Patents
Literature
37results about How to "Fix leaked technical issues" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
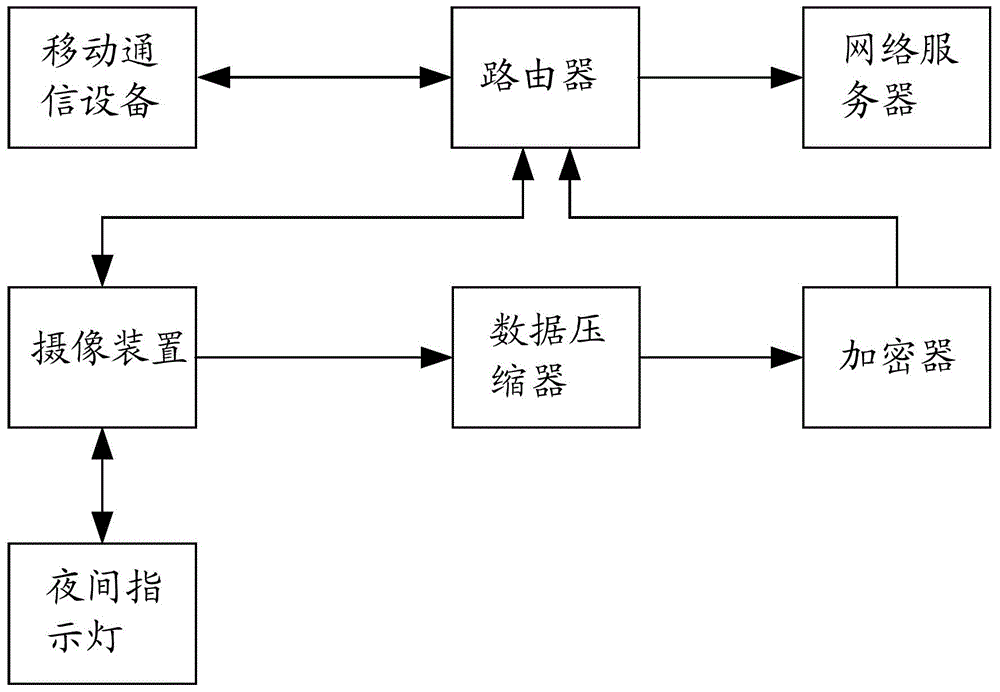
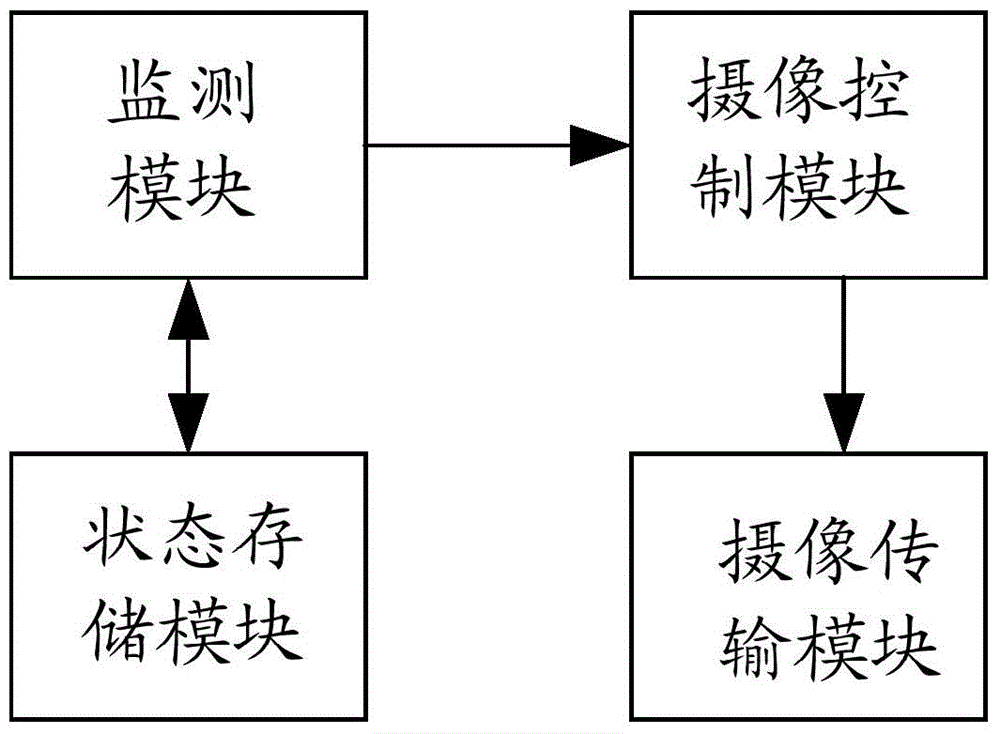
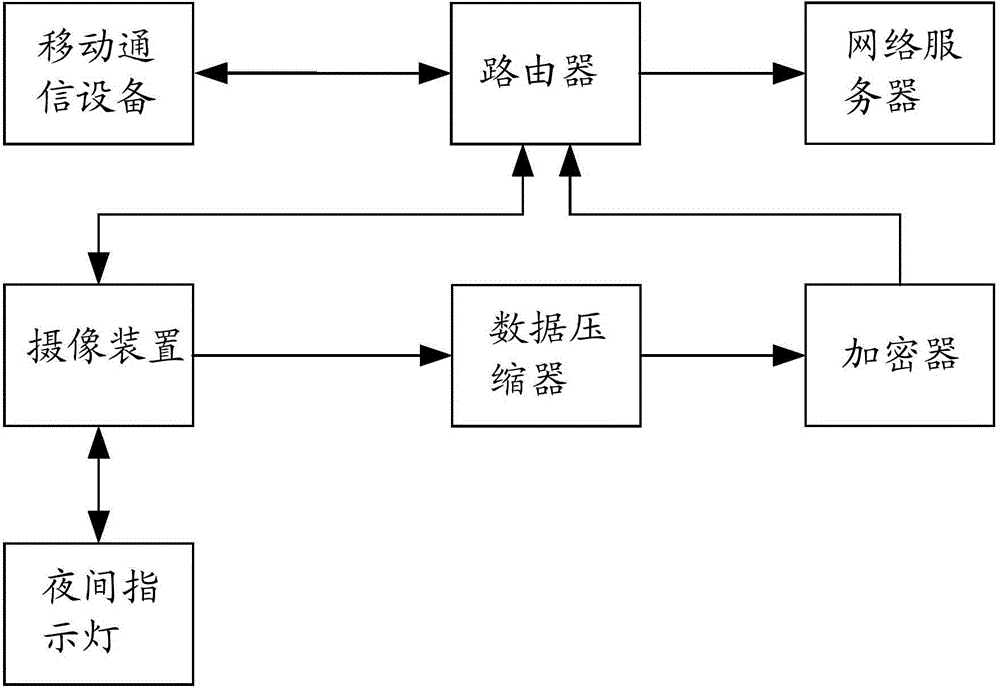
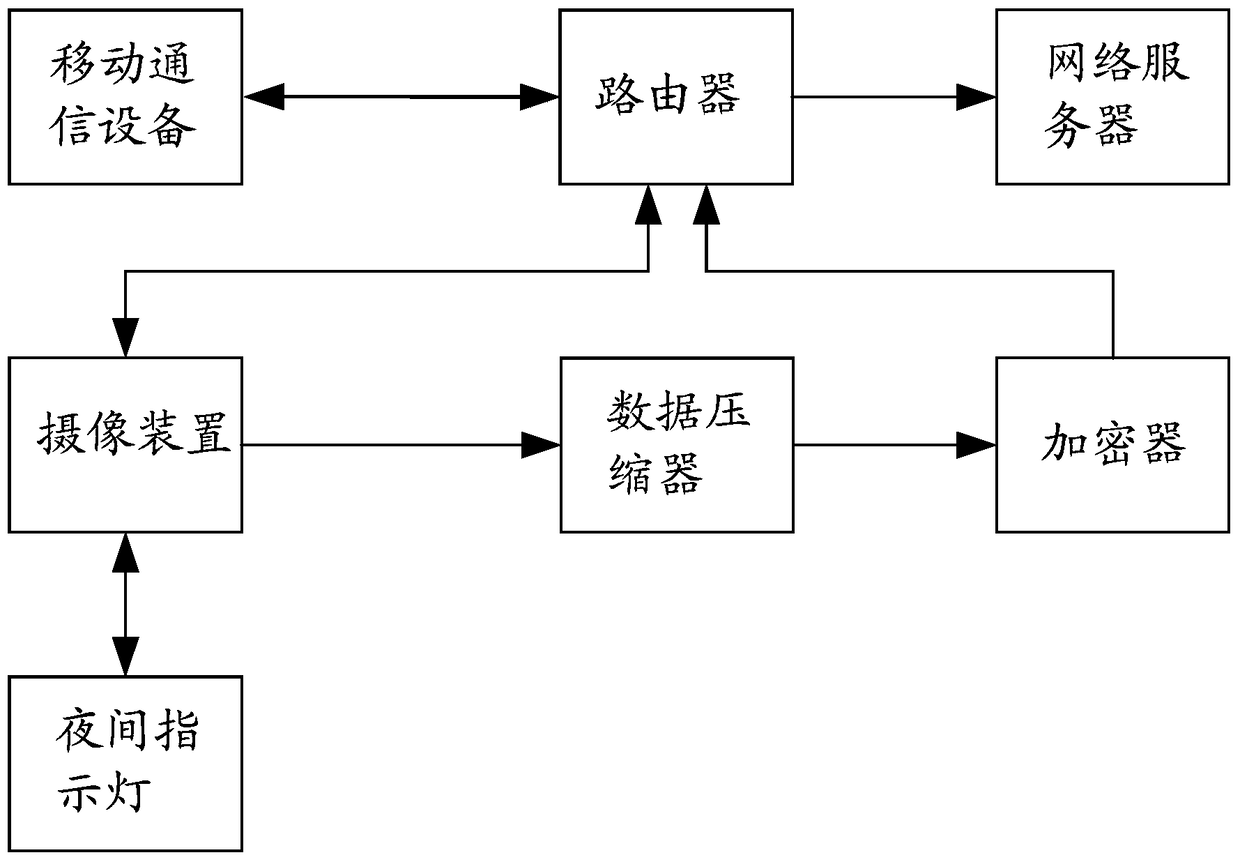
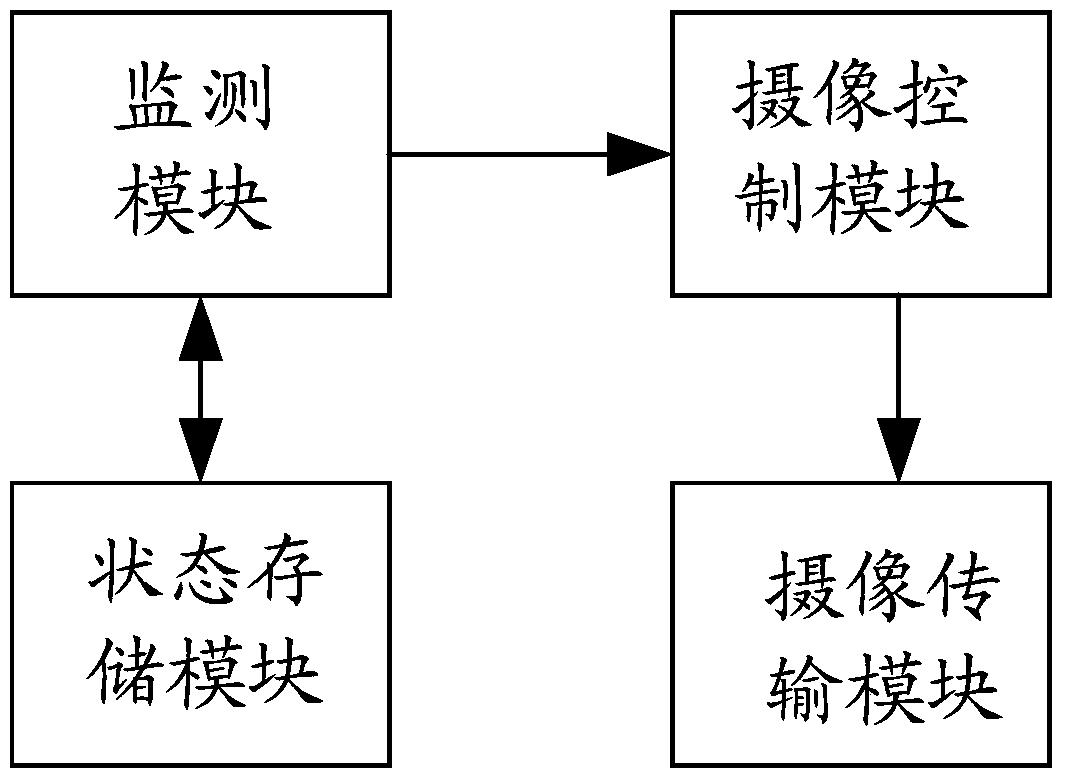
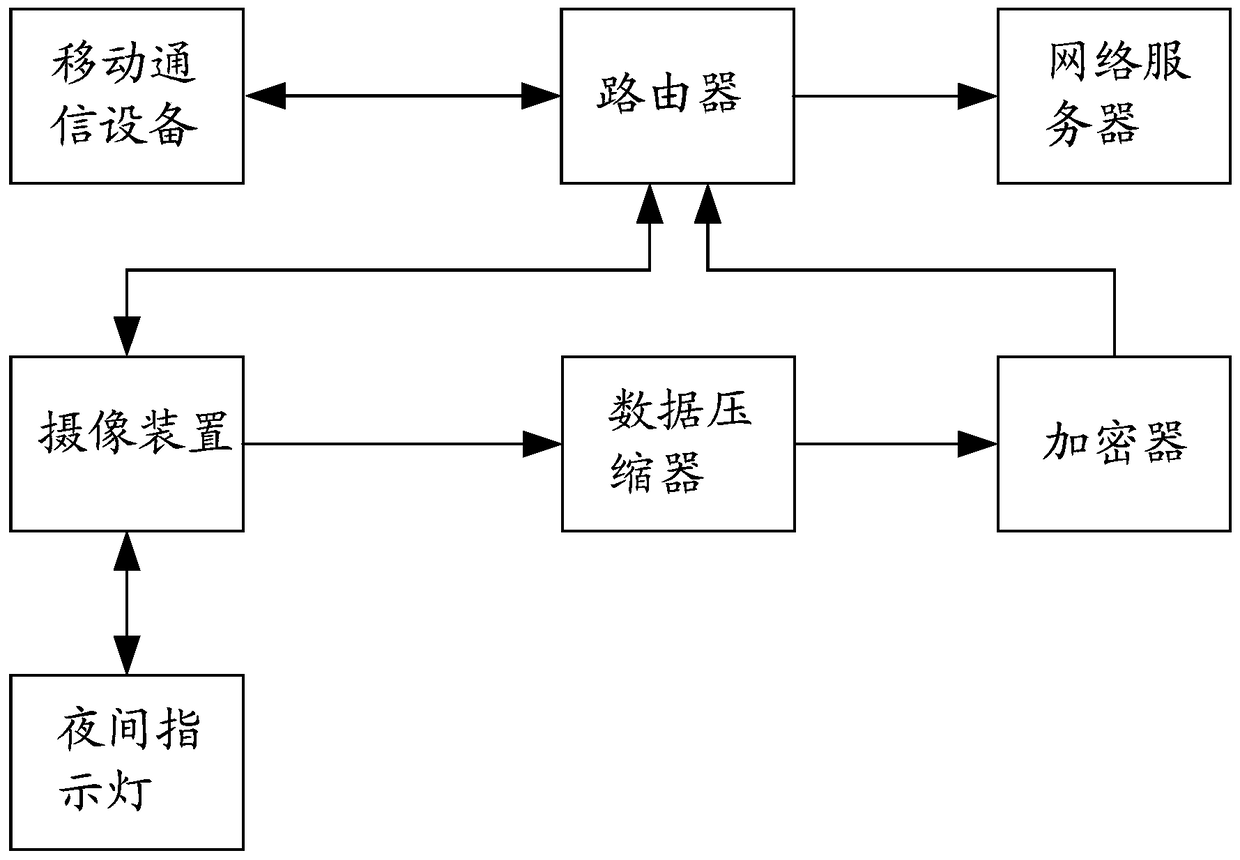
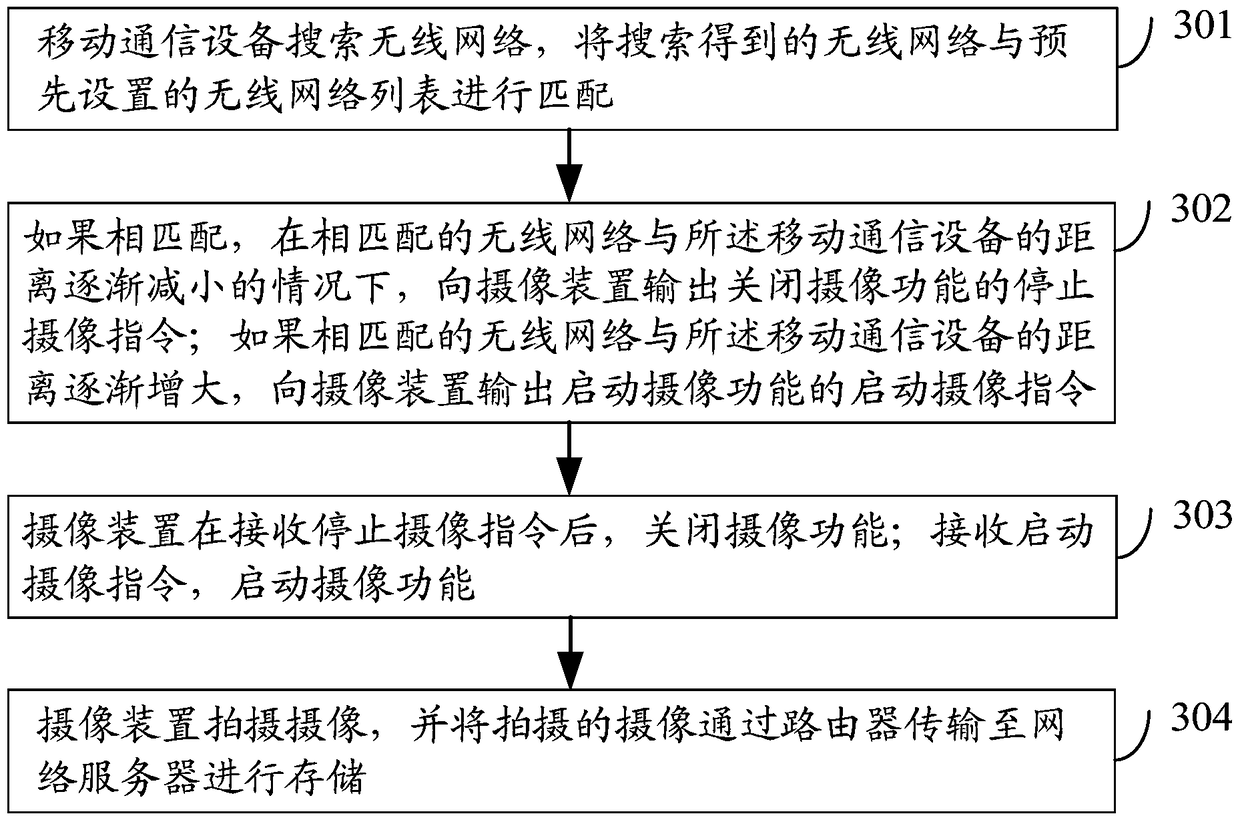
Mobile communication equipment, video monitoring system and video monitoring method
ActiveCN104093007AFix leaked technical issuesPrevent leakageClosed circuit television systemsTransmissionVideo monitoringWireless mesh network
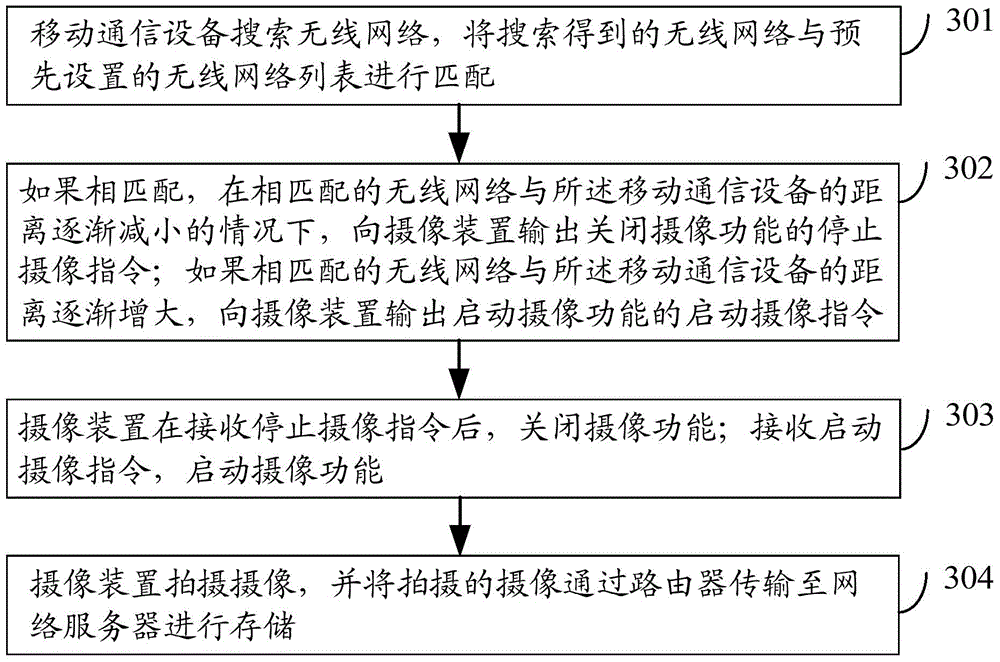
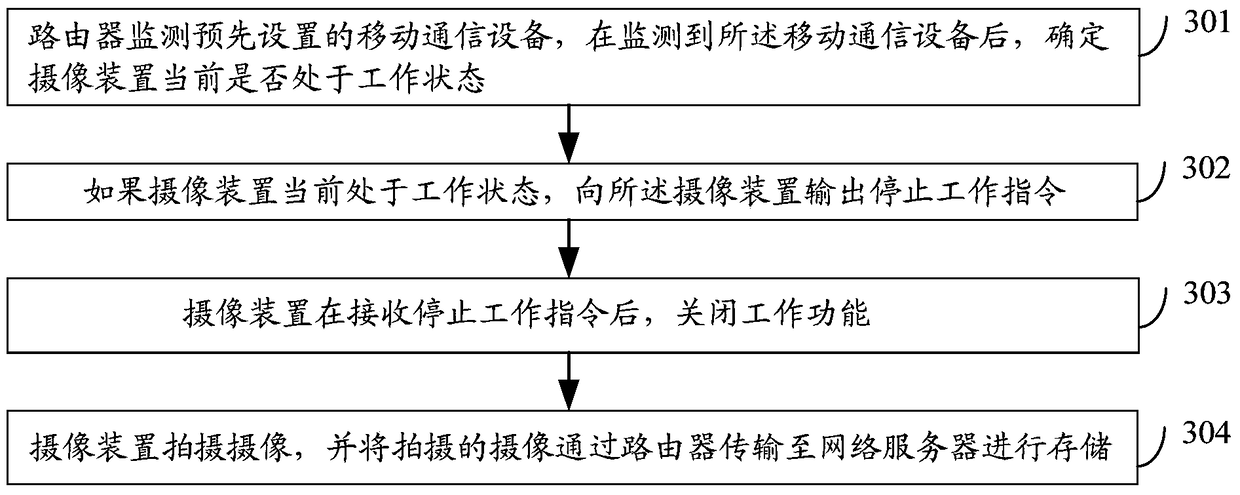
The invention discloses mobile communication equipment, a video monitoring system and a video monitoring method. The method comprises the steps that the mobile communication equipment searches a wireless network and matches the searched wireless network with a preset wireless network list; if the searched wireless network is matched with the preset wireless network list, the mobile communication equipment outputs a working stop command for closing the working function to an image pick-up device in the matched wireless network; the image pick-up device closes the working function after receiving the working stop command. By applying the mobile communication equipment, the video monitoring system and the video monitoring method, leakage of privacy information of users can be avoided and safety monitoring can be realized.
