Sensitive data protection system and method of data circulation and transaction of big data platform
A big data platform and technology for sensitive data, applied in the field of big data, can solve problems such as lack of sensitive data protection, verification of desensitization results, and obstruction of data flow.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0071] For better understanding of the present invention, the present invention is described in detail below with reference to the accompanying drawings.
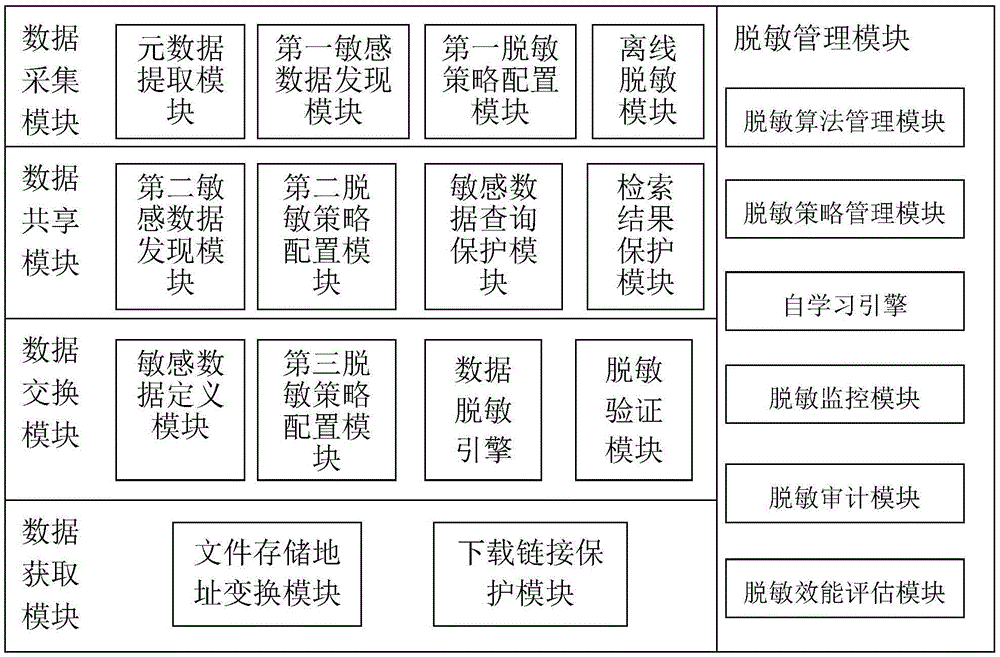
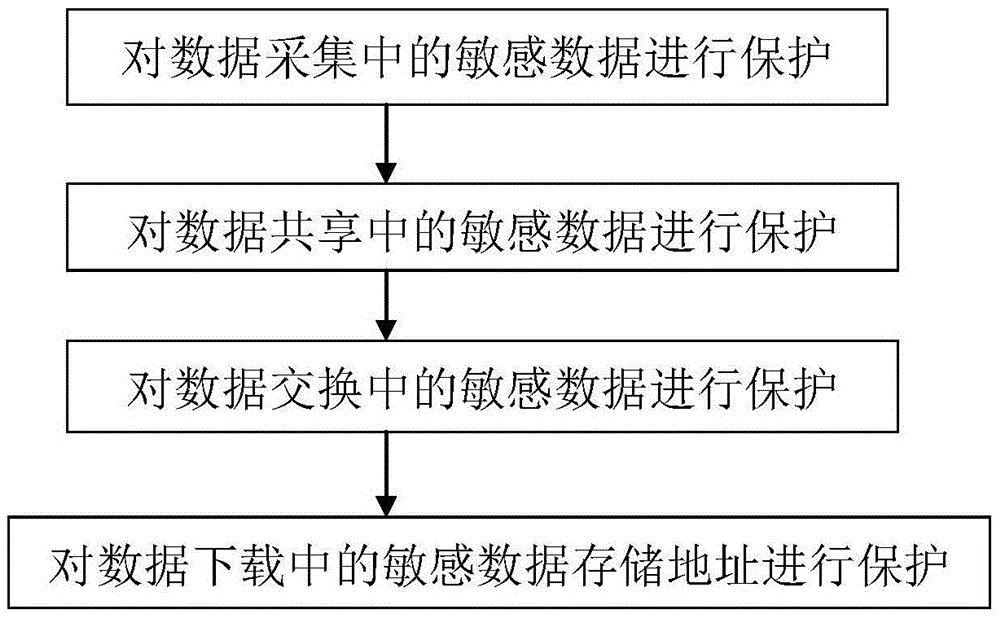
[0072] like figure 1 As shown in the figure, a sensitive data protection system for data circulation and transaction of a big data platform of the present invention includes a data acquisition module for discovering and protecting sensitive content during data acquisition, and a data acquisition module for sensitive data in the process of data sharing. A data sharing module that performs protection processing, a data exchange module that configures a desensitization strategy to desensitize relatively sensitive data in the data exchange process, and a data acquisition module that protects data file download links and storage addresses in the data acquisition process, A desensitization management module that manages, monitors and audits the desensitization and protection of sensitive data.
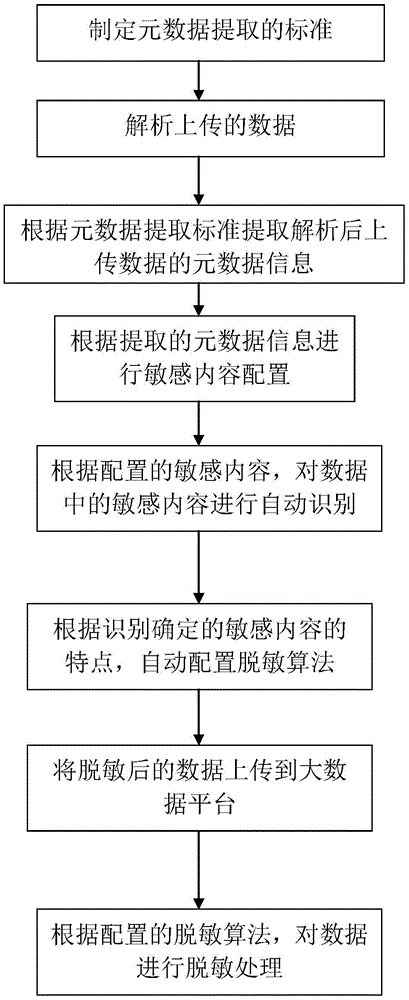
[0073] The data collection module...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com