semantic differences such as variable names in the program do not affect the choice of token embedding.
[0068] 3) Create a directory, and then create a train.py training file.
[0069] 4) Write the GGNN model training code in this file. The code starts with the following package loading code.
[0070]
[0071] 5) In the same directory, create a test.py test file.
[0072] 6) Write the GGNN model test code in this file. The code star...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com