Owner:BEIJING QIHOO TECH CO LTD
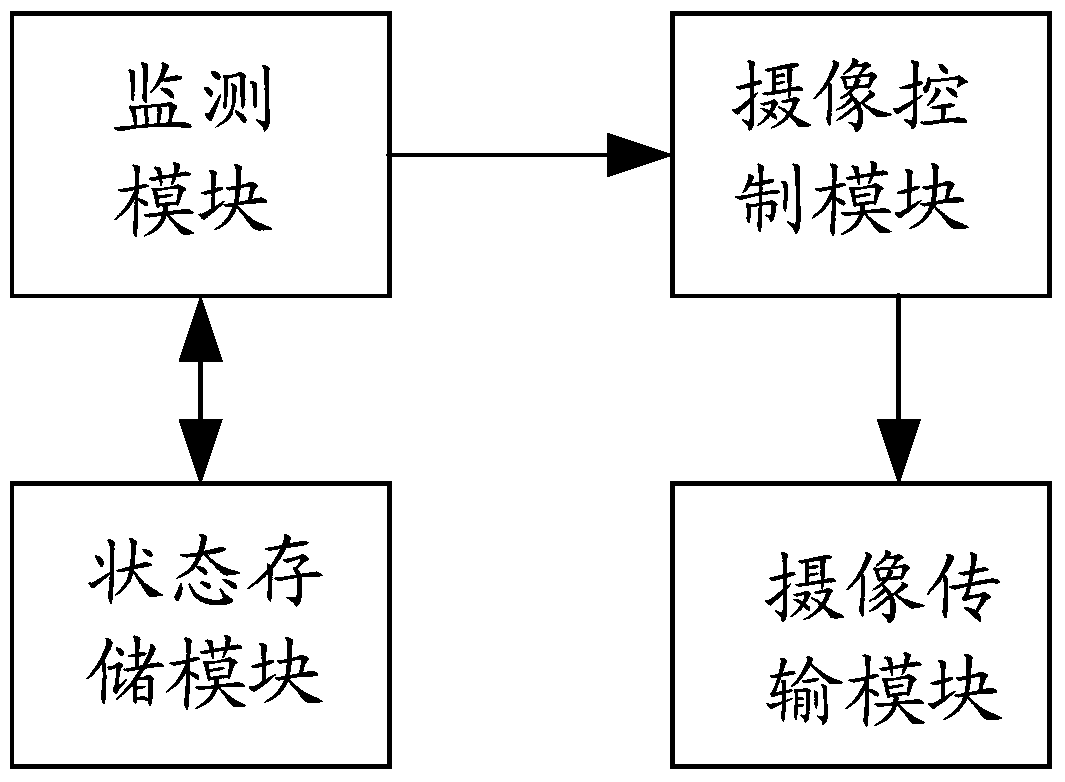
Image pick-up device, video monitoring system and video monitoring method
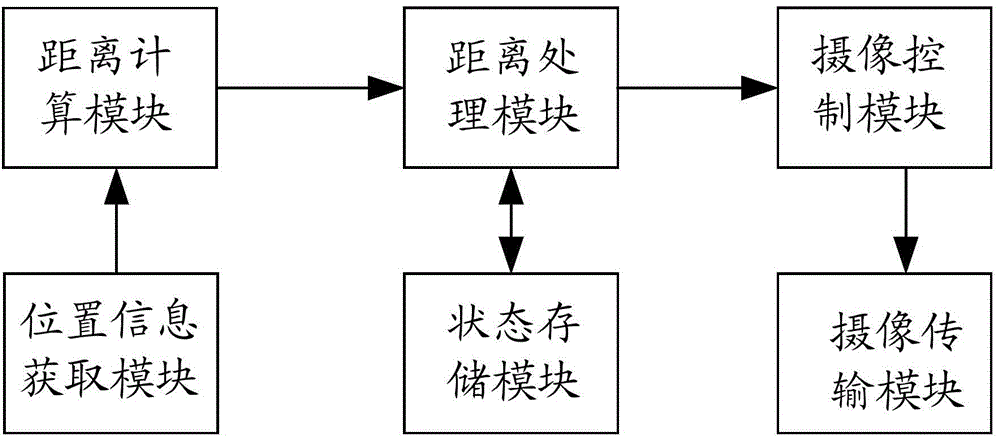
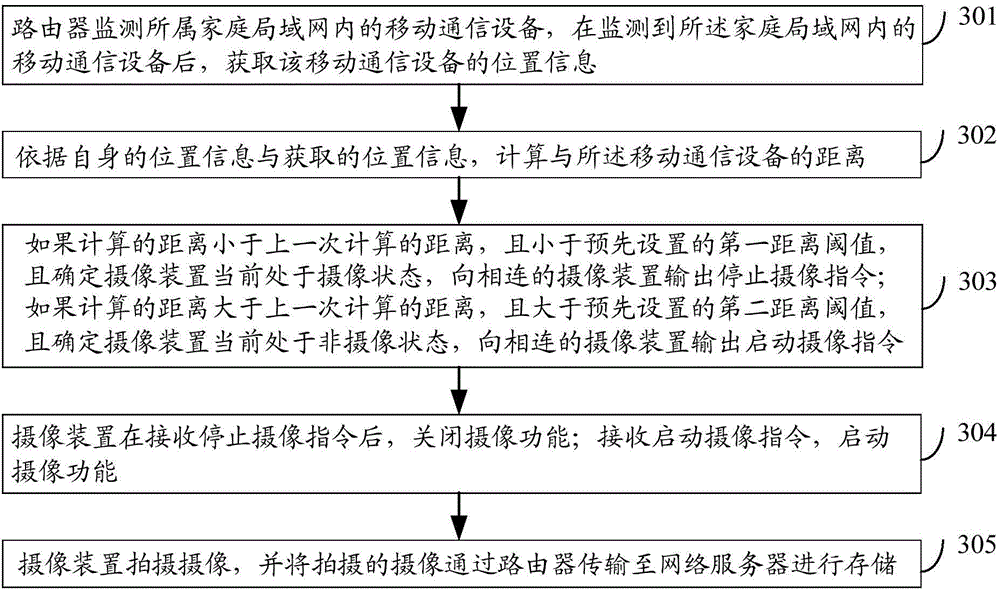
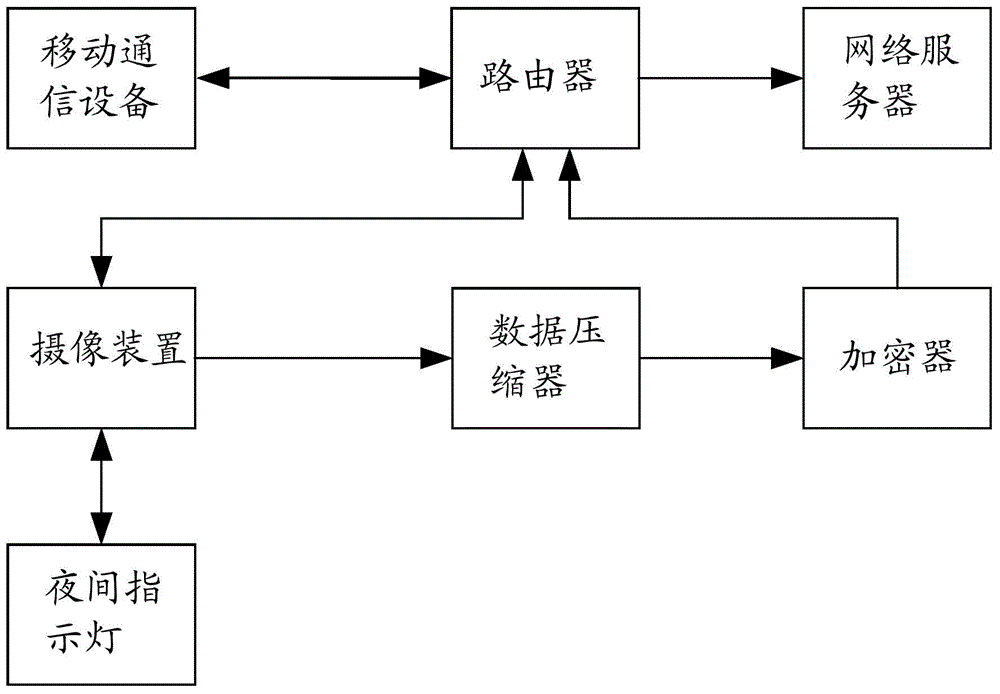
ActiveCN104093008AFix leaked technical issuesPrevent leakageTelevision system detailsColor television detailsVideo monitoringSafety monitoring
The invention discloses an image pick-up device, a video monitoring system and a video monitoring method. The method comprises the steps that a router monitors mobile communication equipment in a wireless network to which the router belongs and the router obtains the location information of the mobile communication equipment after the mobile communication equipment is monitored; the router computes the distance to the mobile communication equipment according to the location information of the router and the obtained location information; the router outputs an image pick-up stop command to an image pick-up device connected with the router if the distance is smaller than the distance computed last time and is smaller than a first distance threshold and the image pick-up device is confirmed to be in an image pick-up state at present; the router outputs an image pick-up start command to the image pick-up device connected with the router if the distance is more than the distance computed last time and is more than a second distance threshold and the image pick-up device is confirmed not to be in an image pick-up state at present; the image pick-up device closes the image pick-up function after receiving the image pick-up stop command; the image pick-up device starts the image pick-up function after receiving the image pick-up command. By applying the image pick-up device, the video monitoring system and the video monitoring method, leakage of privacy information of users can be avoided and safety monitoring can be realized.
Owner:BEIJING QIHOO TECH CO LTD
Camera-shooting device, video monitoring system and video monitoring method
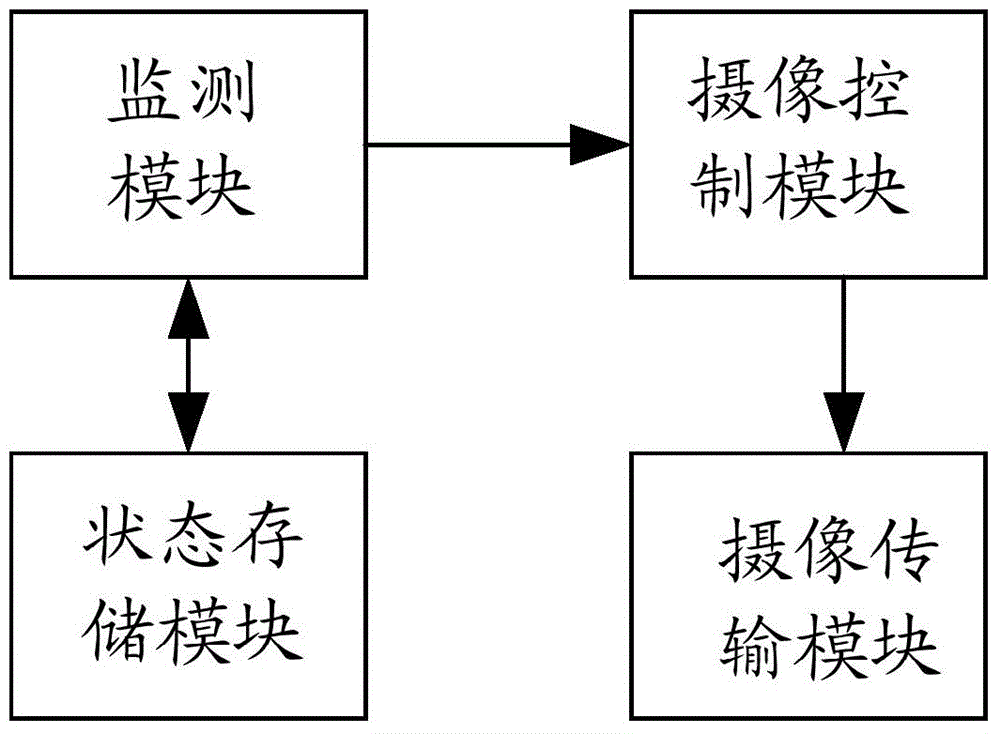
ActiveCN104159076AFix leaked technical issuesPrevent leakageTelevision system detailsColor television detailsVideo monitoringWork function
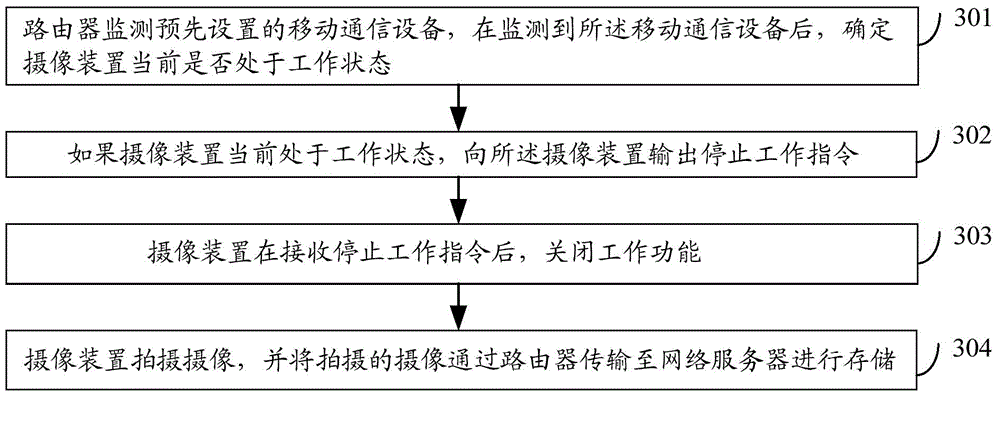
The invention discloses a camera-shooting device, a video monitoring system and a video monitoring method. The method comprises the steps as follows: firstly, a router is adopted for monitoring a designated mobile communication device, and after the mobile communication device is monitored, if being kept in the working state currently, the camera-shooting device outputs an operation stopping instruction; secondly, when no mobile communication device arranged in advance is monitored, if being kept in the non-working state currently, the camera-shooting device outputs an operation starting instruction; thirdly, the camera-shooting device stops the working function after receiving the operation stopping instruction; fourthly, the camera-shooting device starts the working function after receiving the operation starting instruction. Through utilizing the camera-shooting device, the video monitoring system and the video monitoring method, the private information leakage of a user is avoided, and the security monitoring and control are realized.
Owner:BEIJING QIHOO TECH CO LTD
Display method and electronic equipment
InactiveCN104333811AImprove the accuracy of judgmentImprove securityDigital data protectionInternal/peripheral component protectionComputer hardwareDisplay device
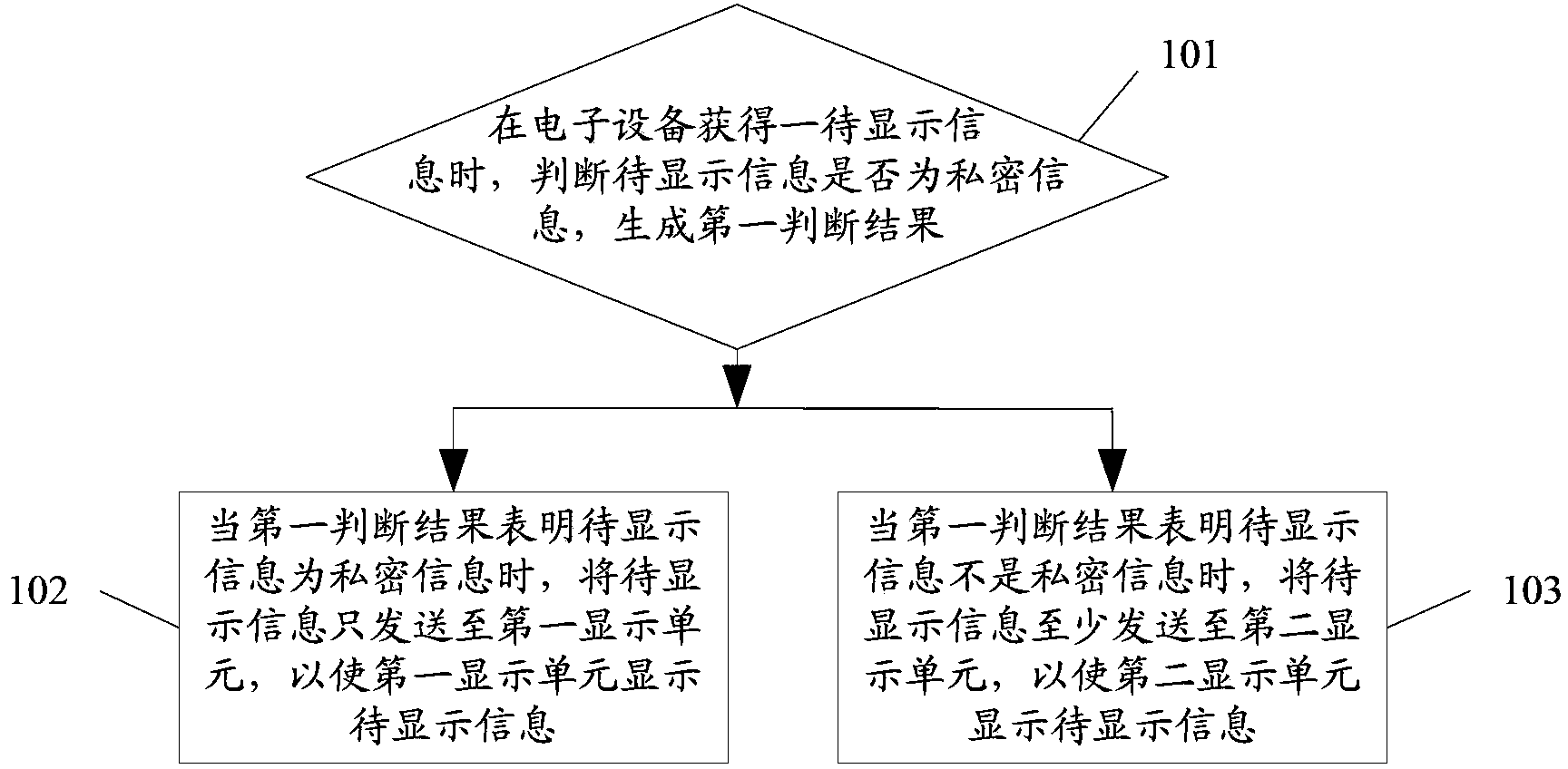
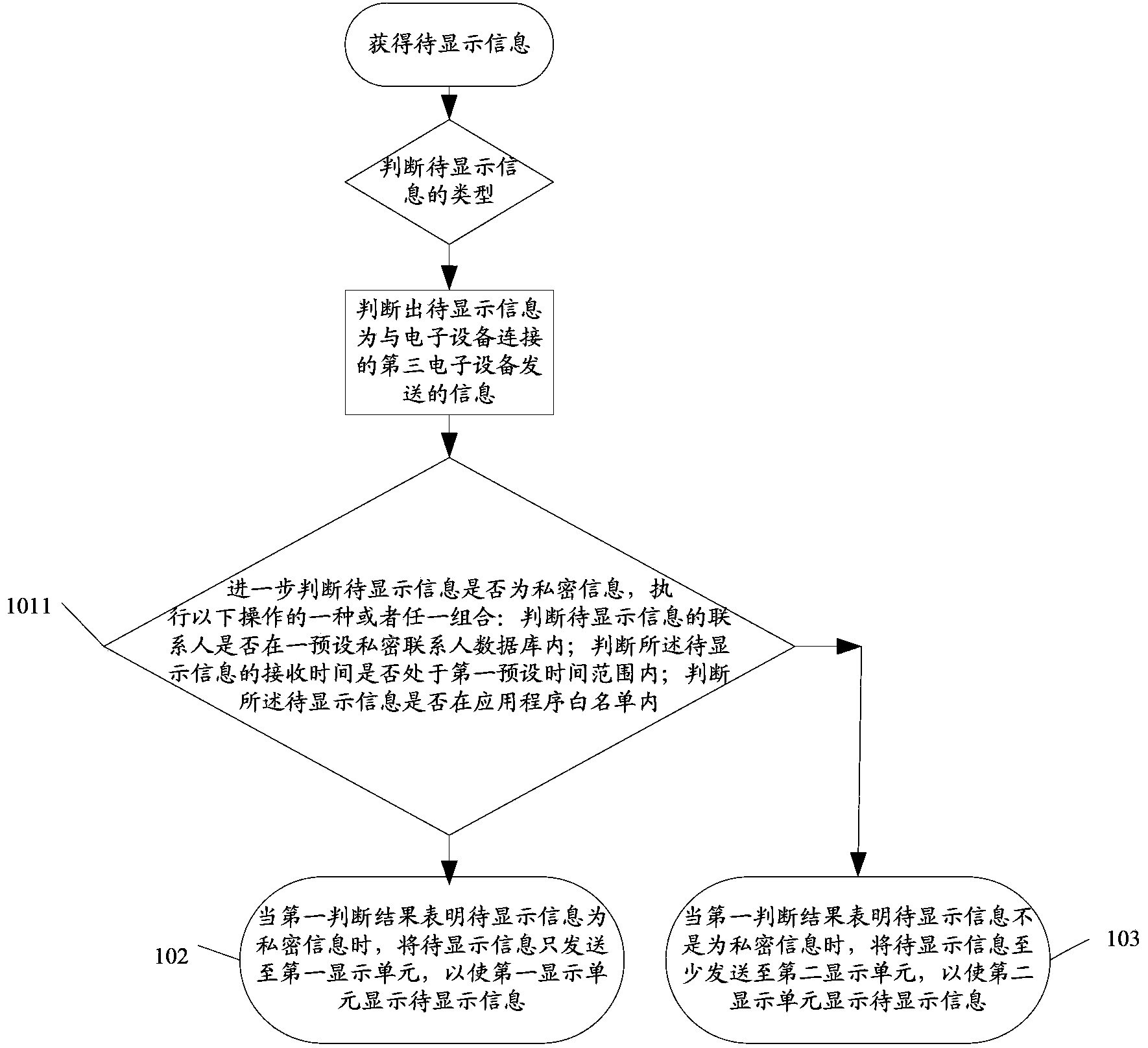
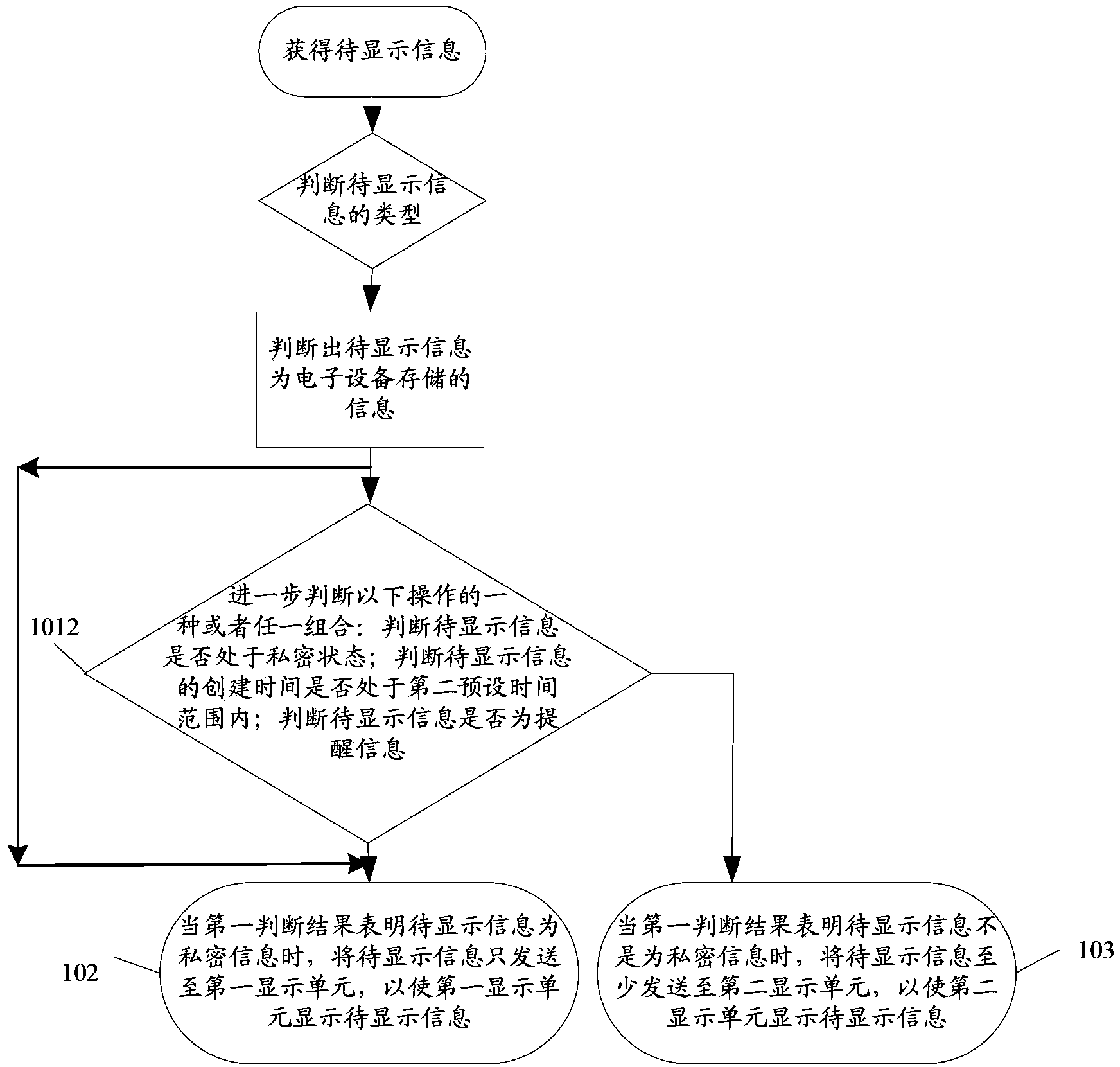
The present invention discloses a display method and an electronic device. The method is applicable to an electronic device, the electronic device is capable of data transmission with a display device, the electronic device includes a first display unit, and the display device includes a second display unit; and the method includes: when the electronic device obtains information needing to be displayed, determining whether the information needing to be displayed is private information and generating a first determination result; in a case that the information needing to be displayed is private information, transmitting the information needing to be displayed to the first display unit only; and in a case that the information needing to be displayed is not private information, transmitting the information needing to be displayed at least to a second display unit.
