Method for detecting validity of magnetic disk, method for authenticating validity of magnetic disk, and corresponding device
A detection method and validity technology, applied in the field of authentication methods and corresponding devices, and disk validity detection methods, can solve the problems of not allowing non-"marked" disks to be inserted and mixed, link parameters mismatch, link errors, etc., To achieve the effect of providing safety and reliability
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
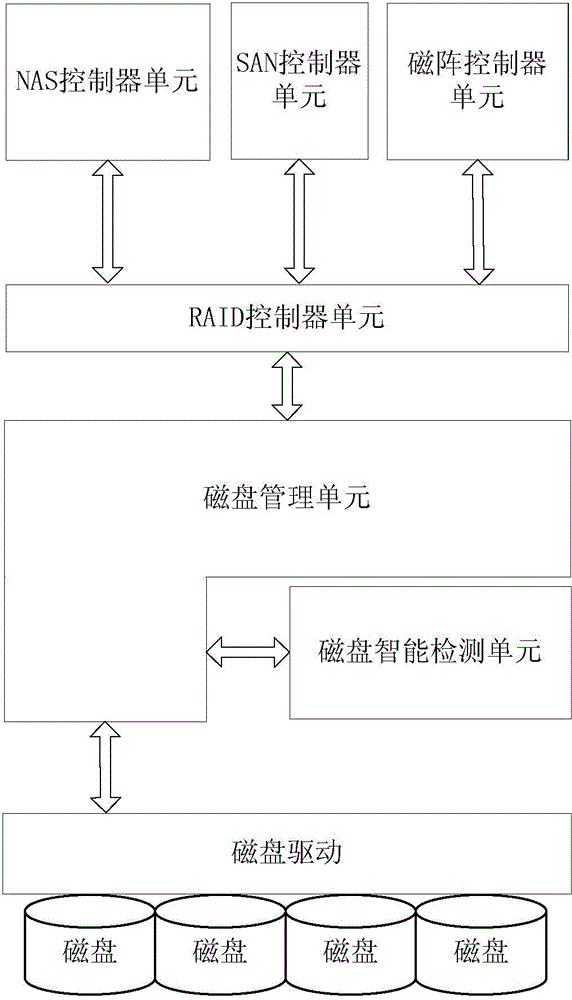
[0077] A disk validity detection method and authentication method provided by the invention are applied to a computer system. figure 1 Shown is a schematic diagram of the computer system structure, the computer storage system includes: disk, disk drive unit, disk management unit, disk intelligent detection unit, RAID (Redundant Arrays of independent Disks, redundant array of independent disks) controller unit, NAS (NetworkAttachedStorage, network attached storage ) controller unit, SAN (StorageAreaNetwork, storage area network) controller unit, magnetic array controller unit.
[0078] Wherein, the disk is a physical disk installed on the storage system as a physical storage medium by the user when using the storage system device, such as a common hard disk or a solid state disk (SSD).
[0079] Disk drive unit. After the disk is connected to the computer storage system, the system needs to use the disk drive unit to control the physical disk and read and write data.
[0080] T...
Embodiment 2
[0139] The technical solutions of the present invention will be further elaborated below in conjunction with the accompanying drawings and specific embodiments.
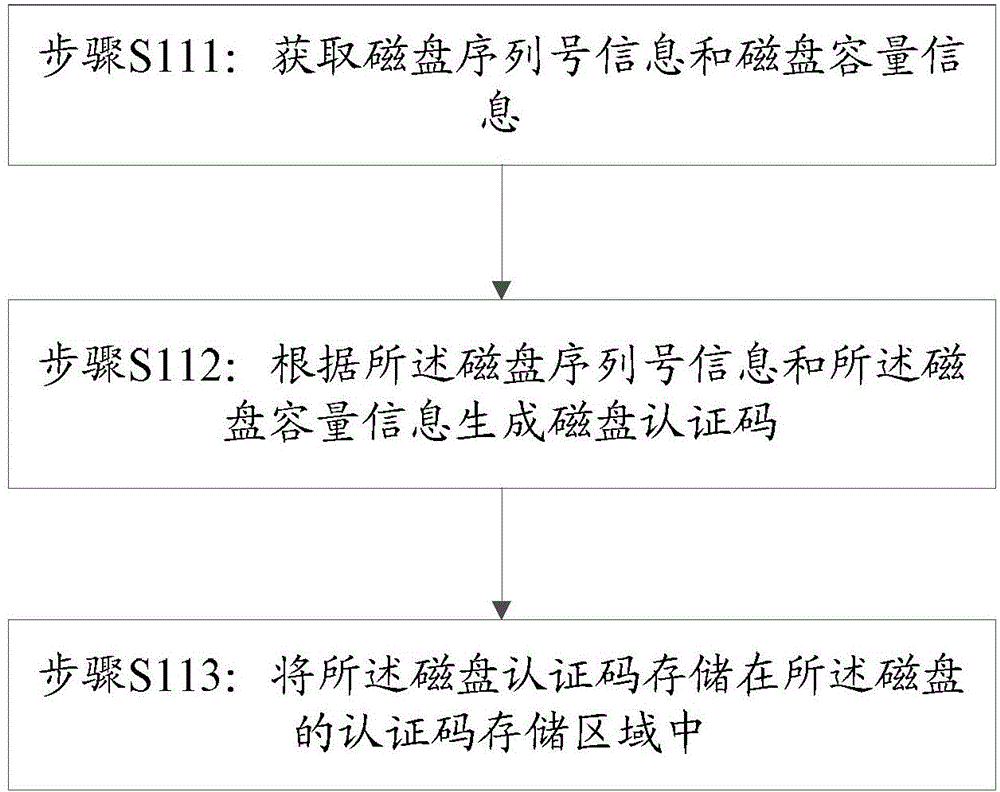
[0140] Such as Figure 6 Shown is a disk certification method of the present invention, such as Figure 6 The method shown includes four steps of reading the disk serial number and capacity information, calculating the disk authentication code, storing the authentication code, and feeding back the disk marking result.
