Security smart card using external terminal for verification and verification method thereof
A technology of external terminal and verification method, applied in the field of smart cards, can solve the problem of high risk of being read and stolen, and achieve the effect of improving security and ensuring the safety of funds
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0032] Introduced below are some of the various embodiments of the invention, intended to provide a basic understanding of the invention. It is not intended to identify key or critical elements of the invention or to delineate the scope of protection.
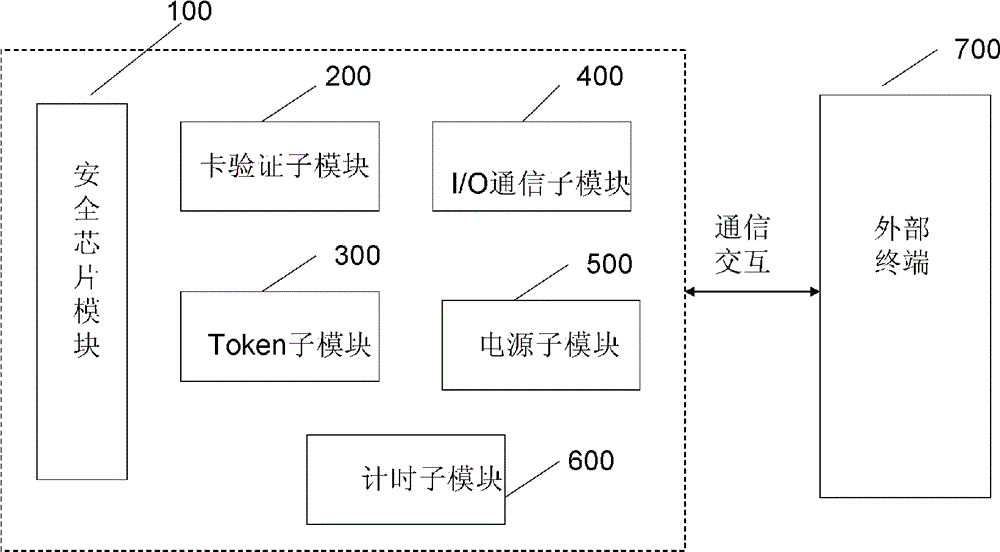
[0033] figure 1 It is a schematic diagram showing the structure of the secure smart card authenticated by an external terminal of the present invention.
[0034] like figure 1 As shown, the secure smart card authenticated by an external terminal of the present invention includes a security chip 100 , a card verification submodule 200 , a Token submodule, an I / O communication submodule, and a power supply submodule 500 . The security smart card authenticated by the external terminal of the present invention performs communication authentication with the external terminal 700 through communication interaction.
[0035] Next, each constituent unit of the secure smart card will be described.
[0036] The security chip module 10...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com