Owner:LENOVO (BEIJING) LTD
Processing box
InactiveCN101581910ASolve technical problems prone to leakage from sliding elementsFix leaked technical issuesElectrographic process apparatusButt jointMaterials science
The invention discloses a processing box. The processing box comprises a powder cylinder for containing carbon powder, a sliding element which can freely slide in the powder cylinder and a sliding element retaining mechanism which leads the sliding element to close a powder outlet at non-using state, wherein a powder outlet part is arranged on the powder cylinder, the powder outlet is formed on the powder outlet part, when in the non-using state, the sliding element closes the powder outlet under the action of the sliding element retaining mechanism; when in using state, the sliding element is moved under the action of external force for opening the powder outlet, an internal element with an internal powder feed inlet is further arranged in the powder outlet part, the internal element and the powder outlet part form a certain space, the sliding element can slide in the space formed by the powder outlet part and the internal element, and the internal powder feed inlet of the internal element is butt-jointed with the powder outlet. As the processing box increases the internal element for re-sealing, the carbon powder can not be leaked out, thereby solving the technical problem that the carbon powder is easy to leak from the sliding element due to the existence of a gap between the sliding element and the powder part of the prior processing box.
Owner:ZHUHAI SEINE TECH CO LTD
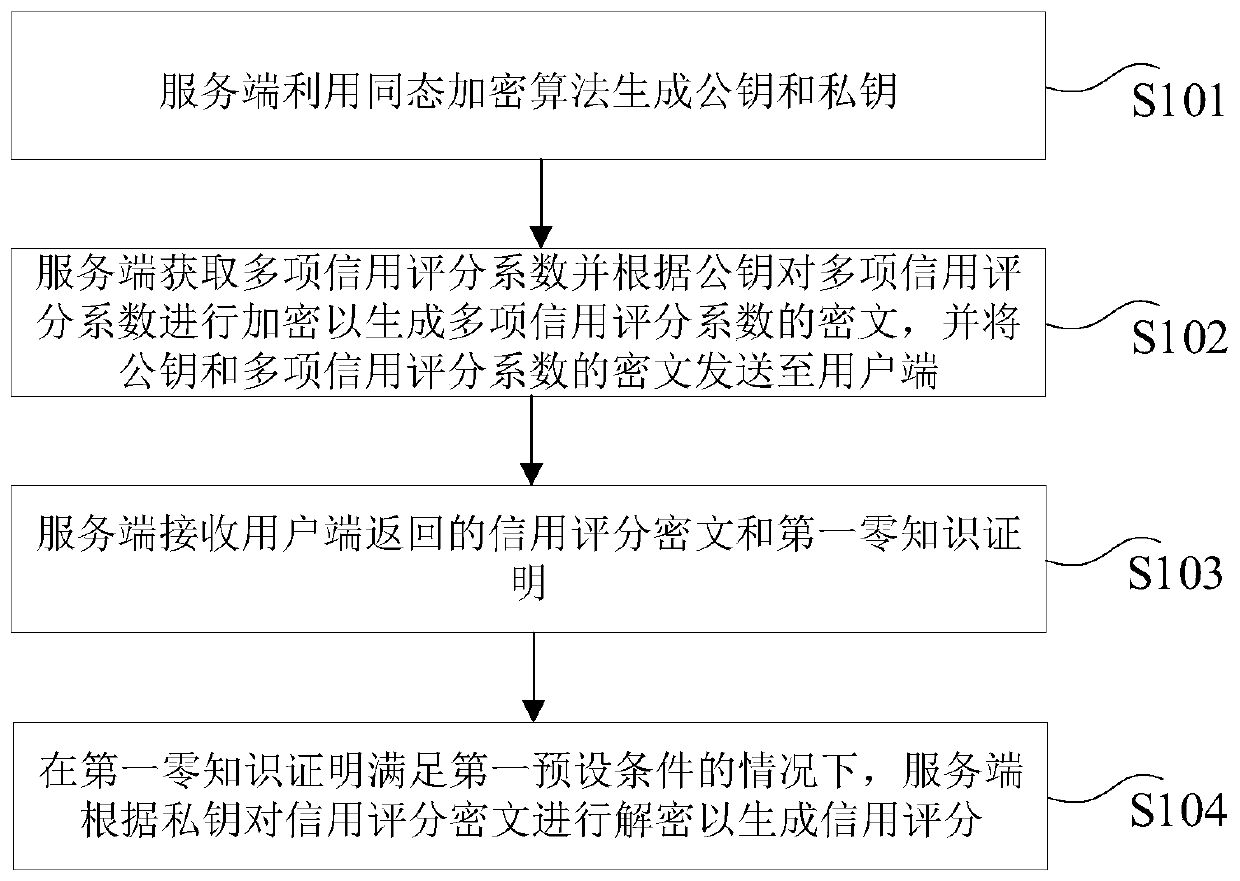
Credit score generation method and device, computer equipment and storage medium
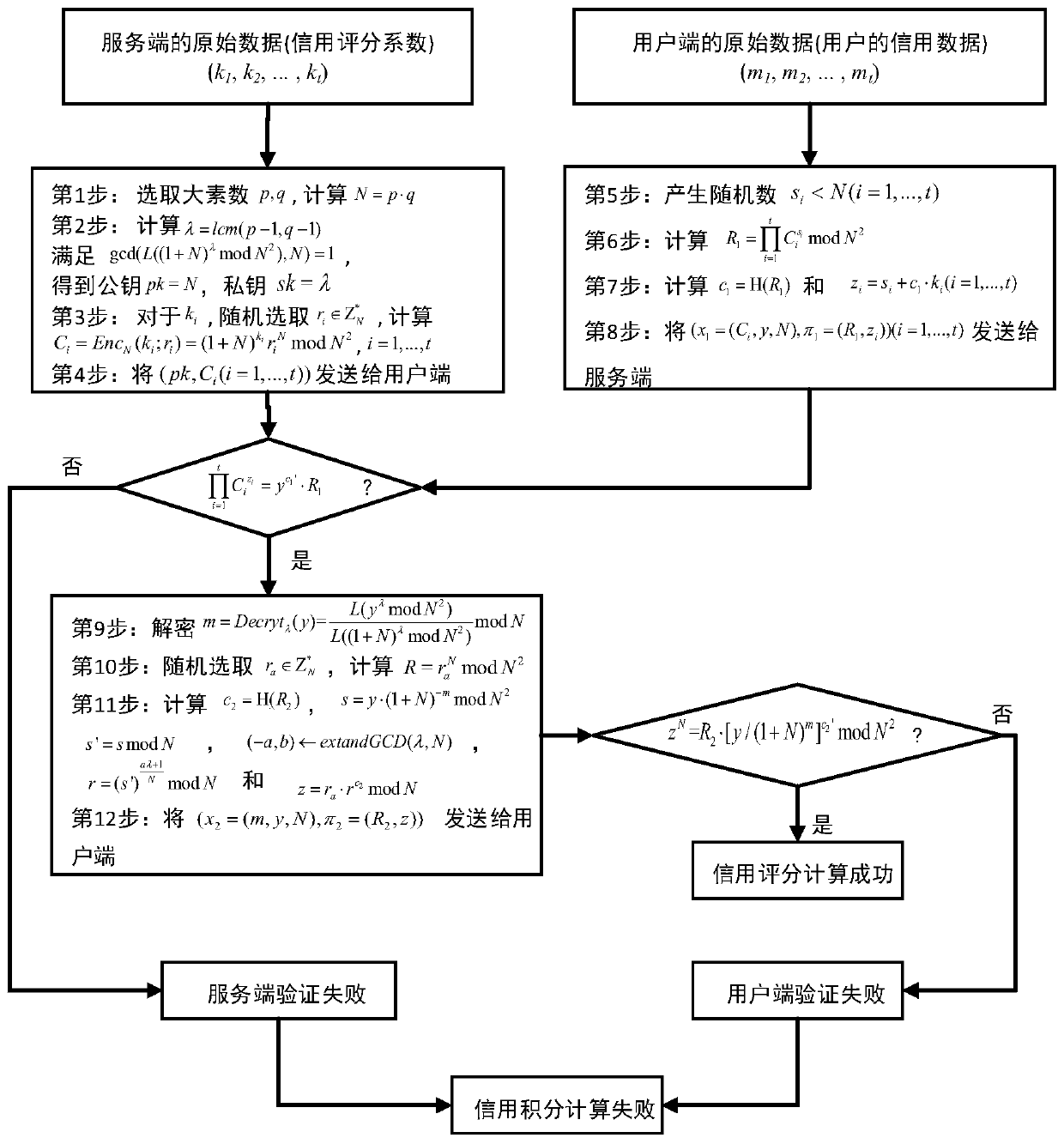
ActiveCN109818752ARealize privacy protectionIncrease credibilityPublic key for secure communicationUser identity/authority verificationCiphertextPrivacy protection
The invention provides a credit score generation method and device, computer equipment and a storage medium, and the method comprises the steps that a server generates a public key and a private key through a homomorphic encryption algorithm; The server side obtains the multiple credit scoring coefficients and encrypts the multiple credit scoring coefficients according to the public key to generate a ciphertext of each credit scoring coefficient in the multiple credit scoring coefficients, and sends the public key and the ciphertext of the multiple credit scoring coefficients to the user side;The server side receives the credit scoring ciphertext and the first zero knowledge proof returned by the user side; And under the condition that the first zero knowledge proof satisfies a first preset condition, the server decrypts the credit scoring ciphertext according to the private key to generate a credit score. According to the scheme, the technical problem of user sensitive data leakage in an existing credit score generation method is solved, and the technical effect of effectively protecting the privacy of the user credit data of the user side is achieved.
Owner:JUZIX TECH SHENZHEN CO LTD +1
Page generation method and device and electronic device
ActiveCN110197053APrevent easy color reversalImprove stabilityProgram/content distribution protectionMultiple layerInformation retrieval
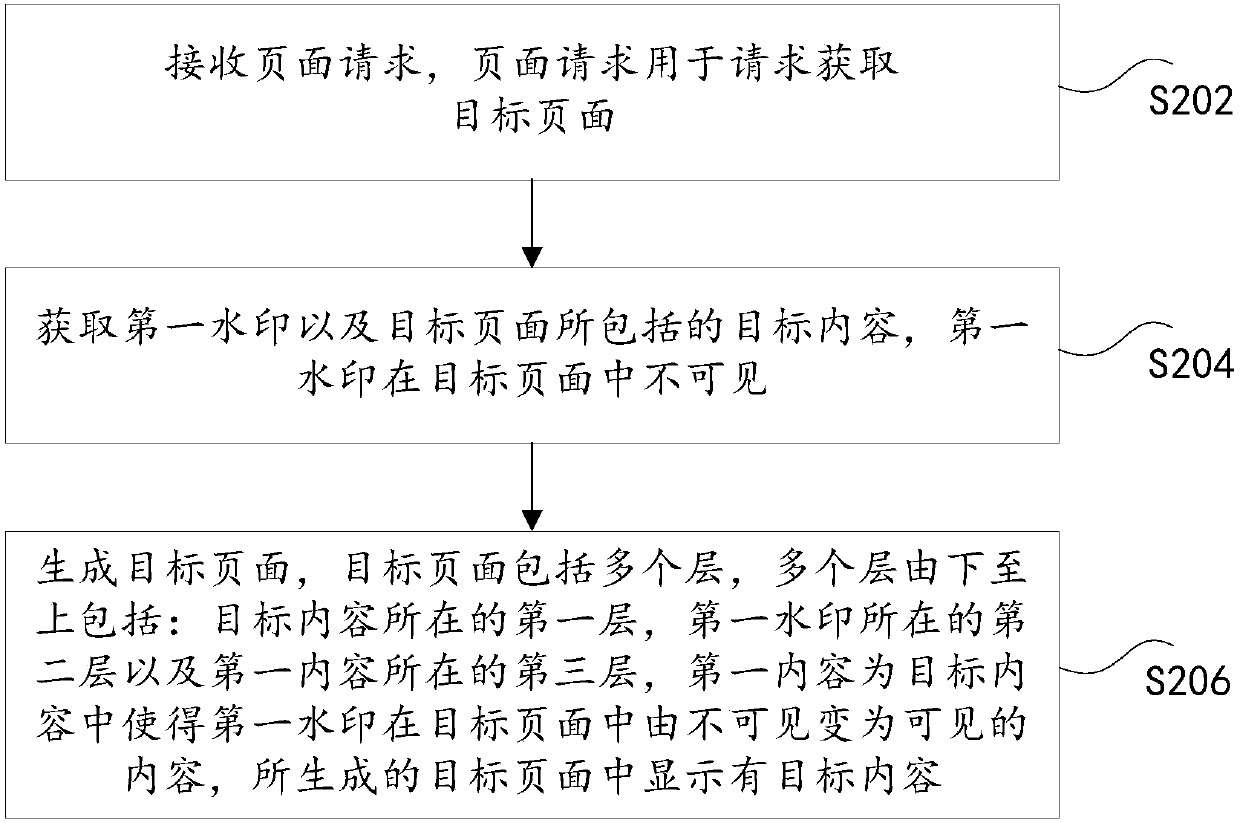
The invention discloses a page generation method and device and an electronic device. The method comprises: receiving a page request, and the page request being used for requesting to obtain a targetpage; obtaining a first watermark and target content included in the target page, the first watermark being invisible in the target page; generating a target page, wherein the target page comprises aplurality of layers; wherein the multiple layers comprise the first layer where the target content is located, the second layer where the first watermark is located and the third layer where the firstcontent is located from bottom to top, the first content is the content, making the first watermark change from invisible in the target page to visible in the target content, and the target content is displayed in the generated target page. According to the method, the technical problem of hidden watermark leakage caused by easy color reversion of the hidden watermark in the prior art is solved.
