Decentralizing login methods and clients and system
A decentralization and login method technology, applied in transmission systems, electrical components, etc., can solve the problems of centralized server insecurity and single communication channel
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
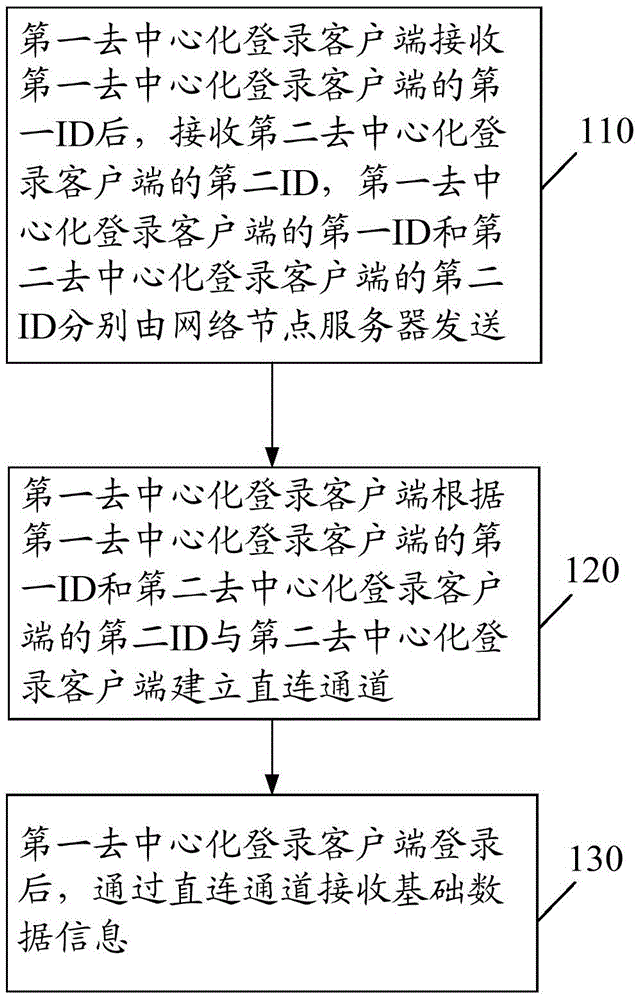
[0065] figure 1 It is the decentralized login method provided by Embodiment 1 of the present disclosure. Such as figure 1 As shown, the decentralized login method is the decentralized login method of the first decentralized login client in the decentralized login system, including:
[0066] Step 110: After receiving the first ID of the first decentralized login client, the first decentralized login client receives the second ID of the second decentralized login client, and the first ID of the first decentralized login client The ID and the second ID of the second decentralized login client are respectively sent by the network node server.
[0067] Before step 110, the first decentralized login client starts, accesses the network node server (NetworkNodeServer, NNS), and establishes a direct connection channel with the network node server. Wherein, the network node server is a network node (NetworkNode) server in a network architecture (SystemsNetworkArchitecture, SNA). Net...
Embodiment 2
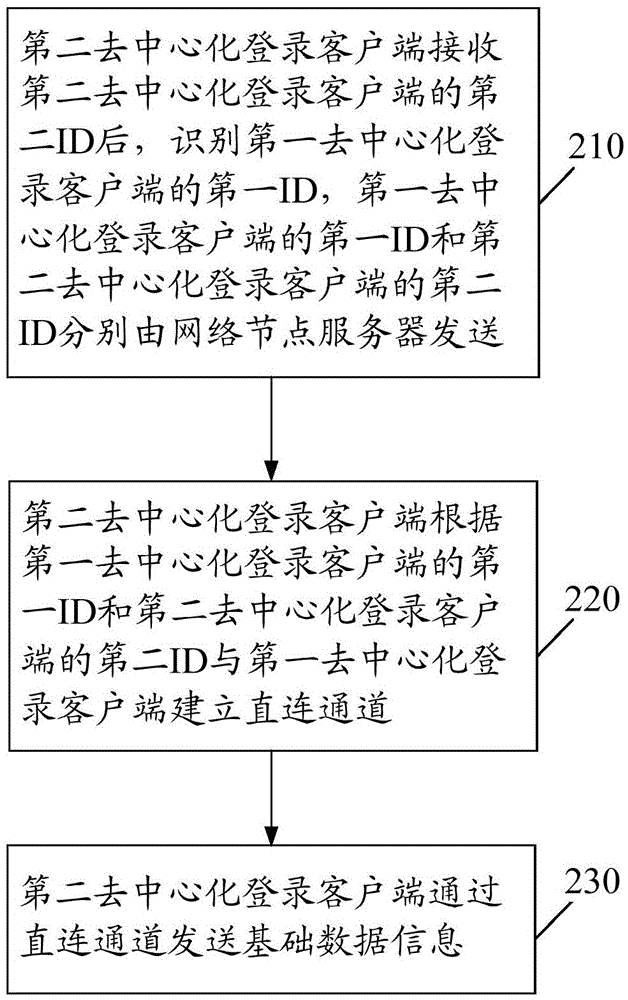
[0093] figure 2 It is a schematic flowchart of another decentralized login method provided by Embodiment 2 of the present disclosure. Such as figure 2 As shown, the decentralized login method is the decentralized login method of the second decentralized login client in the decentralized login system, including:
[0094] Step 210: After receiving the second ID of the second decentralized login client, the second decentralized login client identifies the first ID of the first decentralized login client, and the first ID of the first decentralized login client The ID and the second ID of the second decentralized login client are respectively sent by the network node server.
