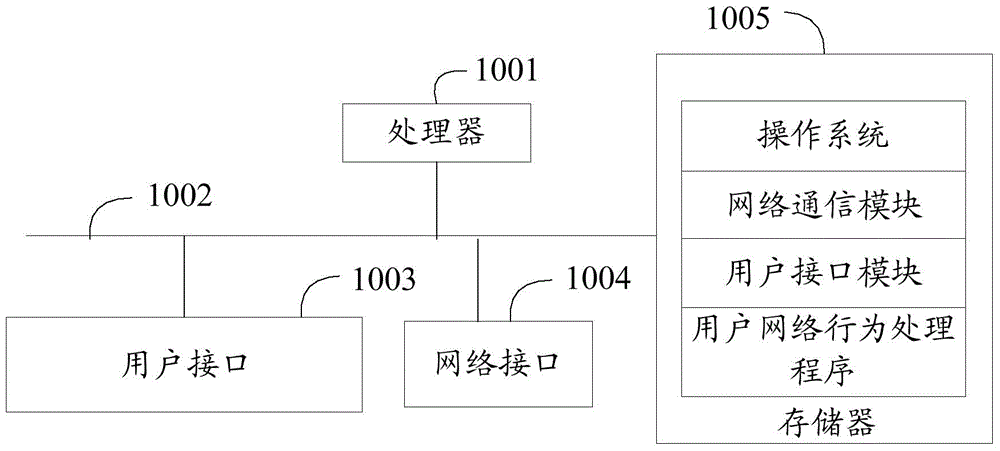
Method and device for processing user network behavior
A processing method and user technology, applied in the network field, can solve problems such as loss of game developers and promoters, troubles of normal users, etc., and achieve the effects of improving the accuracy of judgment, reducing the possibility of false strikes, and reducing losses
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0023] It should be understood that the specific embodiments described here are only used to explain the present invention, not to limit the present invention.
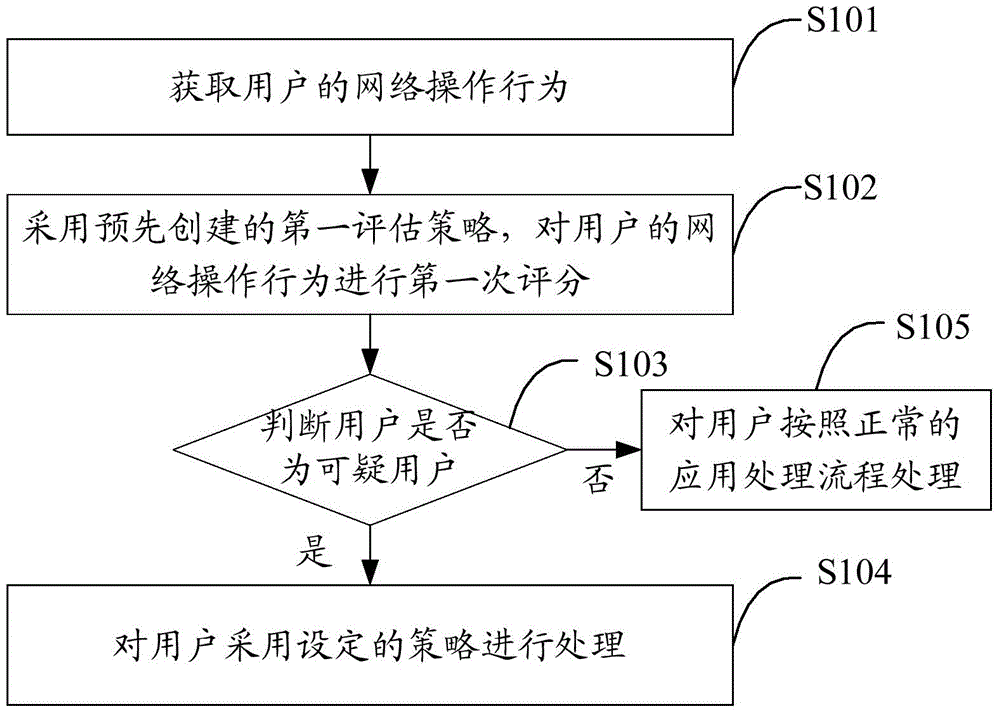
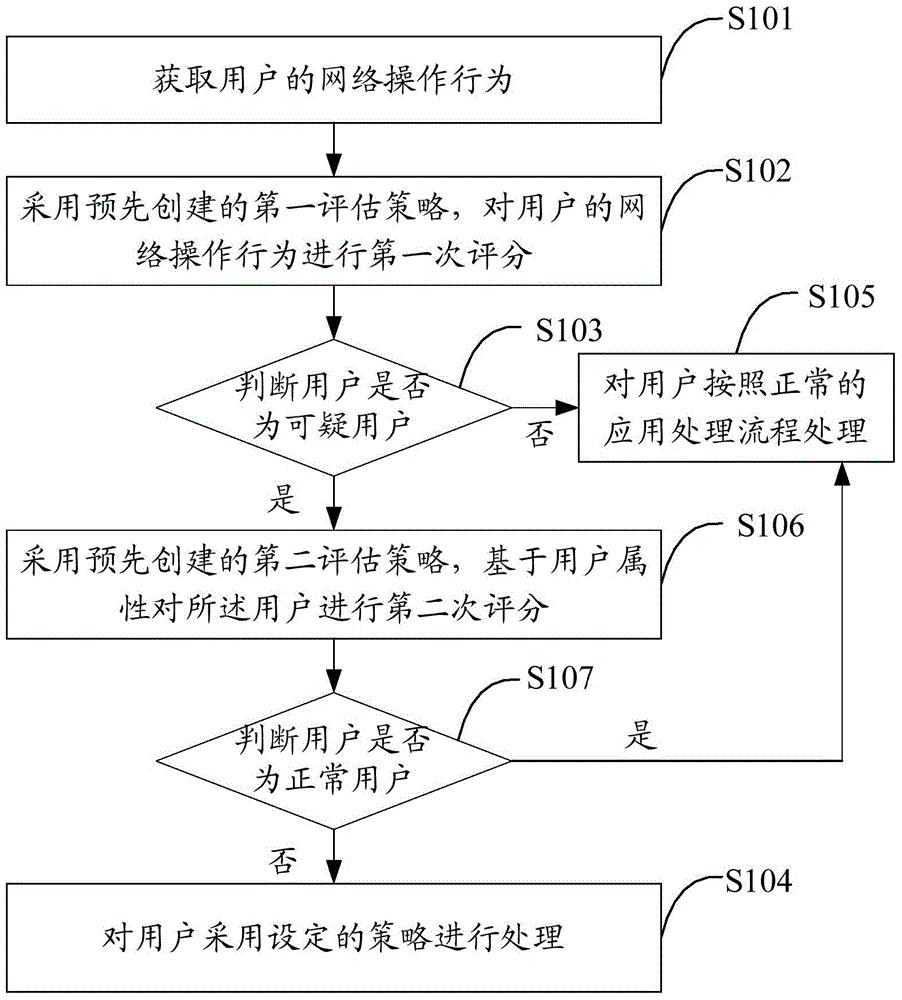
[0024] The main idea of the scheme of the embodiment of the present invention is: by acquiring the user's network operation behavior; using the pre-created first evaluation strategy, to score the user's network operation behavior for the first time; if the scoring result conforms to the preset of the first evaluation strategy conditions, it is judged that the user is a suspicious user; the user is maliciously attacked by using the set strategy, so that the effective interception of malicious behaviors in the network such as network advertisements, network activity services, and web application services can be realized, reducing application developers and Sponsor's Loss. Furthermore, users who are judged as suspicious can be scored for a second time using a pre-created second evaluation strategy, and normal users can...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com