Owner:TENCENT TECH (SHENZHEN) CO LTD
Device information deletion method and apparatus
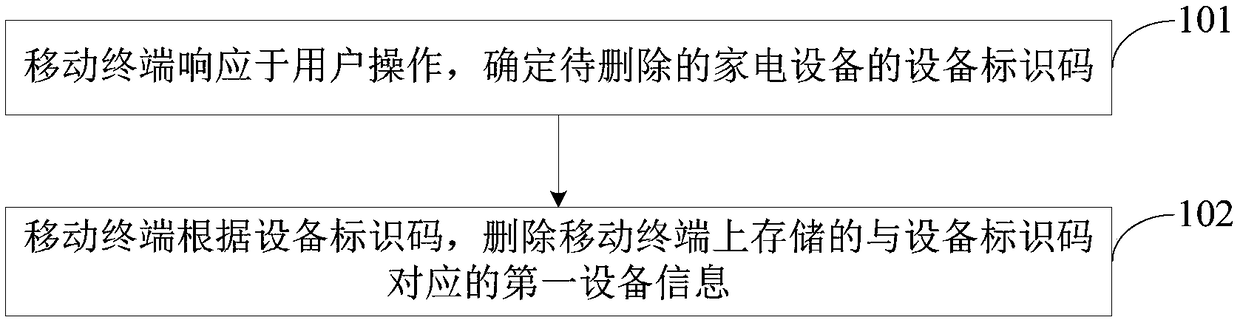
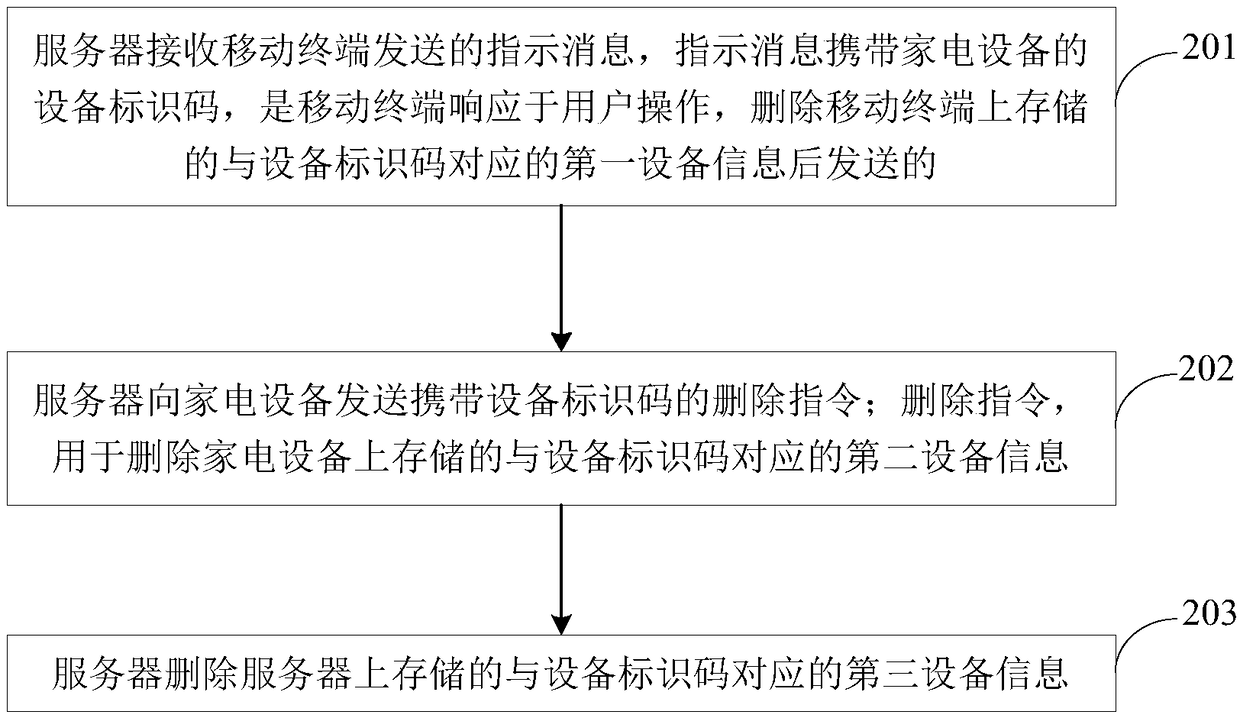
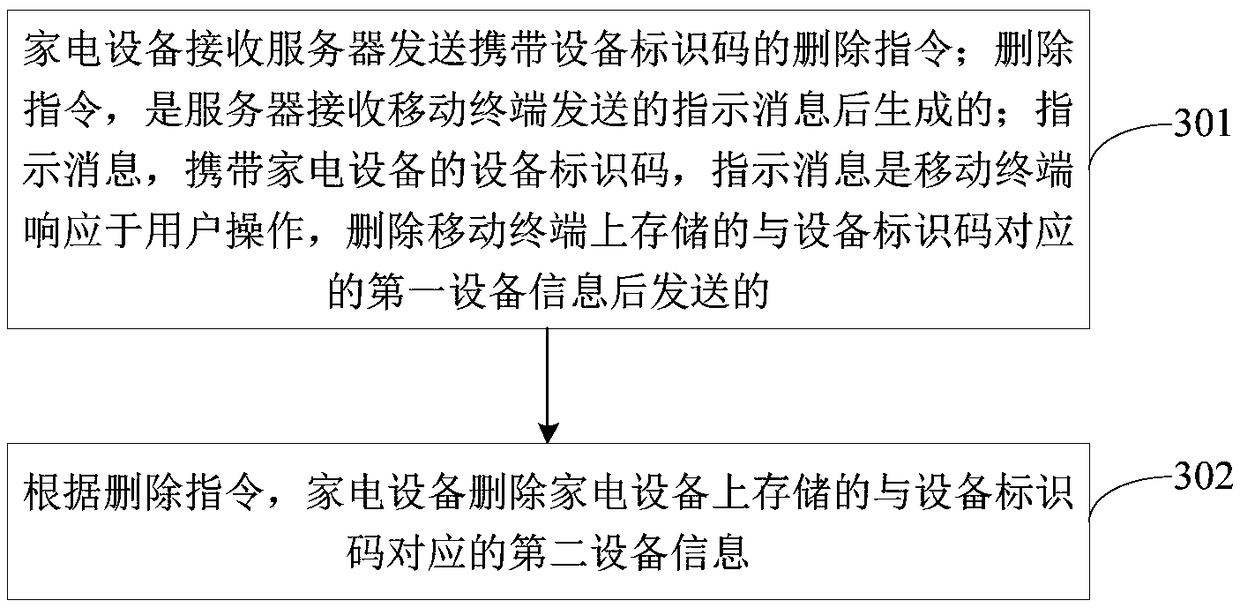
InactiveCN108810110APrevent leakageImprove securityHome automation networksComputer terminalHome appliance
The invention provides a device information deletion method and apparatus. The method comprises the following steps: determining a device identification code of a home appliance to be deleted in response to a user operation through a mobile terminal; and deleting, by the mobile terminal, first device information corresponding to the device identification code stored on the mobile terminal according to the device identification code. According to the method, by deleting the device information stored on the mobile terminal, the home appliance and a server, the technical problems of troublesome operation steps and device information leakage caused by incomplete deletion of the device information in the prior art are solved, and the technical effects of simplifying the user operation, improving the user experience, effectively preventing device information leakage and improving the information security are achieved.
Owner:GD MIDEA AIR-CONDITIONING EQUIP CO LTD
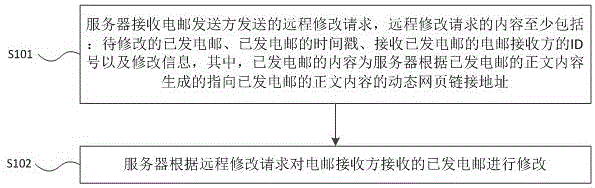
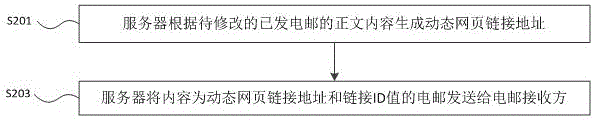
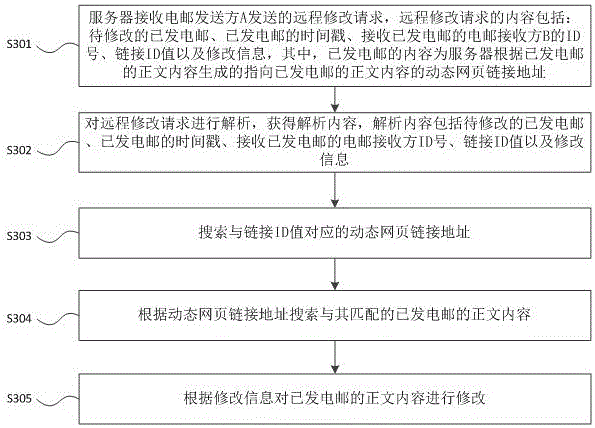
Method for modifying E-mail remotely
InactiveCN105007215AAvoid Embarrassing Situations of RegretFix editing errorsData switching networksTimestampInternet privacy
The invention provides a method for modifying an E-mail remotely. A remote modifying request sent by an E-mail sender is received through a server; the content of the remote modifying request at least comprises the sent E-mail to be modified, the timestamp of the sent E-mail, the ID number of an E-mail receiver which receives the sent E-mail, and modification information, wherein the content of the sent E-mail is a dynamic webpage link address generated by the server according to the text content of the sent E-mail and pointing at the text content of the sent E-mail; the server modifies the sent E-mail received by the E-mail receiver according to the remote modifying request. The technical problem that important or private information is leaked due to that the E-mail is mistakenly edited and cannot be recalled is solved, and the awkwardness due to that the E-mail sender sends the E-mail mistakenly or the E-mail sender regrets after sending the E-mail is effectively avoided.
Owner:陈包容
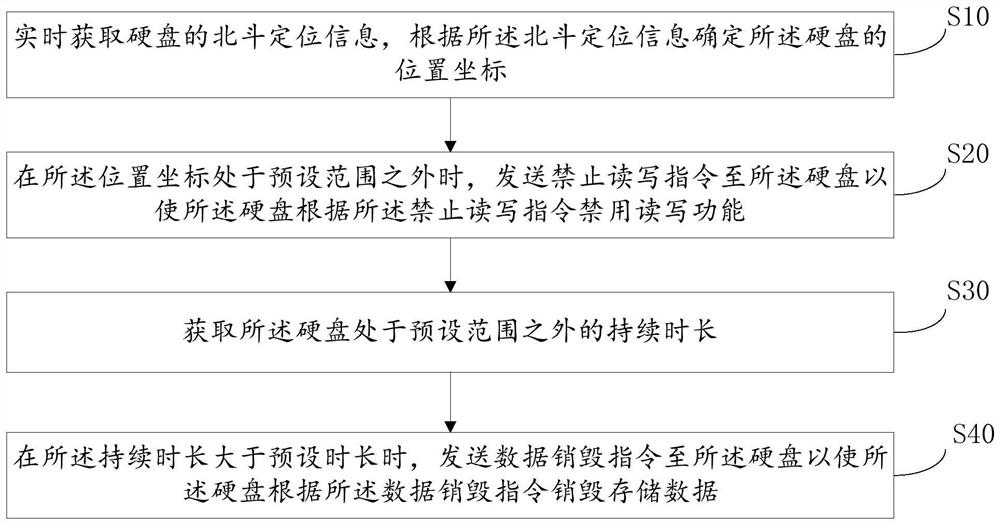
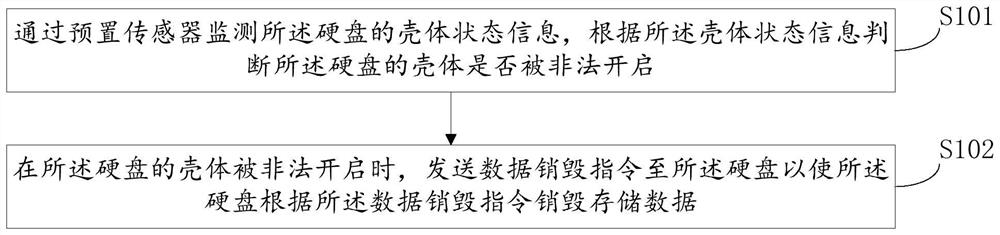
Hard disk protection method and device based on Beidou positioning, equipment and storage medium
ActiveCN113076564AFix leaked technical issuesImprove securityInternal/peripheral component protectionDigital data authenticationData breachEngineering
Owner:山东北斗云信息技术有限公司
Automatic bag removing device for material
PendingCN110641793AResolve Material SpillsReduce manufacturing costBags openingEngineeringControl cell
The invention provides an automatic bag removing device for a material. The automatic bag removing device comprises a bracket, a conveying part, a first clamping part, a second clamping part, a cutting part, a removing part, a driving part, a control unit and a rotating part. The first clamping part is provided with a first position and a second position. The rotating part has an opened state forpreventing the material from passing through and a closed state for enabling the material to pass through. When the first clamping part moves to the second position from the first position, the rotating part is in the opened state. The automatic bag removing device is favorable for separating an outer packaging bag from an inner packaging bag of material and prevents the inner packaging bag from being damaged when the outer packaging bag of the material is removed, so that the work efficiency is improved.
Owner:TIANJIN STANDARD BIOLOGICS CO LTD
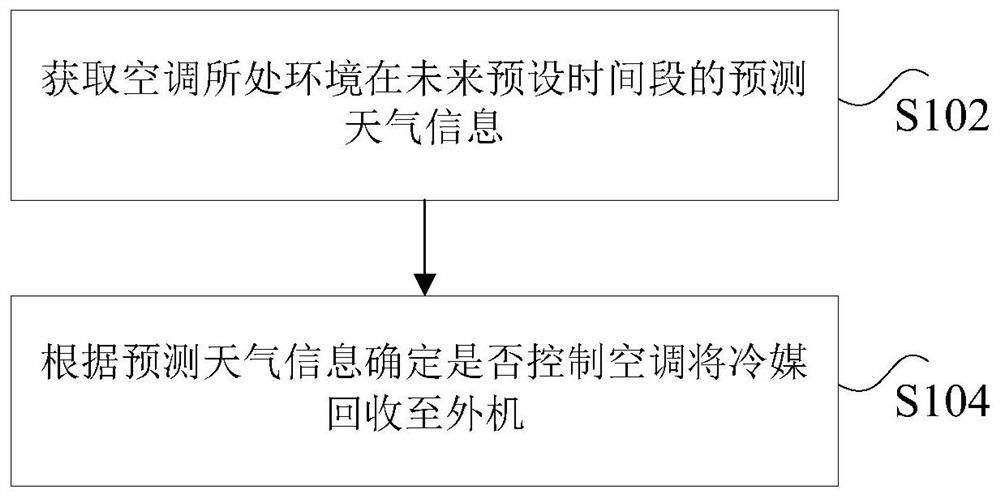
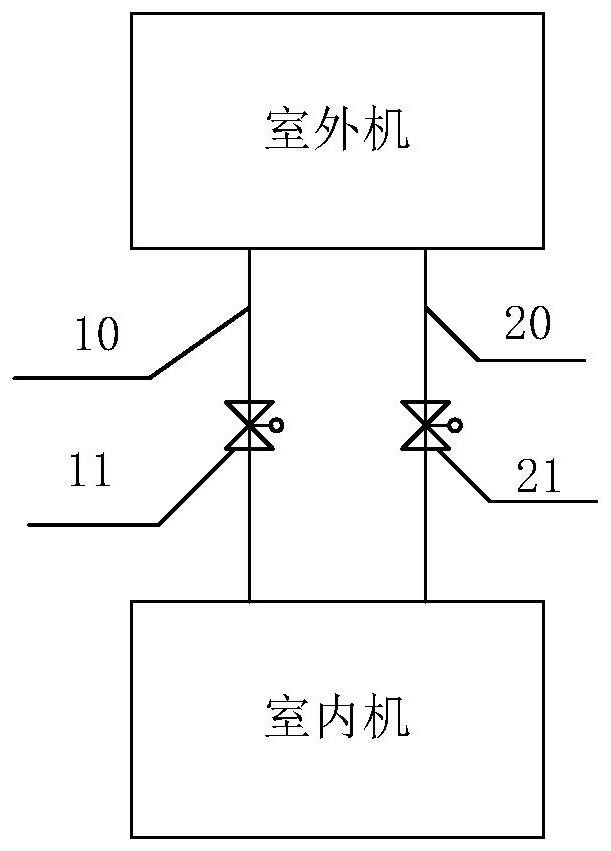
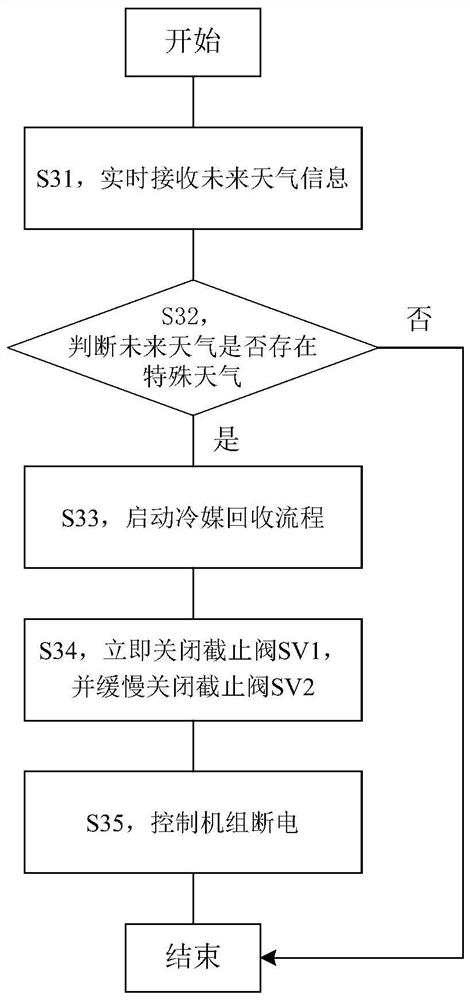
Air conditioner refrigerant recycling control method and device
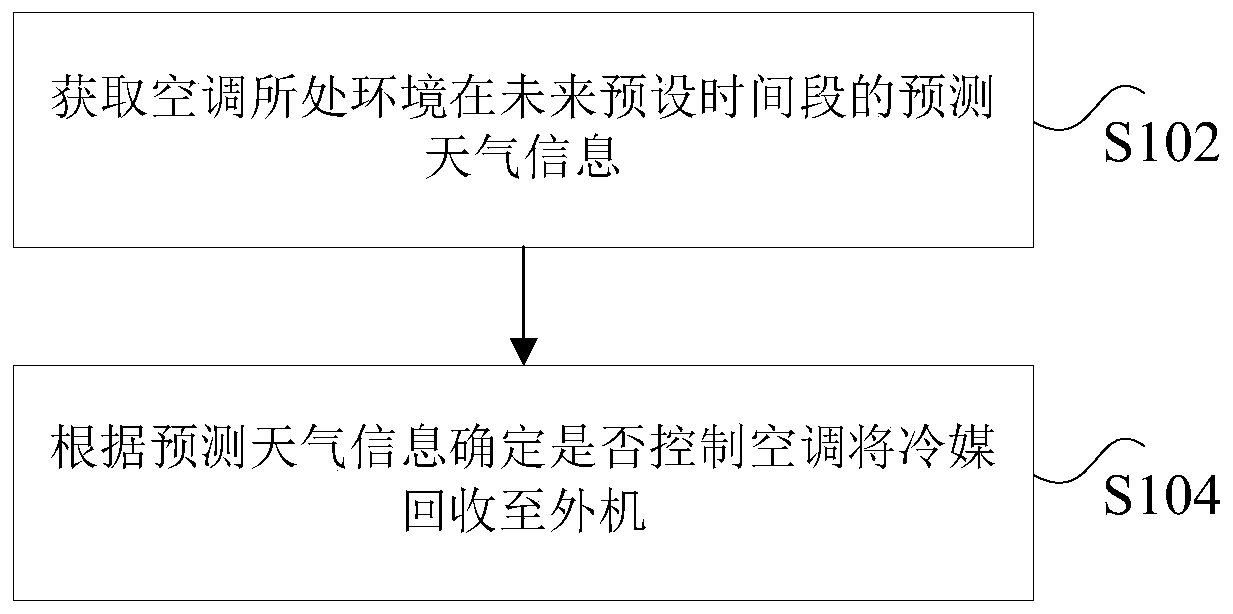
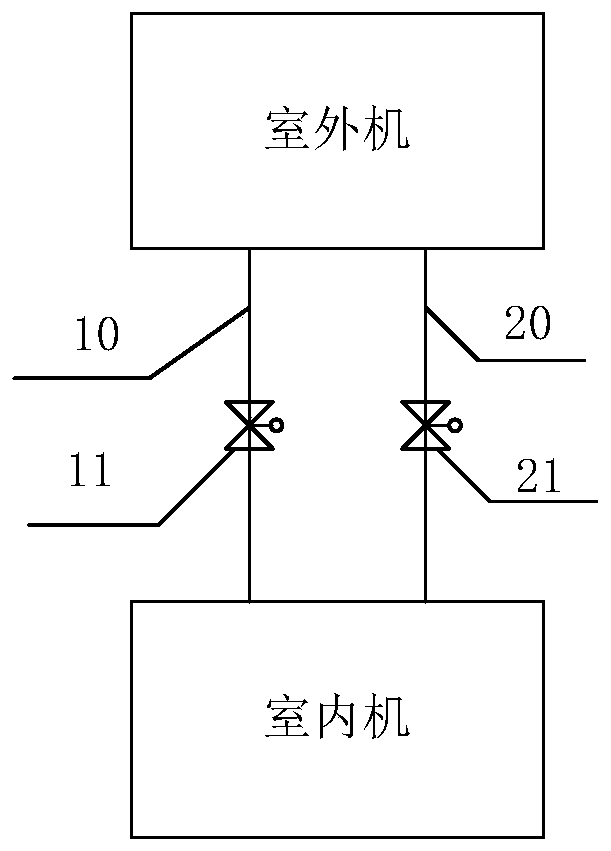
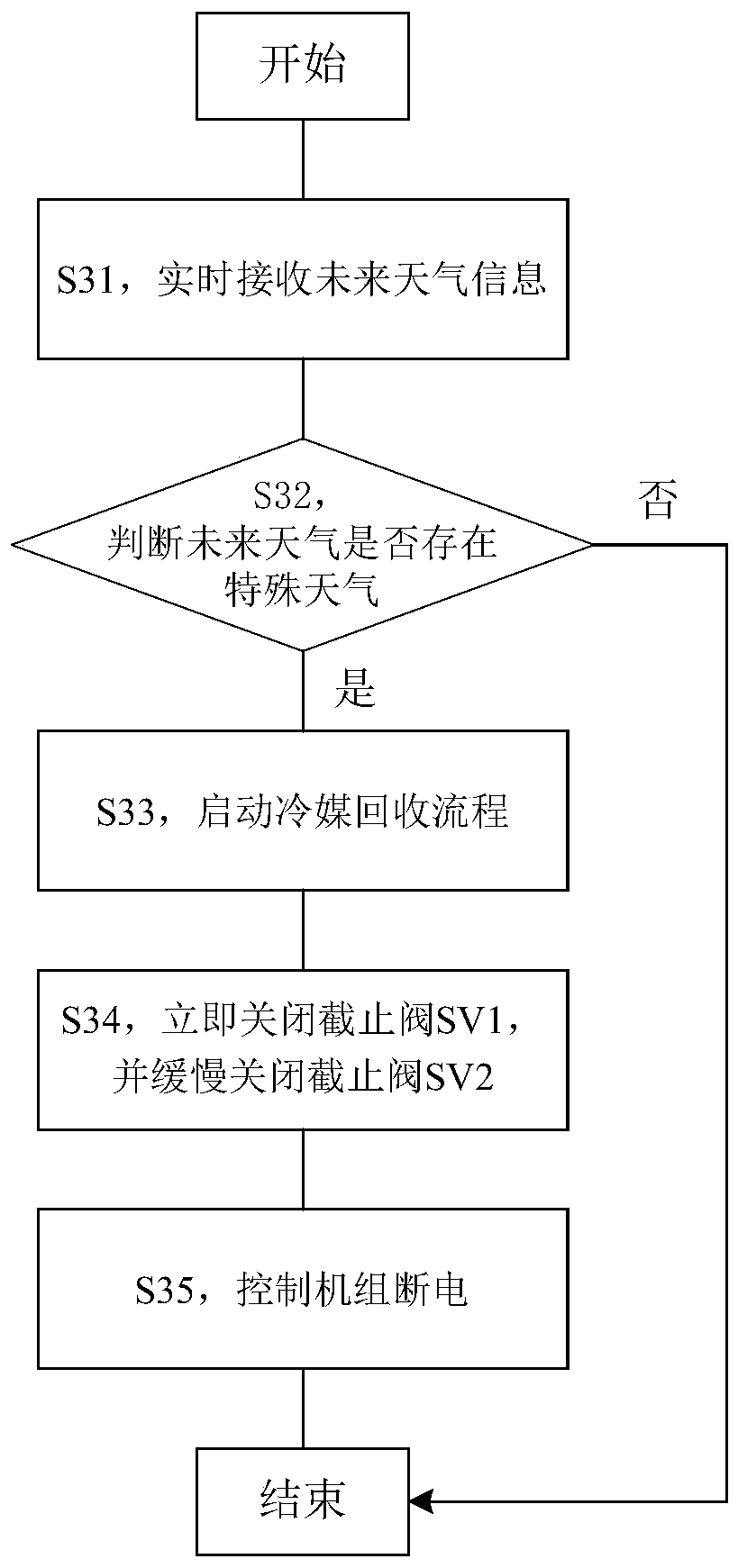
ActiveCN109974192AReach the purpose of recyclingFix leaked technical issuesMechanical apparatusLighting and heating apparatusRefrigerantExtreme weather
The invention discloses an air conditioner refrigerant recycling control method and device. The method comprises the steps that predicted weather information of the environment where an air conditioner is located in the future preset time period is acquired; and whether the air conditioner is controlled to recycle a refrigerant to an outdoor unit or not is determined according to the predicted weather information. According to the air conditioner refrigerant recycling control method and device, the technical problem that in the prior art, the refrigerant is leaked due to the fact that air conditioner indoor unit and outdoor unit pipelines are prone to being broken in extreme weather is solved.