[0095] Before step 210, the second decentralized login client starts, accesses the network node server and establishes a direct connection channel with the network node server. The network node servers accessed by the second decentralized login client are dynamically assigned randomly, that is, the netw...
Embodiment 3
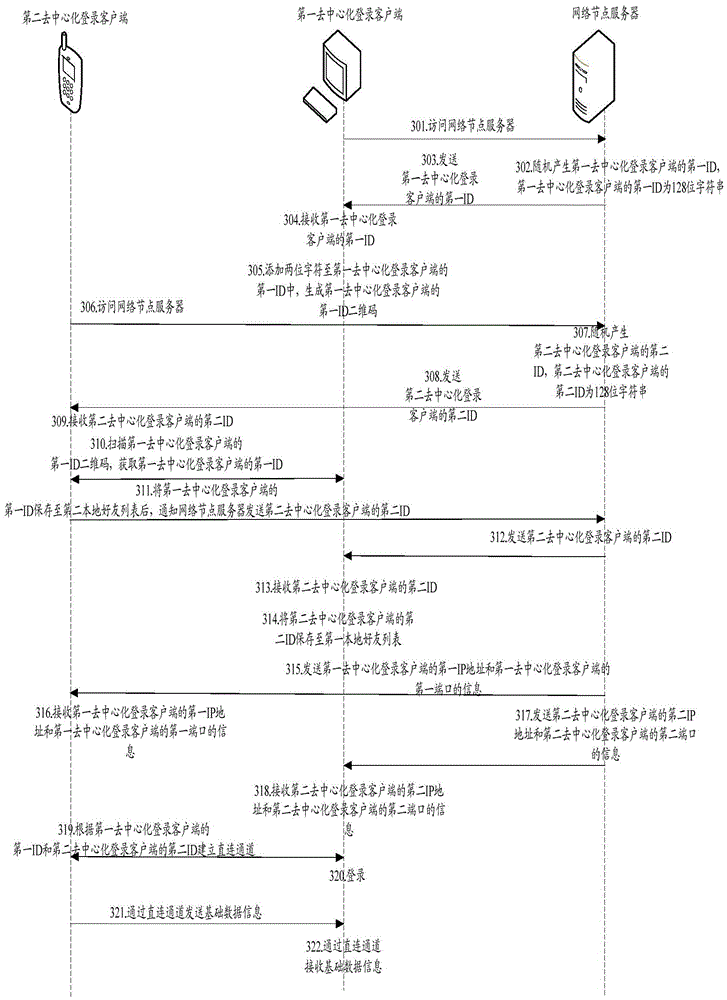
[0112] image 3 It is a schematic diagram of the implementation flow of the decentralized login method provided by Embodiment 3 of the present disclosure. Such as image 3 As shown, the decentralized login methods include:
[0113] Step 301: the first decentralized login client accesses the network node server;
[0114] Step 302: the network node server randomly generates the first ID of the first decentralized login client, and the first ID of the first decentralized login client is a 128-bit character string;
[0115] Step 303: the network node server sends the first ID of the first decentralized login client to the first decentralized login client;
[0116] Step 304: the first decentralized login client receives the first ID of the first decentralized login client;
[0117] Step 305: the first decentralized login client adds two characters to the first ID of the first decentralized login client, and generates a QR code for the first ID of the first decentralized login c...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com