[0141] In step 201, the system obtains the serial number and disk capacity of the disk that has passed the verification through software, and provides necessary parameters for the subsequent generation of the authentication code. If the serial number or disk capacity fails to be obtained, it prompts to mark the disk as failed authentication.
[0142] Step 202, on the basis of the disk serial number and capacity obtained in step 201, the serial number and capacity are combined to generate an authentic...
Embodiment 3
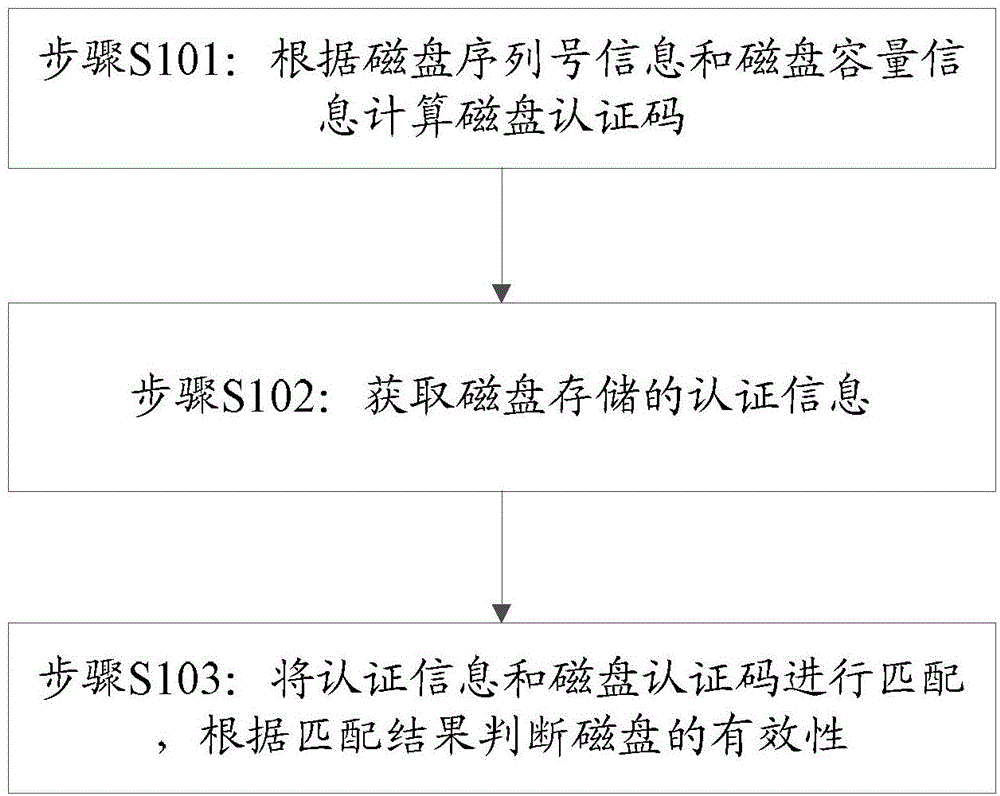
[0151] Such as Figure 8 Shown is the detection method of a kind of disk effectiveness of the present invention, specifically comprises:
[0152] Step 301, obtain the disk serial number and disk capacity, and calculate the disk authentication code of the disk to be identified by using the algorithm described in step 202;
[0153] Step 302, read as Figure 7 The shown disk fixes the authentication information of the two areas, and checks whether the format of the obtained two sets of authentication information is legal.
[0154] Step 303, if only one group of the two groups of authentication information obtained is legal, only extract the authentication code from the legal group of data (if all are legal, then proceed to step 305), the extracted authentication code is the same as the disk authentication code obtained in step 401 to match. If the matching fails, the computer storage system is notified that the disk is an illegal disk and cannot be used.
[0155] Step 304, if...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com