Owner:GREE ELECTRIC APPLIANCES INC OF ZHUHAI
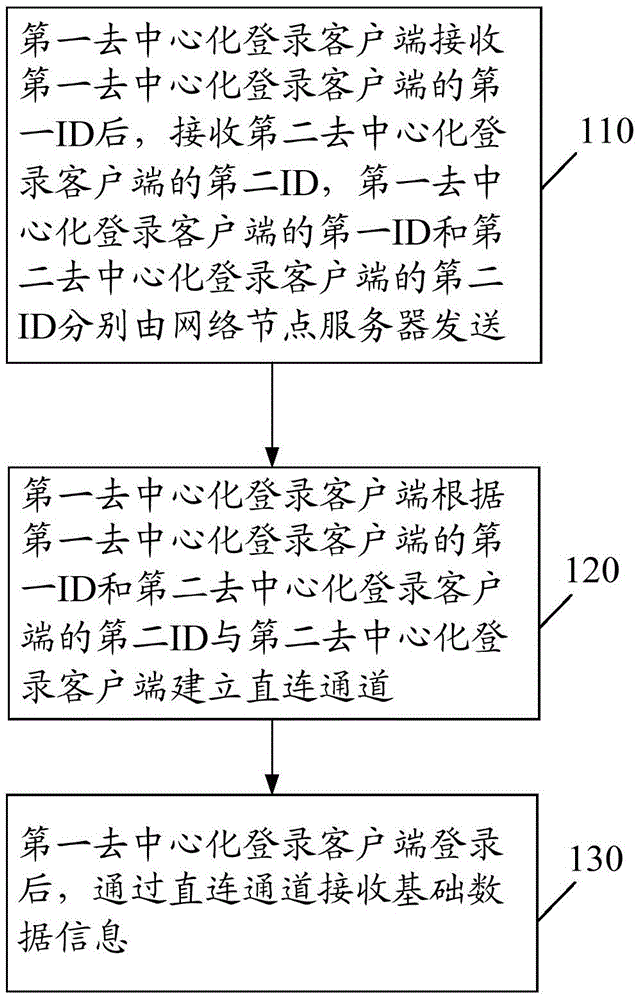
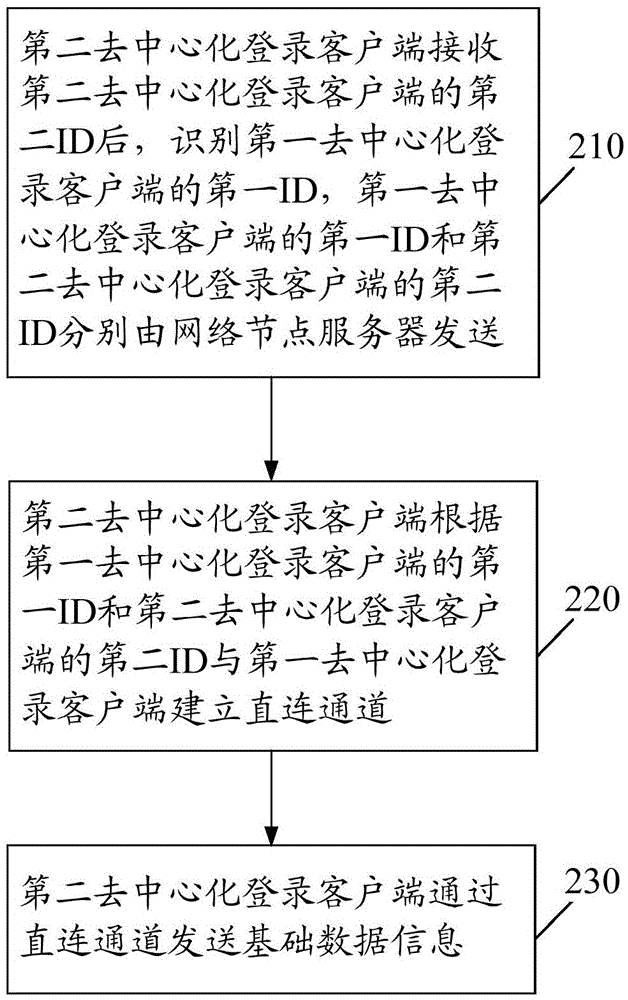
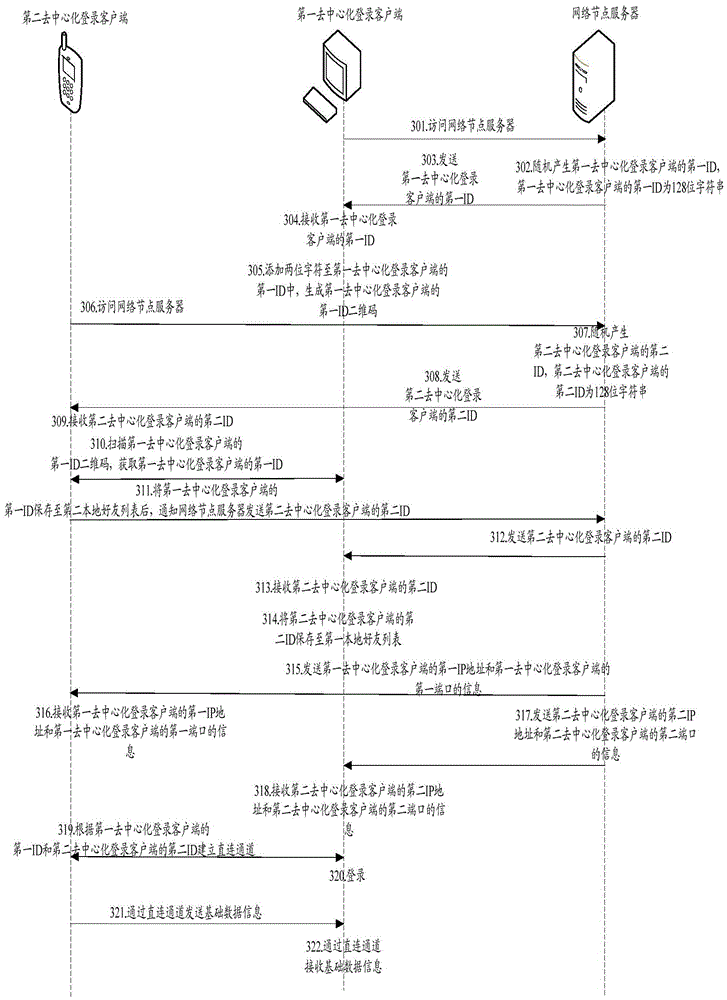
Decentralizing login methods and clients and system
The present invention discloses a decentralizing login method. The method comprises the steps that a first decentralizing login client receives a first identity (ID) number of the first decentralizing login client, and then receives a second ID of a second decentralizing login client, wherein the first ID of the first decentralizing login client and the second ID of the second decentralizing login client are each sent by a network node server; the first decentralizing login client establishes a directly connected channel with the second decentralizing login client according to the first ID of the first decentralizing login client and the second ID of the second decentralizing login client; and after login, the first decentralizing login client receives basic data information by using the directly connected channel. The present invention also discloses another decentralizing login method, a decentralizing login client, another decentralizing login client, and a decentralizing login system.
Owner:BEIJING ZHONGXIANG BIT TECH
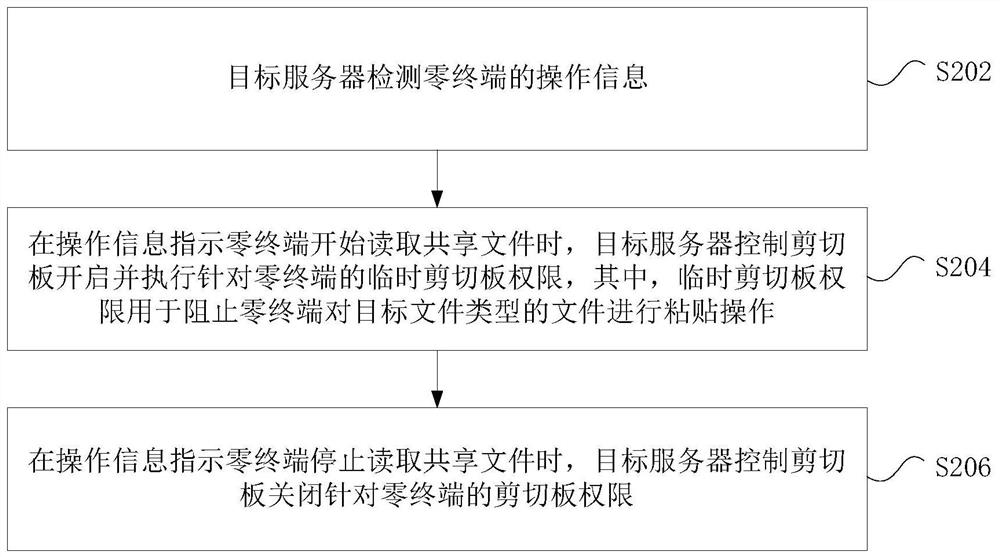
File security protection method and device
PendingCN113553618AEnsure safetyFix leaked technical issuesDigital data information retrievalInterprogram communicationEngineeringClipboard
The invention discloses a file security protection method and device. The method comprises the steps that a target server detects operation information of a zero terminal; when the operation information indicates that the zero terminal starts to read the shared file, the target server controls a clipboard to be started and executes a temporary clipboard permission for the zero terminal, and the temporary clipboard permission is used for preventing the zero terminal from conducting pasting operation on a file of the target file type; and when the operation information indicates that the zero terminal stops reading the shared file, the target server controls the clipboard to close the clipboard permission for the zero terminal. The technical problem that file information is leaked due to the fact that a user carries out screenshot storage on a shared file in a cloud office scene is solved.
Owner:XIAN WANXIANG ELECTRONICS TECH CO LTD
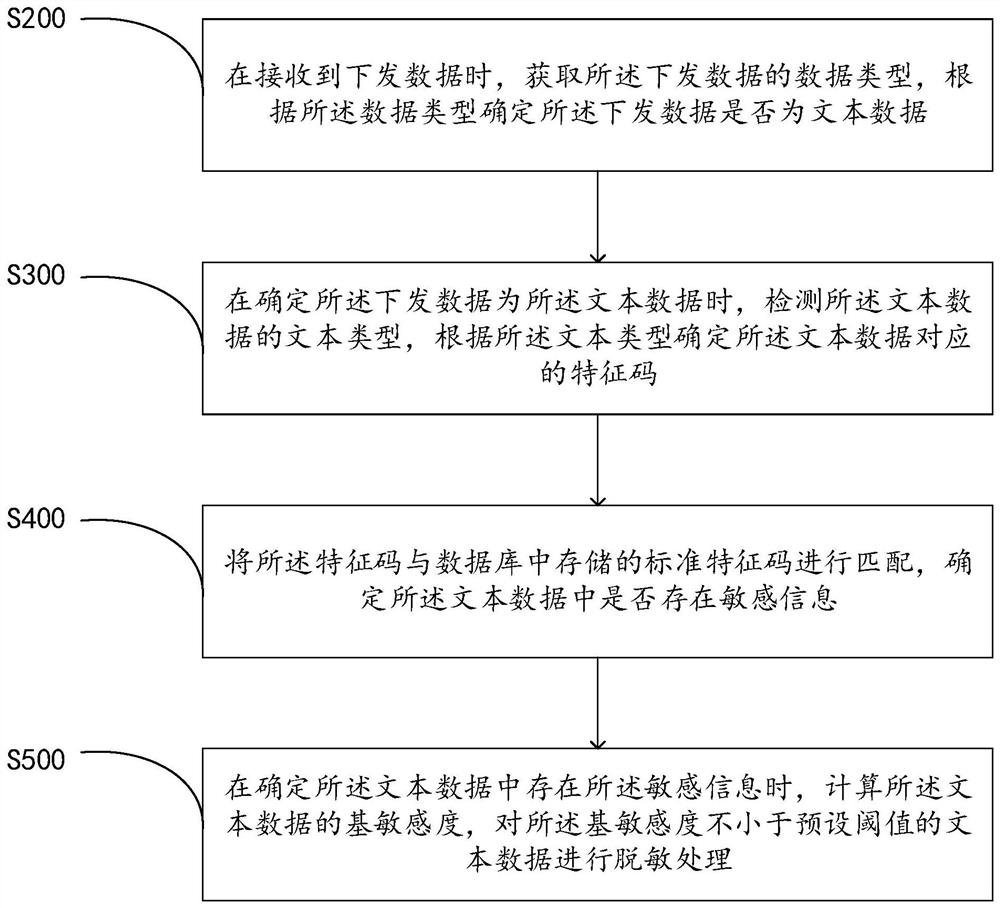
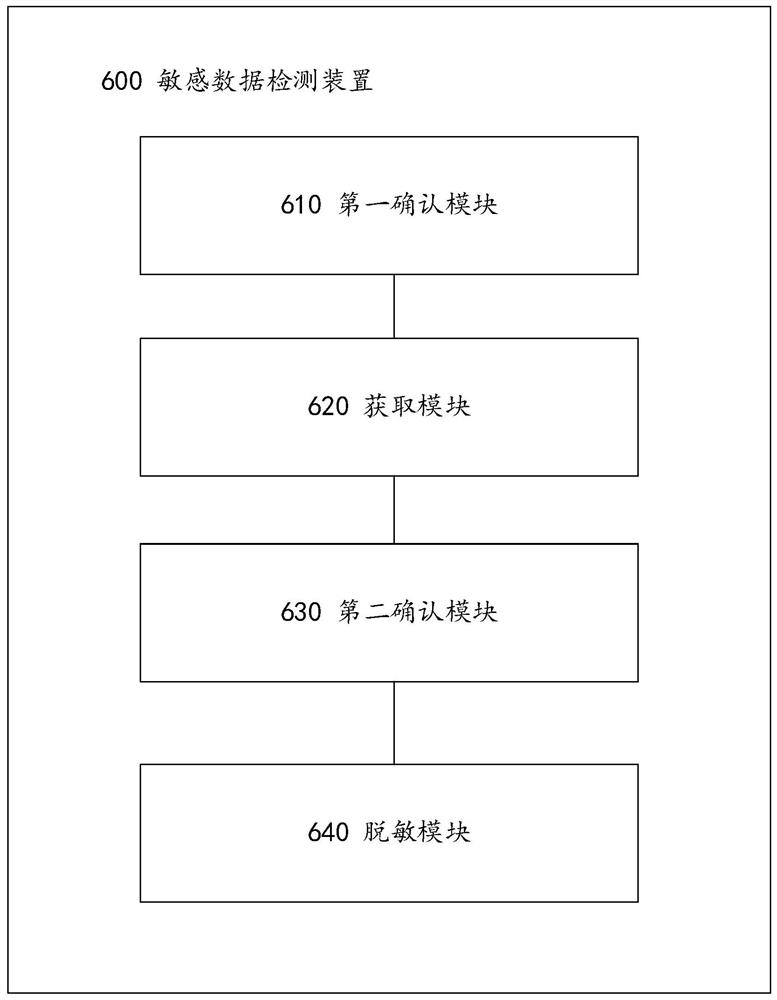
Sensitive data detection method and device, computer equipment and storage medium
PendingCN111783138AFix leaked technical issuesCharacter and pattern recognitionDigital data protectionData classData science
The embodiment of the invention belongs to the technical field of information security, and relates to a sensitive data detection method, which comprises the steps of obtaining a data type of issued data when the issued data is received, and determining whether the issued data is text data according to the data type; when it is determined that the issued data is text data, detecting the text typeof the text data, and obtaining a feature code corresponding to the text data; matching the feature code with a standard feature code stored in a database, and determining whether sensitive information exists in the text data; when it is determined that the sensitive information exists in the text data, calculating the base sensitivity of the text data, and performing desensitization processing onthe text data with the base sensitivity not smaller than a preset threshold value. The invention further provides a sensitive data detection device, computer equipment and a storage medium. In addition, the invention also relates to a blockchain technology, and the issued data can be stored in the blockchain node. According to the method, the identification efficiency and accuracy of private dataare improved, and the safety of personal information is protected.
Owner:CHINA PING AN PROPERTY INSURANCE CO LTD
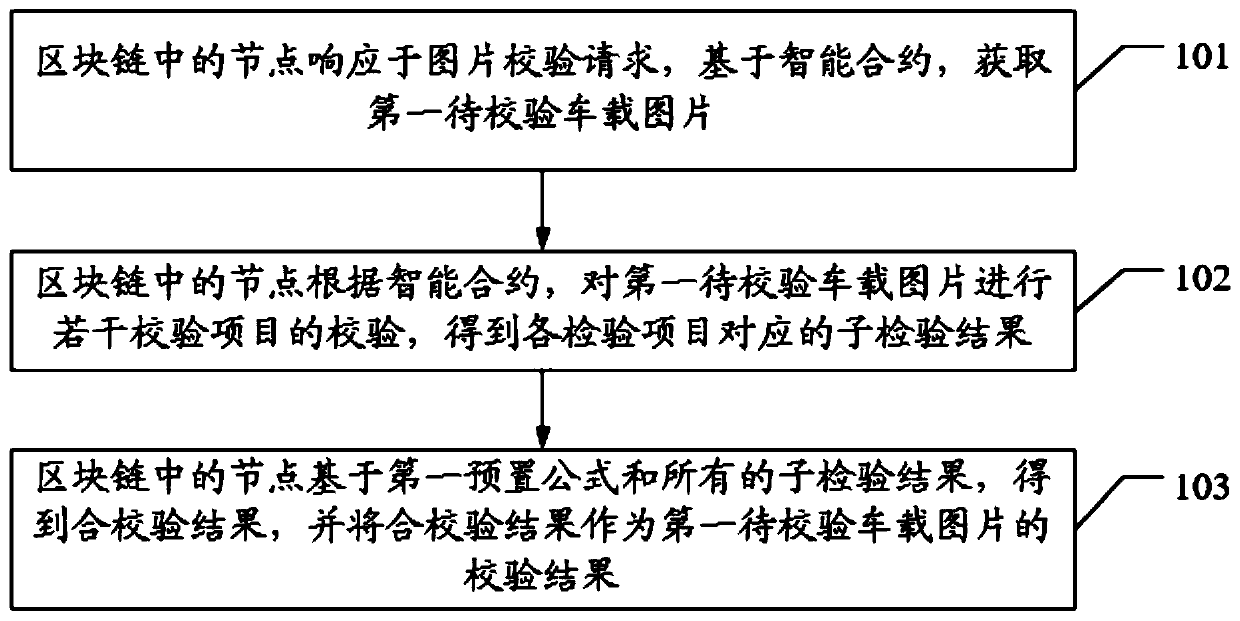
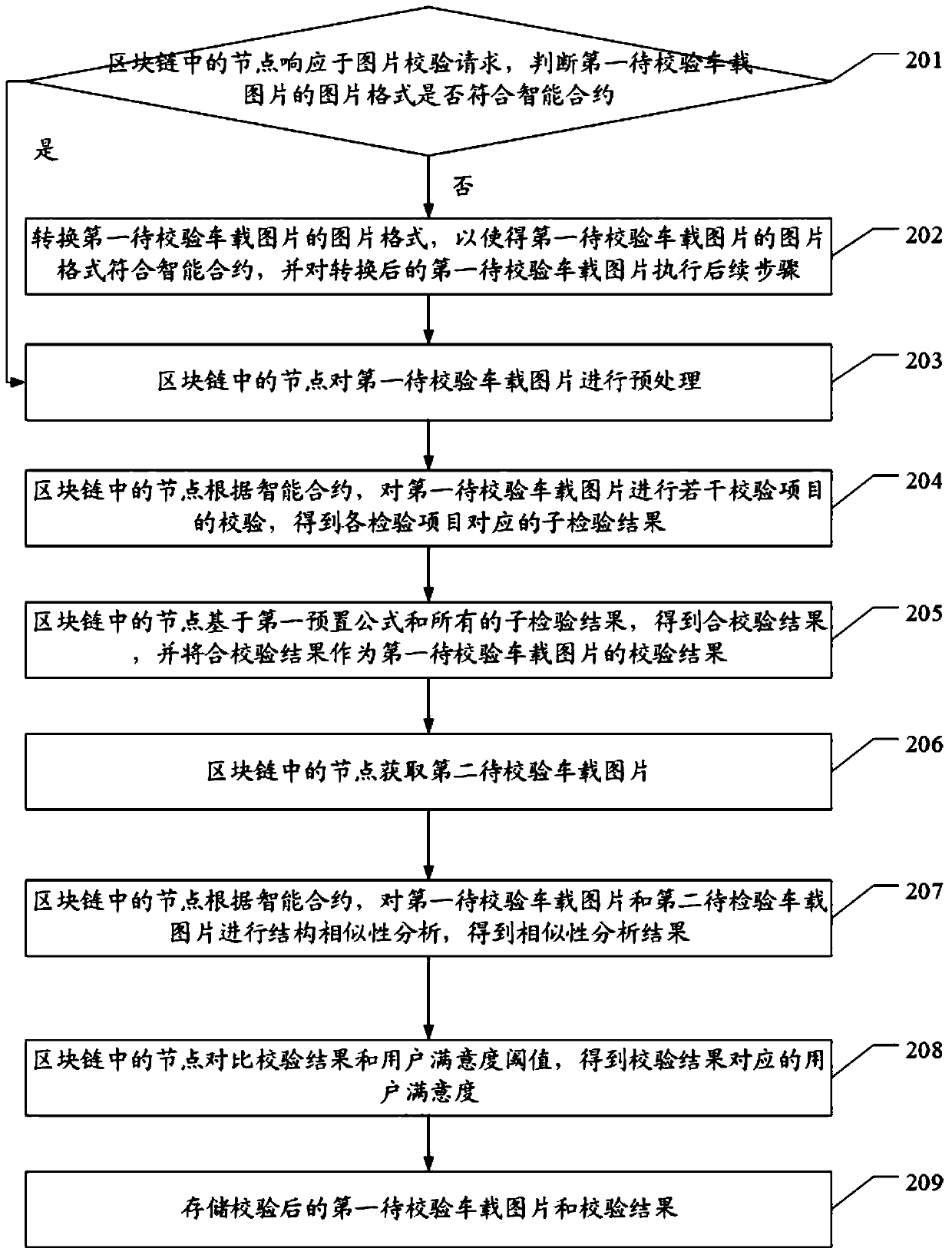
Picture verification method based on block chain in Internet of Vehicles environment
PendingCN110766078AFix leaked technical issuesThe detection process method is safe and reliableFinanceCharacter and pattern recognitionThird partyIn vehicle
The invention discloses a picture verification method based on a block chain in an Internet of Vehicles environment, and the method comprises: a node in the block chain responding to a picture verification request, and obtaining a first to-be-verified vehicle-mounted picture based on an intelligent contract; the nodes in the block chain performing verification of a plurality of verification itemson the first to-be-verified vehicle-mounted picture according to the intelligent contract, and obtaining sub-verification results corresponding to the verification items; the nodes in the block chainbeing based on a first preset formula and all the sub-inspection results, obtaining a combined verification result, and taking combined verification result as a verification result of first to-be-verified vehicle-mounted picture. The technical problem of leakage of the vehicle-mounted picture due to the fact that a third-party platform is adopted for verification when the vehicle-mounted picture is verified in the prior art is solved.
Owner:GUANGDONG UNIV OF TECH
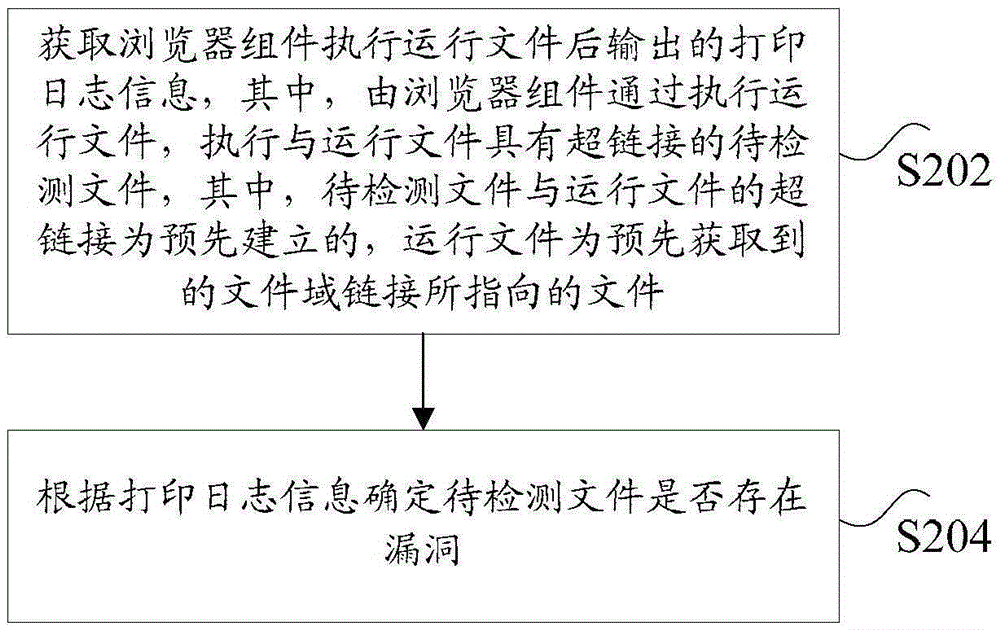
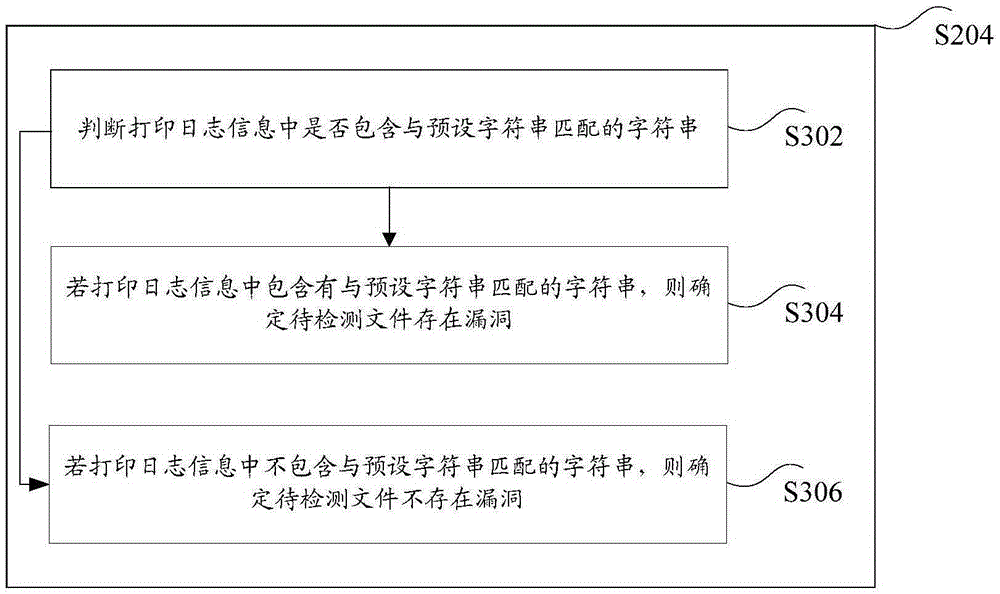
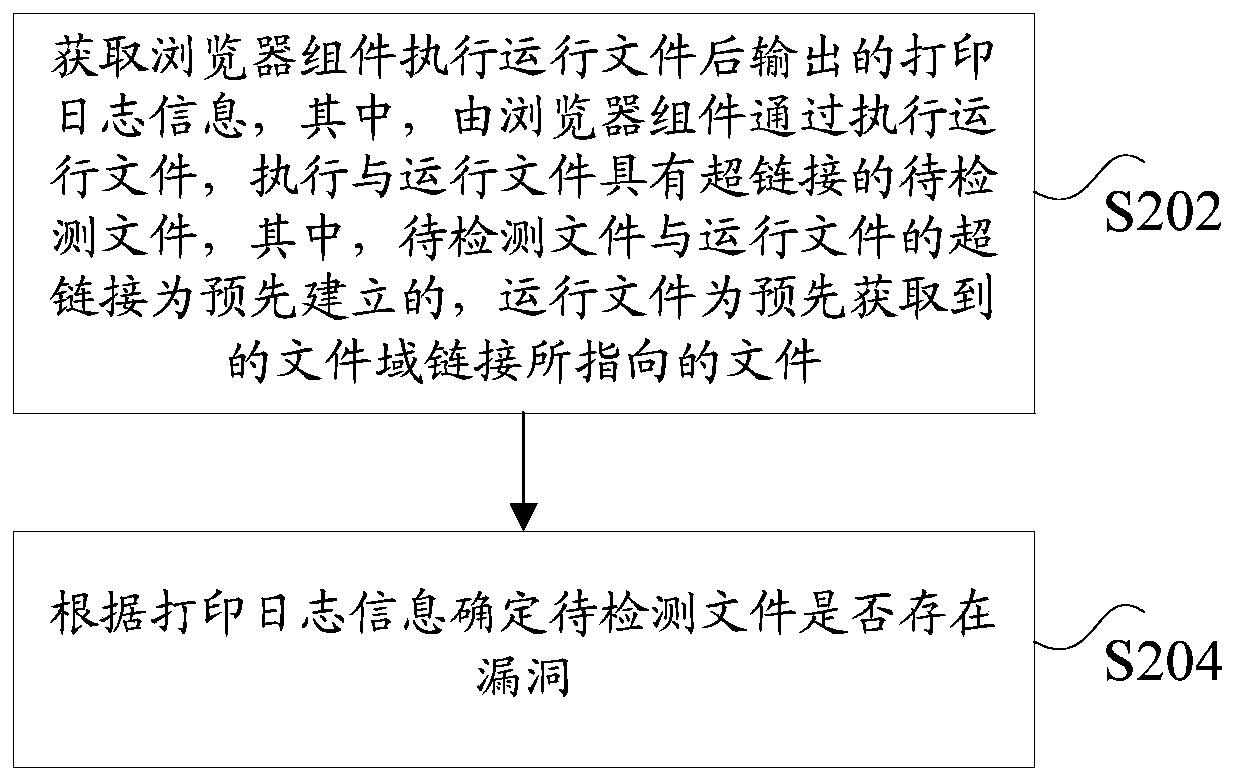
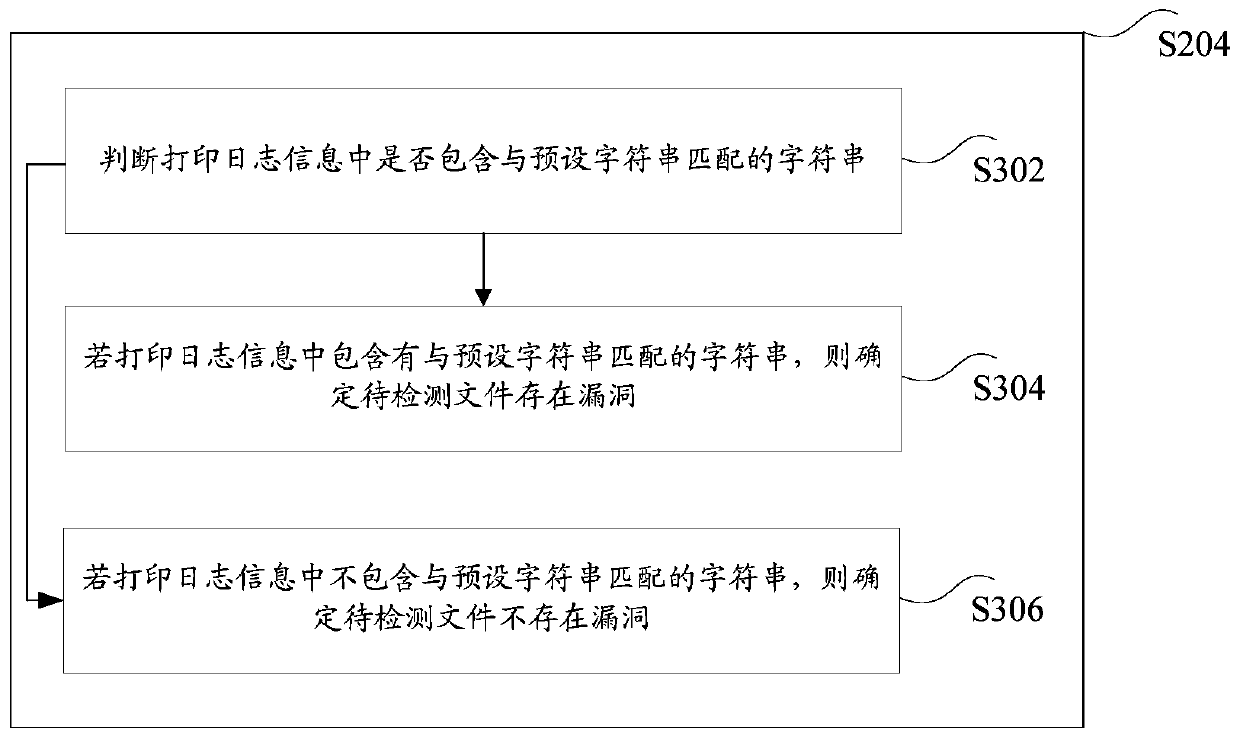
Loophole detection method, device and system
ActiveCN106503548AImprove securityFix leaked technical issuesPlatform integrity maintainanceHyperlinkDatabase
The invention discloses a loophole detection method, device and system, wherein, the method comprises the steps of obtaining the printed log information after the browser sub unit executing the working file, wherein, the browser sub unit through executing the working file, executing the pending to be detected files having hyperlink with the working file, wherein, the hyperlink of the pending to be detected files and the working file being prebuilt, the working file being a file pointed by the preobtained file domain link; according to printed log information determining whether the pending to be detected files existing loopholes or not. The invention solves the technical problem of information leakage caused by loopholes in the files.
Owner:ALIBABA GRP HLDG LTD
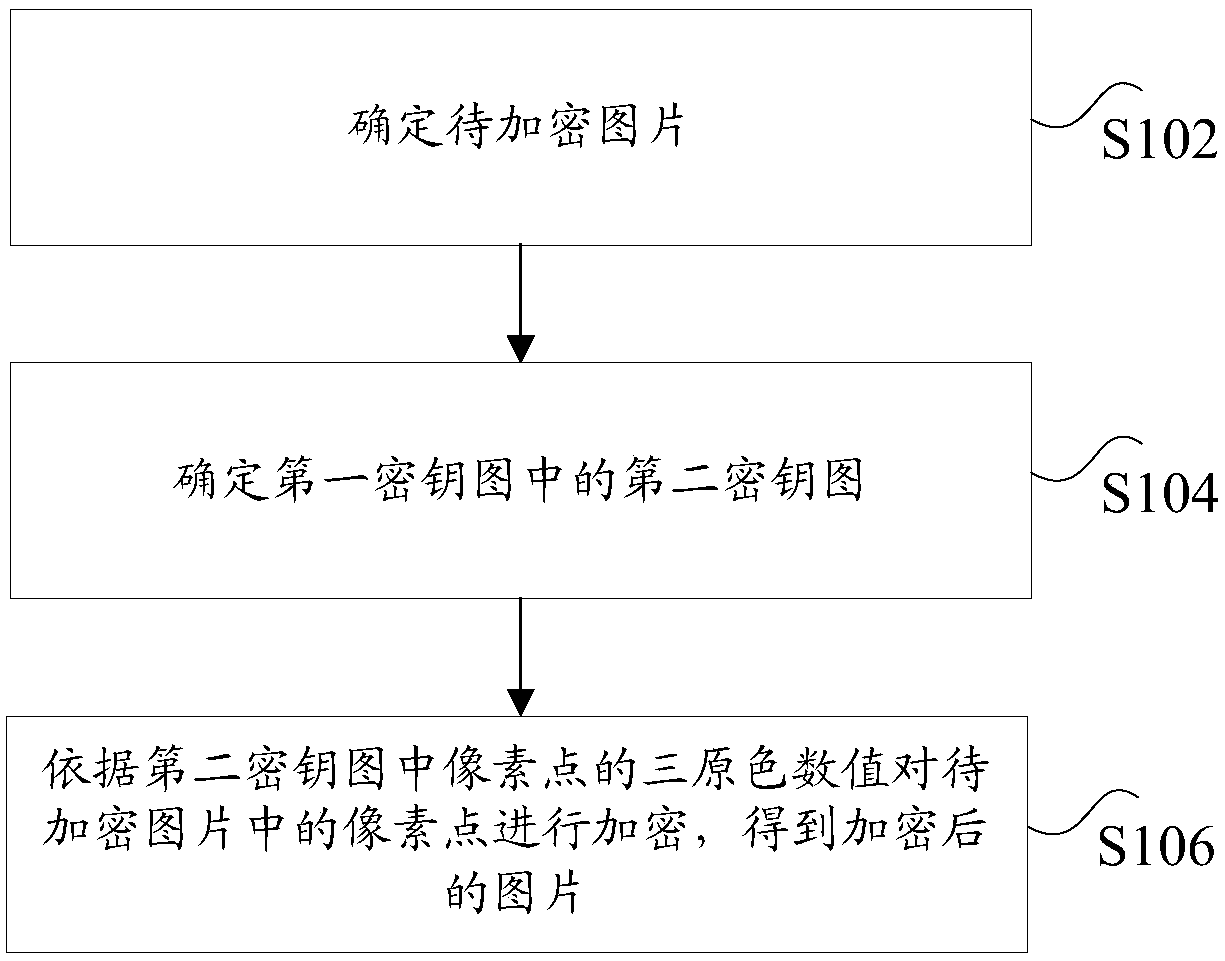
Method and device for encrypting and decrypting picture
InactiveCN109033863AFast encryptionTo achieve the purpose of encryptionDigital data protectionProgram/content distribution protectionComputer hardwareComputer science
The present application discloses a picture encryption and decryption method and apparatus. The method comprises the following steps: determining a picture to be encrypted; determining a second key map in the first key map, wherein the first secret key map is used for encrypting a picture to be encrypted by the three primary color values of pixel points in the first secret key map, the second secret key map is a first rectangular area formed by taking a designated point in the first secret key map as a vertex of the first rectangular area and taking a length and a width of the picture to be encrypted as a length and a width of the first rectangular area; the pixel points in the picture to be encrypted are encrypted according to the three primary color values of the pixel points in the second secret key map to obtain the encrypted picture. The present application solves a technical problem of picture information disclosure due to a lack of effective picture encryption means.
Owner:GUANGZHOU SHIYUAN ELECTRONICS CO LTD
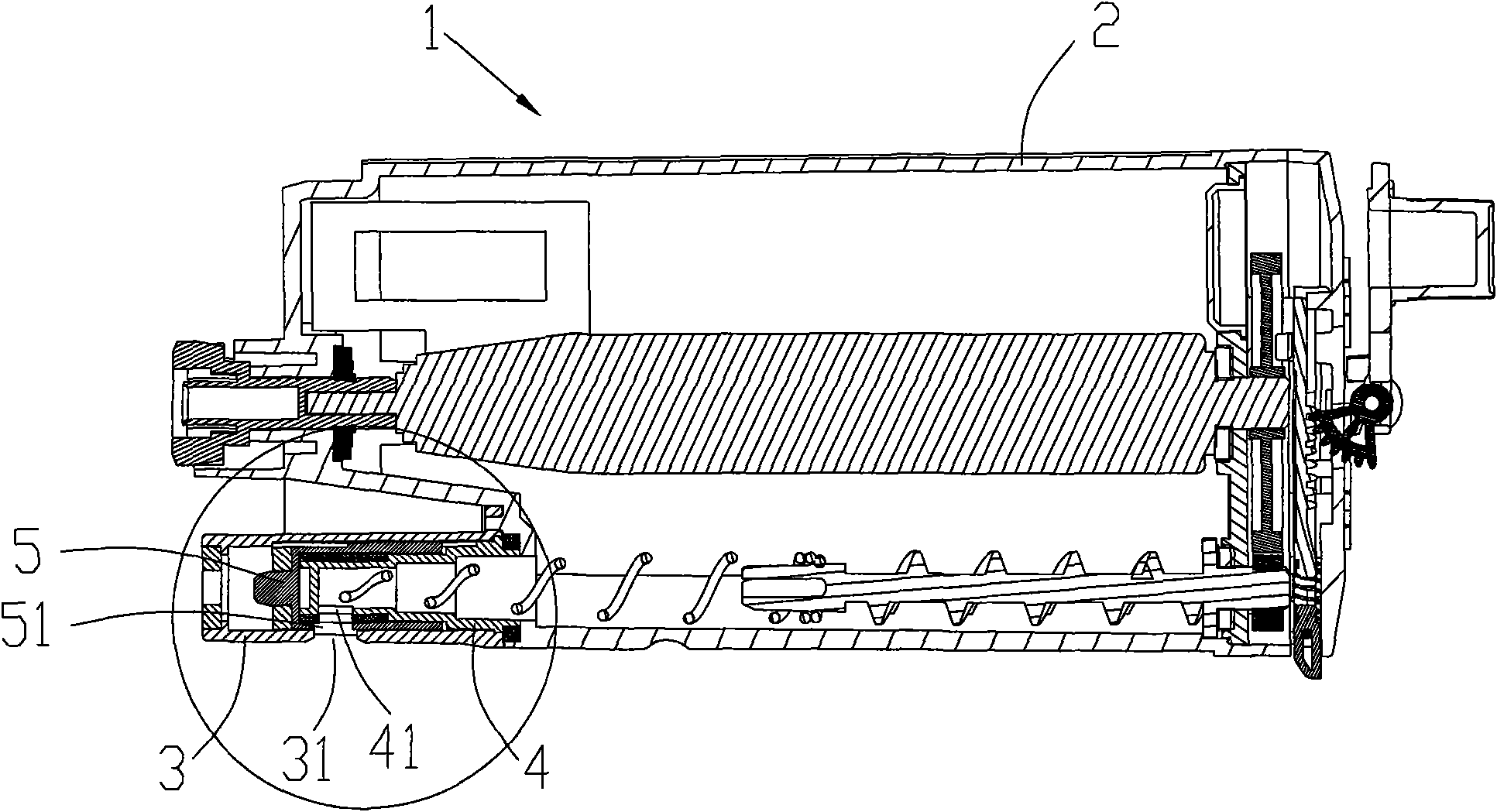
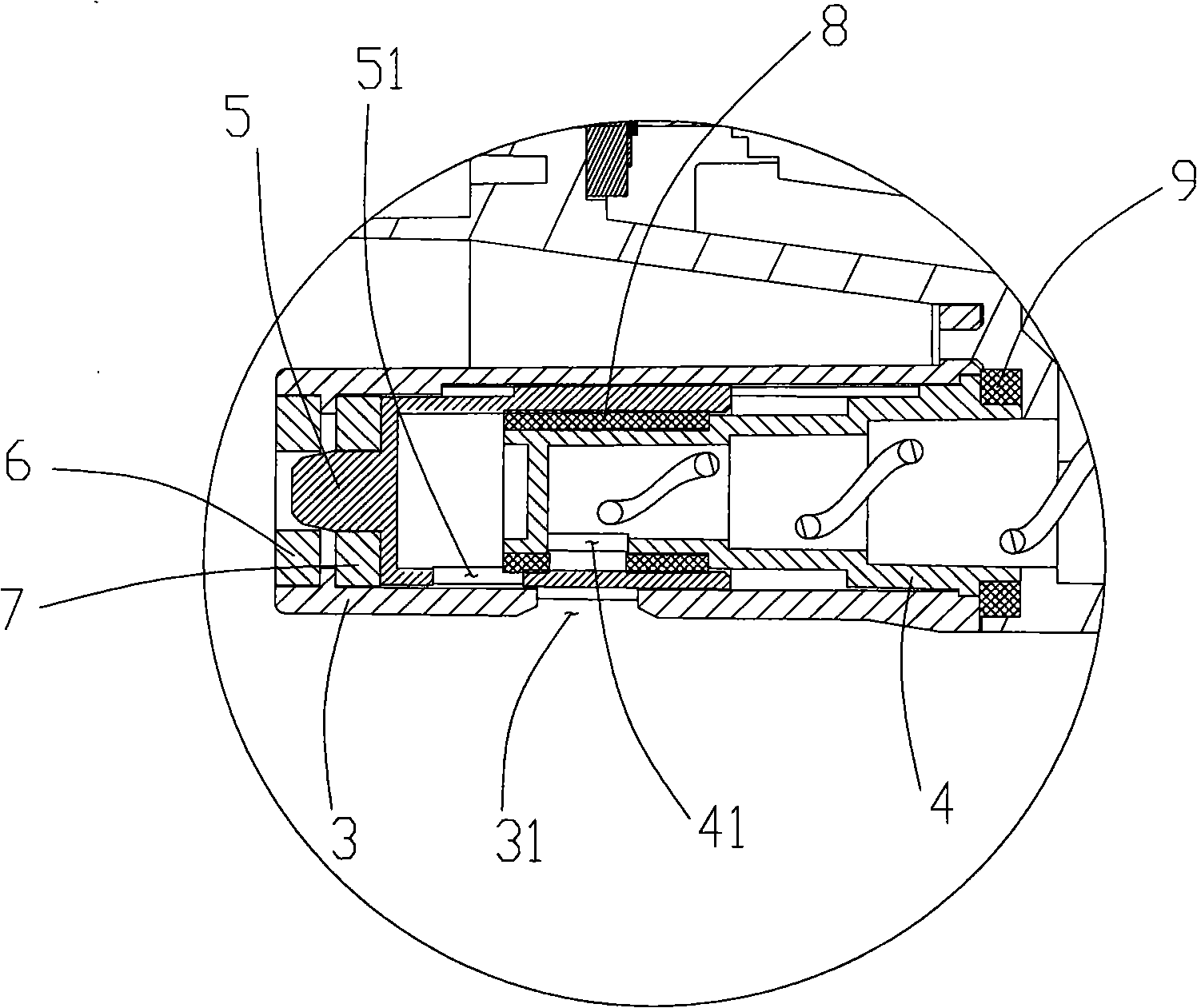
Cartridge and electronic cigarette
The invention discloses a cartridge and an electronic cigarette. The cartridge comprises a tar cup, a tar storage cavity for storing tobacco tar, an atomizer, a smoke channel and a sealing sleeve, wherein the atomizer is arranged in the tar cup; an atomizing cavity and a tar inlet are formed in the atomizer; the smoke channel is located in the middle of the tar cup and used for making the outsidecommunicate with the atomizing cavity; an atomizing seat is sleeved with the sealing sleeve; and the tar inlet is covered with the sealing sleeve. In use, the sealing sleeve is driven to move in the direction away from the atomizing cavity, so that the tar inlet separately communicates with the tar storage cavity and the atomizing cavity. By means of the cartridge, the technical problem is solvedthat in the correlated technology, because no cartridge is employed, the contact time of the tobacco tar and the atomizing cavity is too long, and tobacco tar leakage is caused.
Owner:唯它(深圳)科技有限公司
Viscous and dense material discharging device and viscous and dense material manufacturing system
InactiveCN106512865AFix leaked technical issuesChemical/physical/physico-chemical processesFeed devicesSpiral bladeEngineering
The invention provides a viscous and dense material discharging device and a viscous and dense material manufacturing system, and relates to the technical field of viscous and dense material production devices. The viscous and dense material discharging device comprises a driving mechanism, a material conveying shell, a squeezing mechanism and a padding chamber. The material conveying shell is provided with a material inlet and a material outlet, the padding chamber is connected with one end of the material conveying shell, the padding chamber is provided with a gas collecting part, the squeezing mechanism comprises a shaft and a spiral blade, the spiral blade is installed on the shaft, the shaft penetrates through the material conveying shell and the padding chamber and is connected with the driving mechanism, the spiral blade is located in the material conveying shell, and a first sealing element is arranged between the padding chamber and the shaft. The viscous and dense material discharging device is applied to the viscous and dense material production process so as to solve the technical problem of gas leakage in the viscous and dense material discharging process in the prior art.
Owner:王珈乐
Control method and device for air conditioner refrigerant recovery
ActiveCN109974192BReach the purpose of recyclingFix leaked technical issuesMechanical apparatusLighting and heating apparatusExtreme weatherProcess engineering
The invention discloses an air conditioner refrigerant recycling control method and device. The method comprises the steps that predicted weather information of the environment where an air conditioner is located in the future preset time period is acquired; and whether the air conditioner is controlled to recycle a refrigerant to an outdoor unit or not is determined according to the predicted weather information. According to the air conditioner refrigerant recycling control method and device, the technical problem that in the prior art, the refrigerant is leaked due to the fact that air conditioner indoor unit and outdoor unit pipelines are prone to being broken in extreme weather is solved.
Owner:GREE ELECTRIC APPLIANCES INC
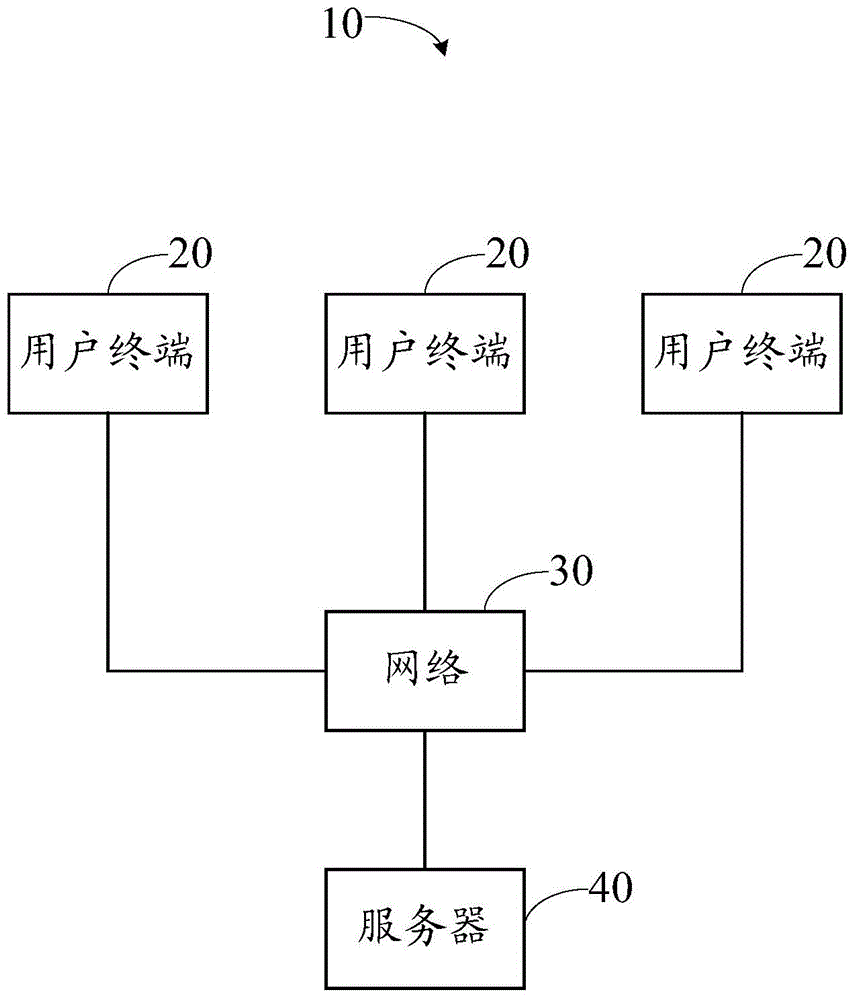
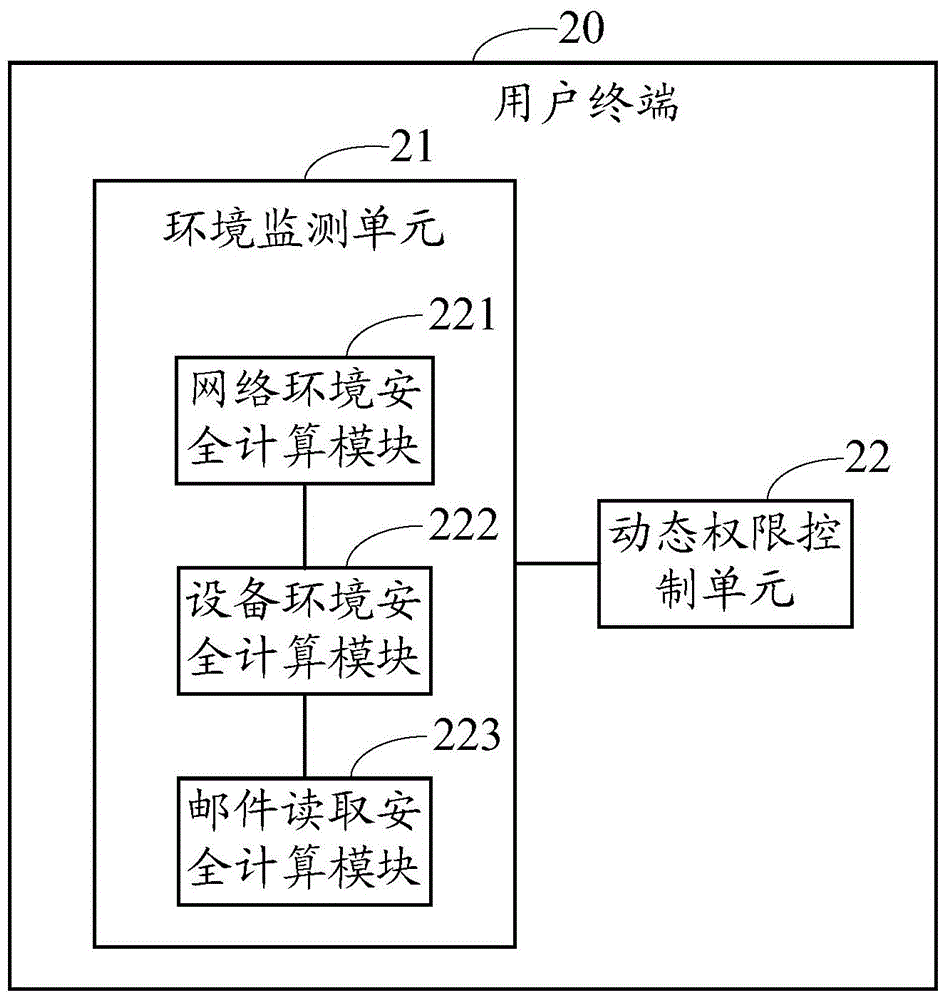
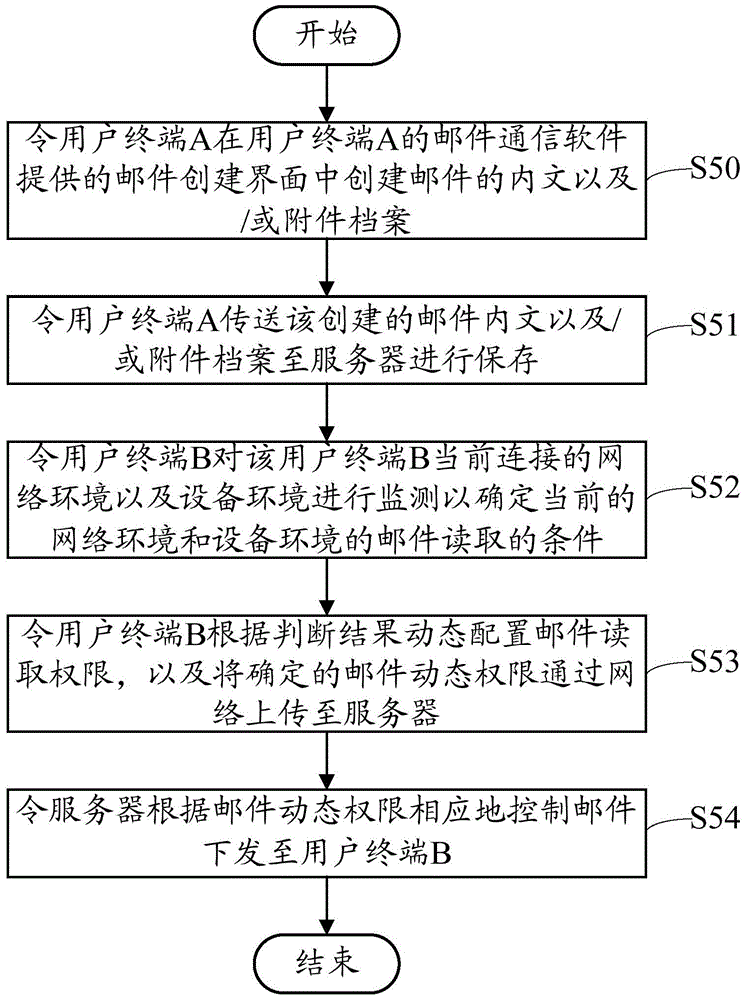
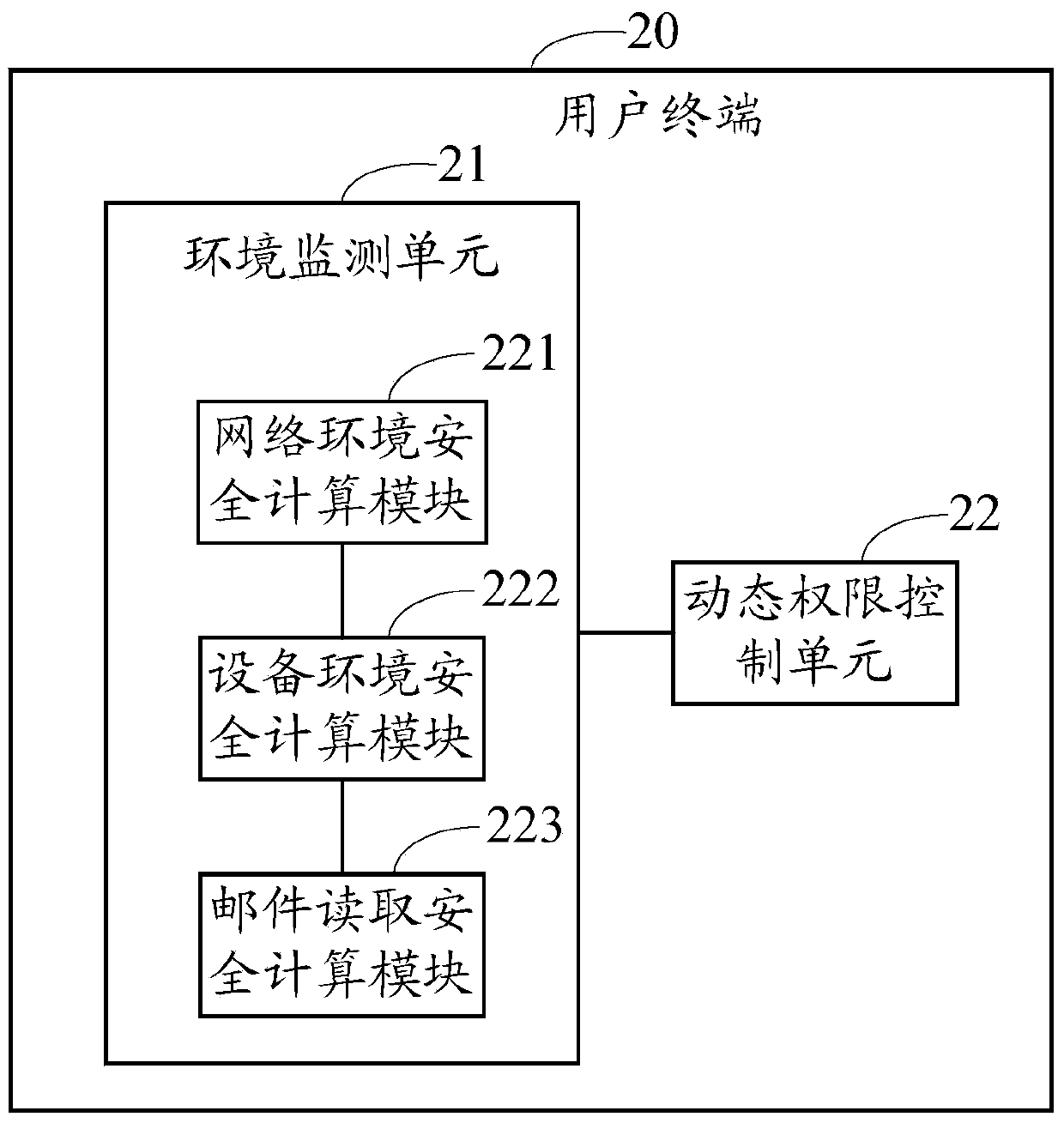
A mail reading system and method
ActiveCN103746900BFix leaked technical issuesData switching networksCommunications softwareAuthority control
Owner:福建省星云大数据应用服务有限公司
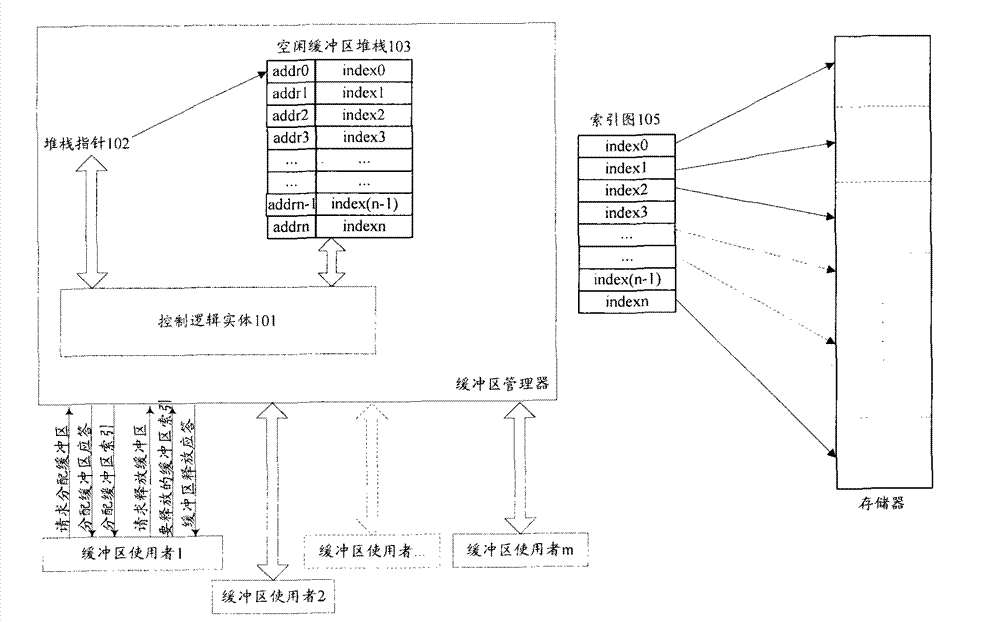
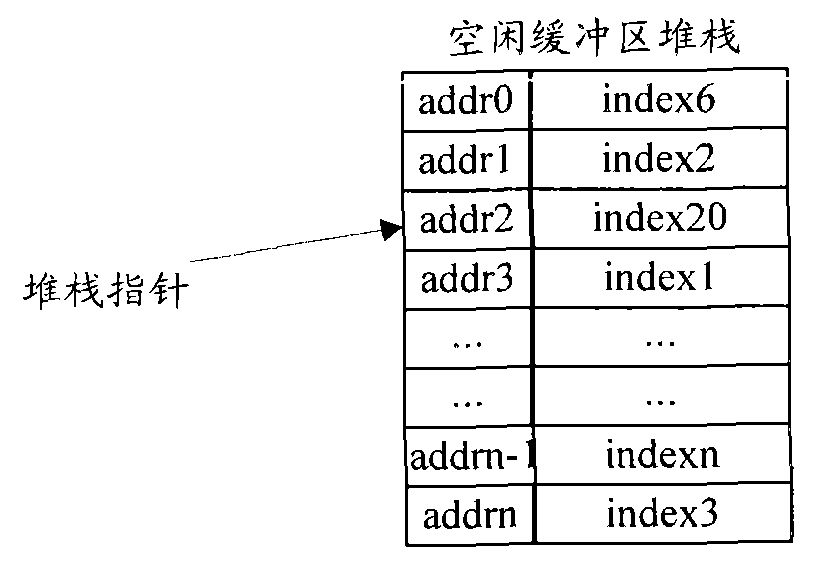
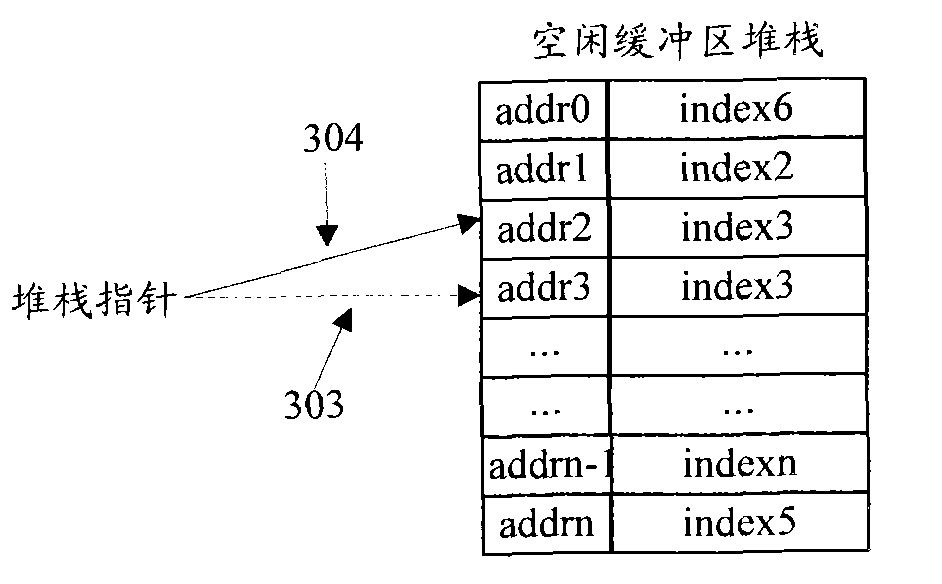
Buffer zone management method and system
InactiveCN101923517BFix leaked technical issuesPrevent leakageMemory adressing/allocation/relocationComputer networkBuffer zone
The invention discloses a buffer zone management method and a buffer zone management system, which are used for solving the technical problem of buffer zone leakage. The method comprises the following steps of: detecting the allocation time of buffer zones periodically; aging the buffer zones which are not released for a long time; automatically performing an operation of pressing the buffer zones which are not released for a long time into an idle buffer zone stack to finish recovering the buffer zones. Therefore, the buffer zone leakage is prevented; and the robustness and the reliability of a buffer zone manager are improved.
Owner:ZTE CORP +1
Vulnerability detection method, device and system
ActiveCN106503548BImprove securityFix leaked technical issuesPlatform integrity maintainanceHyperlinkInformation leakage
The invention discloses a loophole detection method, device and system, wherein, the method comprises the steps of obtaining the printed log information after the browser sub unit executing the working file, wherein, the browser sub unit through executing the working file, executing the pending to be detected files having hyperlink with the working file, wherein, the hyperlink of the pending to be detected files and the working file being prebuilt, the working file being a file pointed by the preobtained file domain link; according to printed log information determining whether the pending to be detected files existing loopholes or not. The invention solves the technical problem of information leakage caused by loopholes in the files.
Owner:ALIBABA GRP HLDG LTD
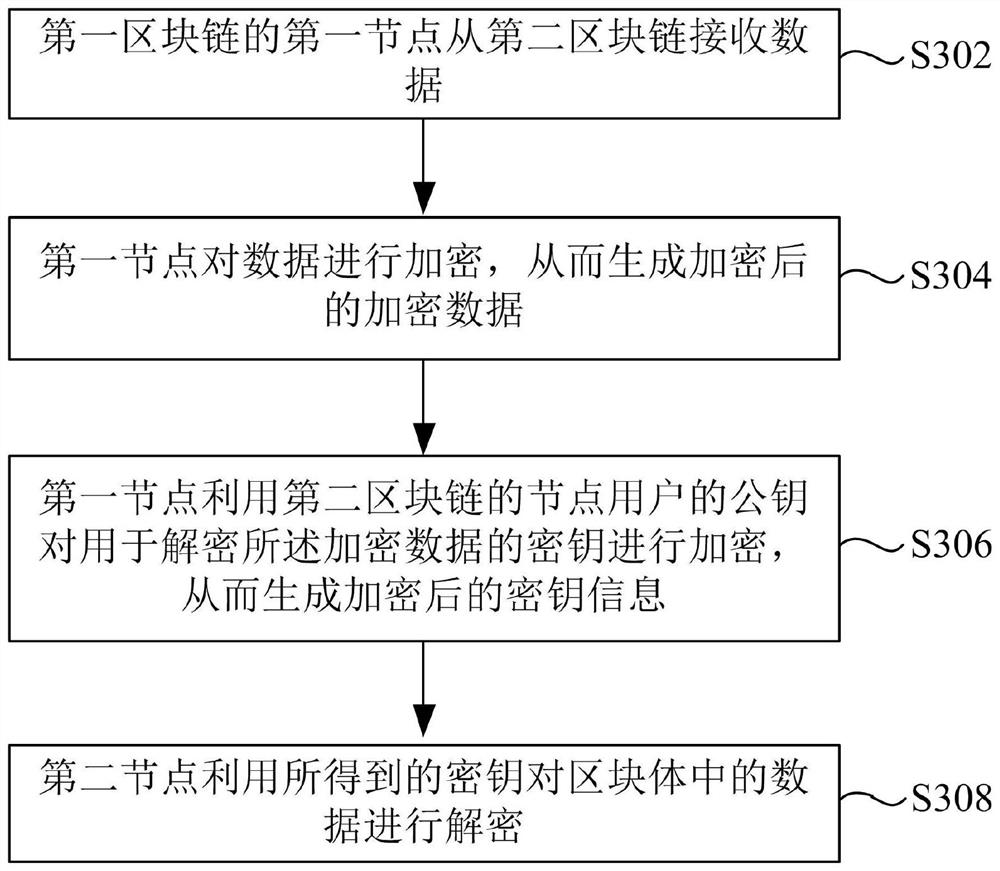
Data processing method and device applied to blockchain node and storage medium
ActiveCN112910633AFix leaked technical issuesKey distribution for secure communicationComputer networkBlockchain
The invention discloses a data processing method and device applied to a blockchain node and a storage medium. The method comprises the steps that a first node of a first blockchain receives data from a second blockchain; the first node encrypts the data so as to generate encrypted data; the first node encrypts a secret key used for decrypting the encrypted data by using a public key of a node user of a second block chain so as to generate encrypted secret key information; and the first node generates a block corresponding to the received data by using the encrypted data as a block body and the encrypted key information as a block head.
Owner:微观(天津)科技发展有限公司
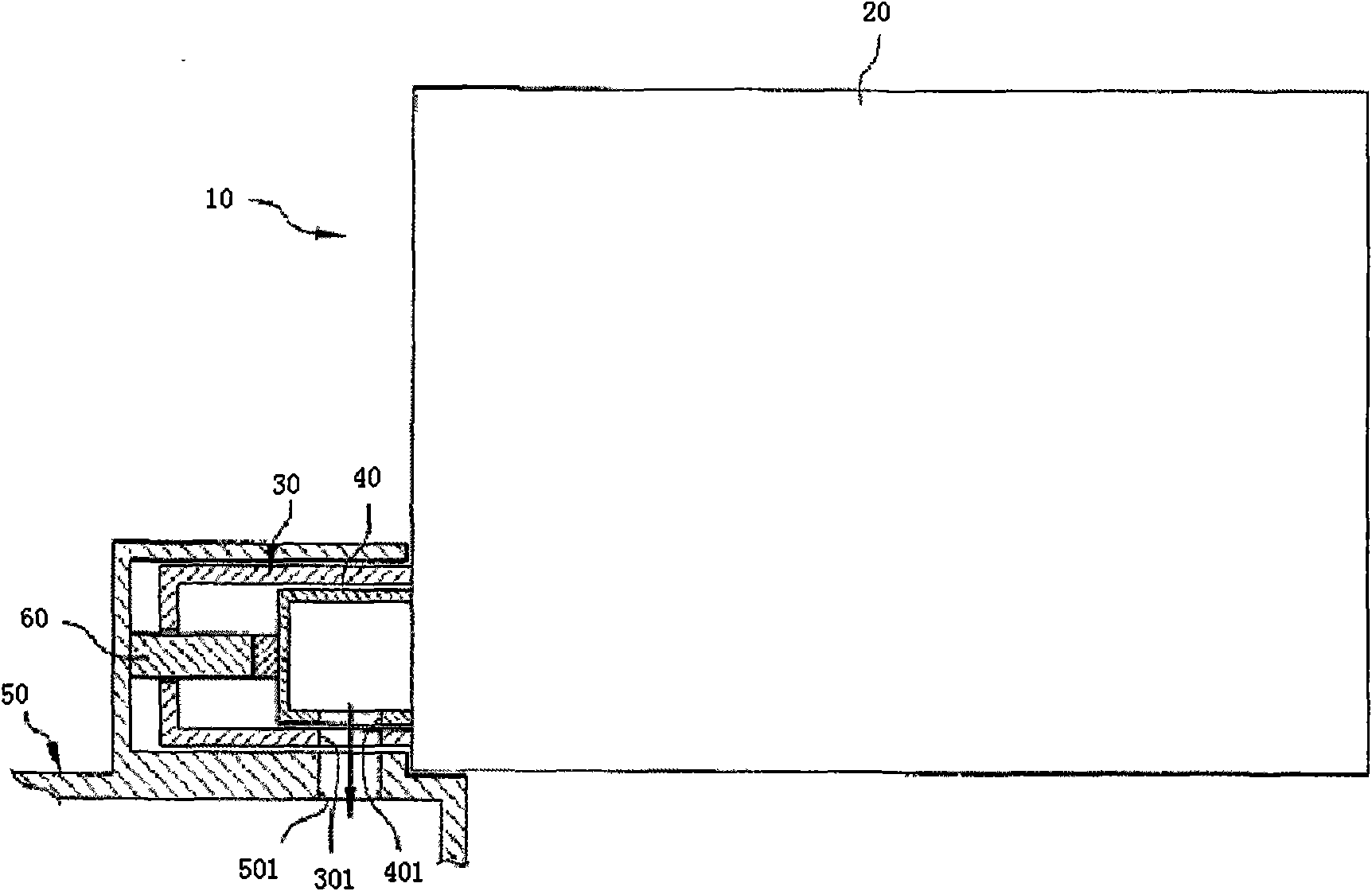
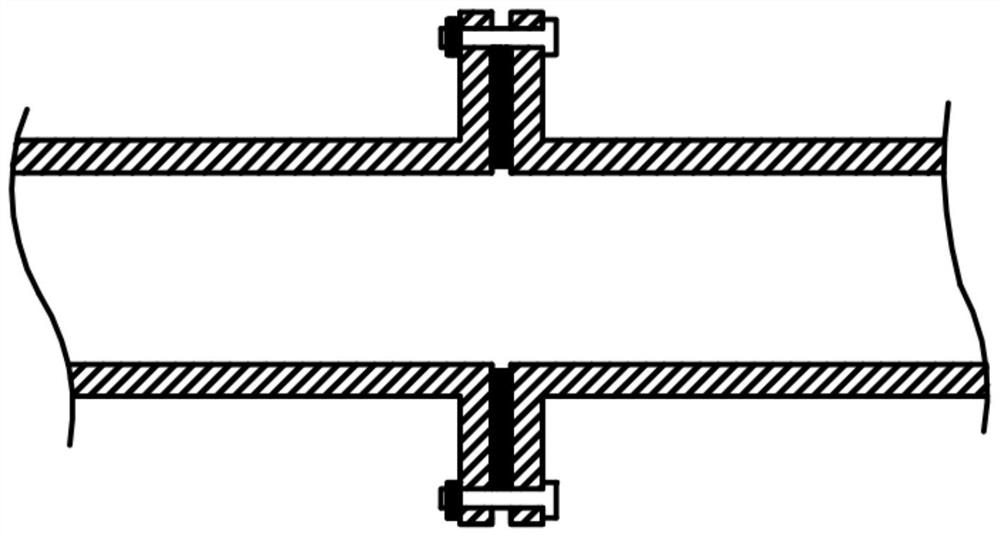
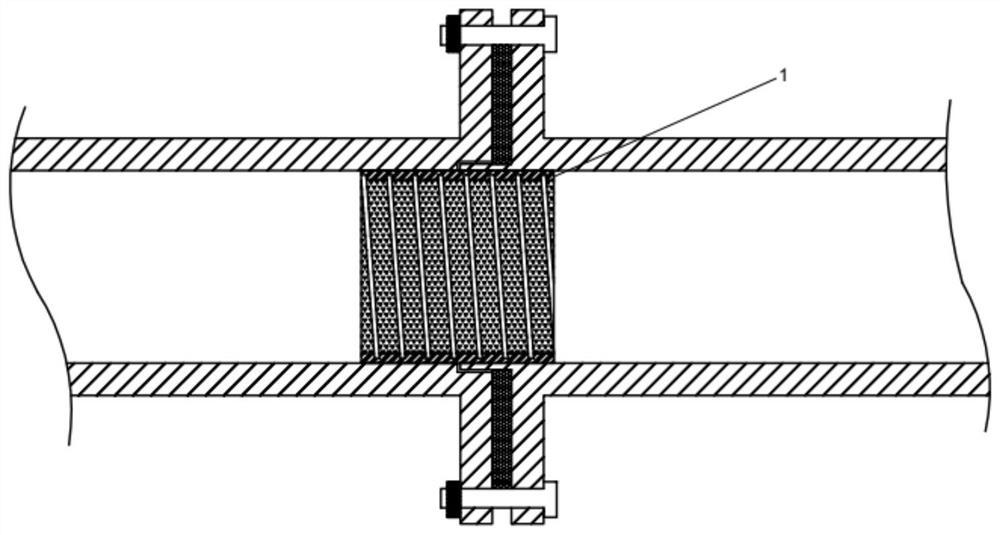
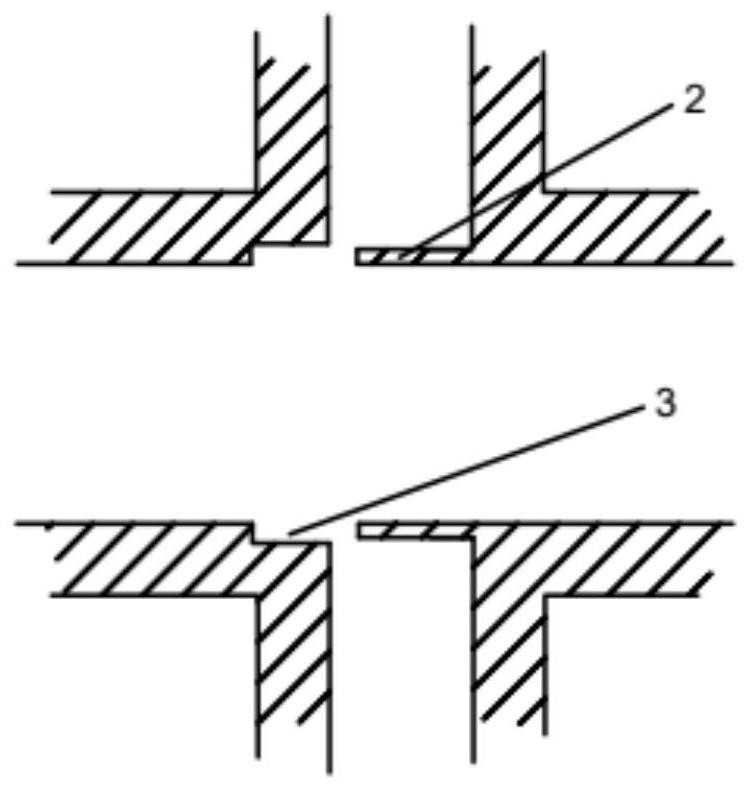
A natural gas pipeline with a flange sealing joint and its installation method
The invention relates to a natural gas pipeline with a flange sealing joint and an installation method thereof, which can effectively prevent flange leakage of the natural gas transmission pipeline. The flange sealing joint includes a male joint and a female joint. The radial end surface of the male joint is provided with a protrusion outside, and the end of the female joint is provided with a recess that can accommodate the protrusion of the male joint. Both the protrusion and the recess are circumferential Set a circle in the direction, and set an internal seal at the connection between the male joint and the female joint. The internal seal is set in a circumferential circle. The outer surface of the internal seal is provided with an adhesive, which can be bonded to the inner wall of the natural gas pipeline. , to realize the sealing of the butt joint; it can effectively solve the technical problem of leakage of the flange of the natural gas pipeline, the sealing effect is good, and the cost is low, and the installation and operation are simple and convenient.
Owner:广西熹海新能源有限公司
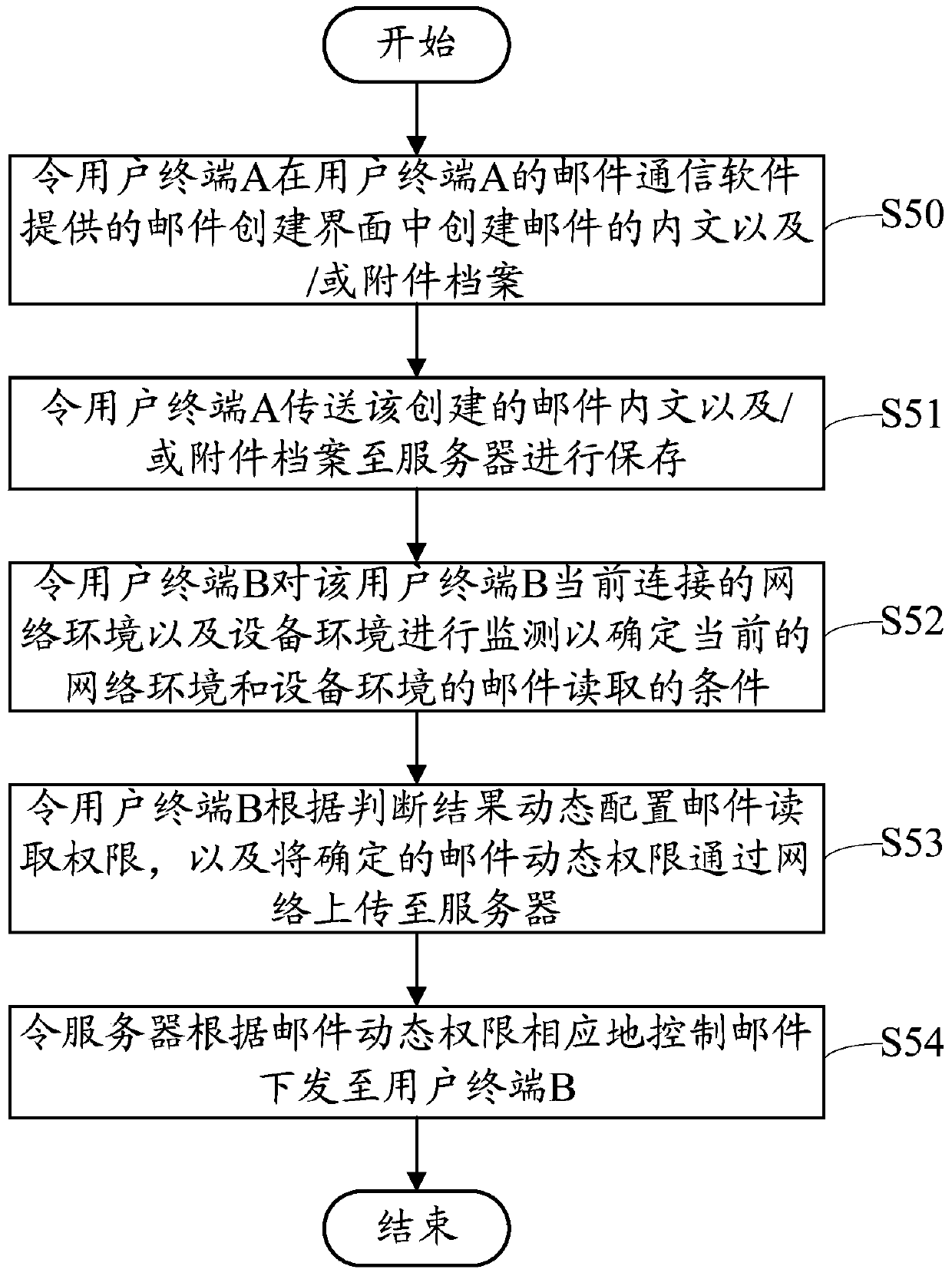
Mail reading system and method
ActiveCN103746900AFix leaked technical issuesData switching networksAuthority controlCommunications software
The invention provides a mail reading system, comprising a plurality of user terminals which are in mutual communication connection and a server in communication connection with each user terminal. Mail communication software, environment monitoring units and dynamic authority control units are installed in the user terminals. The environment monitoring units judge a condition allowing mail reading according to current network environment and equipment environment, the dynamic authority control units determine mail reading dynamic authority according to a judging result, and the server controls a mail to be issued to the user terminals according to mail reading dynamic authority reported by the user terminals. The invention also provides a mail reading method, and is used to solve the technical problem of mail information leakage caused by terminal insecurity and / or network environment insecurity.
Owner:福建省星云大数据应用服务有限公司
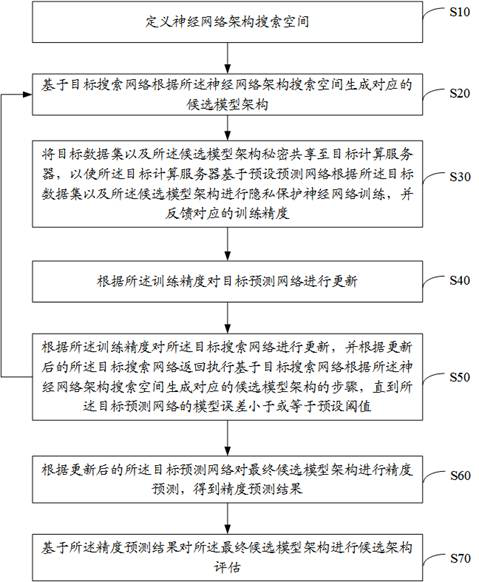
Neural network architecture search method, device, equipment and storage medium
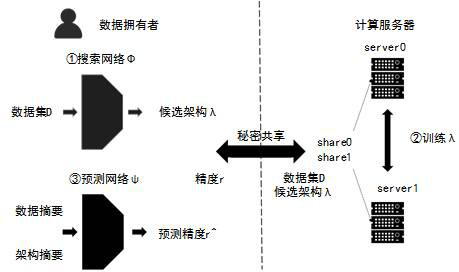
ActiveCN113962391BGuaranteed privacyFix leaked technical issuesDigital data protectionNeural architecturesData setNetwork generation
The invention relates to the technical field of neural networks, and discloses a neural network architecture search method, device, equipment and storage medium. Including: defining the neural network architecture search space; generating candidate model architectures based on the search network; sharing the data sets and candidate model architectures secretly to the computing server, so that the computing server can perform privacy-preserving neural network training and feedback training accuracy; update predictions based on training accuracy Network and search network, continue to search for candidate model architectures according to the updated search network until the model error of the prediction network reaches the threshold; perform accuracy prediction on the final candidate model architecture based on the updated prediction network, and perform candidate architecture evaluation on the final candidate model architecture . The data owner initiates the model architecture search task, uses the secret sharing method to send the data set, and outsources computing tasks such as model training to the computing server, which ensures the privacy of the model and solves the problem of model structure leakage caused by the architecture search.
Owner:PENG CHENG LAB
Camera device, video monitoring system, and video monitoring method
ActiveCN104159076BFix leaked technical issuesPrevent leakageTelevision system detailsColor television detailsVideo monitoringWork function
The invention discloses a camera-shooting device, a video monitoring system and a video monitoring method. The method comprises the steps as follows: firstly, a router is adopted for monitoring a designated mobile communication device, and after the mobile communication device is monitored, if being kept in the working state currently, the camera-shooting device outputs an operation stopping instruction; secondly, when no mobile communication device arranged in advance is monitored, if being kept in the non-working state currently, the camera-shooting device outputs an operation starting instruction; thirdly, the camera-shooting device stops the working function after receiving the operation stopping instruction; fourthly, the camera-shooting device starts the working function after receiving the operation starting instruction. Through utilizing the camera-shooting device, the video monitoring system and the video monitoring method, the private information leakage of a user is avoided, and the security monitoring and control are realized.
Owner:BEIJING QIHOO TECH CO LTD
Mobile communication device, video monitoring system and video monitoring method
ActiveCN104093007BFix leaked technical issuesPrevent leakageClosed circuit television systemsTransmissionVideo monitoringWork function
Owner:BEIJING QIHOO TECH CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com